Despite its status as a hot commodity amongst emerging technologies, the augmented reality industry is not immune to the ebbs and flows that occur in every industry.

The dream of Google Glass lives on via North's stylish and normal-looking smartglasses that bring text messages and navigation prompts into the user's field of view and Amazon Alexa integration for voice-activated assistance.
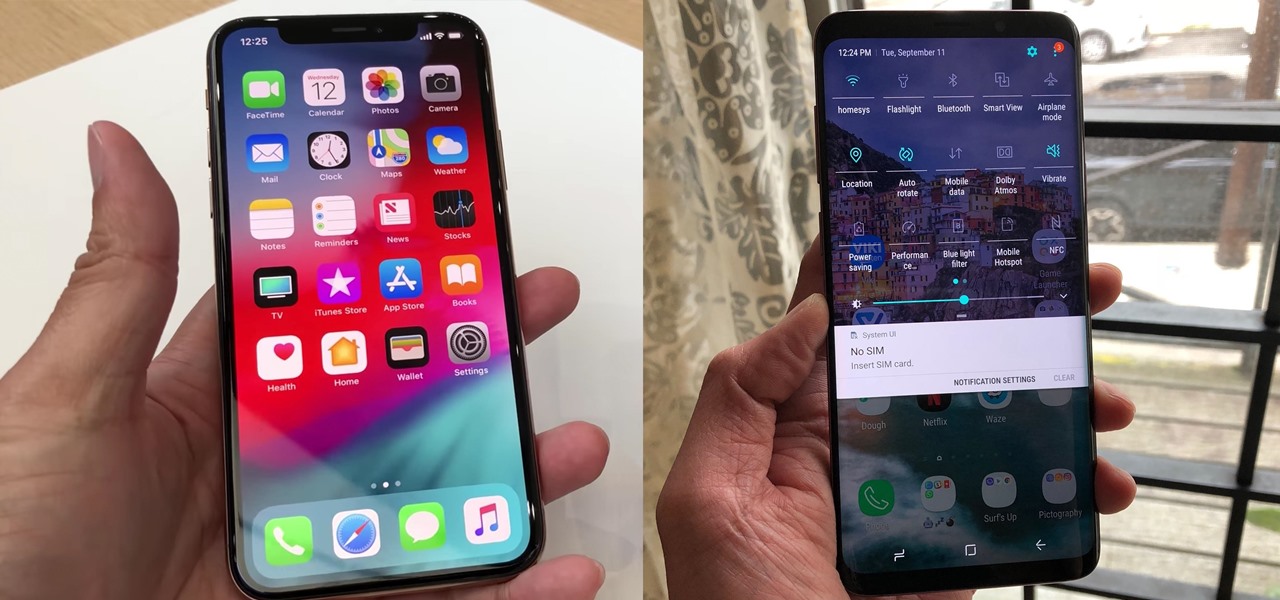
Until next March, the iPhone XS and Samsung Galaxy S9 will be the only phones considered by many. Whether you're an Apple fan wanting to see how your new phone stacks up against the competition or a buyer on the fence, here's how the latest flagships from the two biggest brands compare.

It doesn't matter how cool or groundbreaking a particular technology is, if it doesn't offer the promise of big returns on investments, you'll have trouble drawing interest from both Silicon Valley and Wall Street. That's why we're increasingly seeing existing augmented reality players doing everything they can to focus in on revenue generation, which was the message coming from Snap Inc. this week.

The OnePlus 5T was just released, and it's packing several new useful features. While many OnePlus 5 buyers are feeling frustrated with the quick release cycle, lots of fans are still clamoring to buy the new device. Aside from the larger screen, most of the buzz around the 5T has centered around the new face unlock method. Thanks to a clever hack, you can now get this feature on almost any phone!

If preorder delays are any indication, the iPhone X certainly has some buzz. But does the X have the quality to support that buzz in the long run? After all, a $1,000 (or more) iPhone feels more like an investment than a smartphone purchase. The question on any prospective buyer's mind should be, "Is this thing worth it?"

While IKEA is collaborating with Apple for its ARKit furniture app, Marxent is ready to help the rest of the interior decorating and home improvement crowd with their apps.

At the moment, it would be safe to say that demand for devices running Tango, Google's augmented reality smartphone platform, is relatively low among consumers. Kaon Interactive, a B2B software company who has built more than 5,000 interactive applications for use at trade shows, remote sales demonstrations, and other customer engagements, is betting that there is a market for the devices in sales and marketing.

For years, smartphone makers have been caught up in a megapixel spec race to prove that their camera is better than the next guy's. But we've finally come to a point where even the lower-end camera phones are packing more megapixels than they need, so it's getting harder to differentiate camera hardware.

There are so many cutesy pink, red, and heart-shaped desserts and drinks put out on Valentine's Day, but none of those really get you into a low-light mood. Instead, turn up the heat with one of these aphrodisiac cocktails for grown-ups.

As practically the entire Steampunk world knows by now, IBM has predicted that Steampunk will be the big new trend from 2013 to 2015. They based this prediction on their computers, which sift through broad swathes of the internet in order to see patterns that may help commercial industries. According to them, Steampunk has been on the rise for the last few years, and they predict that it will explode into peak popularity within the next two years. But what does that mean and how will it impac...

You can feel it in your bones. You may die if you don't get this phone. There's just one problem — the price. Suddenly, you come across what seems like manna from heaven. That very device, at a deeply discounted rate, can be yours.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

Steampunk is a tremendously interesting phenomenon because of its reliance on science fiction, and fiction in general. Steampunk can arguably be broken down into two categories: the fiction, and the aesthetic. Sometimes these categories cross over, but they're often more distinct than most people suspect; that said, the aesthetic is firmly based in works of fiction.

Are you thinking about upgrading your iPhone this year? Apple sure wants you to. Of course, that's no different than any other year, but Apple really wants you to upgrade this year. How do we know this? The rumors point to not three, not four, but five brand new iPhones in 2020, with two very different release schedules. All this begs the question what the hell is Apple thinking?

Indian startup Dimension NXG is launching augmented reality headsets into India's consumer market with a bold idea: focusing on immersive computing in education on the high-end. The plan is to give a new kind of AR headset to schoolchildren in remote Indian villages, starting from class 5 (age 10) until graduation.

While Microsoft dominated the augmented reality news at this year's Mobile World Congress, a small AR startup we've covered in the past arrived in Barcelona, Spain, to unveil the next phase of its mission.

Like many things associated with Magic Leap, the start of the company's first annual L.E.A.P. conference got off to a unique start. Taking the stage on Wednesday morning in Los Angeles, the company's CEO, Rony Abovitz, gave a brief introductory speech welcoming the crowd and outlining the mission of Magic Leap.

The gig economy is thriving, and if you aren't already making money with your phone, you could be missing out on easy residual income. Some people just want extra cash, and some even manage to completely ditch the 9–5, enabling them to work at their own pace and set their own hours.

Apple has introduced a special edition iPhone 8 and 8 Plus to bring attention to the ongoing worldwide battle against AIDS. As the second iPhones to carry the (PRODUCT)RED name, these rare iPhones may quickly sell out when preorders open up on Tuesday, April 10, at 5:30 a.m. (PDT), so we'll go over some tips to help you secure a red iPhone before it's gone.

If bezel-less was the goal of OEMs in 2017, 2018 seems to be the year of the notch. Thanks in no small part to Apple's iPhone X, more and more smartphone manufacturers are designing their displays with this polarizing cutout. While many are frustrated with the trend, it's worth taking the time to consider what each phone gains with the unique design.

While everyone was marveling at the latest drama over at Magic Leap involving employees last week, a major rumor listed in one of the reports, related to the company's flagship device, was mostly overlooked.

Hackers can be notoriously difficult to buy gifts for, so we've curated a list of the top 20 most popular items Null Byte readers are buying during their ethical-hacking studies. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2017 selection of hacker holiday gifts — just in time for Christmas.

Update 10/23: The hits just keep on coming. We're now seeing reports of a "smearing" effect when scrolling through apps on the Pixel XL 2. We'll expand on that at the bottom of this article, but it's still worth reading the background information on issues with LG's new POLED displays.

Apple just unveiled a red iPhone and iPhone 7 Plus, dubbed the iPhone 7 (PRODUCT)RED Special Edition, to commemorate the ongoing global fight against AIDS. Apple fans the world over are sure to swarm in and gobble up the initial stock shortly after the new color is released at 8:01 a.m. (PDT) on March 24, 2017, so we'll go over some tips to help you secure a red iPhone before it's sold out.

Google's former Self-Driving Car project, now graduated from Alphabet's X division as Waymo, has found a collaborator and potential new partner in Honda. This is an interesting turn of events given traditional automakers' reluctance to work with driverless-car startups over the years.

I've seen my fair share of heartbreaks when it comes to used phones. As a repair tech, I often had to try and help out customers who bought used handsets which turned out to be useless, either because it was stolen or not working on their carrier's network. More often than not, there was very little I could do. To help you from being stuck in the same situation, here are some tips to prevent you from getting scammed out of your hard earned money when buying a used handset.

When shopping for a new smartphone, you'll encounter comparisons and spec sheets that are filled to the brim with values like mAh, GB, and GHz. To the average consumer, however, these values are meaningless, so we end up looking at which device has the specs with the highest actual numbers.

"It just ticked me off," he said. In March 2011, Neil Singh paid $50 to back the Hanfree iPad stand on Kickstarter. The project was funded at $35,000, but production stalled, and the delivery estimates kept getting pushed back.

The long rumored and recently leaked Amazon phone has finally been unveiled, and in the interest of branding, continues down the Fire line—the Amazon Fire Phone. You can check out the full reveal here (warning: it's long), but I'll take you through all the features that sets this device apart from the rest. Before we get into that though, let's check out the specs:

Even the biggest fan of Mario Kart may have reservations about traveling to Super Nintendo World in Japan in the middle of a worldwide pandemic to experience the augmented reality-enhanced roller coaster ride that recreates the game in real life.

Thanks to ever more powerful smartphones — the iPhone X with its advanced A11 processor and the Galaxy Note 8 powered by Snapdragon's 835 come to mind — the mobile industry is fast closing in on consoles and PCs with regards to gaming. Game developers have been aware of this fact, and have ported many games once dedicated to computers onto our handheld devices.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

Not all Kickstarters are created equal. Some take forever to get their products to supporters, and when the product does arrive (usually much later than promised) it's often very rough around the edges.

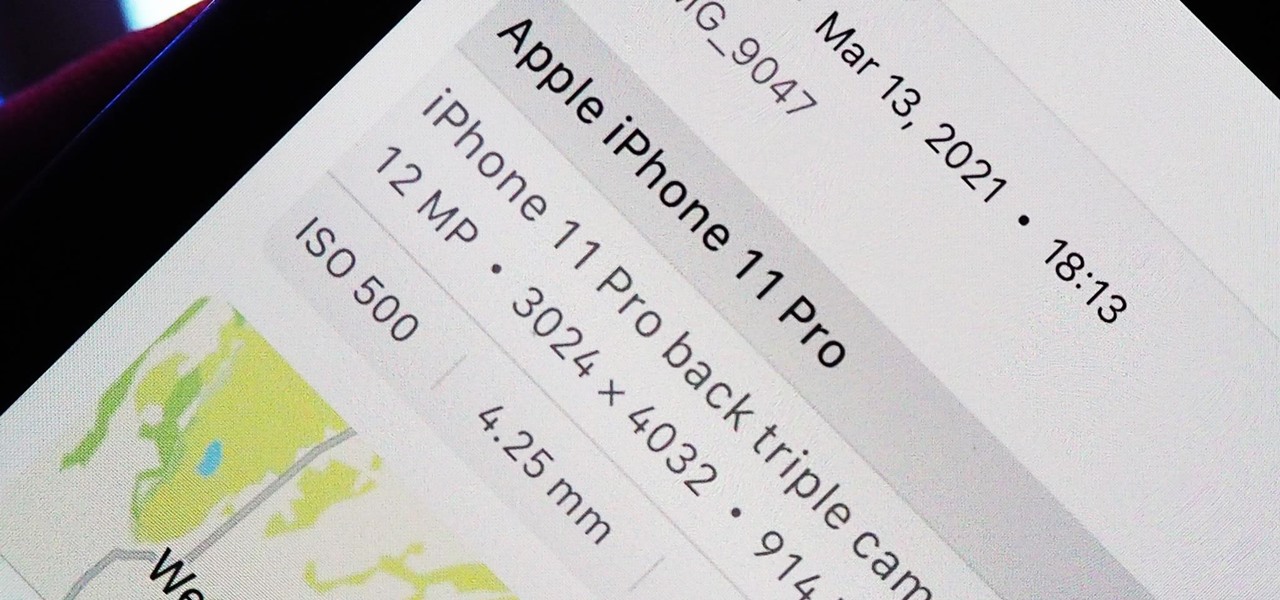
Apple introduces several new privacy settings with iOS 15, including the ability to better manage the metadata in your photos. With just a few taps, you can effectively spoof a photo's geolocation and change its creation date and time, providing a sort of disguise over your personal information. If you constantly take and share photos, it's a welcomed feature, but its results are not permanent and can be reversed.

At its height, the COVID-19 pandemic forced many auto showrooms to close their doors. As the pandemic persists, many consumers are still hesitant to let their socially distanced guard down.

The landscape of the augmented reality space is broad, diverse, and constantly shifting, perhaps more so than any other vertical in technology. At the same time, major players are attempting to standardize various hardware designs and delivery methods, while still others are rushing to claim their piece of virtual property through AR clouds and application stores.

Here at Next Reality, our typical approach to all things augmented reality involves vision combined with remote control, either via a handheld device, gaze control, or hand/finger tracking.

For 2019, Sony is trying to shake its failures of the past and start fresh. Following the unsuccessful Xperia XZ series, Sony is changing the name of their flagship to a single number: Xperia 1. With the name change comes a few upgrades, one of which is its new look. Secondly, its new display is unmatched in the mobile space.

For the uninitiated, it can be difficult to buy that special hacker in your life a perfect holiday gift. That's why we've taken out the guesswork and curated a list of the top 20 most popular items our readers are buying. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2018 selection of hacker holiday gifts.