As the Insider Preview builds of Windows 10 progressed, certain features were removed as new ones joined the fray. Some came back, while others disappeared, seemingly for good. One feature that seems to have been removed are the colored title bars on app windows.
For those unwilling to wait until the Fall for the official release of Apple's latest Mac OS X, El Capitan, you can sign up for the public beta today and get it sometime this summer. If that's still not soon enough for you, there is a way to get it on your Mac right now.
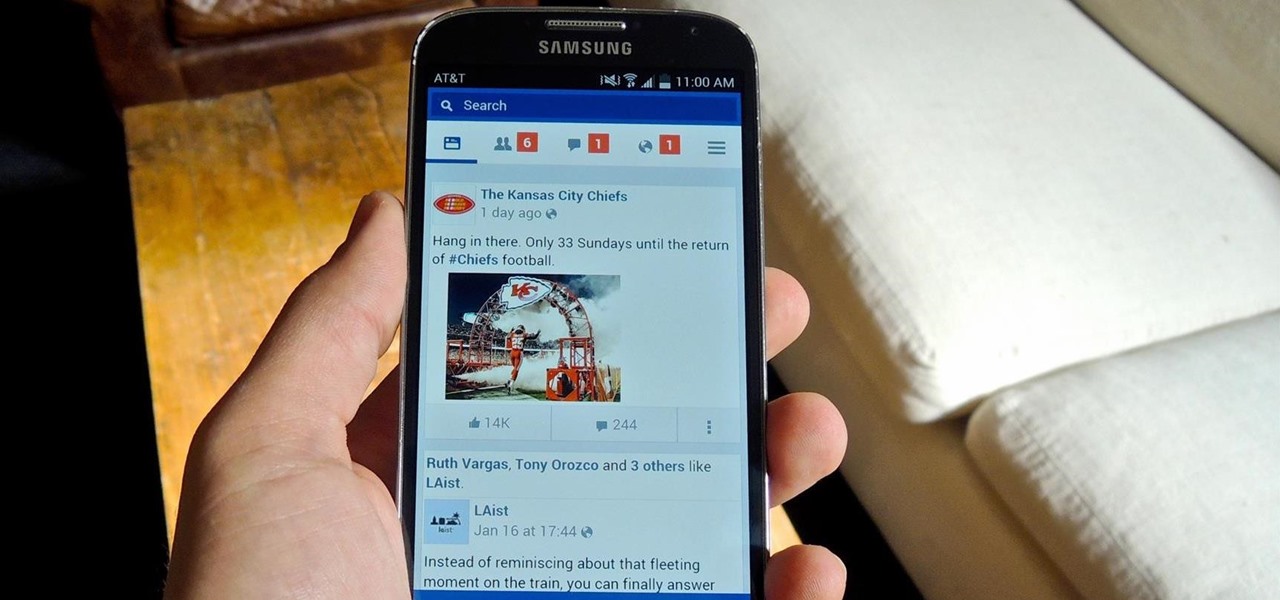
As one of the most frequently used and popular applications available, Facebook is now attempting to be a little more considerate for those Android users that don't have a bleeding-edge device or fast data connections.

Video: . Extraterrestrial life is life that does not originate from Earth. It is also called alien life, or, if it is a sentient and/or relatively complex individual, an "extraterrestrial" or "alien" (or, to avoid confusion with the legal sense of "alien," a "space alien"). These as yet hypothetical forms of life range from simple bacteria-like organisms to beings far more complex than humans. The possibility that viruses might exist extraterrestrially has also been proposed.
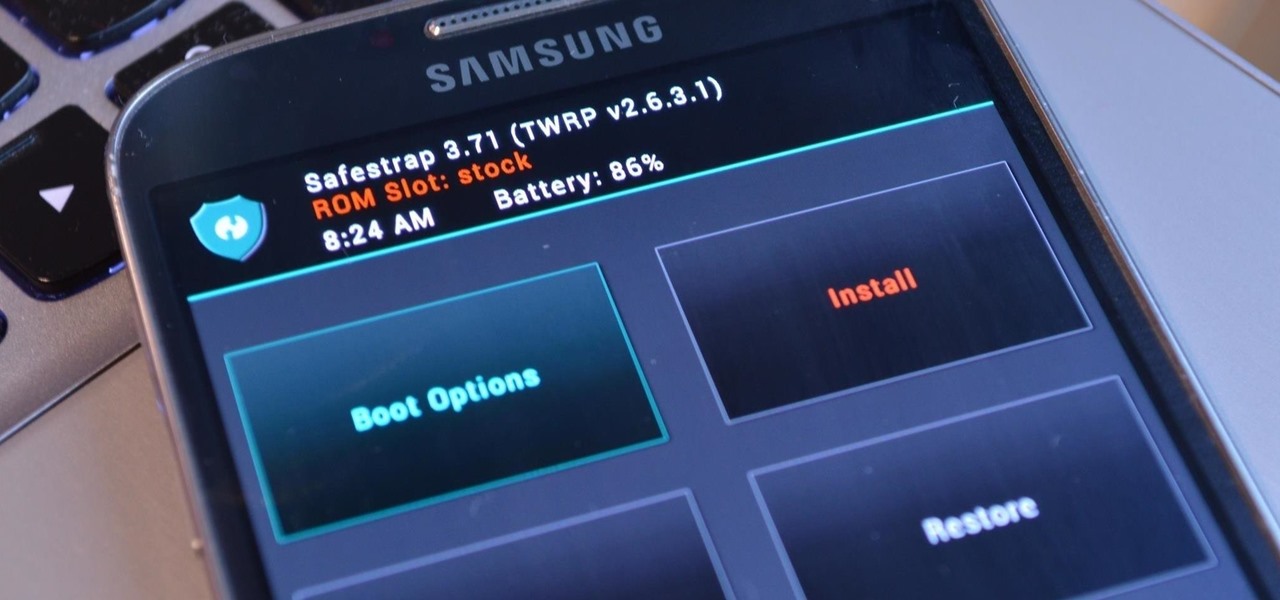
Third-party ROMs like CyanogenMod are the ultimate form of customization for softModders. Hard-working developers offer us alternate Android experiences to replace our often bloatware-riddled stock ROMs.

If you watched a YouTube video on your Android device today, you may may noticed something just a little different. If you haven't, go check out the app in your drawer or homepage. Google today pushed out an update to their YouTube app, but by all accounts, it was never meant to hit the public. This is labeled a dogfood build, which is a term used to describe products going through in-house testing, in effect "eating their own dogfood".

Closing apps in iOS 6 was different that what is now in iOS 7. Shown in the video below is the old clumsy way of closing apps on the old iPads.

Via Twitter, HTC, the Taiwanese device manufacturer, announced today that their barely 18 month old flagship phones will not see official updates for anything past Jellybean. HTC went on to elaborate, saying:

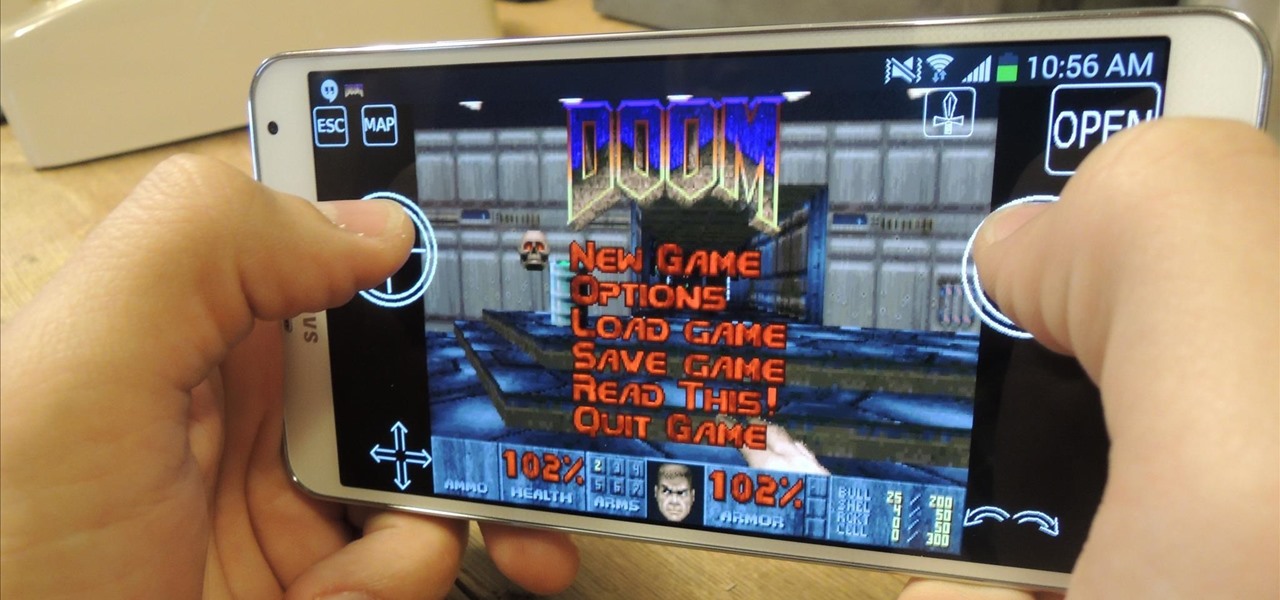
In the wake of its 20th anniversary, the folks over at Eltechs have released Original DOOM, a full shareware version of the revolutionary first-person shooter DOOM for Android, available for free on the Google Play Store. It's unmodded and unaltered from the original FPS classic.

This is how to build a wine rack out of pallet wood. I was tossing around some wine rack ideas and decided that pallet wood, or reclaimed wood, is the perfect choice for a rustic wine rack. All you need for this project is an old pallet (for me a hardwood one is my choice). A pallet that has seen some wear is preferable so as to achieve that rustic look.

When subjects are asked to watch a movie and not display emotions (say, a comedy without laughing, or a tearjerker without crying), they evidently use up glucose in particular areas of their brain in a way that subjects who are free to react however they want do not.

Want to play your video collection on any media extender, console or AppleTV? Step one is to get your movies off of the DVDs and onto your hard drive! If you're like most people you probably have a huge library of DVDs that you've bought and collected over the years. Unfortunately, it's an inconvenient format if you want to playback all that content anywhere around the house. So, learn how to rip and encode that stack of DVDs into a format that you can play on your Windows Media Extender, set...

Create lasting memories by organizing a well-planned family reunion. This video will show you how to organize a family reunion.

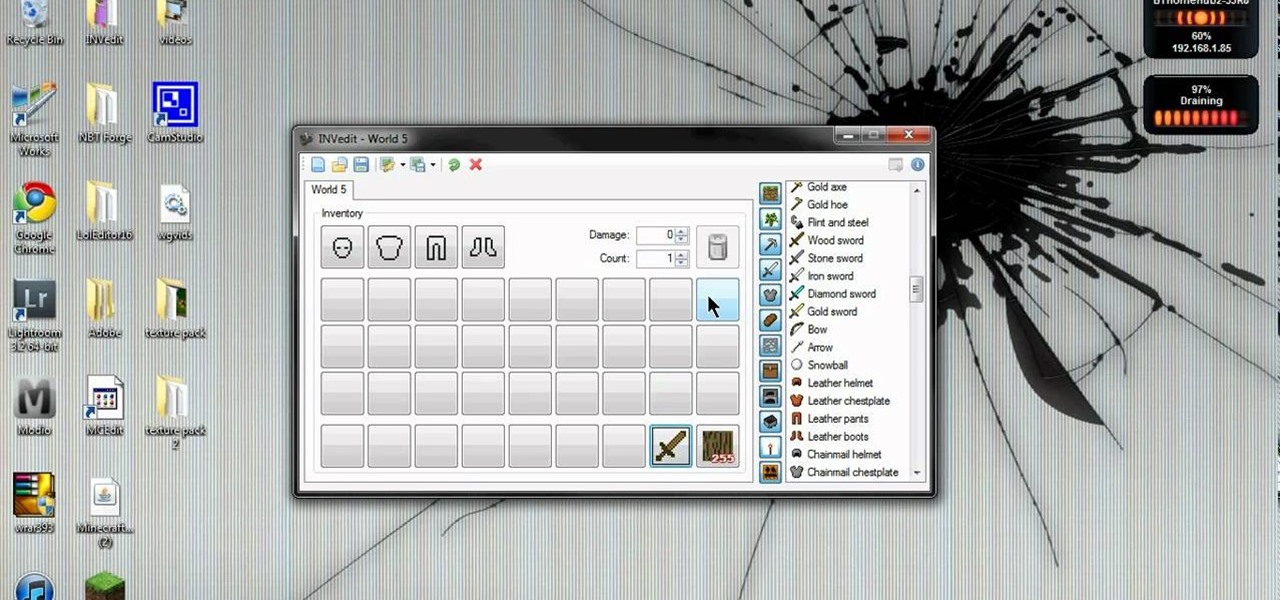
INVedit is an inventory modification program that you can use to hack into your character's inventory when playing Minecraft. Give yourself more items of one time, unlimited resources or whatever else you feel like. Fill a whole island with diamonds or TNT!

Start with just a little bit of money and the multiply it into a vast fortune! All you need is the most current version of the free game hacking software, Cheat Engine! Then open your game in Firefox and follow the tutorial!

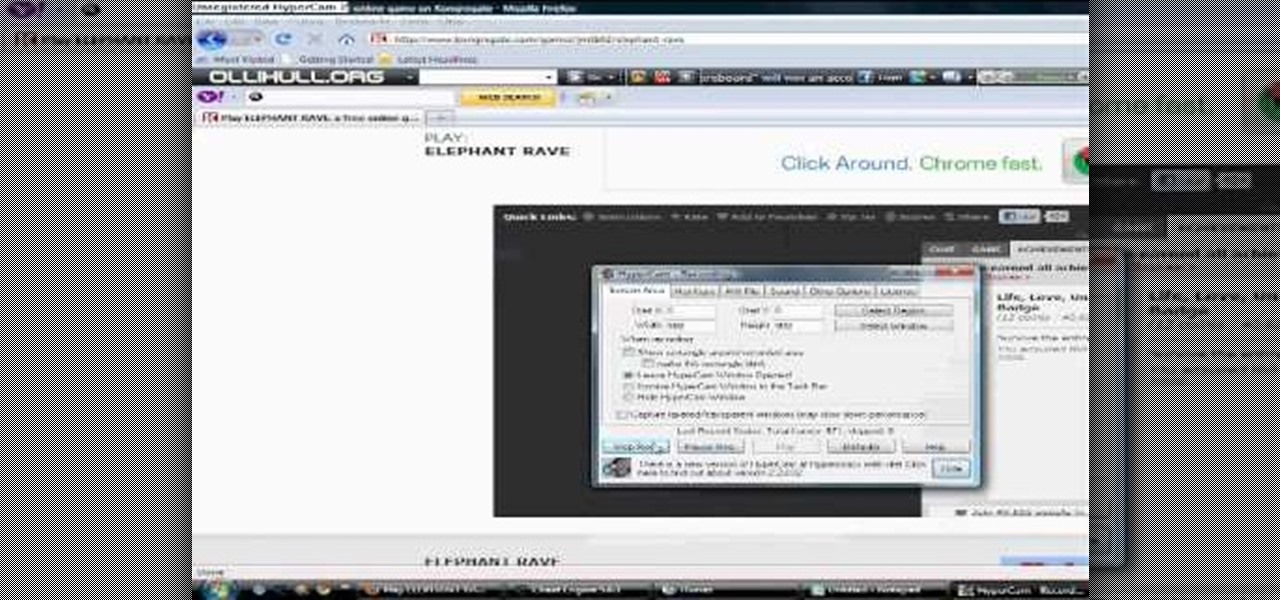
You'll need to make sure that your version of Cheat Engine is at least 5.6.1 or higher. If it is, then you can follow this tutorial, which shows you how to hack the game Elephant Rave and get resources for free!

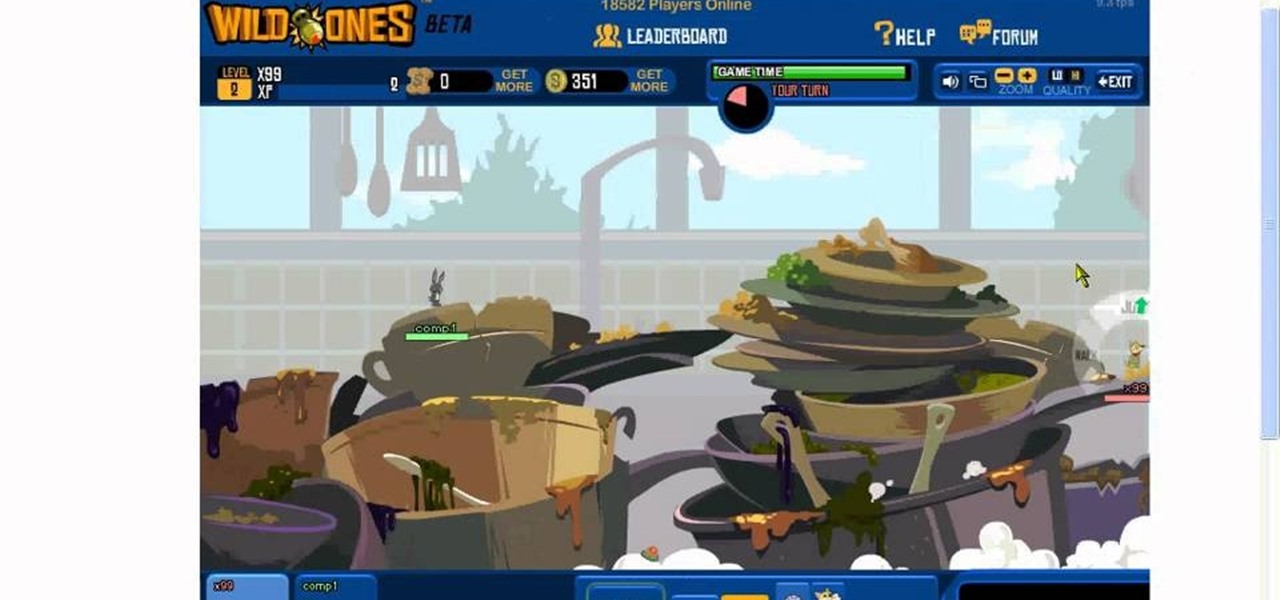
Want to give yourself extra points or resources in the online game Wild Ones? All your friends will be asking you how you passed them up so quickly! Make sure you have the most recent version of Cheat Engine downloaded, first!

Learn how you can get free online education: see this must-have, massive list of resources.

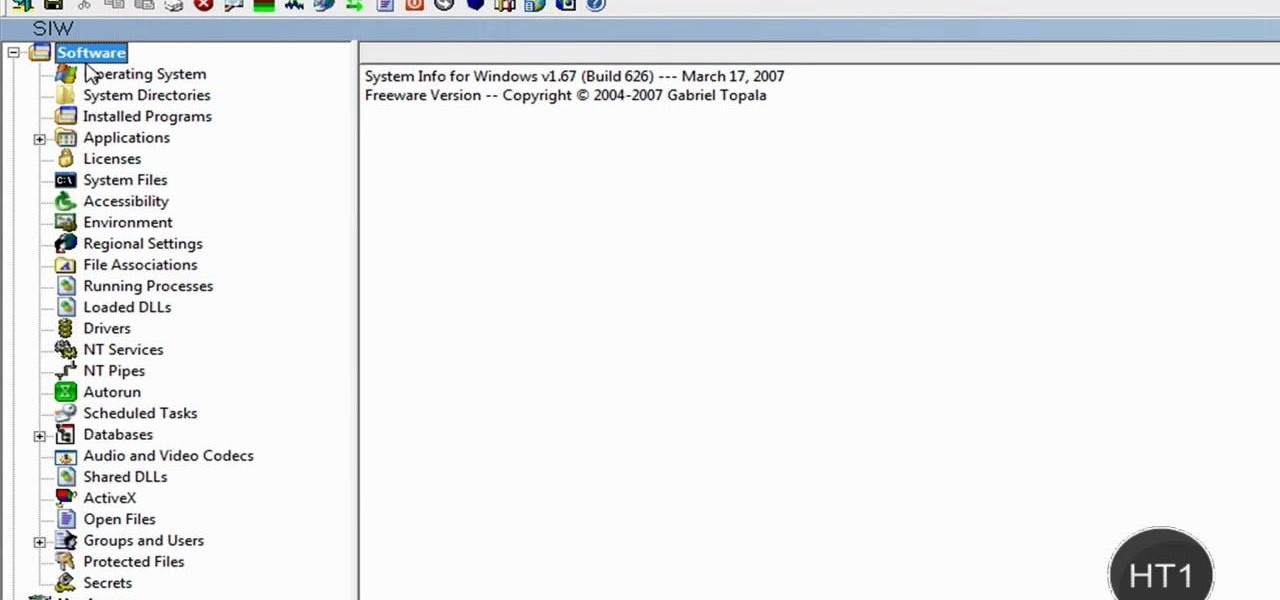
How to find out information / details about your computer? To find out the information about your computer, you need to download software from the website PC World. The following are the steps to download the software:

In this article, I'll be explaining the basics of how microcontrollers work, physically and virtually. First off, microcontrollers are no simple thing, so don't be discouraged if you find it mind-boggling! The world of microcontrollers is fascinating, engaging, and an awesome hobby; it never gets boring. I'll be focusing more on I/O and analog based microcontrollers, such as those running Arduino, and using Atmel chips as examples (these are most commonly available, and easy to program).

The "Albums" tab in Photos is great for sorting through the images and videos on your iPhone since you can narrow things down by your recent pics and recordings, apps used, media types, people, places, and so on. If you never look at all of those folders, however, it could feel like an overwhelming cluttered mess. Plus, there may be some collections you don't want others to see.

Black Desert Mobile is one of the hottest new smartphone games around, but there seems to be something missing in the frame rate department. Gamers quickly noticed many Android phones are stuck on a 30 FPS cap when it comes to performance. It's not that the phones are too weak to handle higher frame rates, but that there is a particular list of approved devices that can achieve this.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.

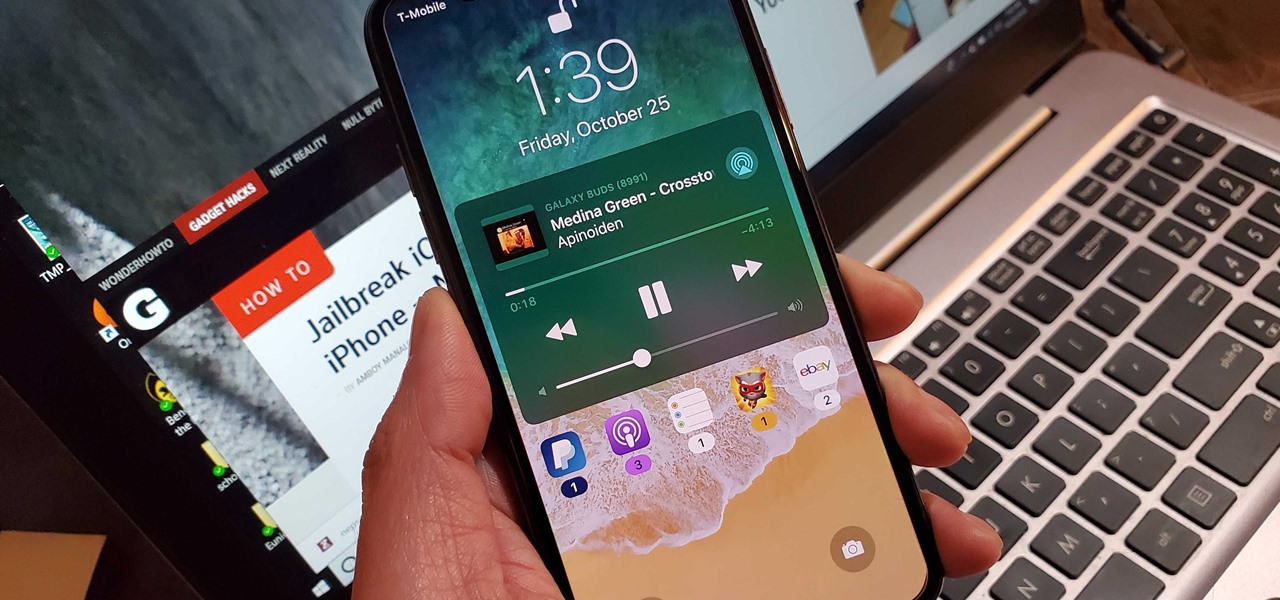
It's easy to take your iPhone's Notification Center for granted. As useful as it is for viewing important alerts, reminders, and more, the feature is pretty drab when compared to the customizable Control Center, Accessibility Shortcuts, and others.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

With Microsoft taking direct aim at enterprises for its HoloLens 2 with a $3,500 price tag, one startup is betting that business will be willing to pony up for glasses-free 3D displays as well.

Face ID does an excellent job with keeping your iPhone safe, boasting a million-to-one odds against unauthorized access when compared to Touch ID, which is 20 times less secure. However, it's far from being truly hands-free, as you still need to swipe up the lock screen once it detects your face to access apps. But if you have a jailbroken iPhone X, this issue can easily be remedied.

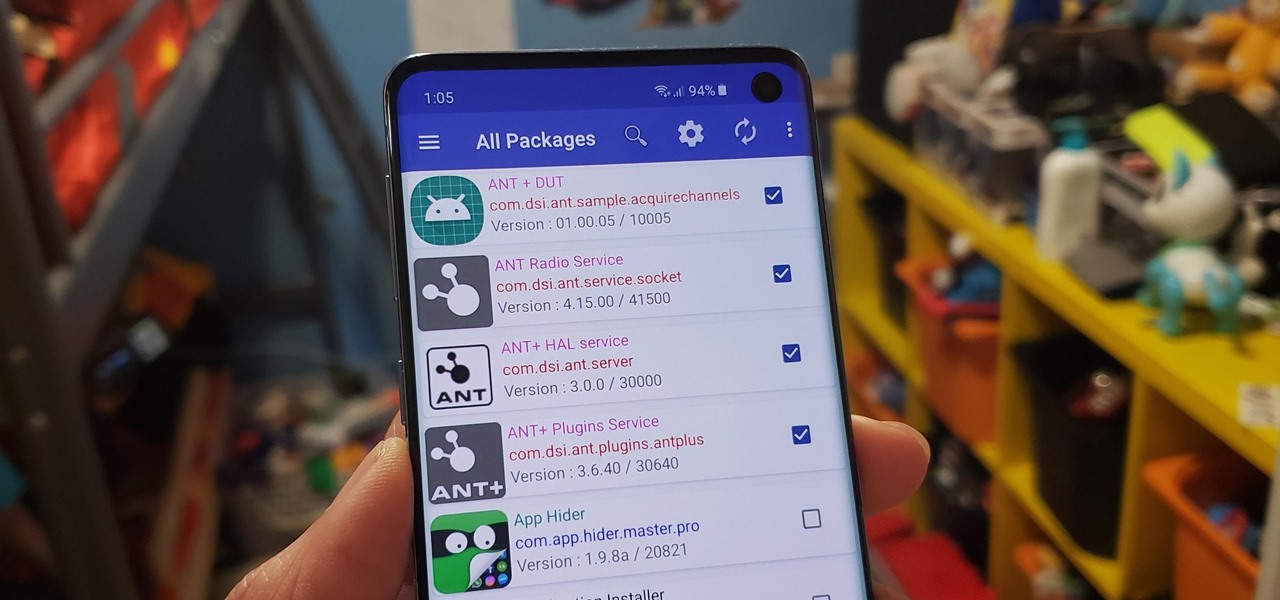
Bloatware remains one of the biggest problems with Android, especially when tied to a carrier. Removing bloatware usually requires you to take extreme measures like rooting. Unfortunately, the Galaxy S10 falls under this annoying umbrella, but there's an easy workaround.

Tapping on your iPhone's display to pick up an incoming call can be annoying when your hands are wet or dirty. It might even fail to register and cause you to miss your call. If you have a jailbroken iPhone, however, you can get rid of this problem entirely, thanks to a free tweak that lets you instantly pick up calls without having to interact with your phone's screen.

After years of user complaints, Samsung is finally letting us remap the Bixby button without the need of a third-party app. The new feature requires One UI a simple app update to Bixby, but there's one major downside: Samsung won't let you remap the button to open other digital assistants like Amazon Echo, Microsoft Cortana, and Google Assistant. Luckily, there's an easy workaround.

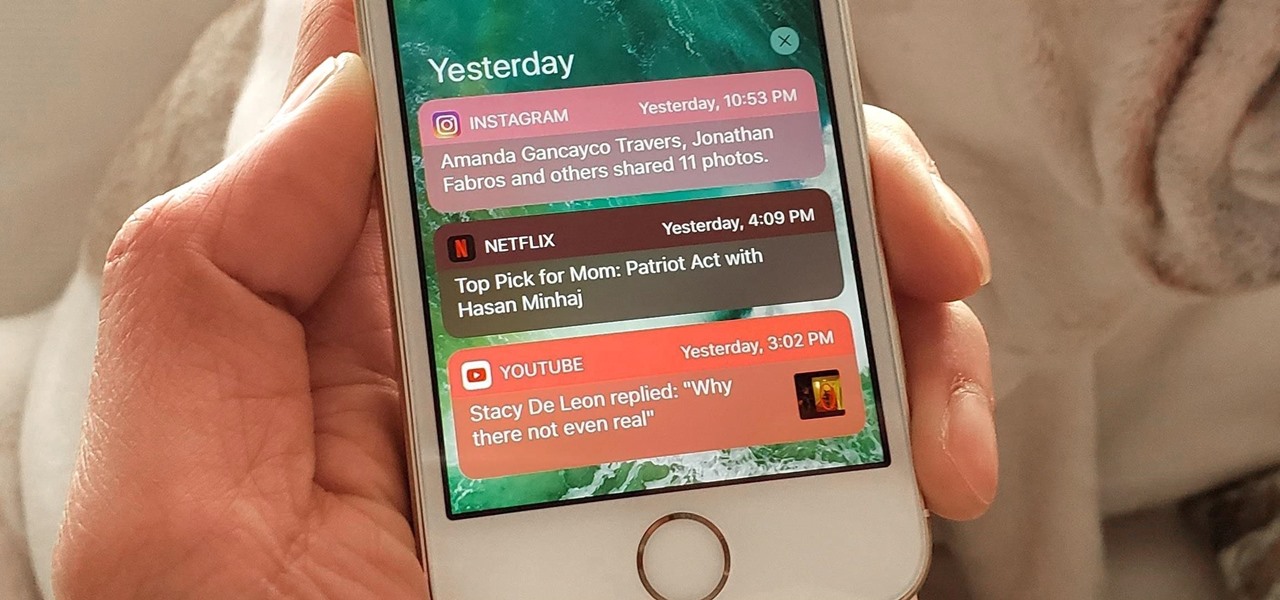
The iPhone's notification system has drastically improved over the years, but it could still use some work. The notifications, while useful, are all monochrome, making it hard to distinguish which app posted each alert, and that's not even mentioning the drab overall look. This is where jailbreak tweaks can come in handy.

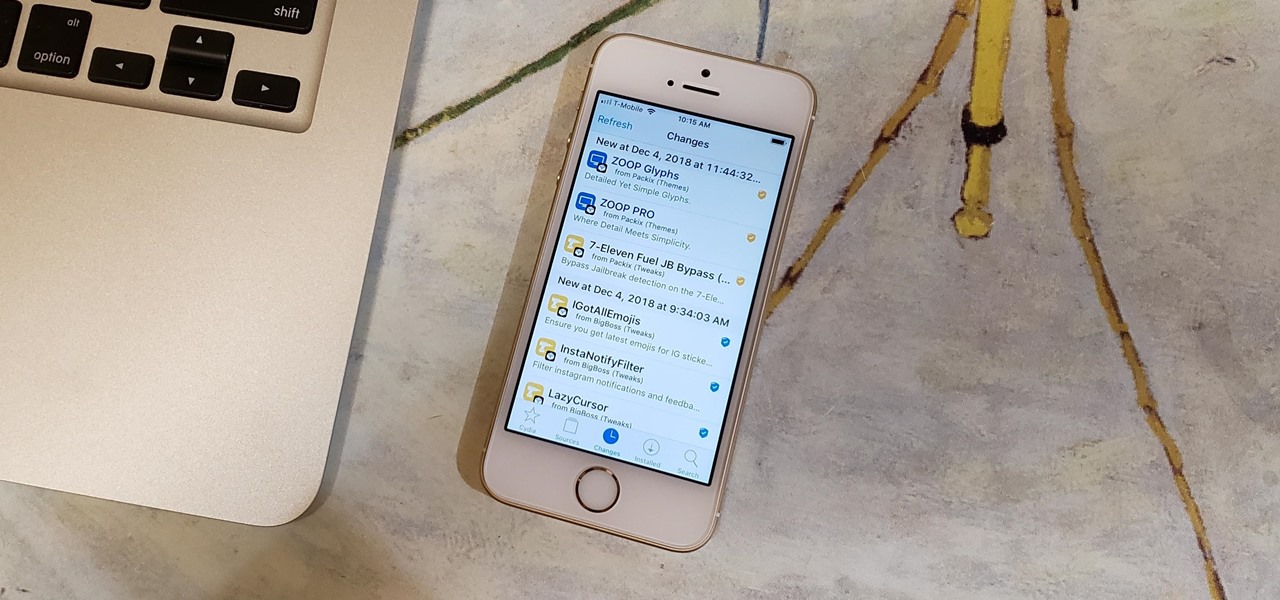
Apple has done a fantastic job of instantly patching iOS exploits through constant firmware updates to keep hackers at bay. Because of this, jailbreaking has largely been pushed to the fringes, resulting in a myriad of tweaks being abandoned by developers which, in turn, have been rendered incompatible with later jailbroken versions of iOS.

To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purchasing will work for Wi-Fi hacking.

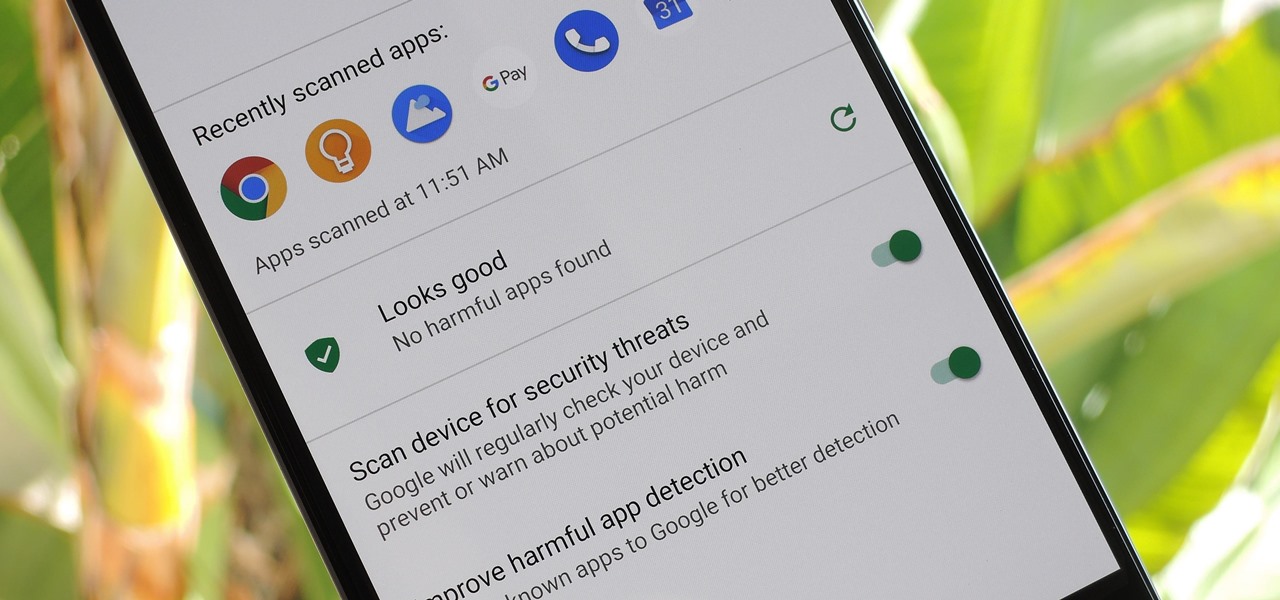
According to Google's new Android ecosystem transparency report, you're eleven times more likely to be infected by malware if you're running Android Lollipop (5.0) as opposed to Android Pie (9). The same report shows that if you sideload apps, you're almost seven times more likely to be infected than if you stick to Google Play as your app source. All of the data provided in the report is quite interesting, but there's a clear pattern among malware-infected users.

The Daily Prophet, the enchanted newspaper from Harry Potter lore, is no longer the sole source for magical moving printed photos.

Low Power Mode can go a long way in preserving your iPhone's battery life in a pinch. It can be set manually or appear as an option once your battery levels dip to 20 and 10 percent. If you have a jailbroken device, you can take Low Power Mode a step further by having it automatically turn on whenever using Do Not Disturb.

This time last year, computer vision company uSens introduced a stereo camera module capable of hand tracking. Now, uSens can achieve the same thing with just a smartphone's camera.

China-based virtual reality headset maker ANTVR has decided to enter the augmented reality space, and to do so it's launching its headset on Kickstarter. The company claims that its new Mix AR device has a field of view that surpasses the Meta 2, the HoloLens, and others within a smaller form factor and at a fraction of the price. But there's a catch.

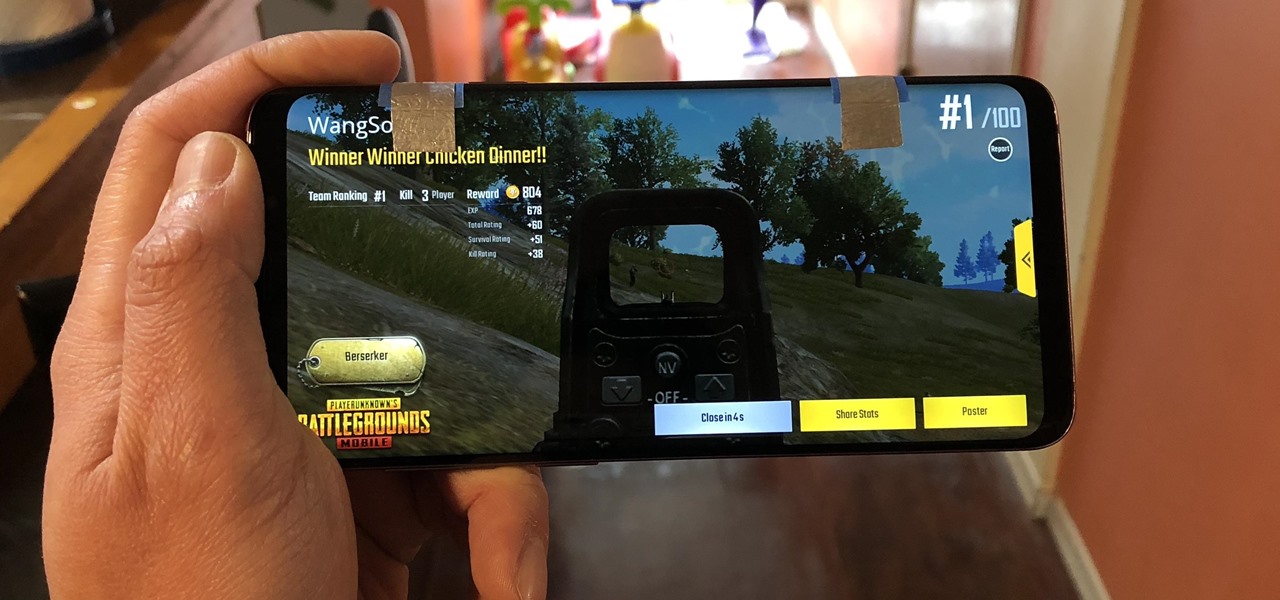
With ultra competitive games like Fortnite Battle Royale and PUBG taking the mobile world by storm, gamers are looking for ways to get a leg up on the competition. One of the biggest advantages you can give yourself is the ability to aim and shoot while on the move, but that's not exactly easy with a touchscreen.