Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

Walsh, a new community under construction on 7,200 acres of former ranch land near Fort Worth, Texas, will one day contain 15,000 homes.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

The Galaxy S8 has finally touched down, and it's an absolutely gorgeous device. Samsung's brand new flagship comes jam-packed with new features — some refined, and some that aren't. Luckily, we've compiled some major features to help you get started as quickly as possible so you can go about the rest of your day and show off your shiny new S8 to friends and coworkers.

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

Kuru is called the shaking disease, its name derived from the Fore word for "to shake." Caused by an organism that infects the part of the brain that controls coordination, people afflicted with kuru shake uncontrollably.

Before you figure out how to strip the paint on your car to bare metal, you should should first ask the question, should I strip all of the paint off. Depending on the type of job you're doing, it may actually be better not to strip all of the paint off.

Greetings my fellow hackers, In the previous article, I discussed briefly about ransomwares and their devastating capabilities. Devastating in a way that ransomwares are not only known to encrypt files but to also lockout some specific functions of the system and hold it up for a ransom.

Welcome finally, to a tutorial on buffer overflows! At last we have reached an exciting part of this series where I will dedicate the entire article on explaining and exploiting the notorious vulnerability. Grab some popcorn, sit back and enjoy the show.

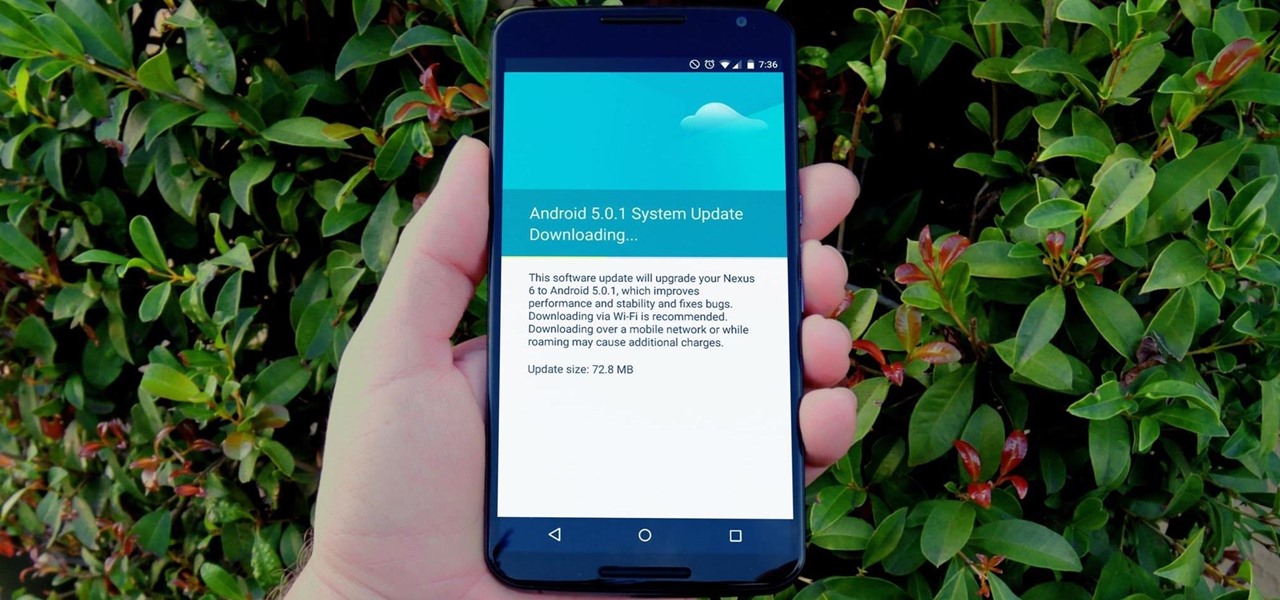
Update (February 2019): The methods below will help on older Android versions, but we've recently revisited this topic. So if you have a newer Android phone and you want to get rid of Google, head here.

One of the main reasons to buy a Nexus device is the fact that they're always the first to get new Android updates. Another great selling point for the Nexus series is that the devices are amongst the easiest to root and mod. Unfortunately, though, these two features are somewhat mutually exclusive.

To say we're a nation of coffee-lovers is putting it mildly. Americans consume 400 million cups of joe in one day alone, but how well do we actually know our morning BFF? We know it comes from a bean, and that more coffee drinks exist than there are ways to skin a pig, but what else?

The world of spices can be bewildering. They promise to make your food more flavorful if you know how to make the most of them. Unless you know a couple of essential tricks, however, it just seems like you're adding bits of colored powder to your food.

It's universally known that broccoli, kale, Brussels sprouts, cauliflower, and all cruciferous vegetables (also known as brassicas) are good for you—but you probably don't know exactly how good they really are.

Foodies and big-time chefs like Thomas Keller go crazy for fleur de sel. This finishing salt appears in fancy eateries and cookbooks the world over, and in the early 2000s, it was not uncommon to see diners in a high-end restaurant sprinkle a pinch of fleur de sel on their plates from their own personal stash.

Many of the beauty products you buy at drug and department stores are loaded with potentially toxic ingredients like parabens, while their active ingredients are made of things like glycolic, lactic, malic, and alpha hydroxy acids and retinoids, which are all derived from foods.

Hard-boiled (also known as hard-cooked) eggs are notoriously easy to mess up. We've all ended up with tough, rubbery egg whites and overcooked yolks that have that unappetizing gray-green ring around the edge. An ideal hard-cooked egg has a firm yet tender white, while the yolk is creamy and well-done without being mealy.

Hello, all. In this article, I will be showing you how to make one of the most useful products known to man. I am talking, of course, about charcoal.

Thought I would cross-post a piece I did a while ago.

Not that long ago I wrote an article discussing what it would be like, realistically, if you were to accidentally travel back in time to the Victorian era. At the end of that article, I mentioned that the best thing you could bring with you on a time-traveling adventure is a Kindle, or similar e-reader, stuffed full of the knowledge of the 21st century. Why a Kindle? Well, I own a Kindle, and I love it. However, there's far more to it than that.

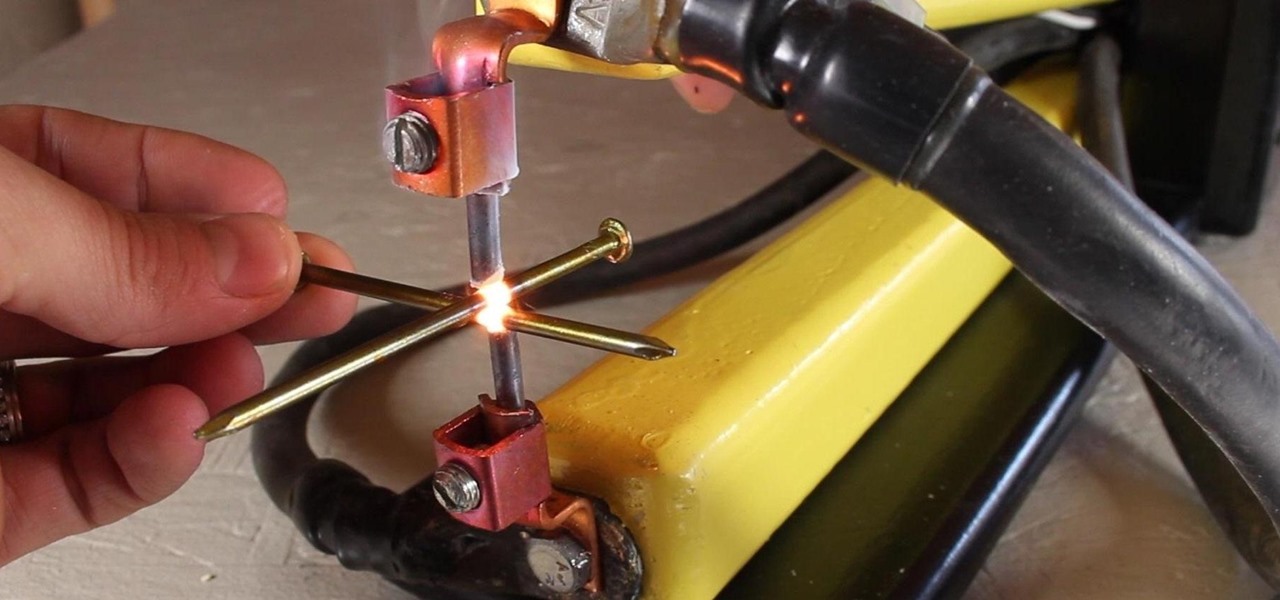
A typical resistance spot welder can range in price from about $200-$800, but with a little resourcefulness and a bit of free time, you can make one like this for about $10 or less.

All kinds of people pretend to be someone they're not on the internet, including scammers, people attempting to wind others up, hackers and web predators. Almost all of these people will leave bases uncovered and they're all easy to expose when you understand how to. Here are my favorite ways of finding out when somebody is lying quickly. Image Search

Today's post is a small go-to guide for beginner programmers in Null Byte. With many of our community members picking up programming from our Community Bytes, it only makes sense to lay out a one-stop guide for your reference. Hopefully this guide will help you make an educated and thoughtful choice on what programming languages you want to learn, and how you want to learn said languages.

In this series of car restoration videos, our body shop owner and hot rod designer shows you how to restore the exterior of that old classic car back into like-new condition. He demonstrates ways to expose rust, grind it away and then repair the body section which rusted.

Apple's newest software update, iOS 17.5 includes one killer new feature for people who like word games: another lexical challenge to complement the crossword puzzles that Apple News already has.

Android has a new security feature that every Android smartphone user needs to start using — even you. It won't change how you use your phone, but it will make life harder for nearby thieves.

While I prefer Android in my personal life, I've had the opportunity to work in the Apple ecosystem. One of the coolest features I've come to rely on is AirDrop, which makes it easy to beam content from mobile devices to desktops and vice versa. Thankfully, Android now has an equivalent.

If you haven't been using Spotlight Search on your iPhone, we've got ten reasons for you to start. Apple's made some significant improvements to the search interface available on the Home Screen and Lock Screen, and it's more useful than ever.

To celebrate YouTube's 17th birthday, Google has gifted the app with new features, including pinch to zoom, precise seeking, and a darker dark theme. But the highlight is a new cosmetic upgrade called Ambient mode, which makes the viewing experience more immersive. Here's everything we know about the new background effect.

When we got our first look at US Army soldiers testing Microsoft's modified HoloLens 2 last year, it still looked very much like the commercial edition, with some additional sensors attached.

Almost 190 secret characters are hiding behind your iPhone's default keyboard, and I'm not talking about what you see after tapping the "123" or "#+=" keys. These special composite characters can include accents, dots, and other diacritics, and you'll even see some strange typographical characters like the section sign, inverted marks, and per mille symbol. Here's how you find them.

Throughout Thursday's virtual Snap Partner Summit, Snapchat's parent company made a profound statement: If you use Snapchat, you're a creator.

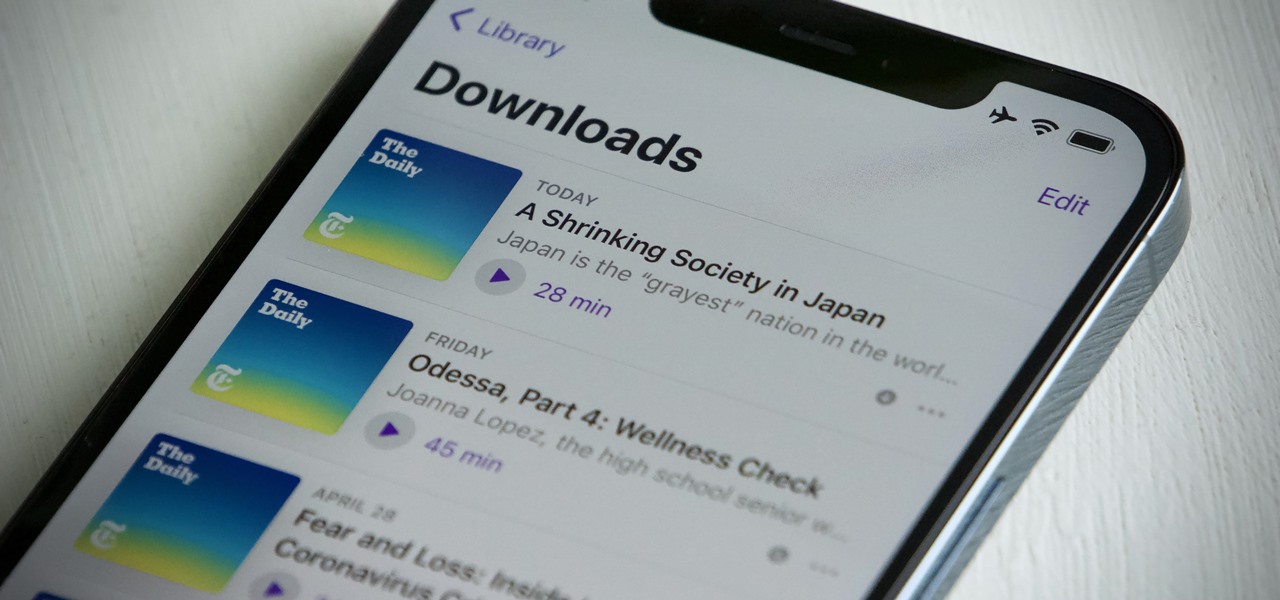
Apple's iOS 14.5 overhauled the Podcasts app, combining new aesthetics with smart and efficient features. While you might find the app better at playing your favorite podcasts than past versions, you might also find something negative about the update on your iPhone: it may be eating up your storage.

Many of us choose to use an iPhone — as well as other devices in the Apple ecosystem — because of the company's dedication to user privacy and security. If you need more proof of that commitment, look no further than iOS 14.5, released April 26, which adds new tools to protect our data while browsing the web and more control over the data installed apps collect on us.

The new iPhone 12, 12 mini, 12 Pro, and 12 Pro Max may seem like minor updates to the iPhone 11 lineup, but there are quite a few features that make them worth the upgrade. Apple has done a good job of highlighting all of those features, but some didn't get all of the love they deserved.

Apple's latest update, iOS 14.2, is finally here. As the name implies, it's the second major update to hit iPhones since Apple released iOS 14 in the fall. The update brings at least 13 new features and changes to all compatible iPhones, including over 100 new emoji and eight new wallpapers.

Apple just released iOS 13.6.1 for iPhone today, Wednesday, Aug. 12. The update is the latest public update for iPhones since iOS 13.6, which Apple released 28 days ago.

Apple released the second developer beta for iOS 13.6 today, Tuesday, June 9. This update comes one week after the release of its first developer and public betas, previously called iOS 13.5.5, as well as the general release of iOS 13.5.1. Apple's first 13.5.5 beta introduced evidence for Apple News+ audio support.

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.