It seems nowadays there's no limit to what type of companies are looking to invest in augmented reality. Given both the positive outlook on the future of AR, and its reported benefits for efficiency in employees, this makes sense. Safran, an international corporation with three main sectors—aerospace, defense, and security—is one such company taking the plunge into incorporating AR in their business.

Most popular virtual reality headsets, like the HTC Vive and Oculus Rift, require a tethered connection to the computer and that imposes some obvious restrictions on how much we can move in our space. We'd all prefer a simpler, untethered option, and Intel wants to provide just that.

In evolutionary times, we were far more likely to die from starvation than from diseases related to obesity. In those times, when food was available, it was best to stuff oneself.
A redstone clock is a pretty easy mechanism to make. A digital readout for that redstone clock is a little harder, and that's what Lesnoydude has made that won him the staff choice award.

In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.

We may not know what Magic Leap's product looks like. And we haven't received even a "save the date" for its launch. But we know that it will display mixed reality comics from Madefire when whatever it is arrives.

Cytochrome P450 (P450s) are proteins found in nearly all living organisms, which play roles that range from producing essential compounds and hormones to metabolizing drugs and toxins. We use some of the compounds synthesized by P450 in plants as medical treatments, but the slow growth and limited supply of these plants have put the drugs' availability in jeopardy and jacked up prices.

At Facebook's first Communities Summit, admins from top Facebook groups assembled to discuss tools to better manage and optimize their members. Here, Facebook CEO Mark Zuckerberg announced that these changes fuel the company's shifting focus from connecting the world to uniting it.

Usually, the mucus lining of the female genital tract presents a barrier that helps prevent infections. But, somehow, the bacteria that causes gonorrhea gets around and through that barrier to invade the female genital tract.

Augmented reality and computer vision company Blippar has a new lease on life, as previous investor Candy Ventures has completed a successful bid to acquire the assets of the beleaguered company.

So you're thinking about downloading the Galaxy S8 Oreo beta, but you're not sure if it's stable enough to use. It is a beta, of course, so you might want to wait for others to give it a try. Over the past ten days I've used the Galaxy S8+ running Android Oreo as my daily driver, running down the best new features. Let's take a look at the bugs, the performance, and the battery life.

As if the swollen, painful joints of rheumatoid arthritis weren't enough, the disease is the result of our immune system turning against cells of our own body. Ever since this realization, scientists have worked to find the trigger that sets the immune system off. Scientists believe that gut bacteria may have a role in initiating the abnormal immune response. Now, a team of researchers from Boston has figured out how that might occur.

Heart disease is the leading cause of death of men and women in the US. Over half a million Americans die from it annually. Atherosclerosis — a build up of plaque in the arteries — is a common feature of heart disease and can be caused by smoking, fats and cholesterol in the blood, diabetes, and high blood pressure.

Warning: If you are eating and for some reason still decided to click on this article, turn around now. Maui, Hawaii health officials have reported finding at least six cases of angiostrongyliasis, a parasitic lungworm that infects humans. Colloquially, it's known as rat lungworm disease. And if you think that name is awful, just wait until you hear what it does to the human body.

The search for a cancer treatment that selectively finds and kills only the cancerous cells has just made a giant leap forward.

With the height of the flu season ahead, there are some good reasons to keep a flu vaccination in mind.

True innovation tends to come from the places we least expect as developers. The Microsoft HoloLens is still a very new product, and some of the other headsets are still just ideas, so the rules for mixed reality are not set in stone. That means all the real problems to be solved are yet to come.

When most people say, "Damn, look at that rock," regarding an engagement ring, they're usually not referencing an actual rock—let alone a space rock.

Welcome back, my greenhorn hackers! In many cases when a computer, phone, or mobile device is seized for evidence, the system will have graphic images that might be used as evidence. Obviously, in some cases these graphic images may be the evidence such as in child pornography cases. In other situations, the graphic images may tell us something about where and when the suspect was somewhere specific.

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

We all carry a bit of anxiety around with us. Is our boss still annoyed because we could barely stay awake in yesterday's pre-dawn meeting? Will our friend hate us forever because we forgot to call them back two weeks ago? Whatever worries pop up in your mind, whether they're monumental or insignificant, it can be hard to quiet those nagging voices, but you can shut down your nonstop mind with a bit of relaxation, distraction, and action.

Welcome back, my budding hackers! I began this series on Linux basics because several of you have expressed befuddlement at working with BackTrack on Linux. As a hacker, there is no substitute for Linux skills.

The latest set of emoji characters, Emoji 14.0, was approved on Sept. 14, 2021, less than a week before iOS 15 and iPadOS 15 hit supported iPhone and iPad models. There wasn't any time to get any new emoji into iOS 15.0, but they're out now in the iOS 15.4 update. So get ready for "Melting Face," "Biting Lip," and "Troll," to name just a few.

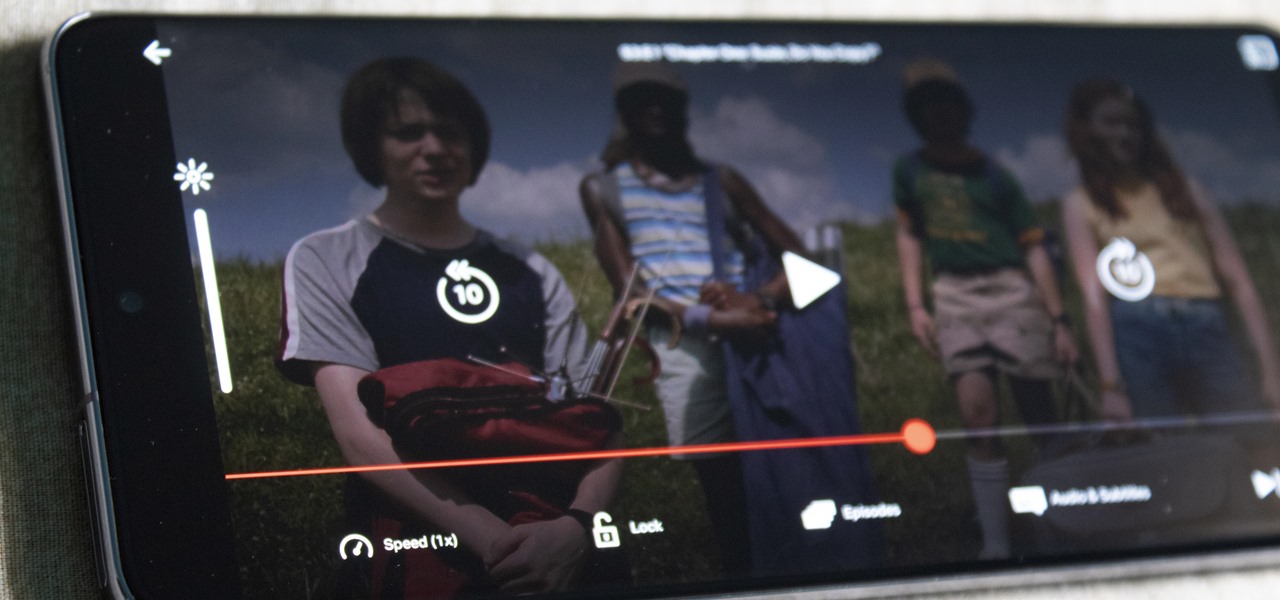
Not including playback speed controls in a video app is a design flaw. These controls are useful tools that let you speed up or slow it down a video. Want to catch all the Easter eggs in Avengers: Infinity Wars? Slow it down. Want to rewatch the last season of Strangers Things before the new season arrives? Speed it up.

The long wait is over — the best augmented reality device on the planet is finally available.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

| Update: ZTE's issues with the US government have finally been resolved. Check out the details below.

After more than a year and a half of silence, the rumors have morphed into reality: Microsoft has finally released an update for the HoloLens. And with that update comes a collection of new features that hint at big plans for the HoloLens this year.

Microbial cells can improve the functionality of clothes in creative and useful ways, including cooling us down during a workout or making clothing glow for better visibility.

A terrifying antibiotic-resistant superbug, one thought to only infect hospital patients, has made its debut in the real world. For the first time ever, the superbug carbapenem-resistant Enterobacteriaceae (CRE) infected six people who hadn't been in or around a hospital in at least a year, and researchers aren't sure how they got infected.

In recent weeks, some people have been shunned from the Null Byte community because they expressed "black hat" aspirations. This is because Null Byte is the "white hat" hacker training/playground. Although most of us think we know what that means, it does beg the question; "Who and what is a white hat hacker?"

Welcome back, my tenderfoot hackers! Well, the first season of Mr. Robot just ended and Elliot and fsociety successfully took down Evil Corp! They have effectively destroyed over 70% of the world's consumer and student debt! Free at last! Free at last! Of course, global financial markets crashed as well, but that's another story.

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

Ever since the much-lauded effects of the Mediterranean diet became widely known, people have been buying olive oil by the gallon. A diet that prevents heart disease, is based on fresh, seasonal foods, and includes a tasty as hell fat like olive oil? Duh—that's a no-brainer.

The hype train that left the station years ago has reached its first stop, and now we finally have access to the Magic Leap One, the device many have claimed would revolutionize the augmented reality space at launch. But is that really true?

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

There are all kinds of theories—many supported by science—about what causes Alzheimer's disease. Tangles of protein called ß-amyloid (pronounced beta amyloid) plaques are prominently on the list of possible causes or, at least, contributors. An emerging theory of the disease suggests that those plaques aren't the problem, but are actually our brains' defenders. They show up to help fight an infection, and decades later, they become the problem.

Hi everyone. Recently I've been studying some topics about Assembly, memory and exploitation, and thought I could write something nice, easy and fast about it, just because I like to share what I learn, and probably sharing what you learn and trying to explain it to a stranger is the best way to learn it better. It worked for me, and I hope it will be useful for you too.

If you've jumped on board HBO Max to watch more than just HBO's content, such as DC films, Looney Tunes, Turner Classic Movies, Cartoon Network, and movies from Warner Bros., there is a downside to HBO's improved service. Namely, you cannot use it on all of your devices yet. The most notable omission is Roku players and TVs. But there are workarounds you can use until an official app comes out.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.