Now that iOS 7 has rolled out to the general public, with an overwhelming fit of mass hysteria, it's only custom for people to start bitching about battery drain—and I don't blame them. I was experiencing some rapid battery drain after first updating my iPhone 5, as well.

You probably know Lenovo from their low-cost Windows PCs here in the states, but something you may not be aware of is that they also make smartphones. Right now, their biggest market is in China, but a rumored merger with BlackBerry could make Lenovo a contender in North America, not to mention one of the biggest smartphone manufacturers in the world.

Although mowing is key to keeping your lawn healthy and good looking, it isn't anything worth jumping up and down for when it comes time to doing it. As it turned out, the first time I mowed my lawn wasn't nearly as fun or exciting as Hank Hill made it out to be. Maybe it was the beer.

Welcome back, my hacker novitiates! Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or service.

Welcome back my fellow army of hackers! Today we'll be hacking a website. Hacking is technically not the right word used here. It should be defacing! So we are going to deface a website...

Who am I? First let me introduce myself. I am Th3skYf0x, an -well lets call it

International, T-Mobile, and Verizon customers all share something in common—their carriers provide unlocked Wi-Fi tethering for free. Of course, you still pay for the data used, but they don't charge you extra simply for using your Samsung Galaxy S4 as a wireless hotspot.

You know that sinking feeling you get when know you've just done the unthinkable? It's the worst. Sending that ridiculous text message to the wrong number or posting a shameful tweet during a weekend bender.

We don't generally think of medicine as being very relevant to Steampunk, but it was a big part of Victorian science fiction. Notable examples that you may be familiar with would be Frankenstein and The Strange Case of Dr. Jekyll and Mr. Hyde.

The art of persuasion is a very crucial characteristic that anyone can learn, and it has countless benefits. Whether it's at work, home, or in social situations, the ability to be veritably persuasive can have an unheralded impact on your daily life.

We frequently associate plastics with the modern era, starting at around the 1950s with the prevalence of bakelite. However, for all of you "you can't use plastic in Steampunk" purists out there, I have bad news for you:

Craigslist is probably the greatest site ever created, and I'm just talking about it's classified section, both awesome and amazingly creepy. Seriously, spend 20 minutes scrolling through the personals and you'll never want to take your eyes off the screen. But I digress—Craigslist is also one of the most convenient places to buy and sell pretty much anything you can think of. I've used it to buy my bed, my old bike (which was stolen!), and my couch. And while Craigslist is great in many ways...

A common problem on bumper covers is that the tabs that attach the bumper to the car get broken. This is critical, as this is what secures and aligns the bumper cover. Many times, a broken tab is all that is wrong with the bumper cover. With the cost of these plastic parts $200 to $700, the replacement cost can break the bank.

Cross-dressing and gender-bending are nothing new, but the realm of Steampunk seems to be especially accepting of role-reversal in dress.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

Of all the places you'd think to check for bed bugs, I doubt that library books would be at the top of your list. As odd as it sounds, though, libraries and library books are some of the most common places for bed bug infestations. Libraries all over the country have reported bed bug problems this summer, and some have even had to temporarily close to take care of the problem. But before you vow to never set foot inside a library again, here's a little primer on how to check your books for be...

It can be incredibly frustrating to take closeup shots with an iPhone camera—or any smartphone camera for that matter. Even if your phone's camera is top of the line, you'll still get a fuzzy picture if you get to close to your subject.

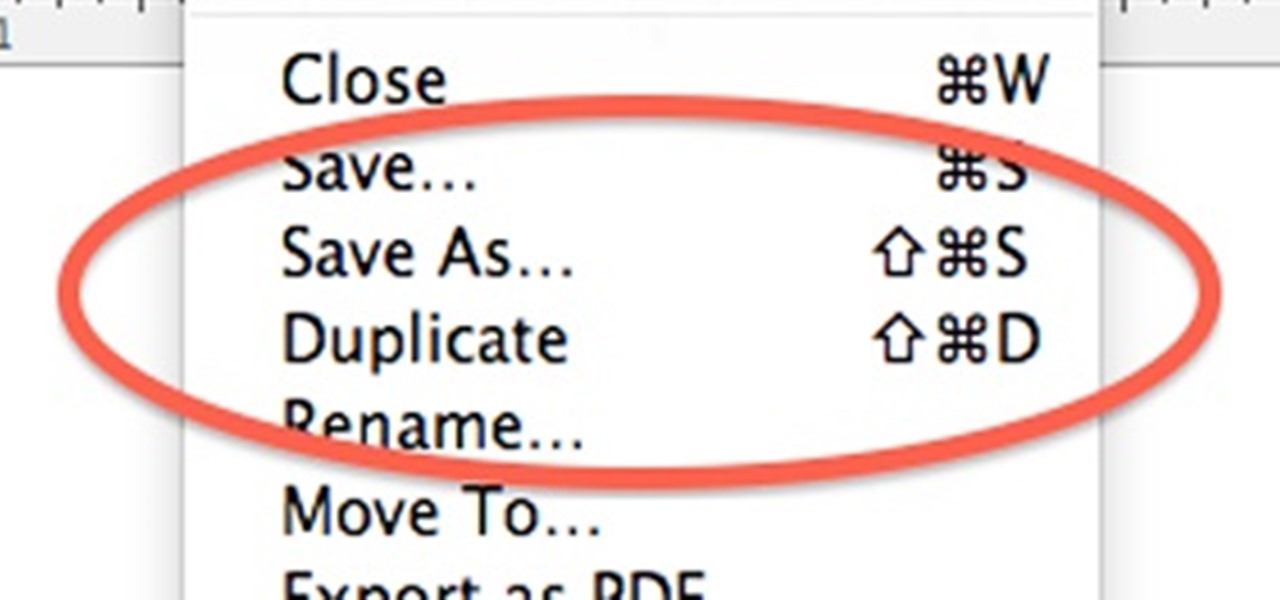
When OS X Lion (10.7) debuted last year, a lot of Apple users were dismayed that the "Save As" option had disappeared, replaced by the "Duplicate" function. Most felt that it just wasn't the same, so when Mountain Lion was released, the "Save As" option was brought back… sort of.

Did you know that there's a way to start a fire by squishing air? In this project, I'll show you how to build a tool that does exactly that—and I'll give you a sneak peak into the principals of how a diesel engine operates!

The guitar is a double-edged sword. I've played all my life, and though I love the act of guitar playing, there are quite a few people I could live with never hearing play again—ever.

OSAGYEFO DR. KWAME NKRUMAH (1909-72) Founder and Father of the Nation Osagyefo Dr. Kwame Nkrumah, the first Prime Minister and President of Ghana, stands out not only among the Big Six but also among the greatest statesmen of history. It was he who canalized the discontent of the people of the Gold Coast Colony into the highly organized movement of protest against British rule, and within a relatively short period won political independence for Ghana on March 6, 1957. With Ghana independent, ...

You want to create a delicious and flavorful meal for your guests but you don’t want to ruin everyone’s diets with a bunch of unhealthy calories. Grilled salmon is not only moist and flavorful but is extremely good for you.

If you like to shop online then it is extremely helpful to have a PayPal account to safely make your online purchases. Help reduce your risk of identity theft by using protected methods like PayPal when your credit card information is involved.

This article is a guide for making Chainmail Armor from start (simple wire) to finish (a finished chainmail shirt). We will be using the European 4 in 1 weave, as this is the most common weave. This is the weave that you usually see in movies. There are several sections to this guide: Materials, Making the Rings, Weaving the Rings, and Making the shirt.

It turns out you CAN have your character in Star Trek Online take a seat in the captain's chair. If you stand on the chair, you can then use an emote in the chat box to have your captain take his seat, just like Picard or Kirk!

Eeverst isn’t for armatures. If you have the ambition of climbing Mt. Everest you will have to do a lot of preparations including physical fitness work, travel arrangements, not to mention putting aside thousands of dollars to make your dream a reality.

Bodyguard jobs can lead to an extremely rewarding and exciting career path. Learn to become a bodyguard with tips on training and salary from a professional bodyguard and former Secret Service agent in this free career video series.

The memories on your devices are precious, even if you don't often get a chance to revisit them. The worst thing in the world is when something happens to your computer or phone, and you end up losing some of those memories because your files weren't backed up or your microSD wasn't fireproof.

Whether you've always dreamed about making your own video games for fun or a career, now you can make the dream a reality with The Unity 2D Game Developer Bundle. Not only does this complete course include a ton of content, but it's not often you get to learn such valuable skills at such a low price. Right now, this course is a huge 98% off its original price, at just $39.99 (regular price $2,189).

Always wanted to learn Python but don't know where to start with the high-level programming language? The Basics for Python Development is perfect for beginners — and right now, it's on sale for just $14.99, which is an impressive 92% off its usual price of $199.

No matter the field you work in, tech dominates every industry in 2020, and that means that you can always increase your earning potential by adding valuable coding skills to your arsenal. Coding can lead to dream software development career paths, lucrative freelance work, and it can be an impressive boost to your résumé. Now, you can learn these valuable skills at home with The Complete One Hour Coder Bundle, an offer at an unmissable 97% off its usual price, at just $34.99 (usually $1,200).

Google Drive has been a gamechanger in the business world. First launched in 2006, Google Sheets has become much more than an alternative to Microsoft Excel. The powerful spreadsheet program is a boon for efficiency that's accessible wherever you have an internet connection—or when you have time edit offline.

If you've tossed around the idea of turning your interest in white hat hacking into a career in cybersecurity or IT, now's as good as time as ever to invest some time and energy into improving your skill set.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

As paper forms become a thing of the past, it's becoming commonplace to fill out contracts, rental agreements, waiver release forms, and non-disclosure agreements online. You can easily fill out forms on your laptop, but how can you best do this using your iPhone or Android device?

My autistic son loves music. One afternoon, when he was nine, I downloaded GarageBand to his iPhone to help with the boredom of a long wait at a doctor's office. Instead of pacing or escalating into a meltdown, he spent the entire hour and a half practicing, learning, and composing. When we finally left that day, the rest of us exhausted and irritated, he shared his first composition with a big smile.

When it comes to augmented reality (AR) on Android, you might be wondering how you can get those cool new games and apps on your unsupported phone. Google has an officially supported device list for its ARCore platform, which usually consists of the more modern devices. You won't find very many older devices on the list for a reason, but that doesn't mean your "old" phone can't use ARCore still.