While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

As a developer, before you can make augmented-reality robots that move around in the real world, controlled by a user's finger, you first need to learn how to harness the basics of designing AR software for a touchscreen interface.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

OpenBSD implements security in its development in a way that no other operating system on the planet does. Learning to use the Unix-like operating system can help a hacker understand secure development, create better servers, and improve their understanding of the BSD operating system. Using VirtualBox, the OS can be installed within a host to create a full-featured test environment.

Andre was enjoying the carefree life of a 12-year-old with his friends, riding his bike and playing sports, like all kids that age. Schoolwork wasn't hard for him, and his grades showed that.

Have you ever seen those super-expensive universal remote controls like the Logitech Harmony and thought to yourself, "Man, I really want one of those, but that's just too much money"?
Welcome back Hackers\Newbies!

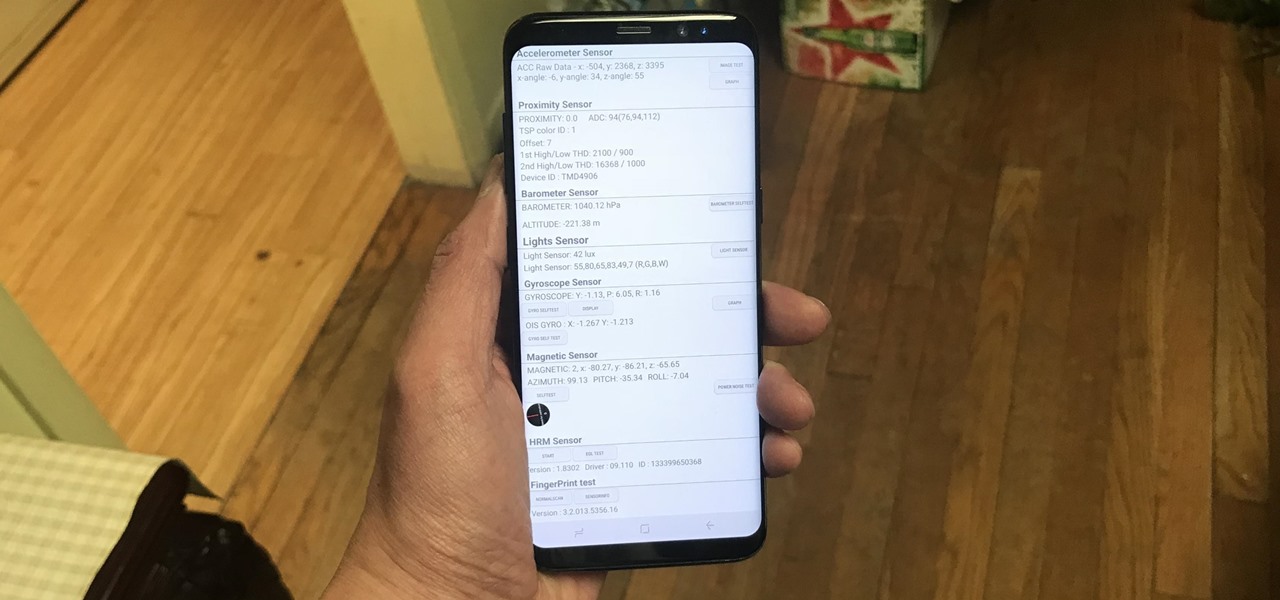
Besides obvious features like a touchscreen and biometric sensors, the modern smartphone comes with an array of state-of-the-art hardware in the form of various sensors that help your device sense the environment around it. And if you have a Samsung handset, chances are, you have a handy feature built in that enables you to check if these sensors are functioning 100 percent.

Becoming someone else for Halloween is a lot of fun, but it can take a ton of tools to accomplish. An elaborate costume can require you to slather yourself in all kinds of makeup, paints, and glues, and putting it on is only half the work. The real fun starts when the party's over, and you have to remove it all.

One of the best things about Christopher Nolan's Batman trilogy is how realistic he makes the caped crusader feel. Unlike the Joel Schumacher or even the Tim Burton versions, Nolan's world seems grounded in some level of scientific fact. But just how close is science to actually being able to replicate some of the Dark Knight's gadgetry?

To some, SCRABBLE is just a board game to play during family game night or during a casual get-together. Others think of SCRABBLE as a mere hobby. But with any activity, there will always be fanatics—the ones who would rather sell their soul than stop—the ones with a constant yearning for self-improvement—the merciless.

If you have an iPhone 15 Pro or 15 Pro Max, your Action button has even more actions it can perform thanks to the iOS 18 software update. These actions are also available on the iPhone 16 series lineup — the iPhone 16, 16 Plus, 16 Pro, and 16 Pro Max — all of which have the Action button.

The last iOS software update was a modest one, but iOS 17.4 has a lot more for your iPhone, including changes to emoji, Podcasts, security, Safari, widgets, Apple Cash, CarPlay, and more.

While new features in Safari, Camera, Photos, Notes, Weather, Messages, and other Apple apps may steal the show on iOS 17, there are some impressive new features you need to know about when it comes to FaceTime audio and video calls.

There's an iOS feature that benefits many users, but it's absolutely vital if you wear AirPods or other headphones models connected to your iPhone. A large number of iPhone users don't even know about it, especially since it's disabled by default and hidden deep in the system settings.

You're probably sharing a ton of information on your iPhone with other people, apps, and services without really realizing it. Now there's a new tool to show you just how much, and it can be an eye-opener as well as a fast way to manage sharing permissions and review your account security.

When setting up your home office or giving it a makeover, the desk is the key to making the room a functional workspace. And if you're in there all day, it also has a significant impact on your health. Standing desks can help offset some of the adverse health risks associated with sitting all day, but it's hard to find a decent standing desk that won't break the bank. That's where Flexispot comes in.

Safari keeps getting better and better on the iPhone, and that's exactly what happened with the latest Safari 16 update for iOS.

You may not always want to, but there will probably be a time when you'll want to know if an email you send — like a job application or a support request — is opened by the recipient. It's actually easy to implement, and you may be using an email client on your device right now that supports email tracking.

You may be tempted to install the iOS 16 developer beta on your iPhone to try all the exciting new features it has to offer, but it may be a good idea to wait if you only have your personal iPhone that you use every day.

Samsung has a cool security feature built into One UI that has an interesting side effect, one that lets you have two separate copies of any Android app on your Galaxy phone. And that's not the only integrated Samsung tool for cloning apps.

There are tons of tools out there that do all kinds of recon, but it can be hard to narrow down what to use. A great way to be more efficient is by taking advantage of scripting. This doesn't have to mean writing everything from scratch — it can simply mean integrating existing tools into a single, comprehensive script. Luckily, it's easy to create your own subdomain enumeration script for better recon.

After years of speculation and rumors, Apple finally debuted AirTag, its tiny Bluetooth tracking device, during its spring 2021 event on April 20. Unlike with Tile trackers, there's no way to attach an AirTag to an object, but there's an entire market out there for AirTag accessories so that you can put one on your keychain, bike, or any other object that you can't just toss a naked AirTag in or onto.

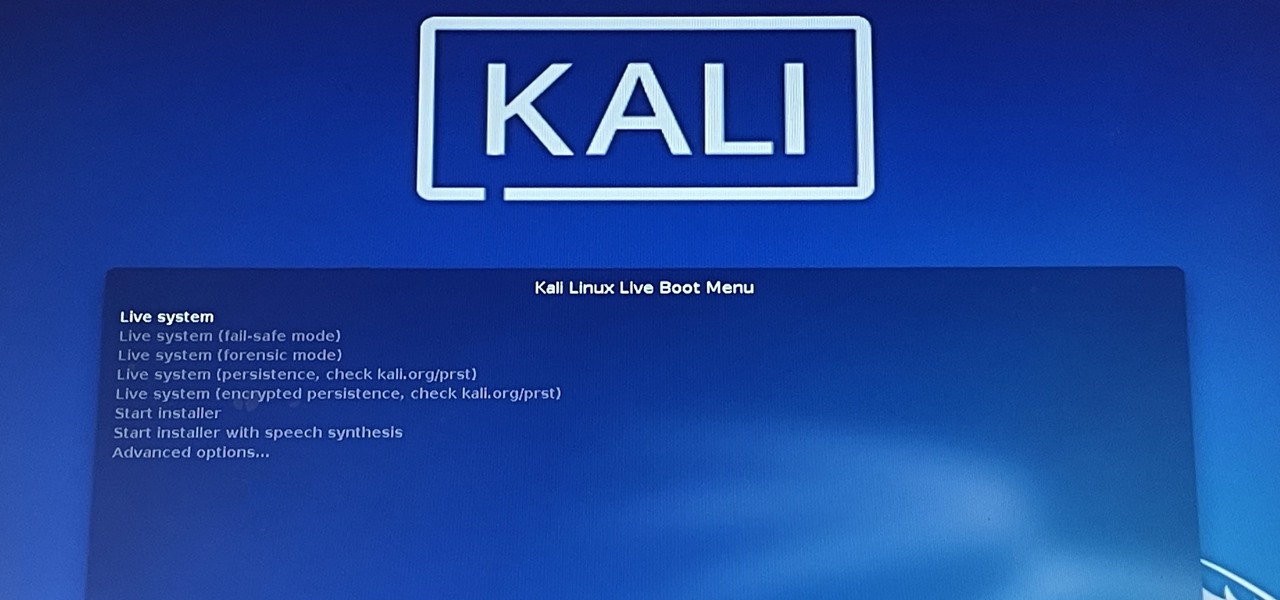
Kali Linux is the go-to Linux distribution for penetration testing and ethical hacking. Still, it's not recommended for day-to-day use, such as responding to emails, playing games, or checking Facebook. That's why it's better to run your Kali Linux system from a bootable USB drive.

When Microsoft unveiled Mesh a couple of weeks ago, the move revealed a major part of Microsoft's next steps toward dominating the augmented reality space, particularly with regard to enterprise customers.

The process of trying out new augmented reality and virtual reality hardware is as personal as it gets. Bottom line, if you can't directly try these immersive devices on, it's difficult to really understand the benefits they can bring to your life and work.

You should feel relatively safe to watch and post videos on TikTok, but like with any online service, you're always at the mercy of hackers.

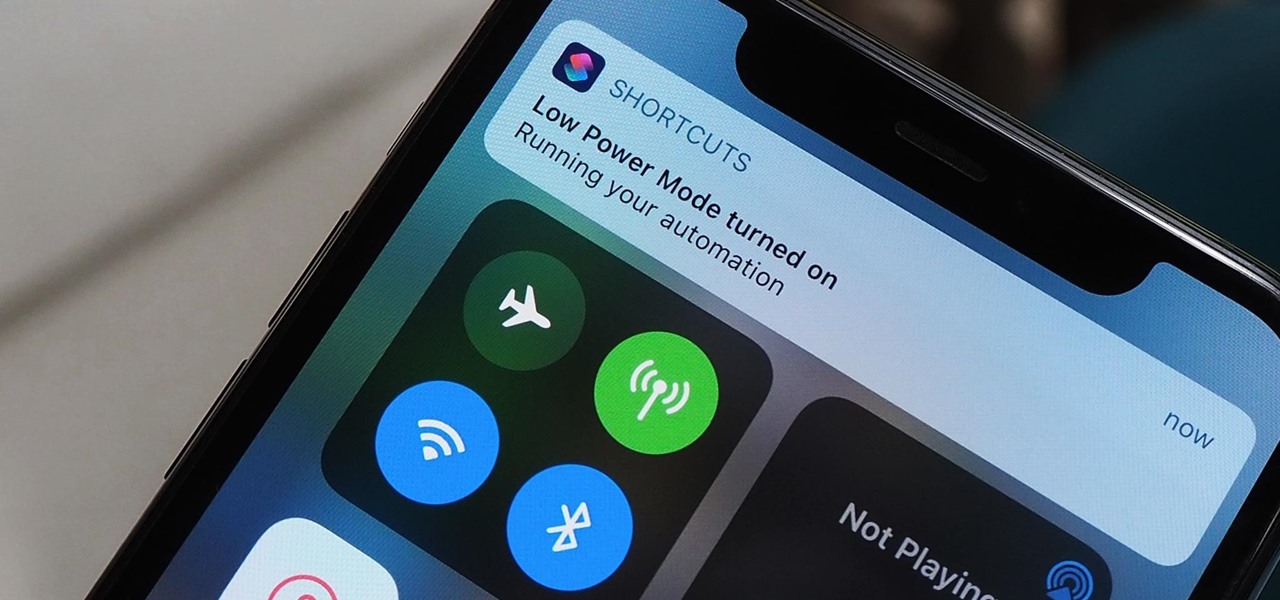
Shortcuts are meant to make your life easier, and iPhone shortcuts are no exception. They can use different triggers, manual or automated, to perform actions in the background, allowing you to do things like send a prewritten text message during a bad date or change your wallpaper at certain times of the day. However, sometimes it's not only about the shortcut itself but about how fast you can run it.

Withstanding an attack from a motivated hacker is one of the most important responsibilities a system administrator must undertake. This is especially true for websites that may contain sensitive customer information and a high volume of users. So it's important for a sysadmin to take proactive measures to find and fix vulnerabilities in their websites.

The new iPhone 12, 12 mini, 12 Pro, and 12 Pro Max may seem like minor updates to the iPhone 11 lineup, but there are quite a few features that make them worth the upgrade. Apple has done a good job of highlighting all of those features, but some didn't get all of the love they deserved.

Browser extensions are extremely useful since they can expand web browsers like Google Chrome and Mozilla Firefox beyond their built-in features. However, we don't always know who's behind a browser add-on or what it's doing beyond what's advertised. That's where ExtAnalysis comes into play.

Are you tired of endless rows and columns of apps on your home screen? Before iOS 14, your only option was to hide apps in folders, uninstall them, or use some sort of elaborate workaround. You could hide a few stock apps easily enough, but that's it. Now, in the latest version of iOS, you can hide apps for real, and even hide entire home screen pages, and still access the apps in one convenient drawer.

You might be giving out your name to every stranger you see, and you don't even know it. That iPhone of yours has a name — generally a combination of your first name and device model — and it broadcasts it to others via AirDrop, Personal Hotspot, Bluetooth, Wi-Fi, and other connections. Sure, it's useful to keep your device name simple and to the point, but there are upsides to changing it.

The art of fuzzing is a vital skill for any penetration tester or hacker to possess. The faster you fuzz, and the more efficiently you are at doing it, the closer you come to achieving your goal, whether that means finding a valid bug or discovering an initial attack vector. A tool called ffuf comes in handy to help speed things along and fuzz for parameters, directors, and more.

Bootloops are a risk inherent to rooted devices — with great power comes great destroyability, after all. While custom recovery sometimes provides a quick fix when you flash the wrong Magisk module, with TWRP becoming more challenging to implement thanks to Android 10, the solution is a bit more complicated nowadays.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

A rather exciting development has recently surfaced in the jailbreaking scene for iPhone. The Checkm8 bootrom exploit was shown off to the public by axi0mX, which made way for the undefeatable Checkra1n jailbreak tool. With it, you can freely jailbreak a variety of older iPhone models without any restrictions. The success rate is quite high, too, when compared to other jailbreak methods.

Network enumeration is one of the essential phases of an attack, but it can take a lot of time and effort depending on the size. We've all been spoiled by Nmap and similar tools, and while there is a learning curve involved, they are extremely useful. But there's also GoScan, a tool that builds upon Nmap, offering an automated way to enumerate networks and services quickly.

The internet has undoubtedly changed the way we work and communicate. With technological advances, more and more people can collaborate on the web from anywhere in the world. But this remote-friendly environment inherently brings security risks, and hackers are always finding ways to exploit systems for other uses.