One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

While most people were worried about having the scariest costume when I was younger, I was always more interested in the candy. While everyone wasted time trying to perfect their costume, I was busy mapping out every detail in my city, finding the most efficient way of getting the most candy in my pillowcase(s) before the night ended. Although I'm long retired from the game, it's about time to pass along all of the tips and tricks I've learned from my youth for getting treats. So, here I pres...

Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what applications are installed and running.
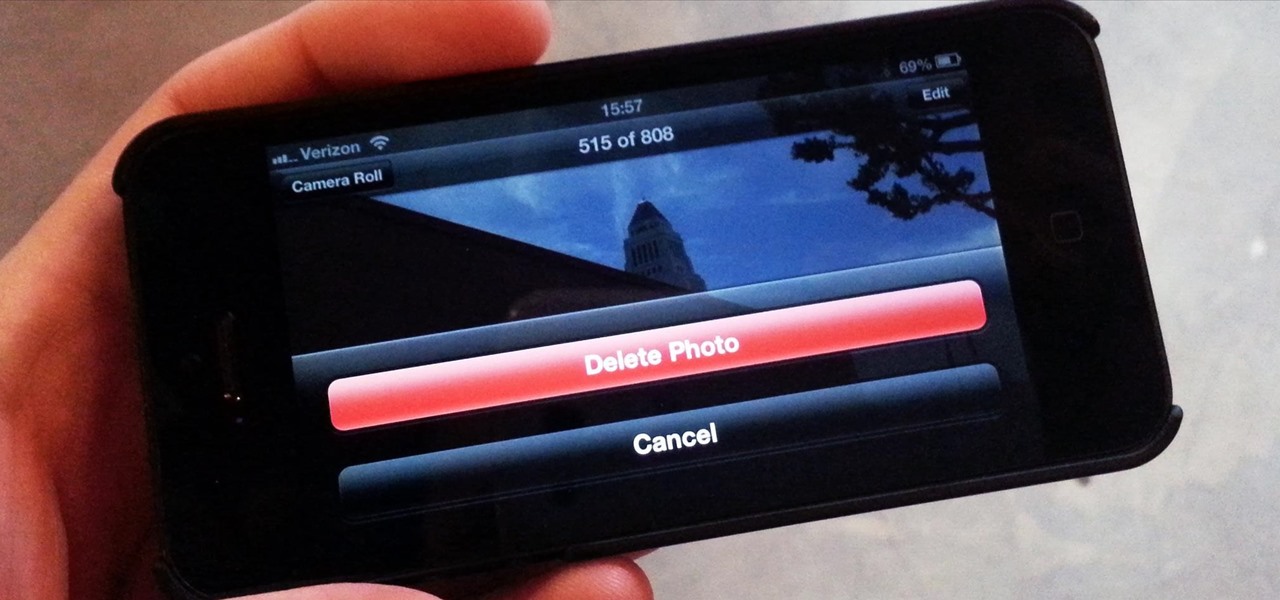
In one of Apple's newer ads, the company claims that "more photos are taken with the iPhone than any other camera." If this is in fact true, then it might also be appropriate to say that more photos are accidentally deleted on iPhones than any other camera.

Most of us have conducted an investigatory science project without even knowing it, or at least without knowing that's what it was called. Most science experiments performed, from elementary to high school students and all the way up to professional scientists, are investigatory projects.

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.

Sometimes, for whatever reason it may be, we just want to take a photo without anyone noticing. Unfortunately, thanks to the extremely large screen and loud shutter sound, taking a picture discreetly with our Samsung Galaxy Note 2 is a hard thing to do.

If I were to lose access to the entire internet for the rest of my life, one of the websites I would miss the most would have to be Wikipedia. Wikipedia has ended countless arguments, informed me of how old and single some of my favorite actresses are, and helped me brush up on thousands of historical topics.

While it's not a highlight of the PlayStation 3, you can actually control the video game console with your smartphone. However, only certain aspects of the PS3 can be controlled from your iPhone, and it's not very obvious what you can and can't do — but that's where we come in.

It's a controversial headline, I know, but bear with me and I'll explain in due course. Disclaimer: I was once a child, and I played lots of video games. I didn't look anything like this child.

Many people find Steampunk problematic for a whole host of reasons, not least of which is the glorification of an era of Western history that featured institutionalized slavery, racism, sexism, elitism, and many more -isms.

There's a lot that goes into making a nice crystal radio set, so this is going to have to be broken down into two parts. The first part is the actual making of a functional radio, and the second part is making the whole arrangement look nice. In this part, I'm actually going to tell you more than just how to make a crystal radio, but I'm also going to explain how and why they work. Crystal radios are pretty Steampunk in and of themselves, since they were first developed in the late 19th centu...

As people continue to upgrade their PCs to Microsoft Windows 8, more and more developers are adding content to the Windows Store. While the offerings are not as vast as Google Play or the iTunes App Store, it does have some solid apps for both productive users and those looking to just while away the time.

I've had a handlebar mustache for about five years now, and I've learned a lot over those years about how to grow and care for it. I will now share all of that information with you! Hopefully this will encourage you to grow one for Movember! The first thing I want to address right now is that I do not use wax on a daily basis. I kind of hate using wax, but I still do it on occasion. I shall teach you my secrets, starting from the beginning!

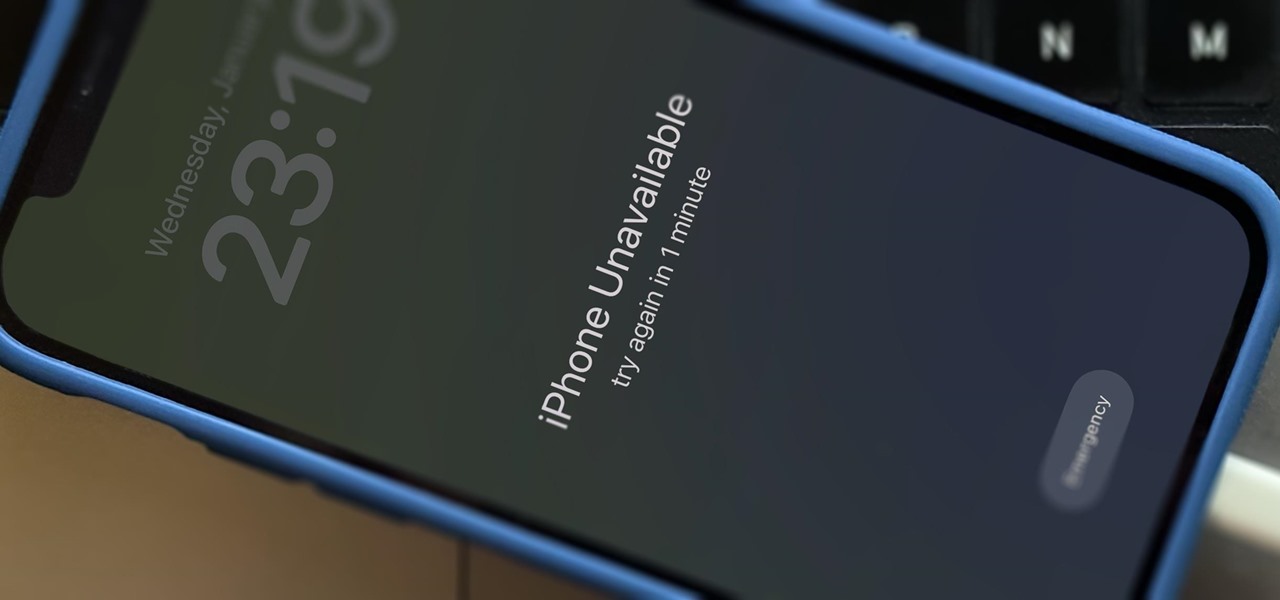
There's only one thing keeping hackers, thieves, law enforcement agencies, and maybe even the people you thought you could trust from breaking into your iPhone should they ever get possession of the device. Their odds of bypassing that thing are pretty good, but there's an easy way to make it an almost impossible feat.

If you have a PlayStation 5 and an Android phone running Android 12, you can stream and play your PS5 games right from your mobile device using PS Remote Play. While simply pairing your PS5's DualSense wireless controller with your phone will give you the basic controls to play third-party games, Remote Play takes a little bit more work to set up.

Billionaire Richard Branson did his part to advance space tourism this weekend by beating Elon Musk (SpaceX) and Jeff Bezos (Blue Origin) to become the first among them to travel into space.

While Touch ID has been a part of the iPhone's legacy since 2013, Apple waited until 2016 to add biometrics to its MacBook lineup, and it's not as impressive. An iPhone with Touch ID can register up to five fingerprints, but Macs can only register a maximum of three per account. If that seems unfair, there's an easy trick to doubling that number, meaning six of your fingerprints could unlock your laptop!

The internet is saturated with low-quality pictures, making it difficult to find a high-resolution image for specific albums, TV shows, movies, podcasts, music videos, apps, and books. Apple uses high-quality images, but it seems impossible to download cover art, posters, thumbnails, icons, and other images from within its apps on your iPhone. Now, with the help of a shortcut, it's as simple as can be.

Enter a password into a password field, and it's a sure bet that black dots or asterisks will obscure the characters. Nearly every website you visit in Safari on your iPhone will do it, but sometimes it helps to see what you're typing or what was auto-filled with iCloud Keychain, LastPass, or a different password manager.

I've been steadily making my way through the series Hannibal, which arrived on Netflix in June. I've just now made it to the back half of the third season, which introduces us to a new villain who (spoiler alert) seeks to become the Great Red Dragon.

Hackers often find fascinating files in the most ordinary of places, one of those being FTP servers. Sometimes, luck will prevail, and anonymous logins will be enabled, meaning anyone can just log in. But more often than not, a valid username and password will be required. But there are several methods to brute-force FTP credentials and gain server access.

It's safe to say that we can call the annual ranking of AR investments a holiday tradition at Next Reality.

Apple's iOS 13 for iPhone includes new features in Safari that make browsing the web a little bit better when compared to iOS 12. Some changes are small while others add functionality that just wasn't there before. Plus, there are more security enhancements.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn from in past discussions. We've dug through the last ten years and found the 15 most popular talks you should watch.

The hugely successful S10 series of flagships may be a tough act to follow, but Samsung has proven that it's up to the task with the Galaxy Note 10. The latest phablet bearing the Note name is the first of its line to come with an even larger variant, and boasts an eye-pleasing design with impressive performance to boot.

You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discover other devices on the same network.

Apple CEO Tim Cook has said that augmented reality (or, AR for short) will "change everything." But what, exactly, is augmented reality?

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

The year 2018 was a rough one for Snap, the company behind the Snapchat app and the Spectacles wearable camera device. From executive departures to reports of slowed user growth, the company that once spurned Facebook's multibillion-dollar advances is now facing a moment of truth as it stares down its uncertain future.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

This time last year, we got our first taste of what mobile app developers could do in augmented reality with Apple's ARKit. Most people had never heard of Animojis. Google's AR platform was still Tango. Snapchat introduced its World Lens AR experiences. Most mobile AR experiences existing in the wild were marker-based offerings from the likes of Blippar and Zappar or generic Pokémon GO knock-offs.

When you can't reach your iPhone or don't have it on you, how do you get help from emergency services? Unless you have one of those life-alert mobile triggers, someone nearby, or some amazing telepathy skills, hope might be the only answer — unless you wear an Apple Watch, that is.

Web applications are becoming more and more popular, replacing traditional desktop programs at an accelerated rate. With all these new apps out on the web comes various security implications associated with being connected to the internet where anyone can poke and prod at them. One of the simplest, yet the most prevalent types of security flaws found in modern web apps are SQL injections.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Throughout this NR50 series, we have talked about the incredible growth the augmented and mixed reality space has seen in the last year. More devices, software, developers, and use-cases seem to arrive daily. For this growth to have occurred, it took the work of many people, from many different backgrounds and skill sets — and Next Reality wants to recognize them for all that they have done and are doing.

Codenamed "Nougat" after the sugary stuff that fills your Snickers bar, Android 7.0 is living up to its name with tons of sweet features. There's almost too many changes over Marshmallow to cover in one go, with new functionality ranging from a revamped Doze Mode for battery saving, to split-screen apps, and even an easier update process. All told, the Nougat update has a lot in store for your phone or tablet.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.