Not to be outdone by Apple and it's new line of flagship phones, Google has followed suit and finally announced the followup to their highly regarded Pixel line of handsets — the aptly named Pixel 2. Thankfully, the tech giant has also joined in on the trend towards more durable devices, and has engineered both the Pixel 2 and Pixel 2 XL to have a rating of IP67 under the IEC standard 60529.

Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.

The search is on to find antibiotics that will work against superbugs — bacteria that are rapidly becoming resistant to many drugs in our antibiotic arsenal.

I spent just about my entire weekend trying to break the 800, 900, and 1,000 levels of Instagram — because it's a game, y'all — by playing around with my follower count. I shamelessly manipulated my IG account in such a way that was extremely time consuming and left many of my friends pretty pissed off at me as I spent most of my time glued to my phone. (Sorry, friends. I know I'm obsessed.)

Mosquitoes are a big problem, and citronella candles are not the solution. There are a lot of mosquito species. The American Mosquito Control Association reports there are more than 3000 mosquito species in the world, and about 200 of those occur in the US. The most common are the Aedes, Anopheles, and Culex species. These are also the three mosquito species most likely to transmit serious illness, and all of them live in the US.

A groundbreaking new Android feature called seamless updates was announced at Google I/O 2016. No longer would we have to wait for updates to download and install — instead, they'd be applied silently in the background, and the new Android version would be waiting on us the next time we restarted our phones.

We've worked hard to reduce the flow of toxic chemicals into our waterways, which means no more DDT and other bad actors to pollute or destroy wildlife and our health. But one observation has been plaguing scientists for decades: Why are large quantities of one toxic chemical still found in the world's oceans?

Lyme is a growing threat as we move into warmer weather in the US. Researchers have said this year could be one of the worst for this tick-borne disease, as a skyrocketing mouse population and warmer temperatures increase the risk.

Colorado State University scientists have developed new tech that quickly identifies the presence of Zika virus in mosquito populations — and in human body fluid.

Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).

If you ever imagined turning the surface of your desk into one large augmented computer, well the future might not be far off, my friends. Lampix, the company that transforms any surface into a smart surface, is currently working on a portable and quite fashionable lamp to project an augmented computer onto any surface that you can interact with using your hands.

You may have heard that Samsung Push is an incredible service that all Android users absolutely love. For one, Push provides extremely useful notifications for Samsung apps to assist you in all aspects of your life.

The culprit probably wasn't what doctors were expecting when a 57-year-old man in Hong Kong came to the hospital. The patient was admitted to the intensive care unit in critical condition. A clue to the cause of the infection would lie in the man's profession—he was a butcher.

A new study confirms that antibiotics can prevent surgical intervention if your child's appendix becomes inflamed, potentially saving his or her life.

Every year, 100-200 people in the US contract leptospirosis, but usually 50% of the cases occur in Hawaii where outdoor adventurers are exposed to Leptospira bacteria found in freshwater ponds, waterfalls, streams, and mud. That's why it's so alarming that two people in the Bronx have been diagnosed with the disease and a 30-year-old man has died from it.

Responding to the emergence of Zika in the US, researchers investigated what type of repellent works best to reduce your odds of a mosquito bite from Aedes aegypti, the mosquito species that spreads the Zika virus.

Where in the world did it come from? All of a sudden, one day, someone had an infection with flesh-eating bacteria. It captured headlines and worldwide attention because it was such a severe, strange, uncontrollable, and really disgusting condition.

When the time comes to replace your car, you most likely have a checklist of criteria that you would like on the new one. Your car is possibly the most expensive possession you have—or the second-most expensive, after your home—so you want to make sure that you are not only getting what you want, but that you are getting the best deal possible.

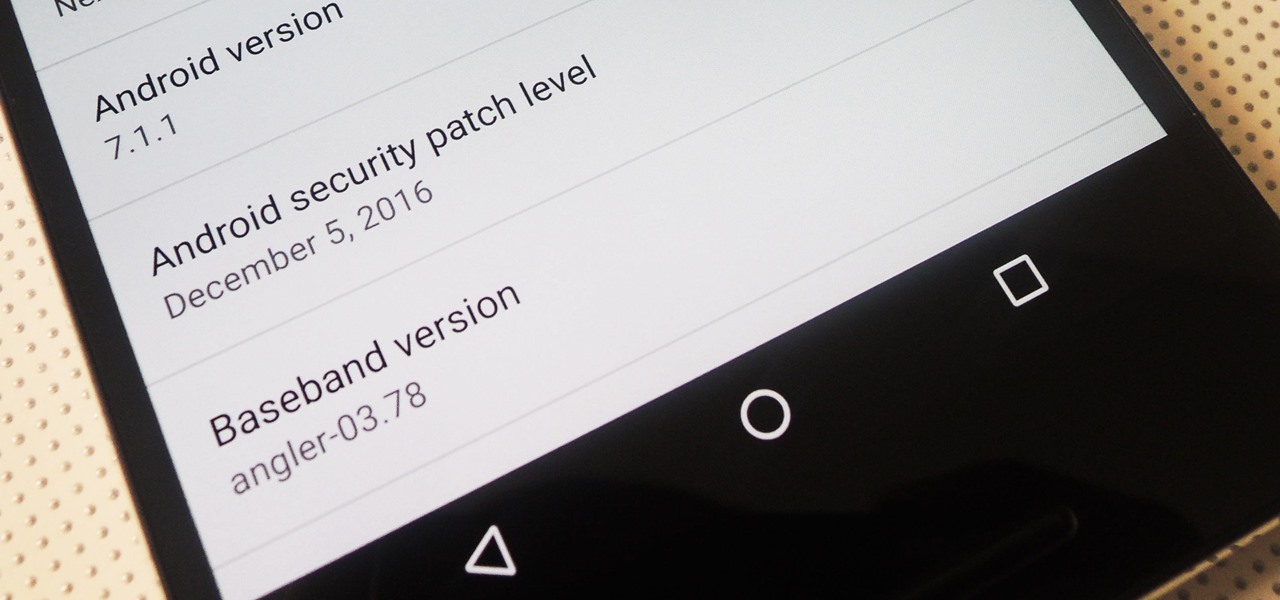
Android 7.1.1 stock images for the Nexus 6P were released last week on December 5, 2016. However, Verizon users seem to have been excluded from the update. Google's factory image page states "All carriers except Verizon" next to version number NMF26F. This doesn't seem fair, especially since Verizon Nexus 5X users received the latest Android Nougat update.

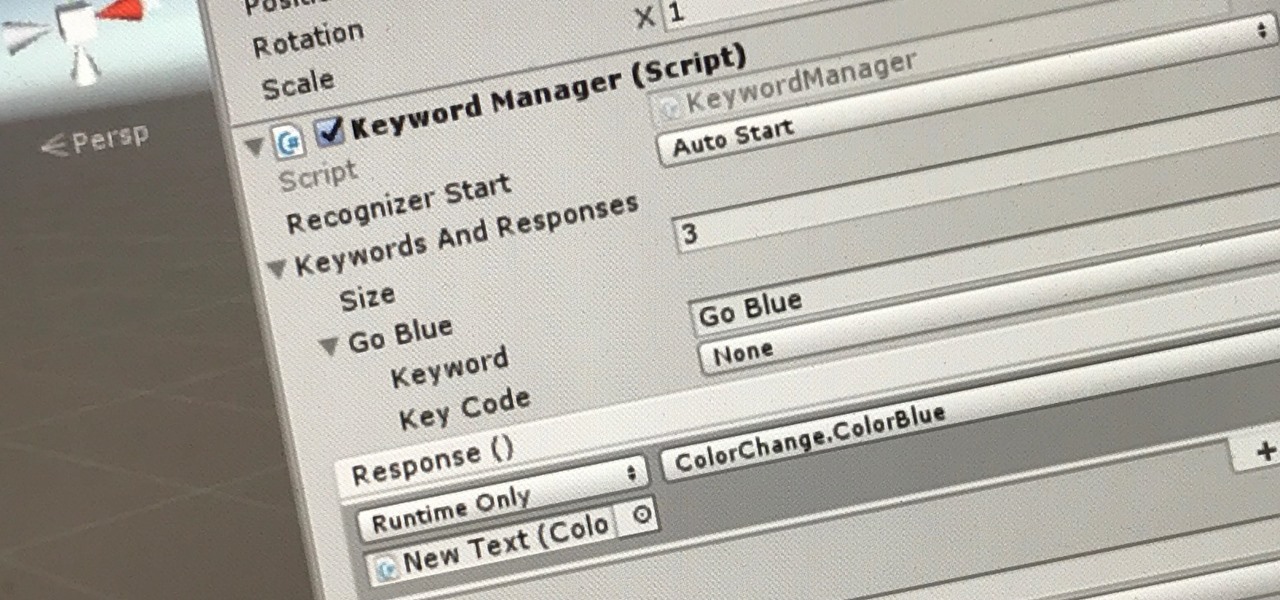
The HoloToolkit offers a great many, simple ways to add what seems like extremely complex features of the HoloLens, but it can be a bit tricky if you're new to Windows Holographic. So this will be the first in an ongoing series designed to help new developers understand what exactly we can do with the HoloLens, and we'll start with voice commands.

It seems like a new, dangerous Android exploit is uncovered every month or two. The latest headliners are NightMonkey and Chronos from the list of CIA hacks reported by Wikileaks, which have been billed as gaping security holes in the world's biggest mobile operating system.

Maybe you decided to make your own pumpkin pureé because of all the buzz about canned pumpkin actually being squash (which, by the way, is a load of bull: it's made with ugly pumpkins, but pumpkins nonetheless). Or maybe you just wanted to be that person that proudly proclaims that they made everything from scratch for their Thanksgiving feast this year (ahem, me).

GitHub is an extremely popular site that allows developers to store source code and interact with other users about their projects. Anyone can download public, open-source files on GitHub manually or with Git, and anyone can fork off someone's project to expand or improve it into its own project. It's a really great site for programmers, developers, and even inspiring hackers.

Breaking off a piece of that Kit Kat bar gets a lot more difficult when the whole thing weighs 13 pounds.

When most people say, "Damn, look at that rock," regarding an engagement ring, they're usually not referencing an actual rock—let alone a space rock.

Passwords are everywhere. We use them to unlock phones, computers, websites, encrypted disks, encrypted files... the list just goes on and on. Savvy users will already have a password manager of some sort that can generate a very strong password on a per site basis. However, these password managers also require a password. Not only that, it has to be something memorable.

Fondant looks pretty, but man, it sure does taste weird. Don't Miss:

Step aside, ginger ale; ginger beer is here, and it's delicious. Ginger beer is made by fermenting a combination of ginger simple syrup, yeast, and water, which gives it its robust flavor and sparkling quality. It's extremely simple to make, but you do have to wait a bit for the final product. After a few days, though, your ginger beer will be sparkling and ready to drink as is, or in your favorite cocktail.

Hummus seems like it should be easy to make, but creating that ideal creamy consistency can be pretty difficult. Often it comes out too chunky, which means your hummus won't be good for dipping into. Luckily, there is one trick that will help you create the creamiest consistency and make you never want to go near store-bought hummus again: add baking soda.

The original frozen hot chocolate is from Serendipity 3, an extremely famous eatery in NYC. However, its fame had created many copycat recipes, which eventually prompted its owner, Stephen Bruce, into releasing the delicious recipe in 2004.
Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain.

I know I'm in the majority when I say that grilled cheese sandwiches are one of life's simplest and best pleasures: gooey, rich, melted cheese, sandwiched between two perfectly-buttered pieces of toast... perfection.

As Android's official app provider, the Google Play Store is packed with thousands of useful programs. But Google's terms of service is extremely restrictive, which means that countless apps simply don't qualify to be hosted on the Google Play Store.

Everyone has their own reality, and in that same vein, everyone has their own guidelines for what makes the "perfect fried chicken." Now, I'm not saying that my version is the ultimate for everyone, but it's definitely a crowd pleaser in my experience.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

I'll be the first to admit that I have a problem: I'm utterly addicted to tea.

First of all, I would like to apologize for a week long absents for the tutorials of this newly series, Raspberry Pi. But obviously I'm back and I present all you guys a article on turning your Raspberry Pi into a hacking platform. I'm gonna use the platform Kali Linux for the Raspberry Pi. I should note that I'm not gonna go into detail on how to install Kali Linux since OTW already has done a tutorial on how to turn your Raspberry Pi into a Hacking Pi. The point of this particular tutorial ...

Welcome to an introduction on writing basic malware, an optional sub-series in which I expose you to malware and its technologies. This is written for those who wish to seek a beginning in malware analysis or enlightenment on the subject. We will be justifying the writing and covering types of malware.

Welcome back everyone. As many of you know, reconnaissance is extremely important in any successful hack. Without proper reconnaissance, we won't know what we're about to get into, literally.

Before I get ostracized by all of you whisky lovers who live and die by whisky served neat, let me say my piece.