The new Samsung Galaxy S4 may be the only phone to include temperature and humidity sensors, but your Galaxy Note 2 has a few weather-detecting features of its own.

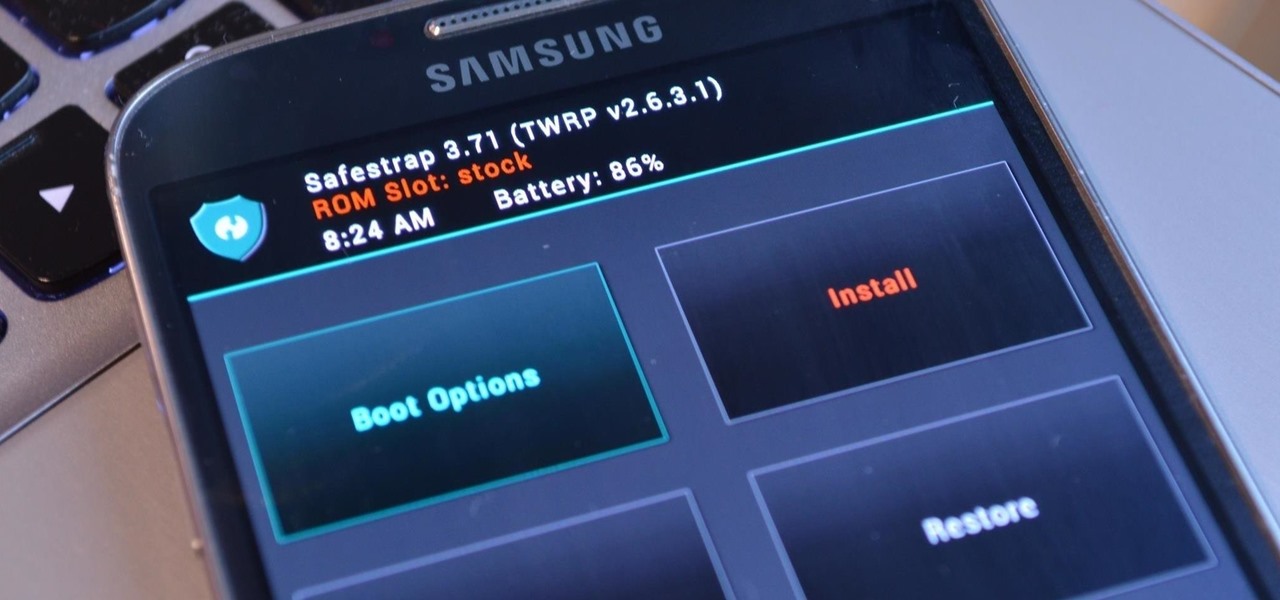
Advancements to Android's open source OS come in the form of ROMs and mods, available all over the web for anyone to find. Installing any of these modifications tends to wipe your phone clean, causing you to lose all of the precious data on your device.

I love my Mac to pieces, but there have been times, so many times, that I wanted to silence that classic Apple start-up chime. I mean, the only thing the sound does is notify everyone around you that you have a Mac, and that you have turned said Mac on, right? Well it's not so vain.

If you have a Mac, you've probably been anticipating the release of OS X Mountain Lion. If you have multiple Macs, you've probably been dreading the long process of downloading and installing it on all of them. Here's how to create a bootable backup disk and save yourself some time. Before You Start

You can learn to deal with the thing we all dread, a computer crash. Hopefully you diligently back up work but even if that's not case, stay calm. There is still hope and even if you're not a wiz at computers there are people out there who can help.

In this how-to video, you will learn how to send a fax for free with your computer. First, go to the website MyFax. You will see a screen with forms to fill. Fill out the appropriate information, such as your name and who you are sending it to. You can also enter an external message with the fax. You can then upload the file you want to fax onto the form. Once this is done, enter the email addresses of the people whom you will be sending the fax to. Once this is all filled out, click on the b...

No more carrying around heavy laptops and thousands of Linux Live CDs and USBs to always be ready for pentesting on the fly!

When you don't have a steady cellular signal or immediate Wi-Fi access but need to communicate with others around you, you can set up an off-the-grid voice communications network using a Raspberry Pi and an Android app.

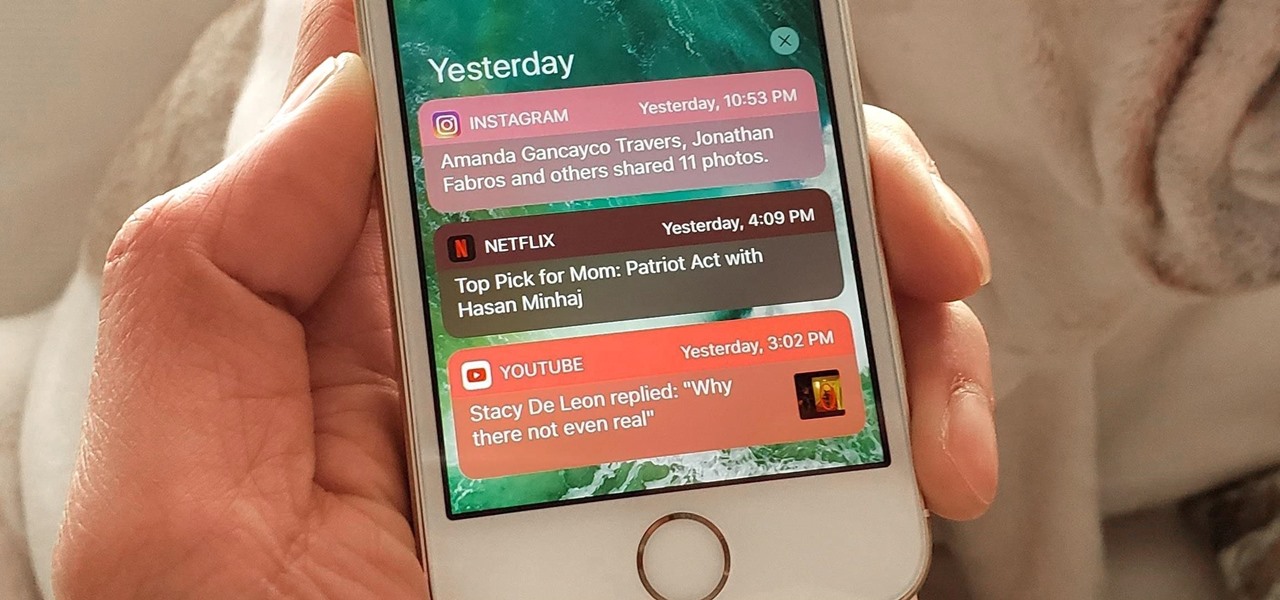
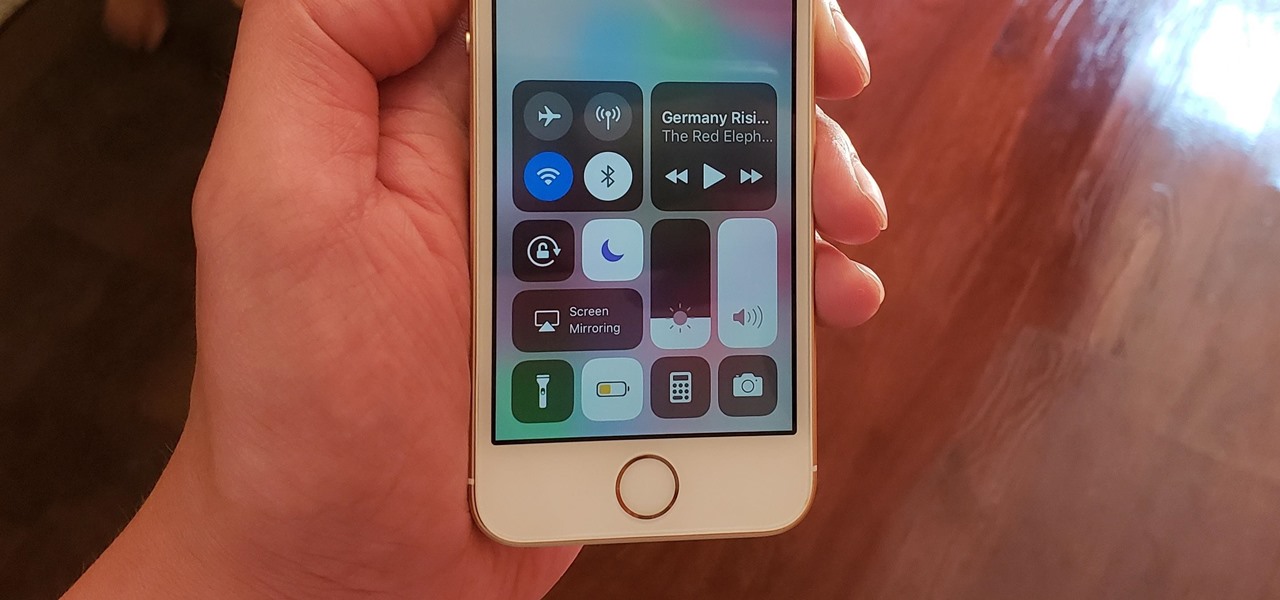
It's easy to take your iPhone's Notification Center for granted. As useful as it is for viewing important alerts, reminders, and more, the feature is pretty drab when compared to the customizable Control Center, Accessibility Shortcuts, and others.

If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them over a Wi-Fi or Ethernet connection.

Here at Next Reality, our typical approach to all things augmented reality involves vision combined with remote control, either via a handheld device, gaze control, or hand/finger tracking.

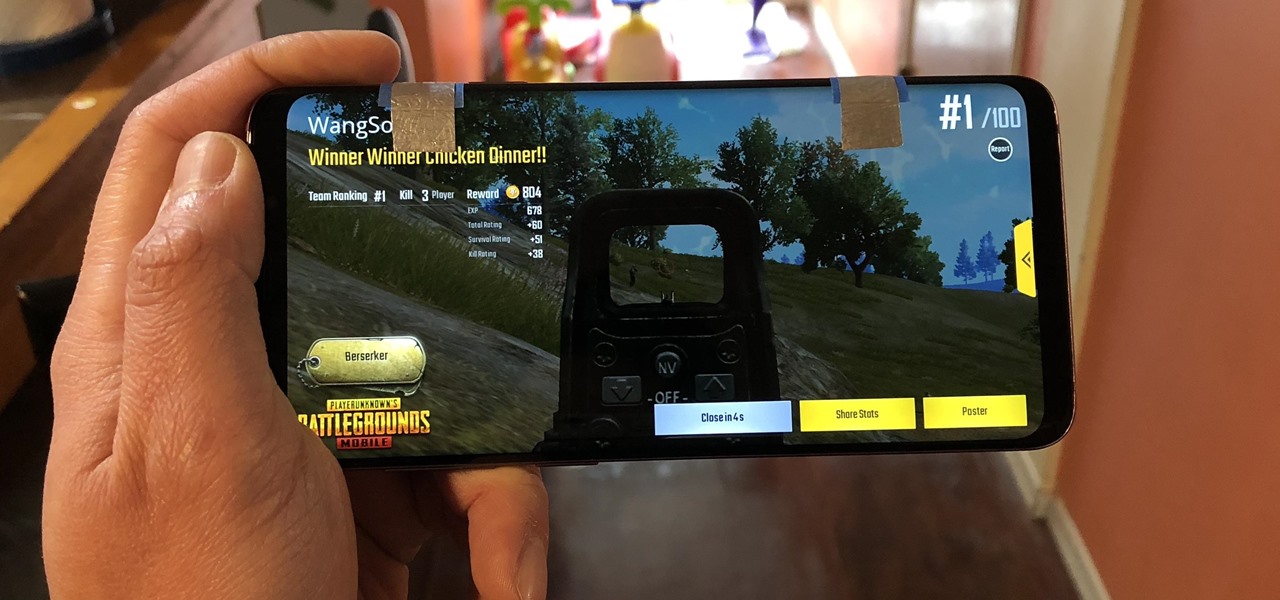
With ultra competitive games like Fortnite Battle Royale and PUBG taking the mobile world by storm, gamers are looking for ways to get a leg up on the competition. One of the biggest advantages you can give yourself is the ability to aim and shoot while on the move, but that's not exactly easy with a touchscreen.

Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't enough, you can steer your way around a network with a convenient tool called Ship, the script for everything IP.

It finally happened! In a world of "go big or go home," Magic Leap has finally done something other than tease us with vague promises and rendered video concepts. Although, other than actually showing us what the developer's kit will look like, it seems little more than a slightly different kind of a tease. To demystify this new product, we here at Next Reality decided to put together what we know about the hardware.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

To hack a Wi-Fi network using Kali Linux, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, so I've rounded up this list of 2019's best wireless network adapters for hacking on Kali Linux to get you started hacking both WEP and WPA Wi-Fi networks.

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

When anyone brings up Tasker, the first topic that always gets discussed is how powerful the Android automation app can be. But all of that power can be overwhelming for some people, so even if you're a Tasker pro, it's hard to share your awesome creations with friends that don't quite understand what's going on.

As the largest wireless service providers in the United States, AT&T and Verizon Wireless carry some serious clout. Sadly, they use some of this power to heavily modify the Android phones that they offer.

As we near the one-year anniversary of its release (and the inevitable unveiling of its successor), the Samsung Galaxy Note 3 remains a device that packs quite a punch when it comes to hardware. It boasts a 2.3Ghz CPU and was the first mobile phone ever to house 3GBs of RAM. Suffice it to say, it can handle any software you throw at it with no discernible lag. Even Samsung's notoriously bloated TouchWiz ROM seems lightning fast.

Third-party ROMs like CyanogenMod are the ultimate form of customization for softModders. Hard-working developers offer us alternate Android experiences to replace our often bloatware-riddled stock ROMs.

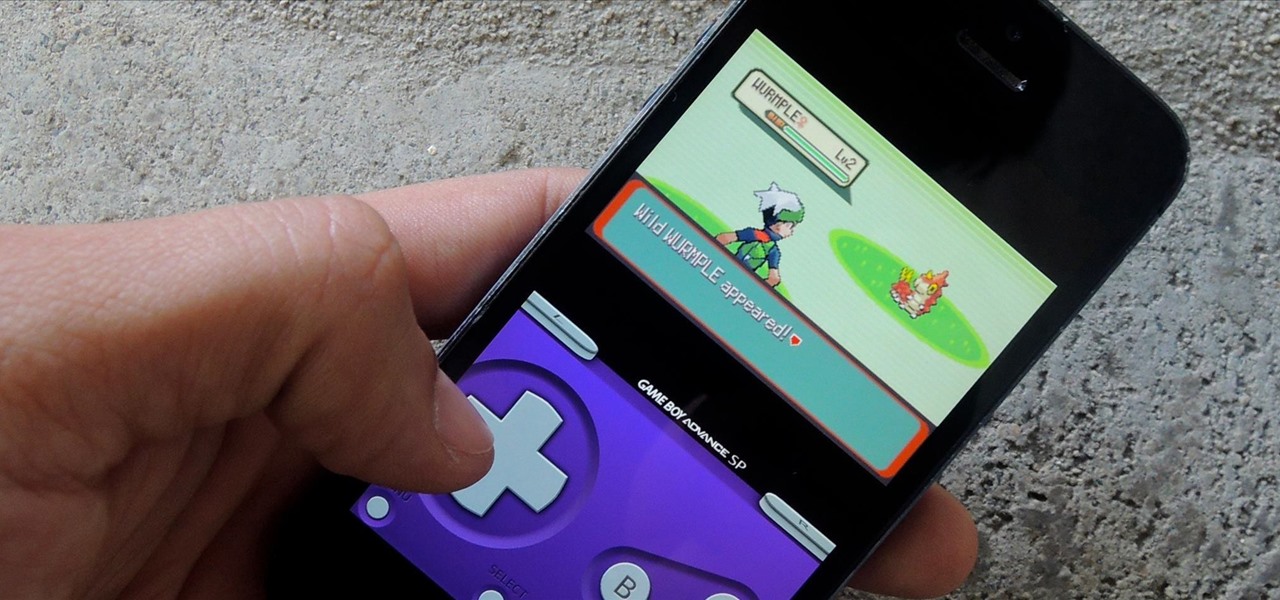
Normally, you'd have to jailbreak your iPad or iPhone to play any games that aren't available in the iOS App Store, like the now-extinct Flappy Bird game. But this isn't the case if you want to play some of your favorite old school Nintendo classics.

Unless you're a pretty avid home cook, you probably don't know a lot about sous vide. Sous vide is a low-temperature cooking method where food is cooked in vacuum-sealed plastic bags in a water bath for a prolonged period of time.

People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people are looking for ways around those hefty internet bills.

In this article, I'll be explaining the basics of how microcontrollers work, physically and virtually. First off, microcontrollers are no simple thing, so don't be discouraged if you find it mind-boggling! The world of microcontrollers is fascinating, engaging, and an awesome hobby; it never gets boring. I'll be focusing more on I/O and analog based microcontrollers, such as those running Arduino, and using Atmel chips as examples (these are most commonly available, and easy to program).

If the importance of augmented reality and VR hardware to Facebook's future wasn't already clear enough, a shake-up in the executive ranks at the company has made it as clear as smartglasses lenses.

The "Albums" tab in Photos is great for sorting through the images and videos on your iPhone since you can narrow things down by your recent pics and recordings, apps used, media types, people, places, and so on. If you never look at all of those folders, however, it could feel like an overwhelming cluttered mess. Plus, there may be some collections you don't want others to see.

Black Desert Mobile is one of the hottest new smartphone games around, but there seems to be something missing in the frame rate department. Gamers quickly noticed many Android phones are stuck on a 30 FPS cap when it comes to performance. It's not that the phones are too weak to handle higher frame rates, but that there is a particular list of approved devices that can achieve this.

With Microsoft taking direct aim at enterprises for its HoloLens 2 with a $3,500 price tag, one startup is betting that business will be willing to pony up for glasses-free 3D displays as well.

Face ID does an excellent job with keeping your iPhone safe, boasting a million-to-one odds against unauthorized access when compared to Touch ID, which is 20 times less secure. However, it's far from being truly hands-free, as you still need to swipe up the lock screen once it detects your face to access apps. But if you have a jailbroken iPhone X, this issue can easily be remedied.

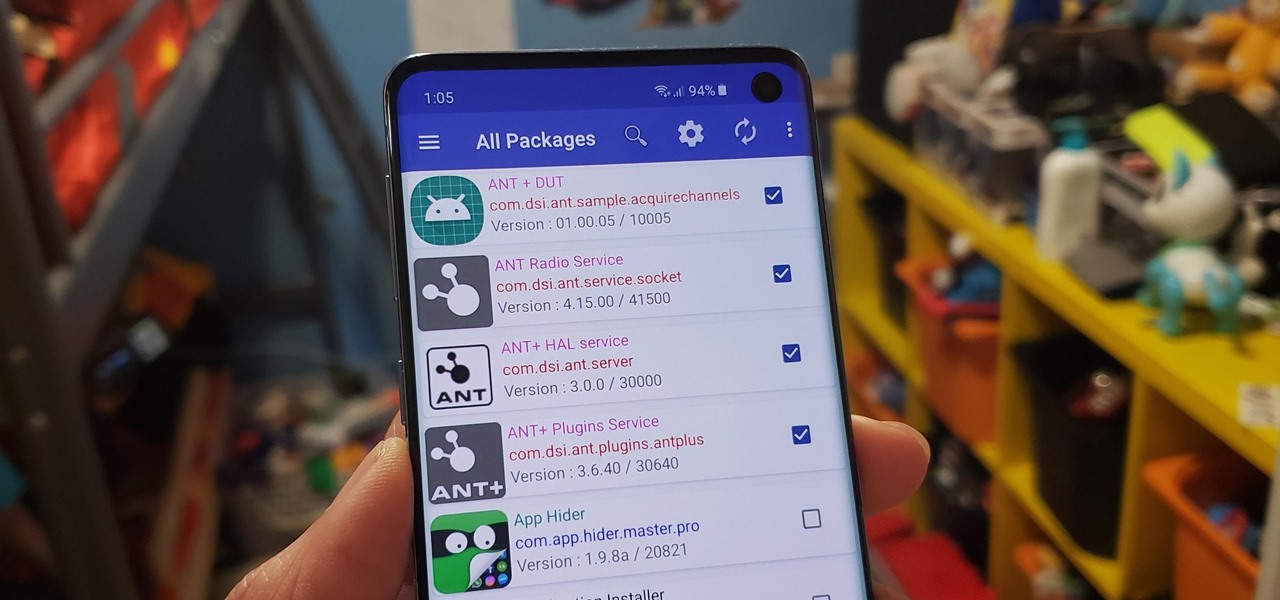
Bloatware remains one of the biggest problems with Android, especially when tied to a carrier. Removing bloatware usually requires you to take extreme measures like rooting. Unfortunately, the Galaxy S10 falls under this annoying umbrella, but there's an easy workaround.

Tapping on your iPhone's display to pick up an incoming call can be annoying when your hands are wet or dirty. It might even fail to register and cause you to miss your call. If you have a jailbroken iPhone, however, you can get rid of this problem entirely, thanks to a free tweak that lets you instantly pick up calls without having to interact with your phone's screen.

After years of user complaints, Samsung is finally letting us remap the Bixby button without the need of a third-party app. The new feature requires One UI a simple app update to Bixby, but there's one major downside: Samsung won't let you remap the button to open other digital assistants like Amazon Echo, Microsoft Cortana, and Google Assistant. Luckily, there's an easy workaround.

The iPhone's notification system has drastically improved over the years, but it could still use some work. The notifications, while useful, are all monochrome, making it hard to distinguish which app posted each alert, and that's not even mentioning the drab overall look. This is where jailbreak tweaks can come in handy.

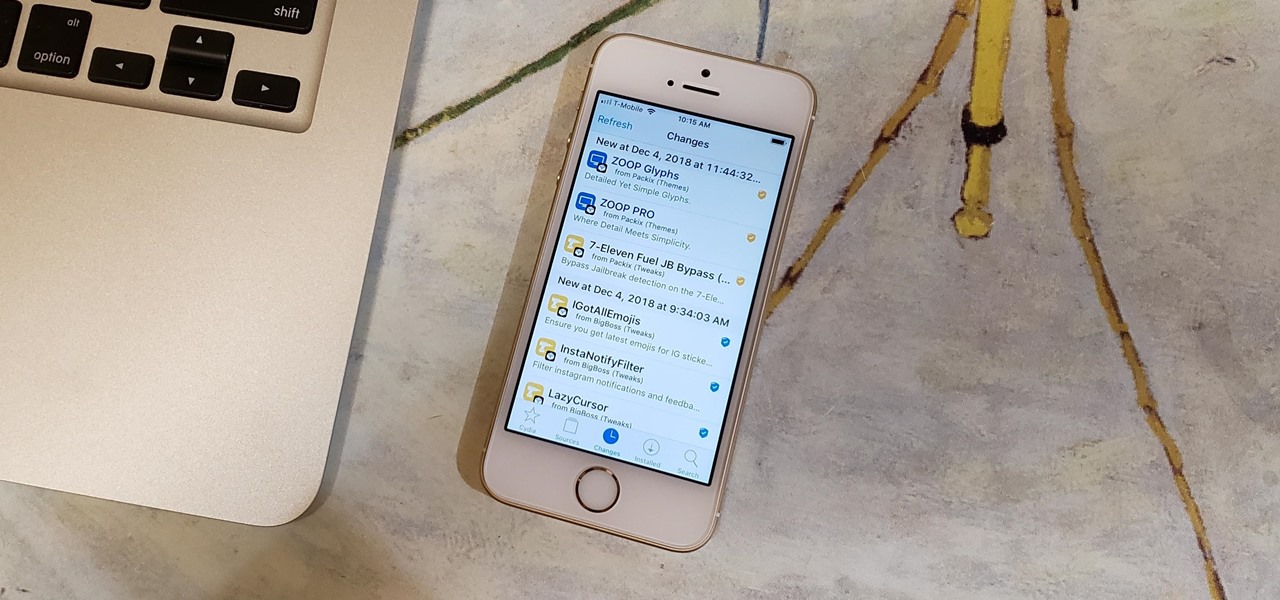
Apple has done a fantastic job of instantly patching iOS exploits through constant firmware updates to keep hackers at bay. Because of this, jailbreaking has largely been pushed to the fringes, resulting in a myriad of tweaks being abandoned by developers which, in turn, have been rendered incompatible with later jailbroken versions of iOS.

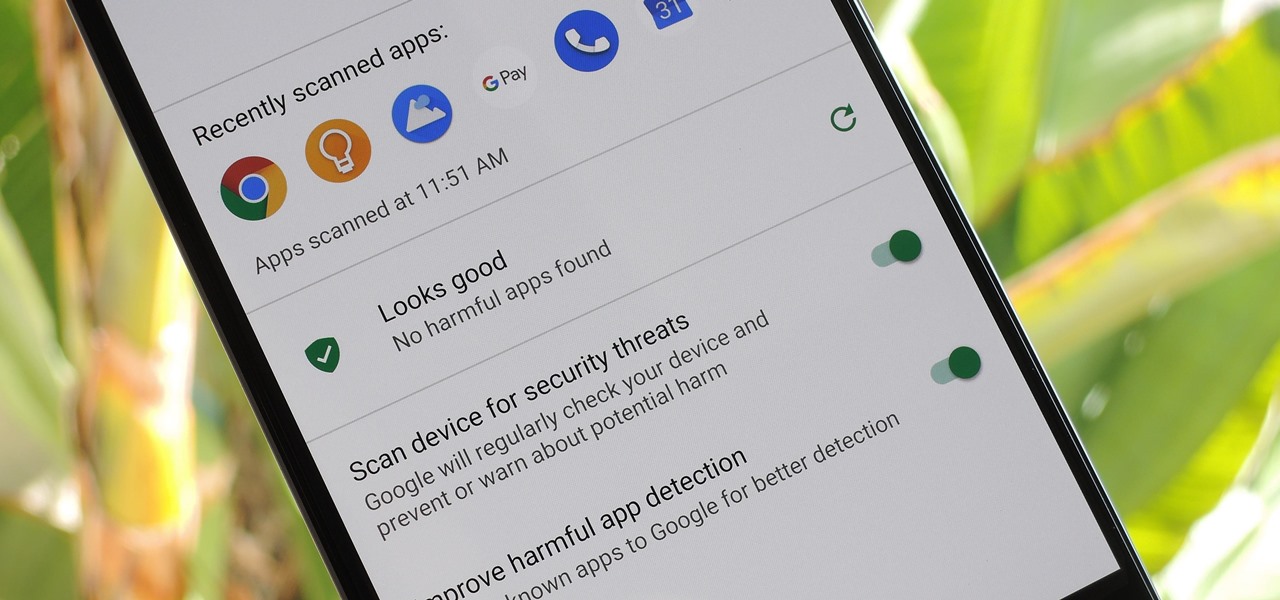
According to Google's new Android ecosystem transparency report, you're eleven times more likely to be infected by malware if you're running Android Lollipop (5.0) as opposed to Android Pie (9). The same report shows that if you sideload apps, you're almost seven times more likely to be infected than if you stick to Google Play as your app source. All of the data provided in the report is quite interesting, but there's a clear pattern among malware-infected users.

The Daily Prophet, the enchanted newspaper from Harry Potter lore, is no longer the sole source for magical moving printed photos.

Low Power Mode can go a long way in preserving your iPhone's battery life in a pinch. It can be set manually or appear as an option once your battery levels dip to 20 and 10 percent. If you have a jailbroken device, you can take Low Power Mode a step further by having it automatically turn on whenever using Do Not Disturb.

Whether you're in high school or college, you no doubt will have your iPhone in your pocket all day long. To make your iPhone last the whole time and even help you out with your studies, these are the accessories you'll want to get your hands on.