While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

The long wait is over — the best augmented reality device on the planet is finally available.

We've already shown you our favorite new action games that have come out this year, but now it's time to share our all-time top ten list. These games are available for both Android and iPhone, they don't have intrusive ads or freemium schemes, and most importantly, they're all completely free to play.

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

Continuing our NR30 series this week, we focused on the leaders of the software development industry that make augmented reality experiences possible. In other news, two of the current leaders in making AR headsets, Microsoft and Magic Leap, are pursuing multiple verticals with their products, as both now appear to be interested in making AR headsets for the military.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

If you want to use your iPhone with another carrier, all you have to do is contact the original carrier to request an unlock, which is usually granted in a few days. Unfortunately, you need to meet specific criteria to officially carrier-unlock your iPhone, like paying off the device in full and completing any contracts. But that doesn't mean there isn't a workaround you can use beforehand.

The misconception that macOS is more secure than the Windows operating system is far from the truth. With just one small command, a hacker can completely take over a MacBook and control it remotely.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

Google is working on something so big they had to name it after an entire galaxy: A new operating system that merges Android and Chrome OS into one unified front.

Watching an ice cream pro build you a custom frozen treat mixed with your favorite fruit, candy, and/or toppings makes buying a cone even more exciting. But why go out for ice cream when you can create your favorite combinations in your own kitchen? While you might not have an expensive frozen slab for ice cream topping your kitchen counters, you can mimic the creamy consistency and customizable options from Cold Stone Creamery and Marble Slab any time you're craving it. Best of all, you don'...

Of course, if it were a perfect form of currency, it would have become the standard by now. But it hasn't. Wanna know why? The story begins with the advent of agriculture, when humans had settled down under groups as units called villages, over 10,000 years ago.

Welcome back, my greenhorn hackers! As hackers, we often take for granted that nearly all of our hacking tools and operating system are free and open source. I think it's important to examine a bit of background on how we arrived at this intriguing juncture in the history of computer software. After all, we pay for nearly all of our other software (Microsoft, Adobe, etc.) and nearly everything else we use in life, so how is it that Linux and all our hacking tools are free?

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

Lenovo brought out the big guns for CES 2014, with the Vibe Z showcased as the Chinese company's' first foray into the LTE smartphone space. Slated for a February release, the ultra-thin and extremely light smartphone will certainly be in the running for top smartphones of this very new year. Photo via CNET

Here's how to make dry-ice at home, or wherever you feel like it! All you need is a pillow case, and a CO2 fire extinguisher.

There is never a dull moment when it comes to the internet. You can find practically anything you want, whenever you want it. To make that process even smoother and more direct, companies have created a bunch of apps designed to help you find what you're looking for, or enlighten you on a subject you may not have even thought of yourself.

There was recently a case that came to national attention where a gentleman was arrested at an airport for having a watch that looked like a bomb, among other things. As it came out, the watch was, in fact, not a bomb, and the man was just an artist who was probably trying to make a statement of some sort. Well, that message was lost amongst the hail of people shouting that either he had been stupid for bringing that watch on the plane and so deserved to be arrested, or that it's a free count...

Steampunk is a tremendously interesting phenomenon because of its reliance on science fiction, and fiction in general. Steampunk can arguably be broken down into two categories: the fiction, and the aesthetic. Sometimes these categories cross over, but they're often more distinct than most people suspect; that said, the aesthetic is firmly based in works of fiction.

This holiday season, give yourself a gift that will keep on giving: a new web development skill. Whether it's to secure lucrative freelance work in the new year, bolster your résumé, or have fun with some frankly outrageous discounts on online course bundles right now (up to 99% off), there's nothing better you can do with your free time. Your future (pro coder) self will thank you.

Former soccer star and current celebrity David Beckham has the augmented reality abilities of Facebook and Instagram as allies in the effort to eradicate malaria from the world.

The venture arms of Samsung and Verizon Ventures, along with Comcast, are among the strategic investors backing startup Light Field Lab and its glasses-free holographic displays in a $28 million Series A funding round

With Microsoft taking direct aim at enterprises for its HoloLens 2 with a $3,500 price tag, one startup is betting that business will be willing to pony up for glasses-free 3D displays as well.

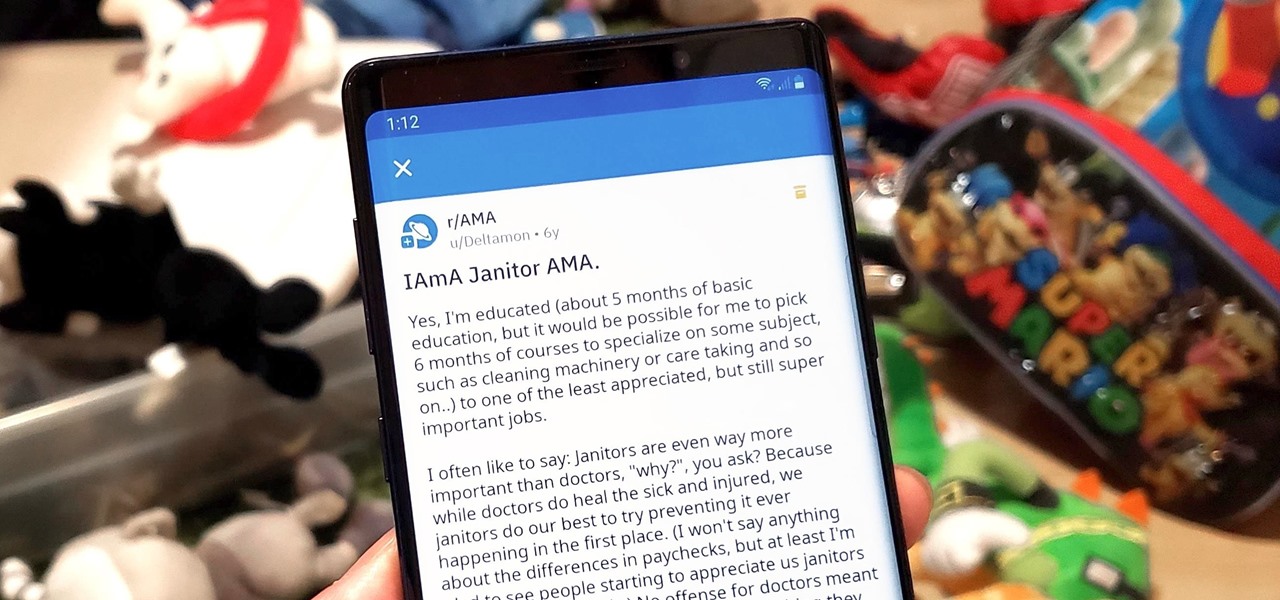
Short for Ask Me Anything, AMA threads are one of Reddit's signature features. They enable you to directly interact with a whole range of interesting personalities, from common folk with amazing life experiences to influential celebrities that help shape politics and culture.

A Series B round of funding, totaling $30 million, will enable Helsinki-based startup Varjo to launch its industrial-grade augmented and virtual reality headset capable of "human-eye resolution" before the end of the year.

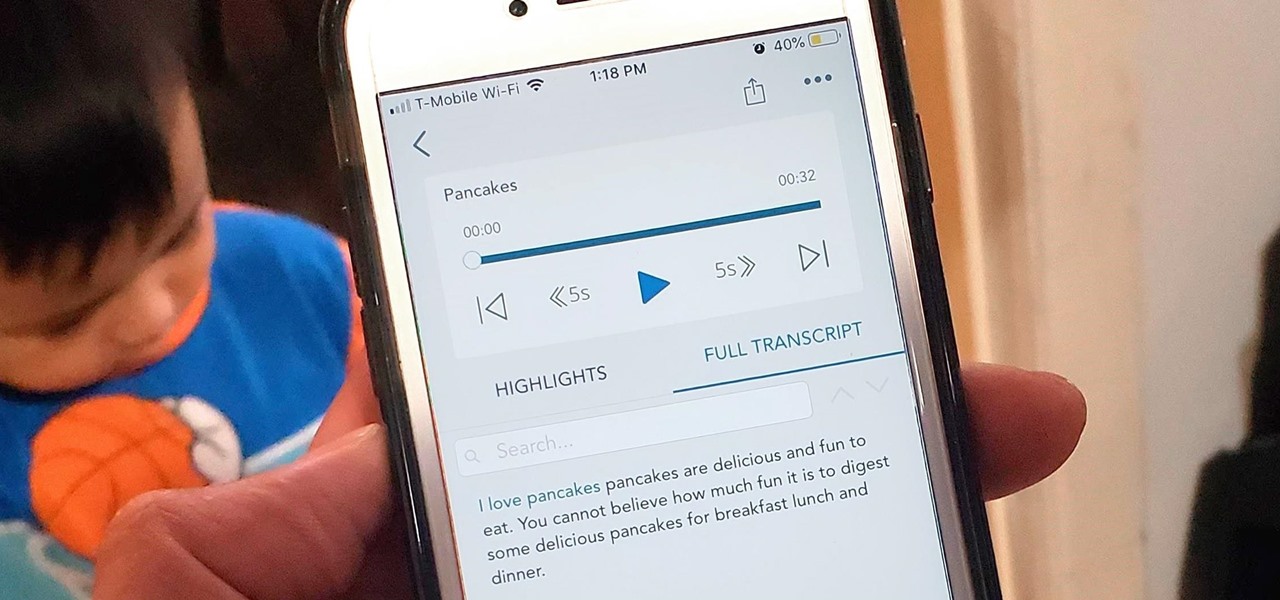
Despite its fifth-place finish in our ranking of the best transcriber apps on iOS, Voicera is still worth highlighting due to numerous factors that set it apart from the crowd. Besides being completely free to use on both iPhone and Android, the app's AI-based transcription service performed extremely well in our testing.

Users of Epson's smartglasses can now tell their devices to "talk to the hand" when it comes to passwords and authentication.

Last week, we told you about Microsoft's Alex Kipman and his nomination for the annual European Inventor Award, presented by the European Patent Office (EPO). And while that's big news in and of itself, it turns out we overlooked a very important detail buried in the EPO's video presentation. What was it? Only one of the most sought-after data points related to the HoloLens since its launch: how many have been sold.

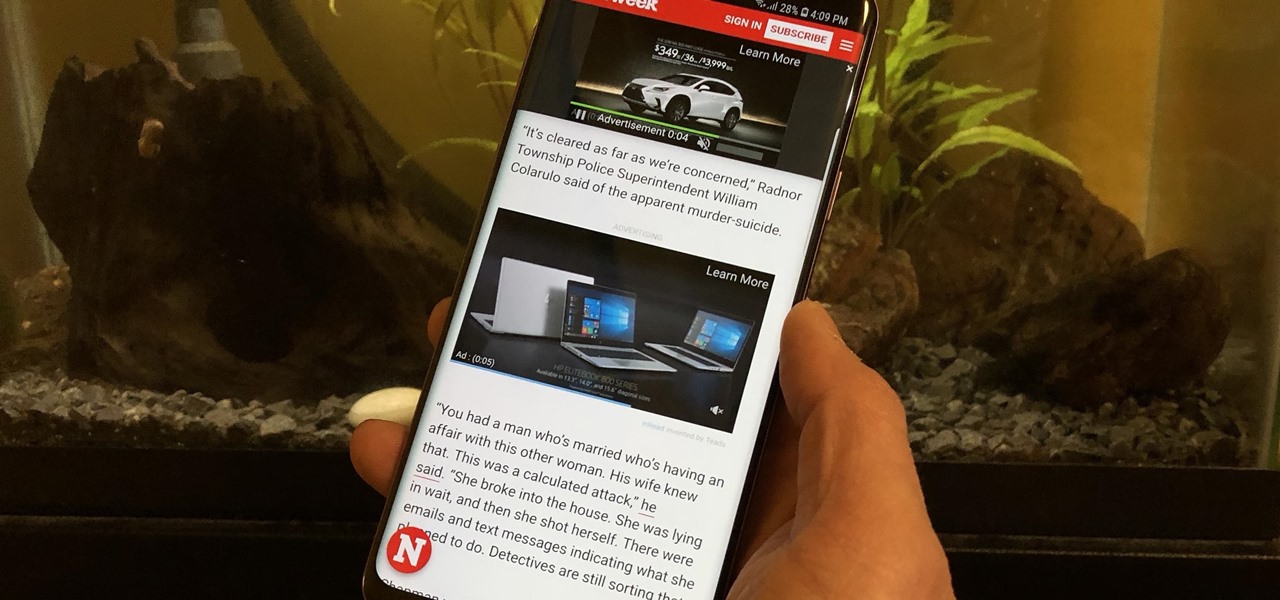
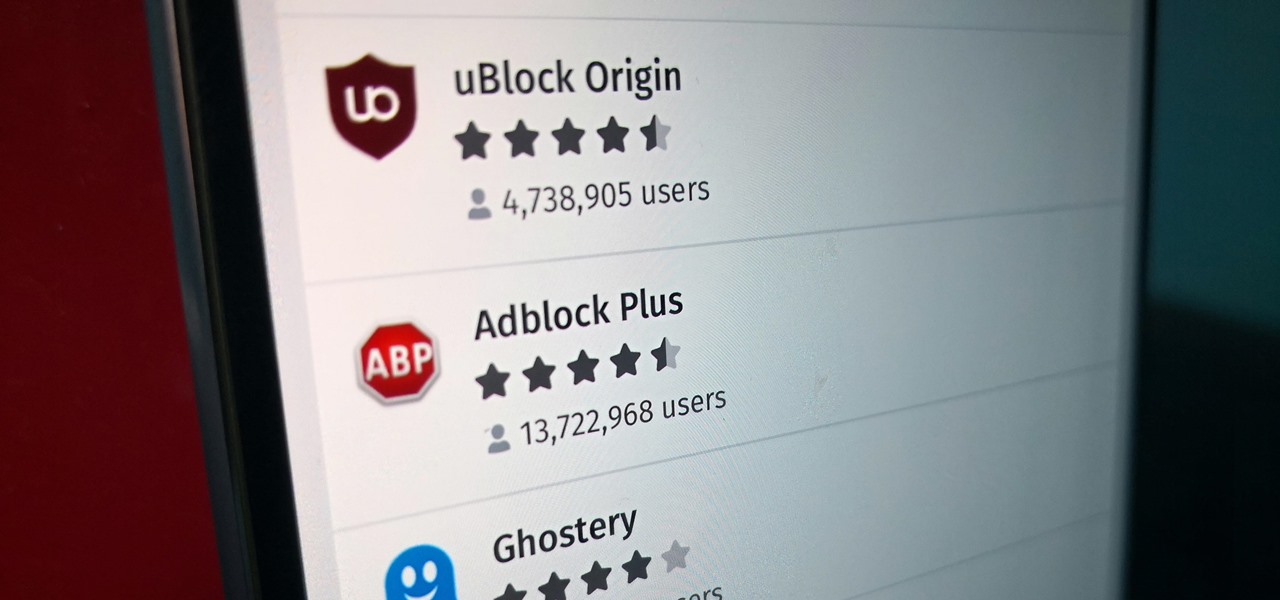
Ads can detract from your mobile browsing experience, especially if they appear out of nowhere as popups or large annoying banners that take up almost all of your screen. If those weren't bad enough, some ads appear as extremely loud videos that can even disrupt others around you. In fact, ads have gotten so obnoxious that even Google itself was forced to act.

The cosmetics industry faced a rude awakening on Friday as beauty behemoth L'Oréal gobbled up ModiFace, one of the leading providers of augmented reality technology to the cosmetics industry (price details for the acquisition were not disclosed).

Samsung and Apple are the two titans of the mobile phone industry. After Apple deployed the iPhone X in November, Samsung had three months to brood until Mobile World Congress, where they unveiled the Galaxy S9. Now that both phones are out, it's time to put them head-to-head.

Features like themes and a tab queue make Firefox an extremely versatile mobile browser. Mozilla is constantly adding bonus functionality like this to Firefox, but a long-time staple is perhaps the most powerful feature: Extensions. This system gives you the ability to add features without having to upgrade the entire app.

If building with Lego blocks in AR appeals to you, rest assured that an app is on the way for iPhones, iPads, and Android devices.

In case you didn't already know, augmented reality is here. It's no longer just an idea in a cyberpunk novel. And while augmented reality has been around for a long time, the actual technology is finally catching up to the idea.

Pentagram has to be one of the most nightmarish creations on American Horror Story (even though she has some pretty tough competition to fend off). Can you think of anything much worse than a pair of hands wriggling their way out of your temples?

One of the most popular usages of modern-day smartphones is listening to music. It doesn't matter if you download or stream your tunes, you are part of a massive group of users who do exactly the same. While statistics are a bit foggy on how many smartphones users download music, we do know that over 68% of American smartphone owners stream music on a daily basis.

An update to the iFramed social media gateway app for iOS adds an augmented reality feature called JuxImage that gives its users Snapchat-like photo and video effects.

If you are an NYC commuter like me, then I'm sure you know how bad the city's transportation has gotten.