This works well for short hair. First of all you need to have artificial hair extensions of golden color or any other color of your choice. You also need a glue gun and hair clips to hold these extensions to your real hair. You can choose to fix these extensions on the left side of your head, just below the hair. Lift your hair at the left sides, add some glue using the glue gun and place the extension. Now add clips to fix it on your hair. Carefully conceal it below your real hair. Take care...
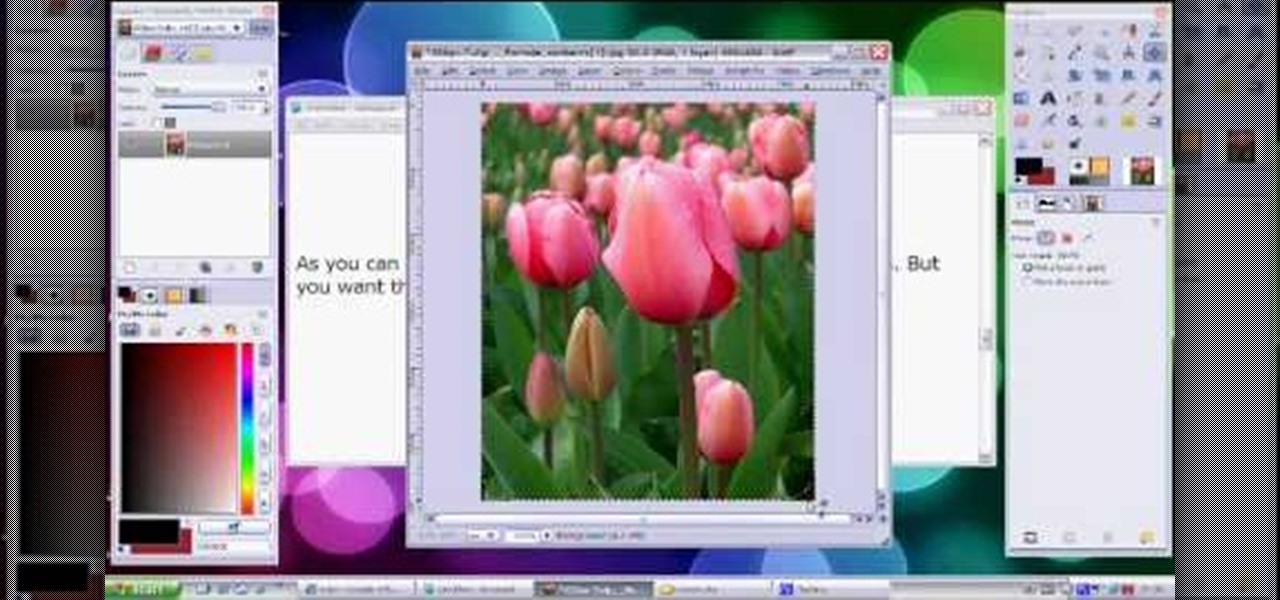
Video demonstrates how to make rounded corners in GIMP. First step is to open an image. The image needs to have transparency for this to work. An alpha channel is to be added to the image. This can be done by going to the layer option in that select transparency and add alpha channel. By doing this if the picture grays out it means the image already has transparency and there is no need to add an alpha channel. Now Select option is selected and in that rounded rectangle is selected. The radiu...

This genius video shows the viewers how to easily embed and add a YouTube video into a PowerPoint presentation with no internet connection! First you will need to make sure you are using Firefox. After getting Firefox, make sure you install a Firefox Add-on called Video downloader. To get this add-on, Google 'video downloader' and install the add-on. you will see a new icon at the bottom of the screen to the right. First, go to the video you would like to download on YouTube and click on the ...

Richpin demonstrates how to remove the inner tie rod end on an automobile. First, get the car up in the air and support it by jack stands. Remove the wheel assembly.
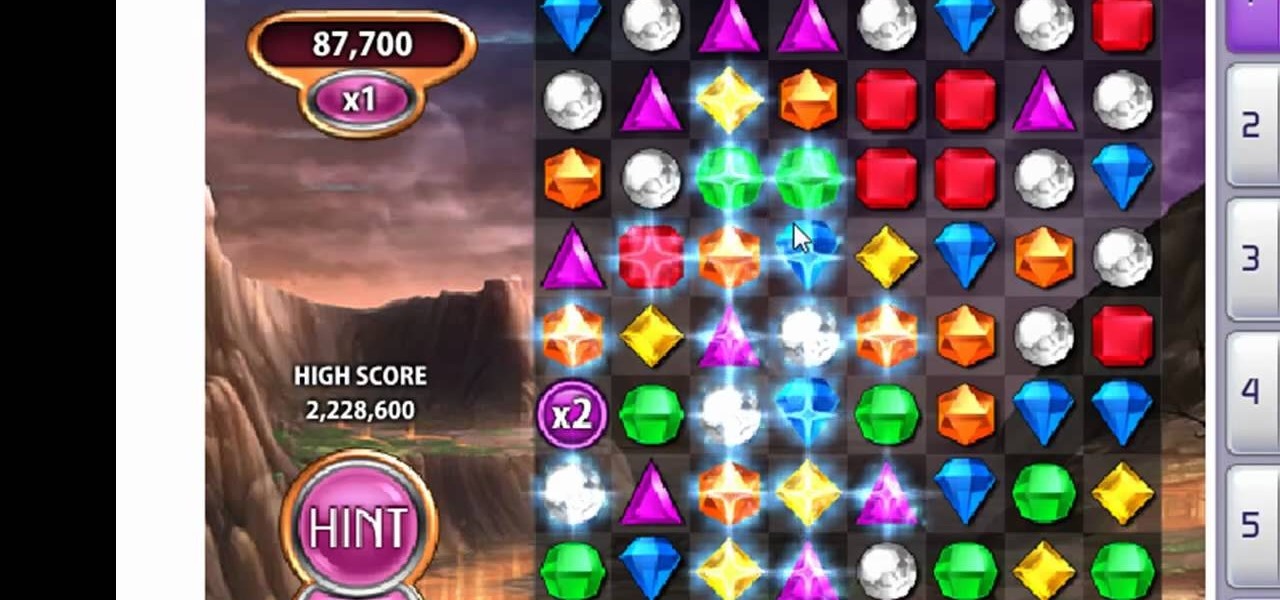
There's no Cheat Engine involved in this Bejeweled Blitz hack. This hack relies on Firefox and a certain extension made specifically for Blitz.

Learn how to do neutral grip pull ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do seated leg presses. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do single arm pec decks. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do medicine ball knee tucks. Presented by Real Jock Gay Fitness Health & Life. Benefits

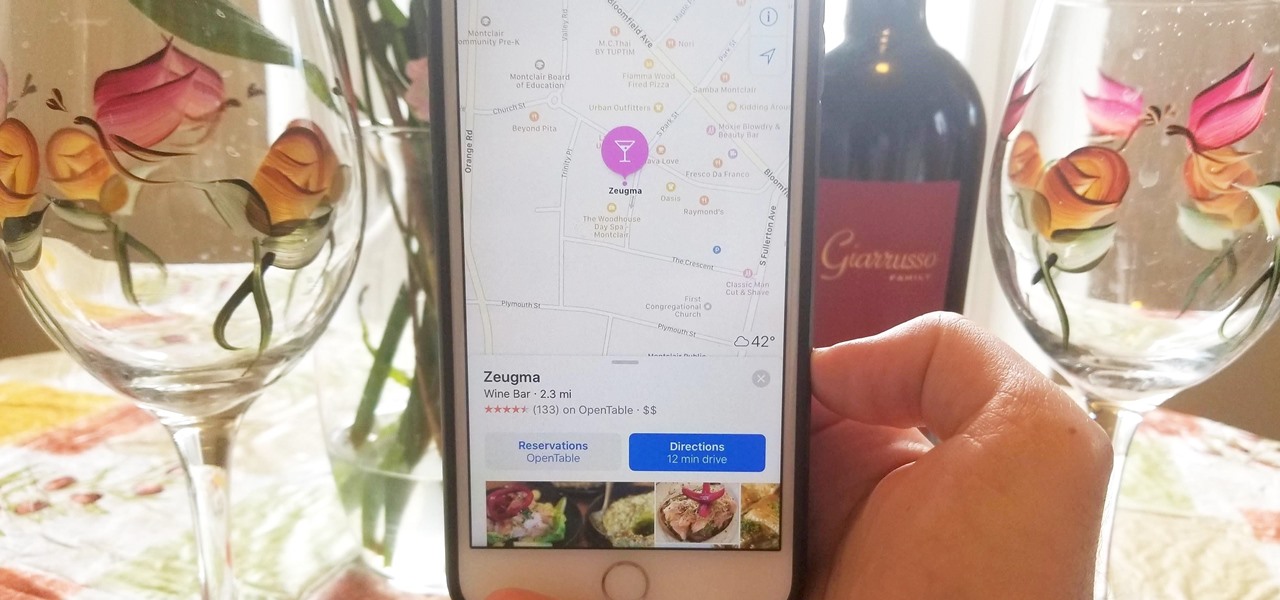
Apple has taken great strides to ensure that iPhone users are having an Apple Maps experience on par or even better than Google Maps can provide. One of the factors powering this is extensions, which adds functionality to certain apps by giving them permission to interact. Among all the possibilities, one extension will let you reserve dinner tables right from inside Apple Maps.

When streaming services like Spotify or Pandora compete for customers, the main differentiating factor is the size of their libraries. While these and comparable services usually run somewhere around $10 per month, a completely free alternative may actually have the most expansive library out there.

Windows XP will always have a special place in my heart—it's the operating system I grew up on. It guided me through the glory days of AIM, Napster, and MySpace, but now it's dead. The OS that had been supported by Microsoft for twelve years officially lost its support on April 8th, 2014. Just like that, Microsoft has killed the beast, but for those of you who stubbornly refuse to cooperate, you can resurrect the dead. If you have Windows XP, this little known hack will get you further suppor...

Grow some of your own food by starting a vegetable garden. You'll eat better and save money. You Will Need

Make everyone in your neighborhood green with envy over your lush lawn with these landscaping secrets. Learn how to get your lawn green with this Howcast landscaping guide.

Learn how to do Super Chests. Presented by Real Jock Gay Fitness Health & Life. Starting Position

Dating websites allow you to see a person in a very intimate context, framing their successes and accomplishments in life to an important audience. The information contained in these profiles often can't be found elsewhere, offering a unique look into the personal life of the user.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

Thanks to its longevity and familiarity among web designers, Flash is still alive and thriving, but HTML5 is catching up since it can render faster in web browsers, can be customized by developers on a per platform basis, doesn't need a plugin to run, and is less vulnerable than Adobe Flash Player to attacks (for the moment).

Amazon's Fire TV set-top box has been out for over a month now, and the hacks are starting to come together. Sure you can play your Amazon Instant Video, Hulu, and Netflix content without any issue, but what about your personal media, like movies and music?

I read a ton of articles online and I am always looking for a way to make the experience a little better. Reading long articles can be tiresome, and if an article has multiple pages, I will most likely skip it. With the ability to endlessly scroll, no site should have multiple pages. It's just a sneaky way to get more page views, IMHO.

It's all about widgets. Widgets are one of the most important features on an Android phone—they can provide valuable information at a glance and are easily customizable.

Social media is where we post our thoughts for the world to see, but sometimes a little more exclusivity is needed. And that's where Scrambls comes in.

You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information inside of plain text, and we can even figure out who's leaking documents online.

My favorite color is blue, but if everyone I knew said the same thing, I'd probably switch to red—there's nothing cool about uniformity. One place I'm guaranteed to see plenty of my favorite hue is on Facebook. The social network has gone through many redesigns, but its signature color scheme has never changed. While Facebook introduced cover photos, which allows for a little more creativity on your Facebook page, everything else is pretty much the same across all one billion plus profiles. B...

One of the most promising avenues of attack in a web application is the file upload. With results ranging from XSS to full-blown code execution, file uploads are an attractive target for hackers. There are usually restrictions in place that can make it challenging to execute an attack, but there are various techniques a hacker could use to beat file upload restrictions to get a shell.

Greetings my fellow hackers, In the previous article, I discussed briefly about ransomwares and their devastating capabilities. Devastating in a way that ransomwares are not only known to encrypt files but to also lockout some specific functions of the system and hold it up for a ransom.

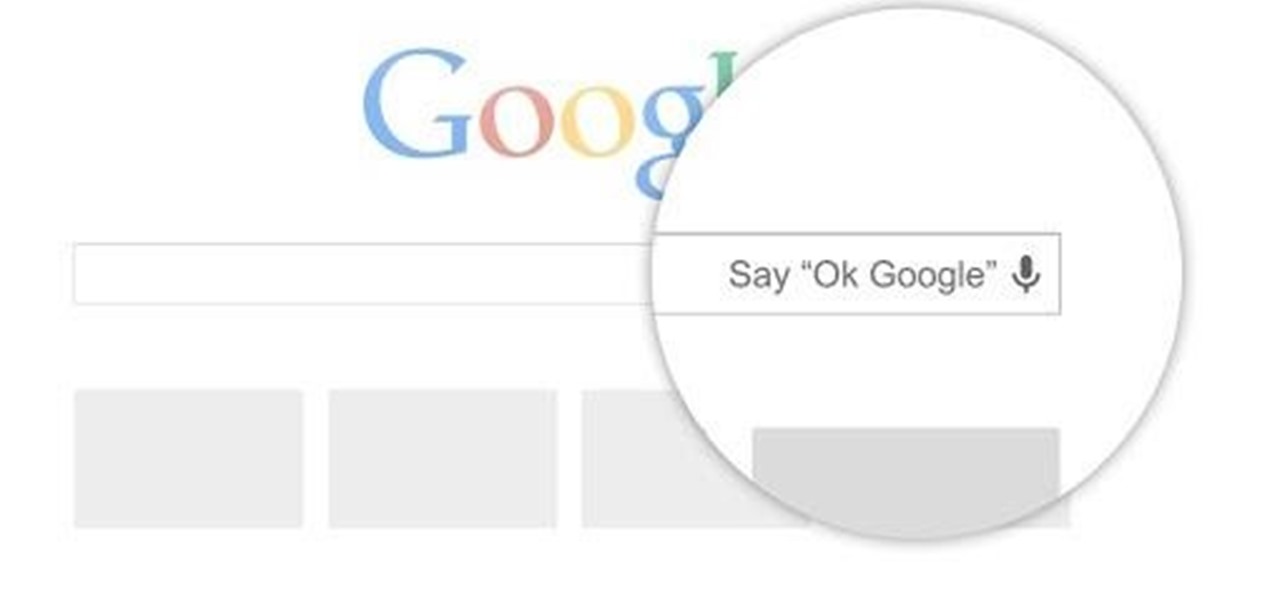
Google hasn't let the throne make them complacent. The king of search has brought one of its newest and most popular mobile features to the desktop. Folks with the latest 4.4 KitKat software available on the Nexus 5 (or those who've installed the awesome APKs we covered for the Galaxy Note 2 and Galaxy S3) have had the "Ok, Google" search feature for a while now.

We've all had that awful, sinking feeling when something you've been typing away at is suddenly gone. Maybe you accidentally hit the Back button, lost your internet connection, or your computer crashed, but whatever the reason, losing your work totally sucks. A lot of word processing programs have a built-in auto-save feature to prevent you from losing everything, but most websites and blogs haven't gotten there yet. An extension for Chrome and Firefox called Lazarus: Form Recovery can help y...

If I'm in a hurry, sometimes I'll just turn my computer off and rush out of the house. Sometimes, I'm in the middle of a long YouTube video when I dash off, only to come back and find that my video position has been tragically lost. Hopefully I don't lose my place in that motorcycle accident compilation video when I get ba... damn it.

For over three years, Facebook users have been able to clog up their Facebook chats with little pictures of smiley faces and red hearts, but now it has finally gone a step further...

In this Software video tutorial you will learn how to mount an image using Daemon Tools Lite. This software takes many different types files and puts them on a virtual DVD drive. Go to www.daemon-tools.cc and download the Daemon Tools Lite program. You then install it. After that double click on the icon on your desktop and it will appear on the bottom right hand corner of the screen. It will say Daemon Tools and the version. Right click > virtual Cd/DVD ROM. To mount an image, click on ‘mo...

This pilates how-to video illustrates the Swimming exercise. This pilates exercise is good for core stabilization, upper back extension and hip extension. This is good to improve back strength and those deep abdominal stabilizers.

Amazon.com has been around for a long time now, but there are still a few things most people don't know about when it comes to buying products from them. Here's a quick roundup of tips to help you get the most out of Amazon and save some money in the process. The holidays are the busiest time of year for online shopping, but these tricks will work all year around.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

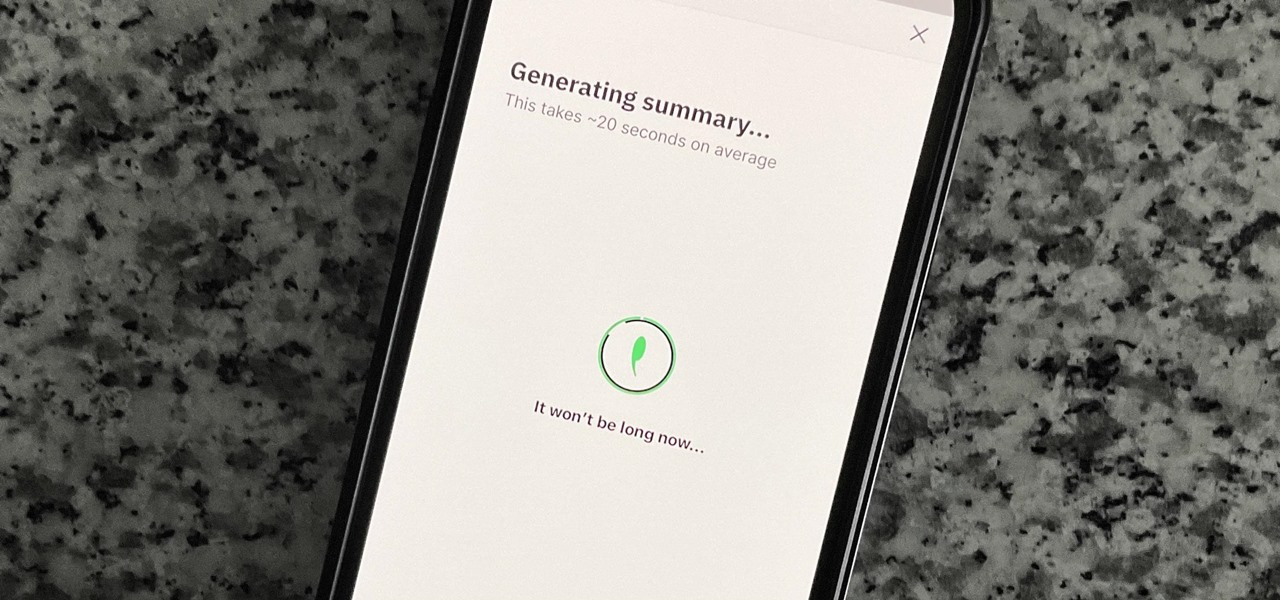
If you're like me, you don't have time to sit down and leisurely read an entire article from start to finish — but you still want to be informed throughout the day. Instead of just browsing the daily headlines, there's a free service that will summarize any article you throw at it, giving you a better idea of what's going on without committing to reading an entire article.

You're reading this so you're probably already safely huddled up in your house or apartment, watching as the entire planet grapples with the unfolding coronavirus health crisis. But unlike some others, you're lucky enough to already have a couple of weeks of supplies and now it's just about what you can do to entertain yourself and your family as you weather the current situation.

For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.

My message to Russian hackers is this: LEAVE BRITNEY ALONE! Russian hacking collective Turla has been targeting governments and military operations in the United States, Europe, Asia, and the Middle East for the past decade. Now, it appears that the group is targeting everyday citizens — specifically Britney Spears fans.