File Transfer Protocol, or FTP, is a network protocol made for transferring files in a client and host fashion over a Transmission Control Protocol (TCP) network, such as the internet. FTP is integrated into most browsers, and you have probably used it before. It is a common way to host files and transfer them easily. To access an FTP, a login is required, unless the server is configured to use anonymous logins (like the Arch Linux mirrors).

XSS stands for cross-site scripting, which is a form of web-based exploitation that uses client-side vulnerabilities in a web page to execute malicious JavaScript codes. JavaScript is referred to as "cross-site" because it usually involves an external website containing the malicious code. That code is most commonly used to steal cookies with a website that the attacker created and hosted on another server. The cookies can then be used to escalate privileges and gain root access to someone's ...

Though it could be argued that Apple's popular and widely used iTunes media player was responsible for the growth and explosion of podcasting, I would argue that iTunes is not the best way to manage and listen to your podcast subscriptions—if you're a iPhone, iPad, or iPod Touch user. Instead, you will find that a $1.99 mobile app called Instacast (iTunes App Store link) is a much better method. Below, a short video introduction to Instacast, plus a written breakdown of its features. Mobile L...

Do you ever wonder if the files you're trashing on your Mac are actually trash? Let's say there are 80 million computer owners running Mac OS. If each user trashes at least 10 files each day, that's 800 million deleted files that cease to exist every 24 hours. If that doesn't sound like a lot to you, a month would equal 24 billion junked files, a year—nearly 1 trillion.

There are a few different types of Apple iPhone and iPad users: general household users who largely consume media—e.g. surfing the web, watching movies, listening to music. Other iPhone and iPad owners use their device(s) to produce stuff—written documents, edited movies, blog posts, music tracks, and the like. And then there are those who are very mobile with their devices. They commute to and from work on a regular basis with their iPhone or iPad. Some users may travel a lot on business, or...

L.A. Noire is the newest Rockstar (GTA4, Red Dead Redemption) game created by Team Bondi ( The Getaway). The game is set in the late 1940’s in Los Angeles. The main character, Phelps, is a war veteran rising through the ranks from police officer to detective. The game is presented in mini episodes (one case per episode) and flashbacks. Once you finish a case, you go straight to the next one. Having played four cases where the character moves from police officer to detective, here are my initi...

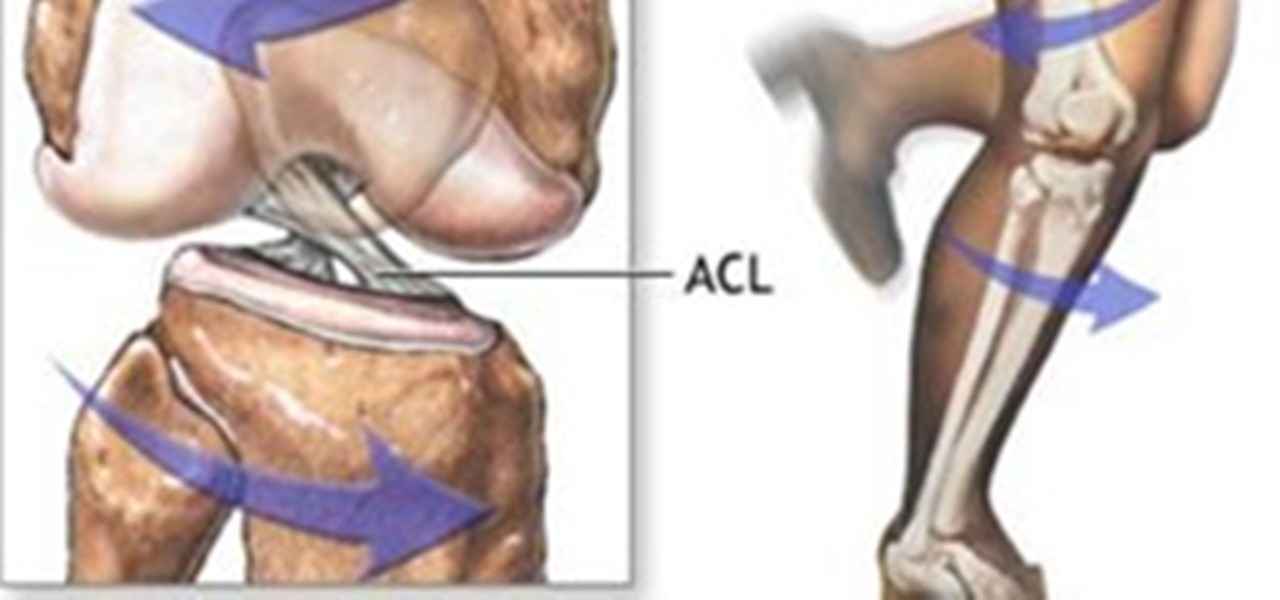
The sudden deceleration, shifting in the knee, popping sound and screaming from the intense pain that immediately follows is becoming increasingly common among our young athletes. Those who

Last week I talked about the video / image side of things, and as promised here is the audio side. Sound is integral to all studio productions, but for most student and low budget production, it's the last thing filmmakers seem to think about, and one of the most noticeable problems with low budget stuff. Sound IS half the experience, and yet it is usually all but forgotten come production.

The sudden deceleration, shifting in the knee, popping sound and screaming from the intense pain that immediately follows is becoming increasingly common among our young athletes. Those who have witnessed or suffered a torn anterior cruciate ligament (ACL) are familiar with the pain, surgery and intense 6 to 8 month rehabilitation that accompanies the injury, not to mention the disappointment of ending a season. Nationwide, this will occur more than 500,000 times this year, and female athlete...

Many things cause a bike tire to deflate. Glass, sharp rocks, tacks, and nails can pierce the tire and puncture the tube within. A tube can be pinched between the rim and tire causing the tube to split when inflated. If a tire has a hole in it, the tube, which is filled with air pressure, will bulge out of the opening and pop. As well, the valve holding the air pressure in the tube can be damaged or faulty.

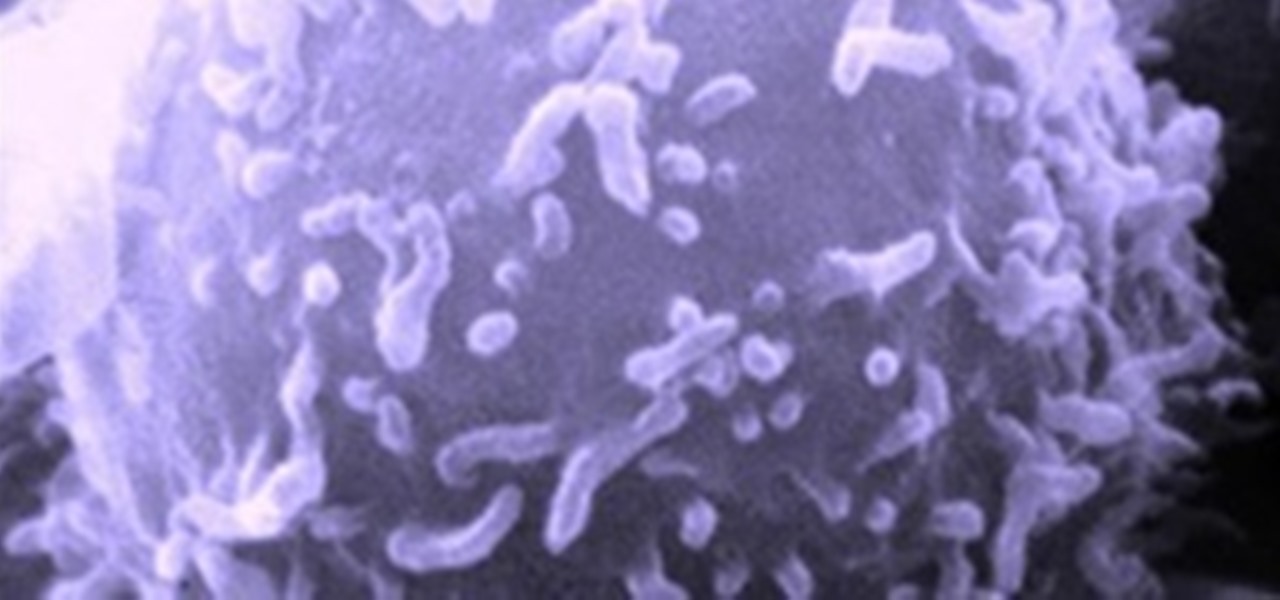
The immune system is not as simple as you might think. Simply, it's formed of two main groups of cells:

How is it that we use Firefox tremendously and yet not care for its needs? You might have noticed Firefox sometimes tends to slow and not respond often. You might have installed countless add-on in Firefox to enhance your using experience, to get the most out of your Firefox use these Hacks. The about:config page contains all most all of the tweaks and enhancements available for Firefox to day.

A lot of different places have computers with controls on them for several things; some have controls for installing software, some for running software, blocking websites, opening certain file formats, etc.
It’s hard to know where to start talking about a book like 2666. That’s partly because, in some ways, it’s actually five books. Published posthumously, the book begins with “A Note from the Author’s Heirs” explaining that, before his death, Bolano stipulated the book be published as five separate works. Instead, his friends and family opted to publish Bolano’s novel as he originally would have – as one single volume divided into five parts. Ultimately the five parts belong together. They shar...

If you've been reading, watching or listening to the news, you sure know about the Trayvon Martin case. If you visit this site often, you may also have noticed that I've not put up any news on this case. I have my reasons. And this post will describe why.

Computer viruses are terrifying. They are undetectable, dangerous, and operate constantly right under your nose. For the average computer user, there are only a few repair options. You could buy expensive antivirus software that causes more problems than it fixes, you can wipe your hard drive clean and lose all of your important data, or if all else fails—just switch to Linux.

If you follow the Anonymous, Occupy, and IT security scenes, you have no doubt heard about a dox release. What is it? How can it hurt you? And most importantly, how can you protect yourself from it? Some of these steps might seem common sense, while others will be an ah-ha! moment. Your private info is both your biggest weakness and your biggest weapon in your battle to remain anonymous. You must learn how to use it as both.

The immune system is not as simple as you might think. Simply, it's formed of two main groups of cells:

Haven't you ever wanted to live in a futuristic home? I think that homes are headed towards an era where they will be controlled by our computers and smartphones. No longer will you have to find your keys to unlock your door, or wait until you get home to monitor your security, because X10 is here.

Welcome to Minecraft World! Check out our advanced tutorials and come play with us on our free server.

When Apple‘s iTunes was introduced back in 2001, it rekindled my interest and purchasing of music. I was so excited by the program that I immediately started converting all my rather large collection of CDs into MP3 tracks. I then sold off my CDs and remaining vinyl albums, and used the money for additional iTunes purchases. iTunes made managing and listening music a wholly different experience. But in the last few years, iTunes has taken a back seat to streaming music services, which I find ...

Two new and radically different ARGs (Alternate Reality Games) have burst into the news in the last week, and illustrate the very best of an innovative phenomenon: the commercial tie-in ARG, and the public service ARG.

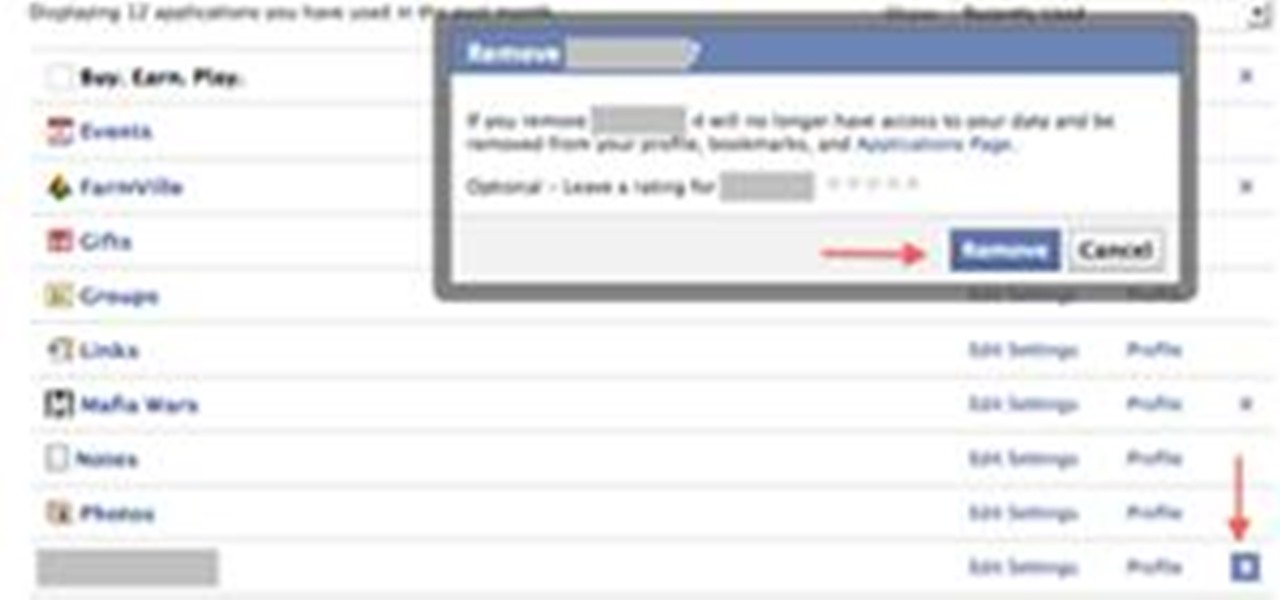
Please share this info with all your facebook friends. It's not just Farmville players that are affected by scams and spam! This post will help you keep your facebook account clean and safe. We start by showing you a scam and discussing what is real, then we show you how to remove pages you don't want, and finally how to remove apps you're not using. Please scroll down to which ever part you need!

Deadly natural disasters can happen at any moment— earthquakes, hurricanes, tsunamis, floods, fires and especially tornadoes. That's why you have to be prepared.

This is an intermediate guide on how to easily fix or retrieve data from a bad hard drive. What we're trying to do:

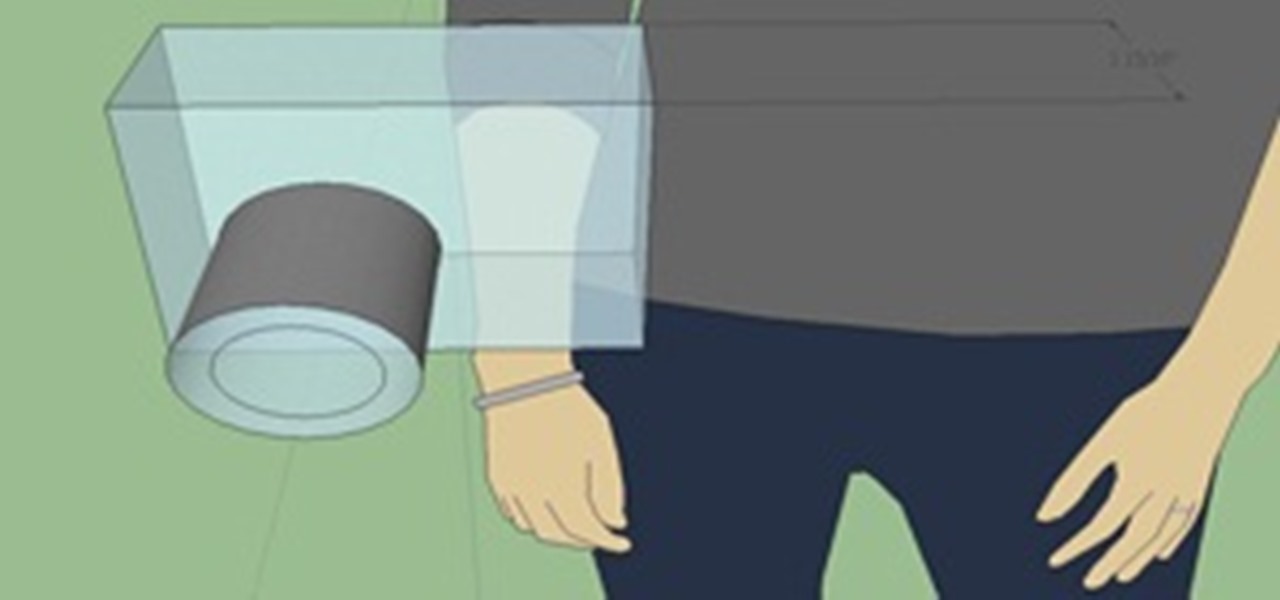
Creating any object you want is as simple as point and click if you have a 3D printer at home. If you don't have one handy, there are a few companies that offer printing services online. But to help services realize your design in extruded plastic, you have to make a 3D computer model for the printing machine. For beginners, the free Google SketchUp application is the best choice of software. Using only a few tool bar buttons and a scroll wheel computer mouse, you can model literally any obje...

Injection is an attack vector that involves breaking out of a data context and switching into a programming context through the use of special characters. These characters are significant to the interpreter being used, but not needed for the general user input being asked for.

This article is all about creating content. This is a very important concept to grasp because the content that you will learn how to create is going to be the basis for how you will advertise and promote your website. Content, meaning articles, videos, and even podcasts. Content is now really the new advertising. Instead of traditional types of advertising and instead of the traditional separation between editorial content and advertising, that has gone the way of the dinosaur.

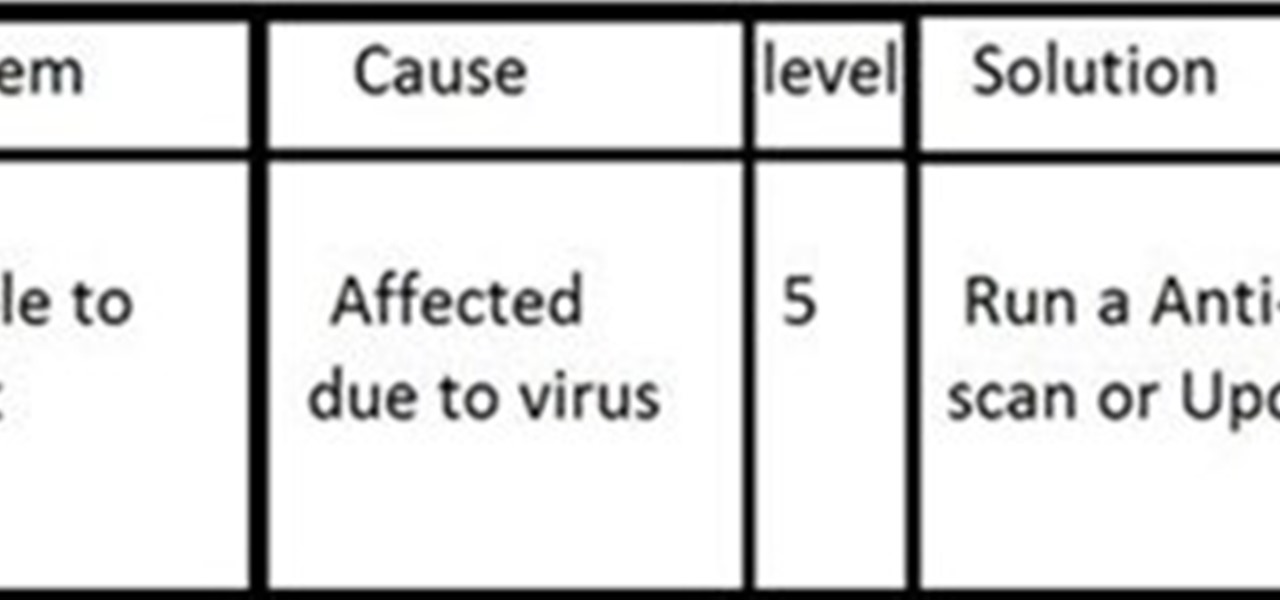
Many windows users, if not all, run into a virus infection once in a while. This is unavoidable when using Microsoft's operating system. Without digressing too much, the fact that Windows is such a popular OS with no controlled software sources makes it easy for viruses and malware to spread. And while there's a plethora of antivirus tools for Windows, sometimes infections (such as certain scareware) can disable the install and/or use of antivirus systems and render your OS unusable until cle...

Today's article serves as a general guide to keeping Windows 7 and Vista clean. The goal is to clean up your messy computer and have it running at maximum performance in no time. The question at hand is—what is your computer's performance like?
Sergio Peralta Advisor: Jessica Davis

Their were many pedestrians in the scene as,they seen firefighters struggling with the horrifying disaster and they couldn't do much only continue to stare as bodies continued to drop..

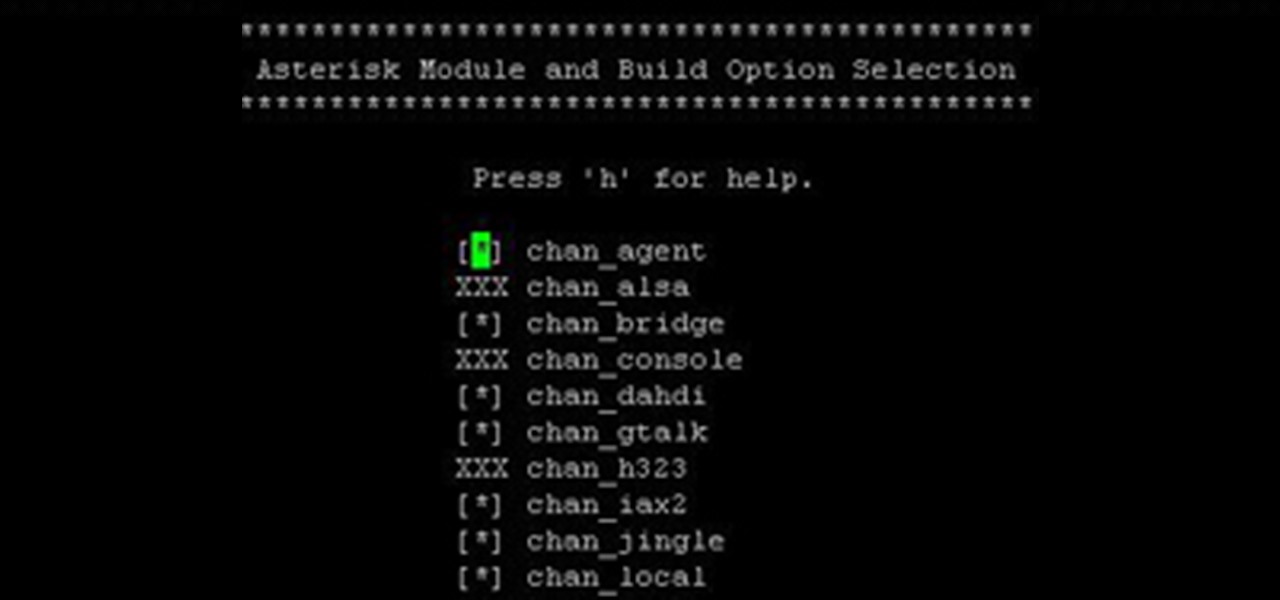
Over the years, I have enjoyed playing with Asterisk. I have found Asterisk to be extremely powerful and fun to play with. There are several books and many scattered how to articles out there, but most are outdated and the information required to build Asterisk from beginning to end can be a bit daunting. I wanted to combine all the steps into a single article and share my experience with everyone. If I have left out any steps please let me know.

Remember what life was like before your iPhone? Before there were palm-sized smartphones with seemingly endless features, there were phones like Motorola's RAZR that peaked with its embedded camera. Before that, there were simple flip phones with texting capabilities, bulky two-pound Gordon Gekkos—even briefcase phones.

INTRODUCTION The everyday PC user doesn't think much about its PC and problems that can cause critical damage to their data or other stuffs stored on Hard drive and other electronic parts until the problem actually occurs. Once a failure happens, the repairs can be costly and very time-consuming and one also have to sacrifice their data stored on hard drives if the damage is more severe!

STANDP'S CUSTOM DESKTOP "ASK NOT WHAT YOUR DESKTOP CAN DO FOR YOU...". http://standp-how-to-vidzzz.wonderhowto.com/corkboard/new-post/text/

STANDP'S WINDOWS 7 "ASTON-2" CUSTOMIZED DESKTOP IT ROCKS COMPLETELY!. DEC

To create an elegant WordPress blog or website from scratch without being noticed that you're a complete beginner, you need that drive and pairs of eyes and ears. It may seem difficult at first but it can truly be fun and exciting.