
How To: Conduct Recon on a Web Target with Python Tools
Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.


Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

If you have a modern iPhone, you have an excellent video recorder at your disposal. Every iPhone since the 6S has the ability to shoot in 4K resolution, and each new iteration has brought new capabilities to the table. But even the best mobile shooter can use a little extra help. That's where these video recording apps come into play, to ensure the footage you capture is as good as can be.

There have been concerns with how much personal information Google tracks and all the things they know about us. Of course, that's what makes Google services so useful, they can use that information to cater to each of us individually. So yes, it serves a purpose, but it's not great for personal data security.

If you're familiar with jailbreaking, you're well aware of the fragmented nature of downloading tweaks. Unlike the iOS App Store, which contains about two million apps of varying categories, installing jailbroken packages often requires you to first install a separate repo into either Cydia or its replacement Sileo, as many of these tweaks aren't available outright.

As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing man-in-the-middle attacks.

Google's Allo is still a work in progress, but the innovations to the chat and messaging app just keep on coming. The latest update rolling out now includes chat backups and a group incognito feature that we're very excited about.

Its a voice modulator which can be used to change your voice instantaneously so you can disguise and pull pranks etc.
When you delete a file, Android doesn't actually remove it from your storage drive—instead, it simply marks that space as empty and pretends the file doesn't exist anymore. But deep down inside, the file that you originally wrote to that location is still physically there, at least until you randomly happen to save another file on top of that same spot.
Chrome's Incognito Mode is a great feature for folks that don't want their browsing history tracked. When it's enabled, Incognito Mode makes sure that all cookies and cache that are saved while you're browsing are deleted as soon as you leave a webpage.

Did you know that your face shows others how much alcohol you drink? Whether you've never had a sip of booze with those around you or you're known as the party animal of the group, the genes that shape your appearance also show others just how much you enjoy liquor. Pinpointing the big drinker in any setting is easy to determine: you just need to make eye contact.

How much privacy are you getting as an AT&T customer? With the recent leaks confirming the National Security Agency's surveillance on AT&T users, and the ongoing trial of Jewel v. NSA, it seems not much at all.
There is nothing worse than losing valuable information or programs on your computer. And if you've ever accidentally deleted a file or document, you know how agonizing that entire process can be.

Got a Samsung Galaxy Note 2 phablet? Sure, it has its problems like any other mobile device, but it's still one of the hottest phablets on the market right now, because, well... it's awesome, right?

You can easily set up your devices in studio one. Run the studio one. You should now on the start page of the studio one. There you can see the recent files, news feed etc. Now studio one automatically select an audio device
In this video, viewers learn how to install Wiiflow. Viewers will need to install cIOS 249 and 222 / 223. Wiiflow is USB Loader that you can use on a Wii that have modified or hacked. Wiiflow enables you to play your "legal ISO backup" by using any USB storage device like a thumb drive or a more substantial external hard drive. This video demonstrates how to do this in a way that is easy to follow.

If iTunes ever crashes, you're in for a world of pain and frustration. How do you get all of your digital music back? If you didn't back it up on an external hard drive, then you might be sweating it, but wait… do you have an Apple iPod or iPhone? There may be hope for you yet.

The iPhone doesn't stop at last year's excellent iPhone 12 lineup. Apple's been developing its iPhone 13 models for a while now, and there are a lot of rumors already with eight or nine months still to go until a release. This year, we're expecting four new models with similar sizes and features to 2020's offerings. If you want to know what makes the 2021 iPhones so different, we've got answers.

Apple's iOS 13 has been available for beta testing since June, and the stable release pushed out to everyone on Thursday, Sept. 19. To help you make the most out of iOS 13 for iPhone, we've rounded up everything you'll want to know, whether a colossal feature, small settings change, interface update, or hidden improvement.

Penetration testing, or pentesting, is the process of probing a network or system by simulating an attack, which is used to find vulnerabilities that could be exploited by a malicious actor. The main goal of a pentest is to identify security holes and weaknesses so that the organization being tested can fix any potential issues. In a professional penetration test, there are six phases you should know.

When you don't have a steady cellular signal or immediate Wi-Fi access but need to communicate with others around you, you can set up an off-the-grid voice communications network using a Raspberry Pi and an Android app.

If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them over a Wi-Fi or Ethernet connection.

Here at Next Reality, our typical approach to all things augmented reality involves vision combined with remote control, either via a handheld device, gaze control, or hand/finger tracking.

It finally happened! In a world of "go big or go home," Magic Leap has finally done something other than tease us with vague promises and rendered video concepts. Although, other than actually showing us what the developer's kit will look like, it seems little more than a slightly different kind of a tease. To demystify this new product, we here at Next Reality decided to put together what we know about the hardware.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.
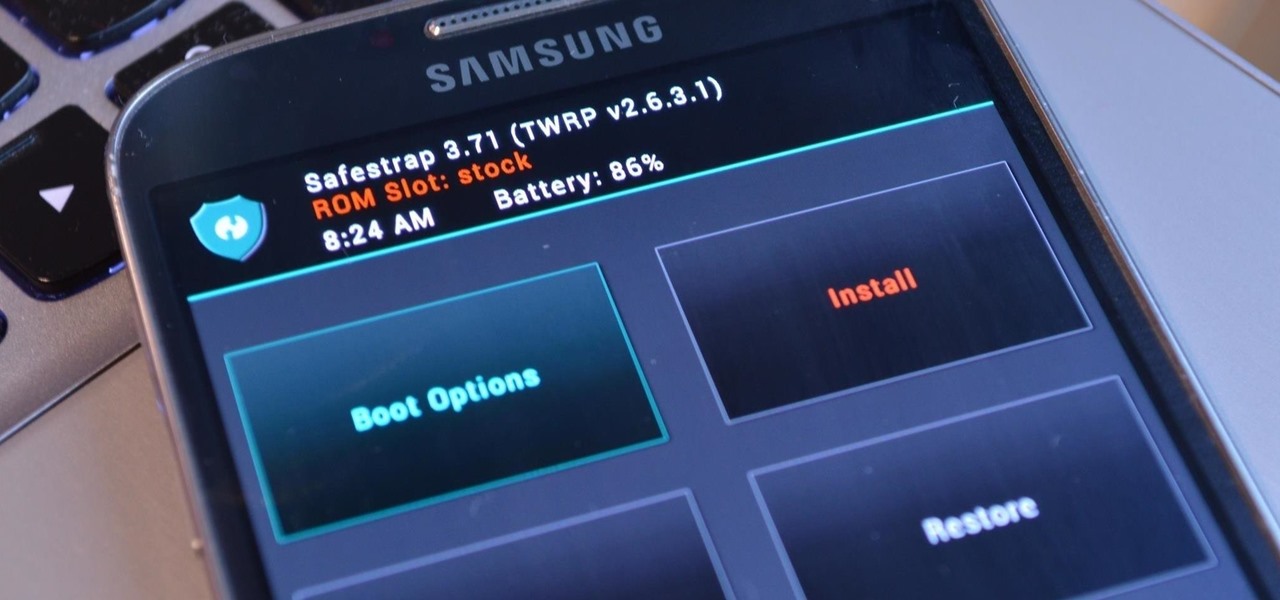
Third-party ROMs like CyanogenMod are the ultimate form of customization for softModders. Hard-working developers offer us alternate Android experiences to replace our often bloatware-riddled stock ROMs.

If you're in the market for a new smartphone and want nothing but the best of the best, now's the time to act. Some of the greatest phones money can buy are being released as we speak, while others are still in their prime and will continue to be for most of 2024. Whether you want an iPhone or Android, we've rounded up the best picks you have to choose from for top-of-the-line specs and advanced features.
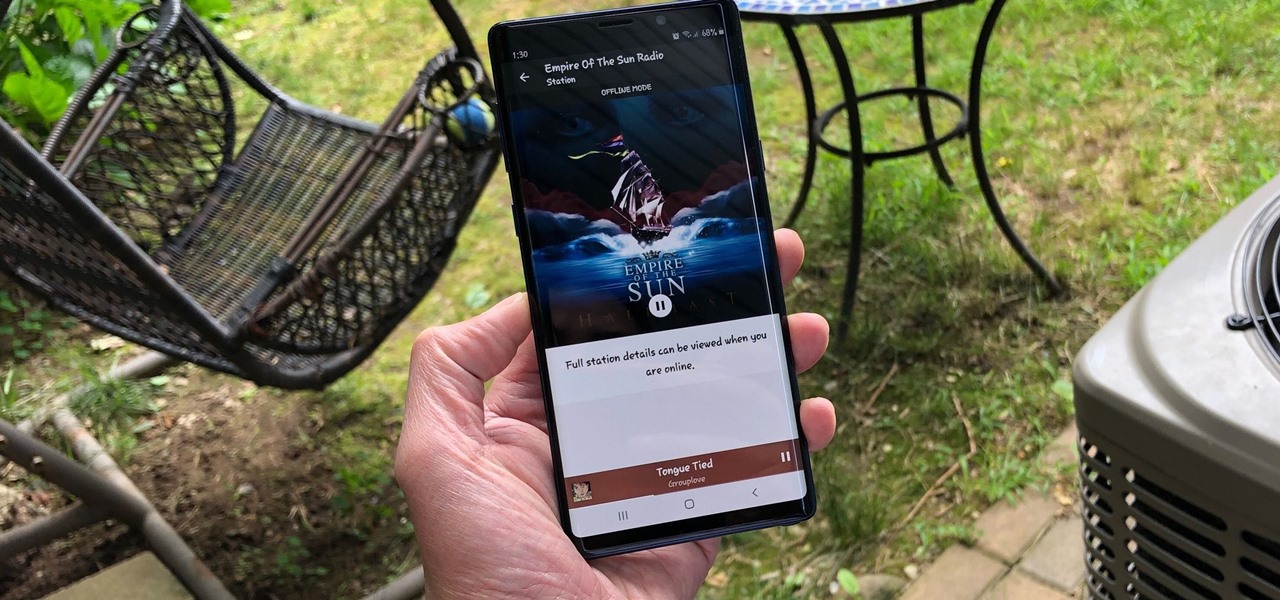
Tuning into a favorite station on Pandora has become part of a routine for many, and it's easy to see why. The app automatically plays songs tailored to your tastes to ensure a relatively hands-free experience. And if you're a subscriber, Pandora even has you covered in moments where there's poor cellular service by letting you keep listening to your go-to tracks uninterrupted.

Your Instagram feed is jam-packed with interesting and lively photos, videos, and stories that largely offset the iOS app's comparatively bland user interface. If the interface's dull colors have always bothered you, you can splash on some much-needed color to better reflect your personality and tastes.

Sileo is an ideal marketplace for developers to showcase apps, tweaks, and themes that Apple would never allow in the App Store. While a majority of these packages are free to try out, there are jailbreak apps that cost money for your iPhone. But actually paying for mods can be a bit tricky.

If waveguide display maker DigiLens has its way, enterprise businesses and consumers will soon be able to purchase smartglasses for less than $500 — as long as they can supply their own computing and battery power.

First, I want to give credit to the author where I first found how to do this: Astr0baby's Blog. This article was dated, so I took the script on his page and reworked it to make it work today. (I also included the way to make it hide the cmd line popup.) Requirements
Libraries is a cool new feature in Windows 7 that helps you find and manage all of your documents, music, pictures and videos in one location, no matter what location there in. This video from Microsoft outlines the usage of this new feature.
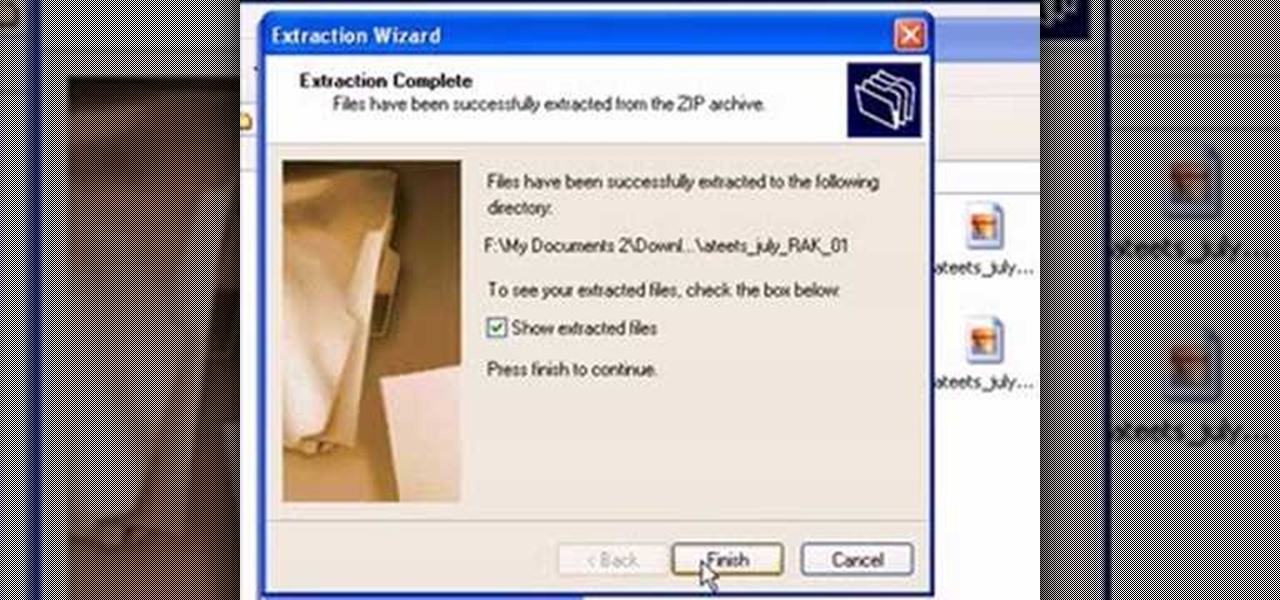
This video from scrapwow shows how to unzip a file in Microsoft Windows XP.Firstly, open Windows Explorer application and navigate the file you want to unzip. Once you've located the file, double click on it. A new window will open. Here you will have Extract all files option which you can choose from menu to the left.Clicking the button allows you to extract a single file or a zipped folder, containing a number of files. In this case Extraction Wizard will open, leading you through the extra...

Even if you're a master at the grill, dealing with the tank can be a little intimidating if you've never done it before. But there's really not much to worry about. Exchanging or refilling your gas grill tank is easy to do.

When I first bought my Western Digital Passport drive I had all intentions of putting hundreds of movies on it and plugging it into my USB enabled DVD player that's hooked up to my TV. Unfortunately, it didn't work. The drive draws power through the USB cable, and the LG DVD player I have doesn't supply enough. I thought that if I bought an external case with it's own power adapter, took the drive out of the Passport and put it in there, it might work. Nope. Didn't work either, it was still d...

There are some important new features in the Photos app on iOS 17 and iPadOS 17 that will streamline editing, give your pets more recognition, help you learn about the world you've captured, and even add a bit of fun to your day. There are even a few hidden tricks that may surprise you.

Many of the iPhone 15, 15 Plus, 15 Pro, and 15 Pro Max features were carried over from last year's models. Still, quite a few capabilities are exclusive to the 2023 lineup, and some may be worth the upgrade.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.