Adobe's Photoshop has an arsenal of tools, filter and effects, like the warp tool, and mastering them makes for successful digital art. Learn how to work the warp tool in this free Photoshop tutorial video series.

Geraniums are extremely hardy flowers that can be planted both indoor and outdoors. Learn how to grow and care for geraniums in this free landscaping video series.

Eczema is a skin condition where skin is extremely irritable and sensitive. Learn how to care for eczema with expert tips in this free health video series.

Bean sprouts are an extremely healthy and delicious way to enjoy legumes. Although sprouting can seem intimidating to some, it is really an easy process. Any whole bean can be sprouted - Mung, Garbanzo, Kidney, Moth, Adzuki, Lentil, etc. Sprouts can be eaten raw in salads or cooked. Watch this how-to video and try this simple method for sprouting mung beans.

Prepare an easy vegan asian cucumber salad which serves 6 people. It only takes 10 minutes to prep but will take 2-3 hours or even overnight to marinate.

Prepare this wonderful easy vegan meal for six. It only requires a 10 minute prep time and it cooks in 35-40 minutes.

Our gardening expert will explain how to set up your perfect perennial plant business. Learn which plants go together, how to position the plants for just the right amount of sun, and how to determine if your adjustment has been successful. Are the flowers, shrubs and grasses happy after all of the work you have put in to meet their needs? Once you have mastered the basic care and maintenance of your garden, then you can concentrate on working toward exactly the look you want. Martha Cycz dis...

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

As a root user, you have a lot of responsibilities to make sure your phone stays secure. Expectedly, some things may slip through the cracks. Remembering to check which apps have been granted root access is extremely important. All it takes is one bad app, so it's good to learn how to avoid that at all cost.

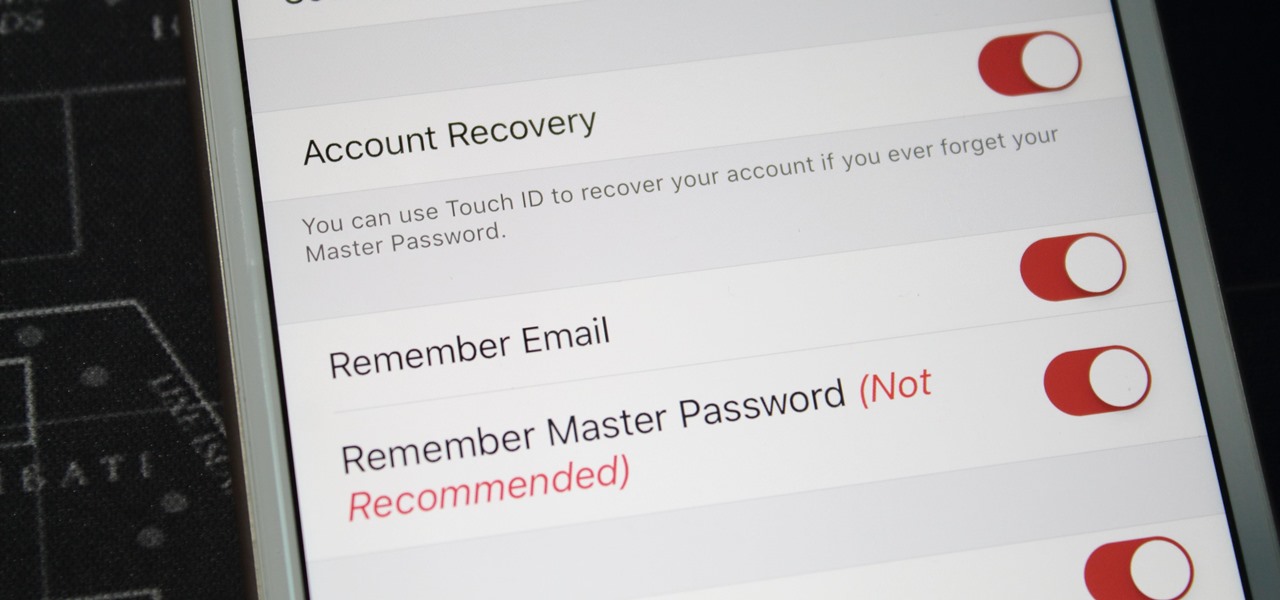
With any password manager, the only password you need to remember is the master password that locks the vault from both hackers and the company. This makes the master password very important. But what happens if you forget this password? Well, LastPass has you covered.

Escape rooms, those real world puzzle games that challenge teams to solve a mystery and gain their freedom from a locked room, are all the rage right now. But augmented reality games such as The Lockdown could make them obsolete.

Even though smartphone audio quality has improved in recent years, the tiny built-in speakers aren't always loud enough. But if you want to turn the volume up to 11, all you need is a few household items to make a rig that will amplify your phone's speakers throughout the whole house.

When it comes to busted smartphones, liquid damage ranks right up there with shattered screens as one of the most common issues owners have to deal with—as well as the most embarrassing. Thankfully, though, with the rise of waterproof phones such as the Samsung Galaxy S7 and even the iPhone 7, this is becoming less and less of a worry. But not everyone has a waterproof device.

Breaking off a piece of that Kit Kat bar gets a lot more difficult when the whole thing weighs 13 pounds.

When most people say, "Damn, look at that rock," regarding an engagement ring, they're usually not referencing an actual rock—let alone a space rock.

God, chili is amazing this time of year. It's hearty, filling, freaking easy to make, and it warms you from the inside out.

Welcome back everyone. I apologize for the lack of training articles, but I've been rater busy lately. I've recently picked up a second job and my college courses are now back in session, so I'm a bit strapped for time.

SentrySafe puts all sorts of measures in place to protect your valuables and important documents. This particular SentrySafe has an electronic lock, four 1-inch bolts to keep the door firmly in place, pry-resistant hinges, and it's able to withstand drops of up to 15 feet. That all sounds great, until you find out that you can open this safe—and pretty much every safe like it—in a matter of seconds using only a magnet. A rare earth magnet, to be precise.

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.

Welcome back everyone. As many of you know, reconnaissance is extremely important in any successful hack. Without proper reconnaissance, we won't know what we're about to get into, literally.

The start of a new year is generally thought of as a chance to start over, a time to improve or "fix" things in your life. Yet most people who set stringent New Year's resolutions find themselves failing within weeks—or even days—of setting their lofty goals.

Recently I've been looking around our wonderful community and I've seen some absolutely hands-down fantastic python scripting articles. But, in the end, these series weren't very extensive. I've been wanting to do a series on teaching python for a while now, and I don't mean just the basics, I mean to make an extensive series that takes it all the way from "Hello, World!" to popular third party modules, and everything in between!

We're all familiar with the sinking feeling that happens when you cruise through a recipe, only to arrive at an instruction that calls for a tool you don't have. Some of the best food hacks (and my personal favorites) exist to combat that problem. Why spend money on a kitchen tool—or worse, avoid a recipe altogether—when you could find a new way to achieve the same result?

Some people are of extremely secretive nature. They do not like sharing their personal events in their lives with anyone. Thus people around that person wont be able to figure out details on their life's personal matters. It is not like they want to hide some mysterious secrets from the world, but it is just their nature that they do not want others to know much about them or are too shy to share their feelings with others. Being secretive is neither good nor bad, it is just how they are.

There is no shortage of games for your iPhone, and I'm sure you and your friends are probably sick to death of playing Candy Crush Saga by now. To spice things up, instead of waiting for cool new addicting games to come out, take control and make your own, then share them with your friends.

I don't like a lot of app icons on my home screen. It makes everything on my Nexus 7 feel dense and congested. As a minimalist, I like a simple and well-organized home screen, which is why I regularly utilize my app drawer to launch apps.

Repetitive use of apps over time will eat up your storage space with by caching data on your device. This can be useful at first, speeding up your apps by not requiring them to re-download frequently used data, but as a cache grows, even the initial performance improvements can be outweighed by the unwelcomed loss of storage space. And if a cache grows too large, the time it takes an app to access the cached data can be even slower than the time it would've taken to re-download the data in th...

Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my beginner's guide to hacking Wi-Fi.

Curious about fishing? Looking for an easy pattern to start off with? Check out this instructional video and learn how to tie a simple calf's tail jig. This fishing jig is particularly successful in the fall season.

At a very early age, I would go on summer camping trips. I remember every night being handed a pack of sparklers that were my own, to swing around wildly, which gave me many valuable life lessons on cause and effect.

Before there was Gray's Anatomy, physicians and medical students used anatomical flap books to explore the inner workings of the human body—a scientific illustrated guide that takes its name from the moveable paper flaps that can be "dissected" to reveal hidden anatomy underneath. Similar to pop-up books, these instructional tools mimic the act of human dissection, allowing doctors and students to study the intricacies of the body normally concealed by flesh.
When stories are told about people in need, the ones with happy endings include the details of someone that produced an action that caused the people in need to be better off than before. Do we have to wait for the identification of a need? Could we on purpose just plan to present products and services that cause our customers and client to see an improvement in their circumstances just because of the business interchange with an owner manager of purpose? The fair exchange of products or serv...

It doesn't matter if you're a chocolate lover or just a casual chocolate eater, these chocolate brownie trifles are extremely addictive! If you whip up a batch of these trifles, you're sure to be the king (or queen) of the potluck or dinner party. No doubt about it. Everyone can enjoy a sweet chocolaty dessert.

There's more to playing guitar than just holding it and strumming it. There's a correct way to do things. You need proper posture and you need to hold the guitar correctly, whether you're left-handed or right-handed. Also, you need to hold your guitar pick the right way. This will teach you that. Extremely helpful for any beginner guitar player.

Legumes like pinto beans are not only delicious and a staple in any Mexican meal but are also very healthy for you. They may take a little time to cook from scratch but can be made in large batches with out much effort and are extremely cost effective.

Getting regular cardiovascular exercise is extremely important to maintain good health but it can be difficult to find an exercise that isn't strenuous on the joints. Luckily aqua jogging is a great workout for any age.

No matter what age you are or what kind of life you've lived you can put your story out there by writing an autobiography. Every life can be interesting if written about in a well formulated, and honest manner.

Glitches are everywhere in the video game world, and you can call them what you want... glitches, cheats, cheat codes, hints, secrets or tips. In order to find a glitch, you have to keep your eyes open or follow a recommendation from a gaming friend. Either way, to catch a secret glitch, you need to be ready; the cheats for the taking, whether a weapon or secret passageway, so take it, before it gets patched.