Recognizing the signs of schizophrenia is the fist step toward getting help and proper treat for a loved one with this serious mental health affliction. With proper medication and therapy schizophrenia can be controlled so check for and understand what to look for.

Learn the ancient method of threading in order to get rid of unwanted facial hair.

This video will show various ways to get rid of blackheads. The first step in all of these various techniques involves steaming your face. This will allow your pores to open, which will enable to blackheads to come out more easily. First of all, you may use a blackhead removal tool, which is a metal tool which you can use to remove blackheads individually. Other techniques include pore strips, which you apply on your face when wet and pull off after it had hardened and dried, taking blackhead...

The team at blackhead no more demonstrates how to quickly and easily remove stubborn blackheads from the nose, using a unique product called BLAKhead Masque. If you've ever had acne like this, this video can help you. BLAKhead Masque is applied much like any other facial mask, hardens like a wax and extracts your blackheads much the same way as waxing body hair, without the painful hair pulling process. This product works on both men and women, and can make life easier for those with this typ...

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

Over the past decade, Marvel Studios has been a dominant force at the box office, raking in more than $21 billion dollars. Averaged out over that span of time, the yearly earnings of those movies outweigh the gross domestic product of some countries.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

Apple CEO Tim Cook has said that augmented reality (or, AR for short) will "change everything." But what, exactly, is augmented reality?

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

When it's all said and done, it doesn't really matter who did it first — the more important question is who did it best. Still, it's nice to know who's really responsible for groundbreaking innovations in the smartphone space.

Before you go ahead and delete your Facebook — don't lie, you've been thinking about it — consider this. Facebook offers users a wide variety of privacy options to mess with, which can help you find a little control over your information. We're not saying this solves Facebook's privacy crisis, but it might be a more reasonable option than throwing in the towel entirely.

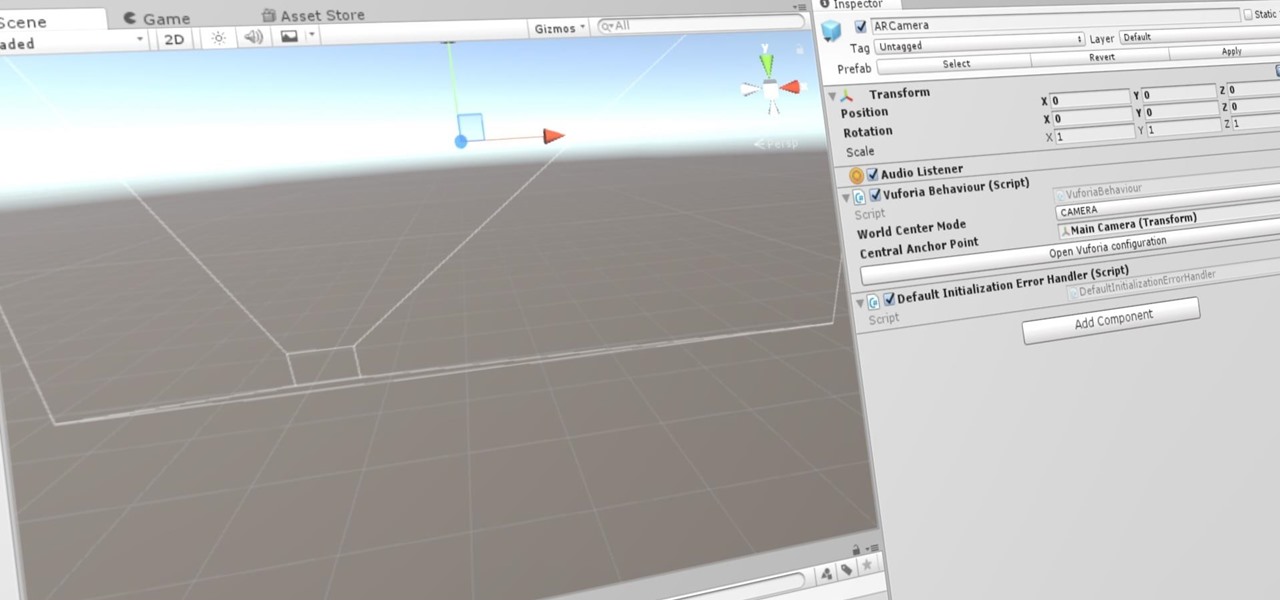
Now that we've set up Vuforia in Unity, we can work on the more exciting aspects of making physical objects come to life on the HoloLens. In this guide, we will choose an image (something that you physically have in your home), build our ImageTarget database, and then set up our Unity camera to be able to recognize the chosen image so that it can overlay the 3D holographic effect on top of it.
As a hacker or an aspiring one, You need to be careful and anonymous if your doing anything illegal. But you slipped up. Now someone is tracking you! Well luckily you read this post ahead of time and have a backup plan!

Alopecia is also known as hair loss. he most common form of alopecia or hair loss that we see is alopecia areata. It usually shows itself as round patches of hair loss on the scalp, however, it can affect the facial hair and body hair. Learn some tips on how to slow and treat the loss of hair in this medical how-to video.

Personification of the Infinite Consciousness. Lord of Hosts. Master of the Universe. These are just three of the hundred-odd titles of the Hindu god Ganesha. Luckily, drawing the Hindu deity Ganesha isn't so complicated.

With Adobe Photoshop on your computer, it's super easy to change or adjust the skin tone of somebody in a digital photo. The process uses some basic selection and color adjustment tools, and it's a fun way to make a friend's face nauseously green or lessen the effects of overly strong, sometimes even orange, makeup.

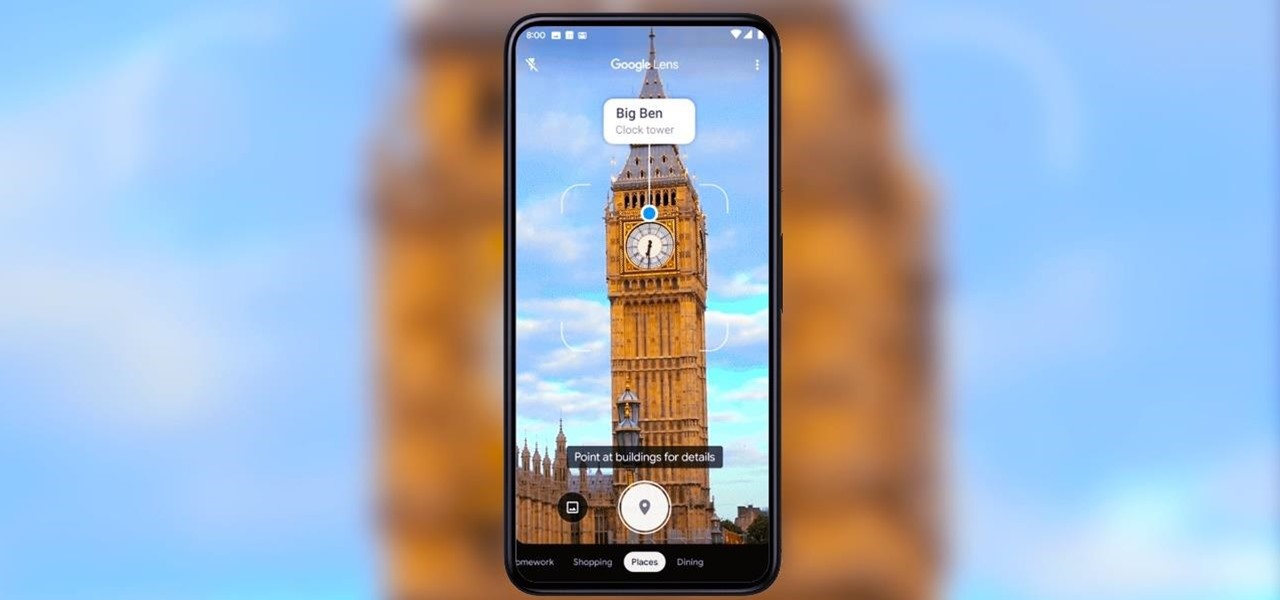
This week, Apple unveiled its own version of Google Lens in the form of Live Text. In response, Google just hit back with a new feature for its visual search tool called Places, a new search category that can recognize landmarks and return information on them within the camera view, which Apple touted as a capability of Live Text during its WWDC keynote.

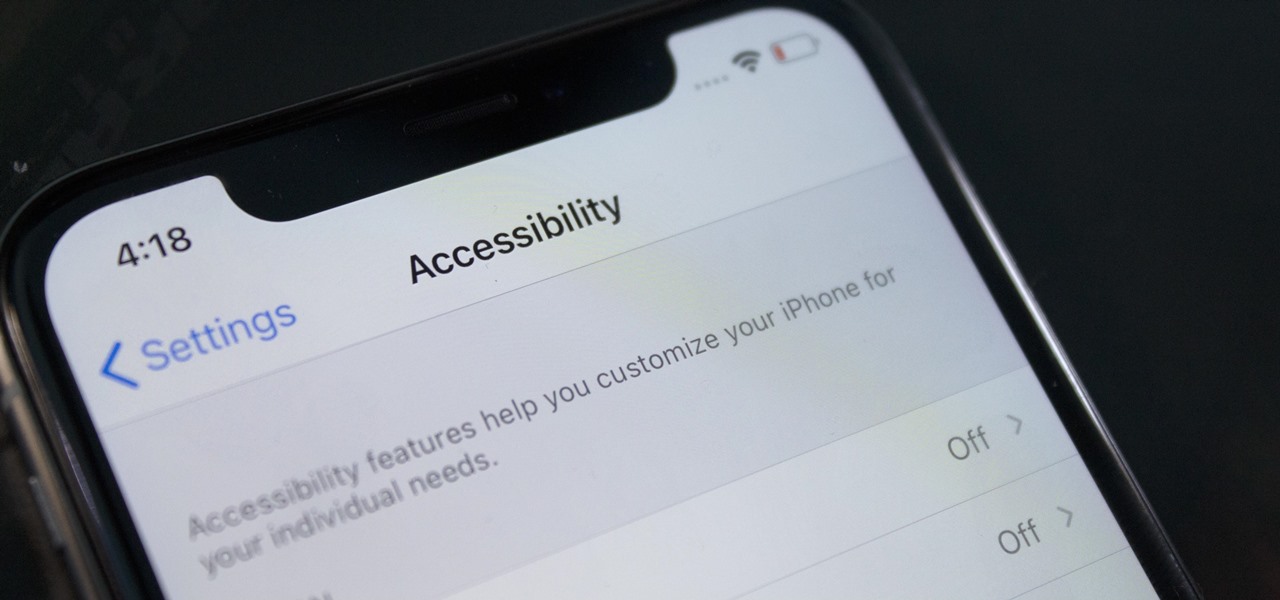
According to the CDC, one in four U.S. adults has a disability, where limitations can involve vision, cognitive function, hearing, motor skills, and more. That's why the iPhone has accessibility features; so that everyone can use an iPhone, not just those without any impairments. Apple's iOS 14 has only made the iPhone even more accessible, and the new tools benefit everyone, not just those that need them.

Smartphones are more like computers than actual telephones. Unfortunately, thieves, hackers, and other bad actors know this and are always looking to make money off your personal data. Thankfully, your Galaxy S20, S20+, or S20 Ultra has tools to combat these threats — as long as you know where to look.

Now that the dust has finally settled on Microsoft's big HoloLens 2 announcement, the company is circling back to offer more granular detail on some aspects of the device we still don't know about.

One could argue that, at least for the moment, software development is more important to the augmented reality experience than hardware. Since a viable augmented reality headset has yet to emerge for the broader, mainstream consumer market, currently, the same devices that make texting and selfies possible are leading the charge to enable easy-to-use AR experiences.

LG is really coming strong at the flagship smartphone market in 2018. They have already released three new flagship caliber smartphones this year: the V30S ThinQ, V35 ThinQ, and the G7 ThinQ. But LG isn't done with flagship phones yet — they've just announced the V40 ThinQ.

Contrary to popular belief, augmented reality apps have been available for a while now. I remember using the Layar app (still available for iOS and Android) to explore nearby businesses and landmarks with varying success via an early-generation Android handset.

A picture is worth a thousand words, and depending on what you're taking a picture of, it could be worth a lot more. Our phone's camera can easily capture high quality photos, scan barcodes, and make us Instagram famous. You can compare prices of items and download applications just by scanning a QR code. Of course, we can always do this stuff a little bit better on our iPhones.

Over the past few months, Google has prioritized the development of its video communications products as the demand for social distancing solutions continues to increase in response to the COVID-19 pandemic.

Silicon Valley-based startup 8th Wall has spent much of the last few years building a reputation for enabling AR experiences that are platform agnostic via web browsers and mobile apps. Now, 8th Wall is promising to give developers the freedom to build and host AR experiences from anywhere via a simple web browser.

With the imminent arrival of the HoloLens 2 expected any day now, Microsoft is preparing new users to take advantage of its software from day one.

Former soccer star and current celebrity David Beckham has the augmented reality abilities of Facebook and Instagram as allies in the effort to eradicate malaria from the world.

Although early attempts at consumer smartglasses have employed trackpads and handheld or wearable controllers for user input, its the gesture control interfaces of the HoloLens 2 and the Magic Leap One that represent the future of smartglasses input.

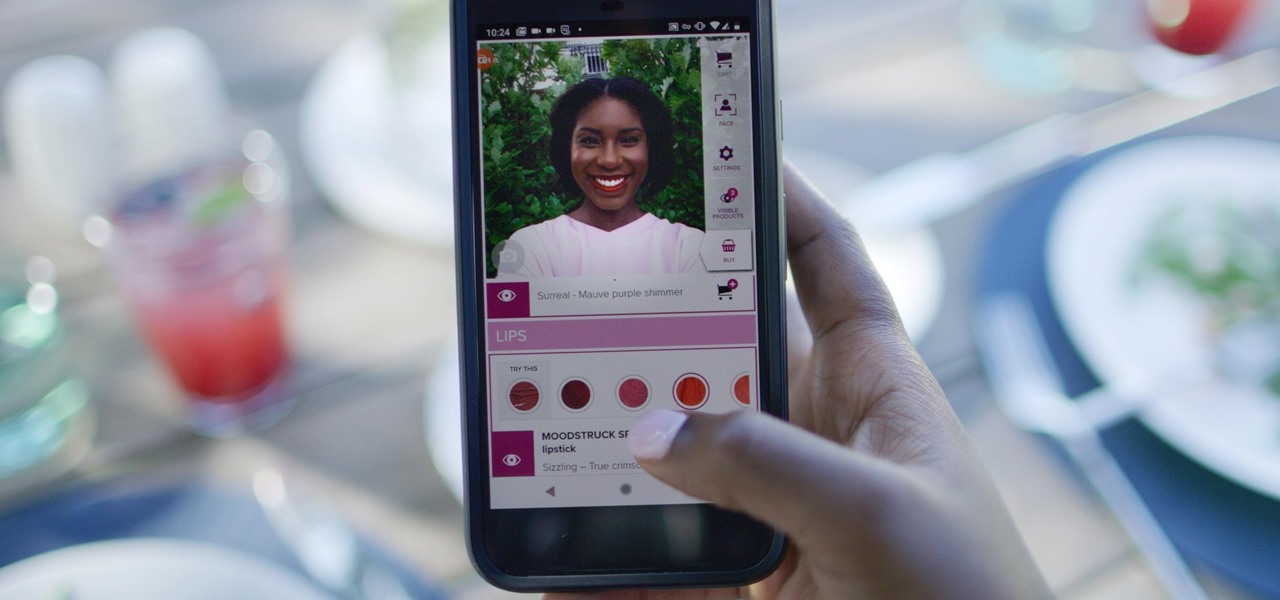
Now that some of the best-known beauty brands are leveraging augmented reality to market and sell products, the rest of the market is beginning to catch up — fast. The latest competitor to add AR to its arsenal is direct sales makeup company Younique.

Closed captions are great for watching YouTube videos on mute, or simply following along with a video that's hard to understand. It's easy to turn on captions on YouTube's desktop site, but in the YouTube Android app, the closed captions settings are tucked away.

The recent industry whispers in augmented reality are mostly about Apple and its rumored fashion-friendly smartglasses, but one company isn't waiting for the iPhone heavyweight to enter the fray.

Like clockwork, Apple has unveiled the latest additions to its ARKit tookit at the annual Worldwide Developers Conference, where ARKit first said hello to the world in 2017, as well as some new tools that take a direct shot at Unity, Unreal Engine, and others.

After a rough run of news, smartglasses maker North still has the confidence of investors, as evidenced by its latest round of funding.

Because of its ability to place digital content into the real world, augmented reality lends itself well to artists and creatives.

We've seen a variety of AR experiences related to athletic footwear over the years, but Puma is betting sneakerheads will buy into a version of interactive design where sneakers are the augmented reality experience

Last week at Mobile World Congress 2019, Google put an augmented reality twist on its annual Android Partner Walk via its ARCore toolkit.