You can find a ton of live wallpapers for your Android device on Google Play, but the more alluring interactive ones are a harder to come by, which can bring your home screen to life using a few finger swipes and taps.

If you thought humans were reading your résumé, think again. Robots do, and their one solitary objective is to systematically crush the hopes and dreams of those who don't make the cut. Instead of paying a few humans to read thousands of résumés over a couple weeks, many companies use computer programs that can do the job in less than an hour. In fact, at least 90 percent of Fortune 500 companies use what they call an applicant-tracking system, aka rejection machines.

Of the hundreds of uses for our devices, the one that I cherish most is the ability to kill time just about whenever and wherever I need to. Whether it's reading news, checking social media, or watching videos, we have a ton of ways to pass the time in that two-hour DMV line or dentist's waiting room.

Food can smell great before, during, and after cooking. A pot of stew simmering away on the stove will tantalize you all afternoon, and there's nothing better than the smell of fresh-baked cookies lingering in the house for hours.

The U.S. Postal Service has been in trouble for quite some time. With more and more people choosing to go digital to take care of bills, legal documents, and pretty much all other forms of correspondence, they haven't exactly kept up with the times. I mean, let's be honest—when was the last time you sent snail mail?

The art of persuasion is a very crucial characteristic that anyone can learn, and it has countless benefits. Whether it's at work, home, or in social situations, the ability to be veritably persuasive can have an unheralded impact on your daily life.

If you haven't walked into a department store or seen one of those millions of jewelry commercials airing over the last month, you might not know that February 14th is Valentine's Day.

It's almost here. Another year has come and gone, and it's time to watch the Baltimore Ravens and the San Francisco 49ers battle it out in New Orleans for Super Bowl XLVII. For the truly football-obsessed, this Sunday is a day almost as exciting as Christmas. Personally, I just use it as an excuse to cook food that's way less healthy than usual since I never quite became a football fan (sorry, Dad).

Many people that I know who have gone to see the Hobbit have come back unimpressed or annoyed with the film. I LOVED it. When those non-specific people, cough Loziers cough, gave me their reasons for not liking the movie, I was very annoyed... I considered the demands that they were placing on Peter Jackson and his team to be very high and unreasonable. So, as a method of venting my anger, here is how to watch the Hobbit. If you’ve read Lord of the Rings and the Hobbit, please, go back, and R...

Like most new things, the Start Screen in Windows 8 has its adorers and detractors, but either way you slice it—it's here to stay. I'm still getting used to the Start Screen, so I'm not sure if it's a love or hate feeling yet, but I do know one thing—I want my own background!

You may or may not care about this, but sometimes it physically upsets me when I see gears stuck together haphazardly, with no concern for whether their teeth interlock. I mean, what do you do with non-interlocking gears?

There's definitely a lot of new things to get used to in iOS 6, with over 200 added features, but which ones stand out about the rest? Well, it all depends on what device you're using. Some features will only work on newer models, but most of the hidden features are accessible to all.

It's September 1st, 1859, and the Earth looks more or less like something out of an apocalyptic movie or Sci-Fi novel. All communications have failed, it's so bright outside at midnight that people are getting up and making breakfast, and people all over the world are seeing auroras. The solar storm that produced the electromagnetic pulse and caused all this mayhem is known as the Carrington Event, and storms like it happen about about once every century.

Of all the places you'd think to check for bed bugs, I doubt that library books would be at the top of your list. As odd as it sounds, though, libraries and library books are some of the most common places for bed bug infestations. Libraries all over the country have reported bed bug problems this summer, and some have even had to temporarily close to take care of the problem. But before you vow to never set foot inside a library again, here's a little primer on how to check your books for be...

Say whatever you want, but Steampunk is primarily a maker culture. Consider that Steampunk has existed since the 1960s and yet more or less languished in obscurity until approximately 2005, which is when it made the leap to costuming. That costuming was what provided the leap to the tangible, despite the fact that Steampunk art had also existed for years.

Let's face it—if you care about anyone around you, then you brush your teeth. Brushing is an excellent way to not only prevent tooth decay, but to keep people from running away from you with their noses pinched.

Hello! This tutorial is made for all who like to sunbath, but also do not want to get those tiny first wrinkles too soon. Or even skin cancer.

Brushing your teeth is a necessity. You don't want to walk around with yellow teeth and stinky breath, and it's common courtesy to those around you to care about your personal hygiene at least that much.

The introduction of smartphones has been what some may see as a step backwards in technology regarding batteries. The first cell phone that I had would last 3-4 days on a single charge; however, the lack of functions minimized the use that is saw.

OSAGYEFO DR. KWAME NKRUMAH (1909-72) Founder and Father of the Nation Osagyefo Dr. Kwame Nkrumah, the first Prime Minister and President of Ghana, stands out not only among the Big Six but also among the greatest statesmen of history. It was he who canalized the discontent of the people of the Gold Coast Colony into the highly organized movement of protest against British rule, and within a relatively short period won political independence for Ghana on March 6, 1957. With Ghana independent, ...

In this article, I'll be explaining the basics of how microcontrollers work, physically and virtually. First off, microcontrollers are no simple thing, so don't be discouraged if you find it mind-boggling! The world of microcontrollers is fascinating, engaging, and an awesome hobby; it never gets boring. I'll be focusing more on I/O and analog based microcontrollers, such as those running Arduino, and using Atmel chips as examples (these are most commonly available, and easy to program).

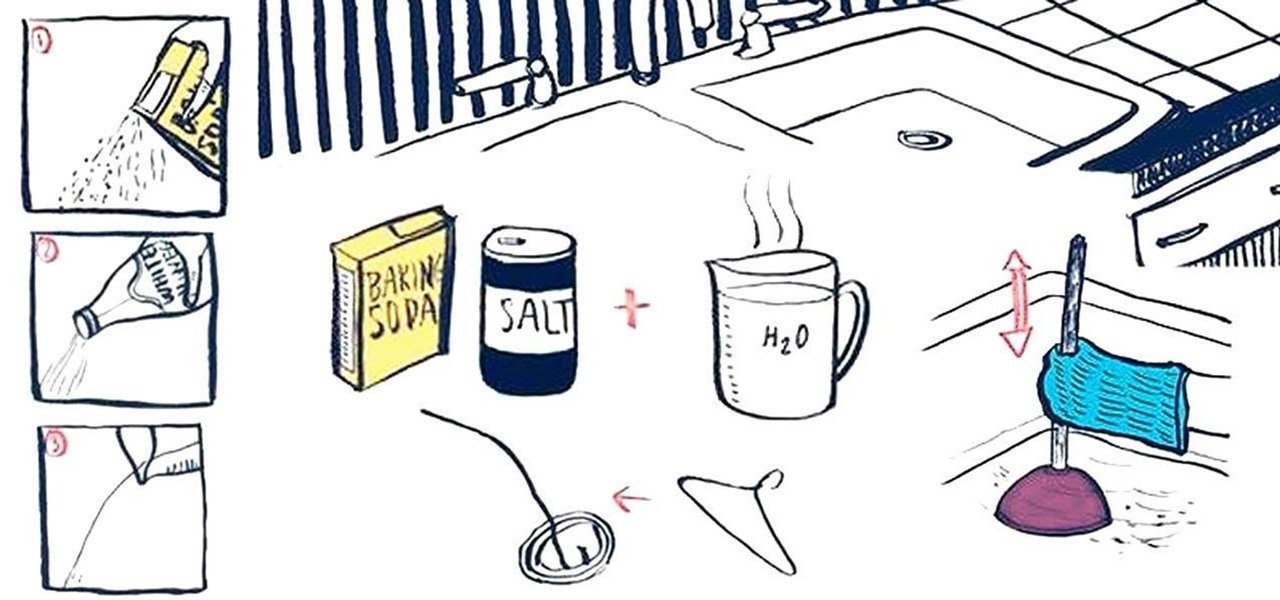
Oh, boy. A stopped-up drain. It'll inevitably happen with any home plumbing system and your kitchen sink is no exception. That clog won't go away on its own and will require immediate attention to keep any standing water from rising. But you don't have to resort to calling an expensive plumber or using a bottle of hazardous chemicals. Using simple kitchen staples or common household objects, as well as some determination, you can unclog your kitchen sink on your own without paying a dime.

It's been done for ages, but for most of us, "regift" entered our vocabulary after the 98th episode of Seinfeld—"The Label Maker." In this episode, Elaine calls Dr. Whatley (played by Bryan Cranston) a "regifter" after he gives Jerry a label maker—the same label maker that Elaine gave Whatley.

If you're trying to decide if you should get a chemical peel, or if you've decided to get one but don't know where to start, this series will show you how to prepare for, how to get a chemical peel and how to care for your skin afterwards.

Hugo Guias shows how to do a "back mobe" on a kiteboard.

In this video clip series, our expert will demonstrate several first aid techniques that can easily be done to treat minor injuries and basic situations that you might find yourself afflicted with. Bee sting treatment, abrasion care, blister care and more.

For a car to operate normally, it must have some basic care and maintenance. In these automotive repair videos, learn how to maintain your engine cooling system. The cooling system keeps your car from overheating on the road; a lot of heat is generated by an internal combustion engine, which must be properly dissipated. Our expert will show you how to not only spot and remove the heater core hose in a car but how to determine what is wrong with it, change it if needed and reassemble the vehic...

n this video series, let Mickey Denoncourt show you how to take care of road bikes. He shows you the important differences between a road bike and other bicycles. Mickey illustrates gear constructions of road bikes, and he offers advice for repairing and shifting these gears. Also, learn when to replace your bicycle tires as well. If long bike rides are your fancy, learn how to take care of your own road bike today!

Since the start of the COVID-19 pandemic, Google has packed new functionality into Google Meet to compete with Zoom, Microsoft Teams, and other video conferencing platforms.

The movie theater business is hurting due to the pandemic, but that hurdle is actually the perfect set of circumstances for movie studios to lean hard into augmented reality marketing.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

A good smartphone can be the perfect workout companion. You have music for motivation, videos for pushing through boring cardio sessions, GPS to keep you on course, and even an array of sensors for gathering data about your workout. But not all phones are created equal when it comes to helping you stay fit.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

It's always a big deal when the company that makes Android releases a new phone. Google's Pixel series has made a name for itself in three short years behind its camera prowess, but now it's time to start competing with the major players. That said, Google should like how their Pixel 4 and 4 XL stack up against the iPhones and Galaxies of the world.

Apple has packed a lot of new features into the iOS 13 update, and practically no core app has gone untouched. The Messages app, in particular, got plenty of love, including new ways to dress and use your Memojis.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

While hackers know and love the Raspberry Pi, many don't know of its cheaper cousin, the microcontroller. Unlike a Pi, which can be used more or less like a regular computer, microcontrollers like the Wi-Fi connected ESP8266 require some necessary programming skill to master. In this guide, we'll build an Arduino program from scratch and explain the code structure in a way anyone can understand.

Next to Apple, Snap is currently one of the most important companies on the planet in terms of delivering products that are moving augmented reality into the mainstream. That's why it's no surprise that Facebook, which is also focused on AR and tried to acquire the company for $3 billion several years ago, duplicates many of the smaller company's features.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.