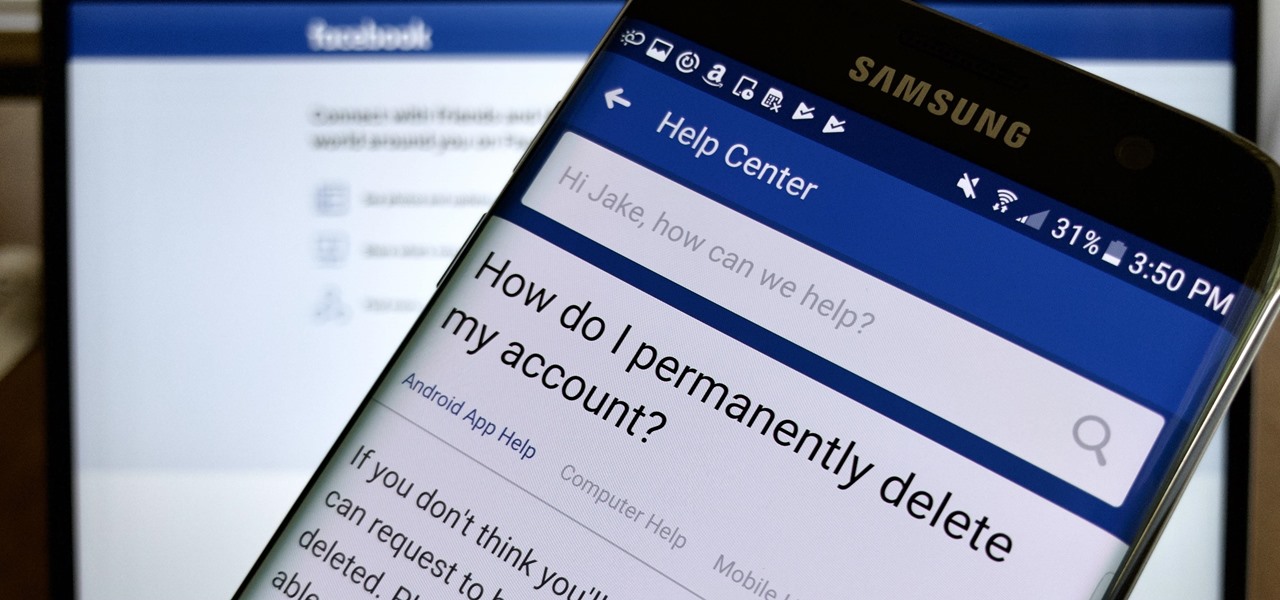
With the news that Cambridge Analytica obtained over 50 million Facebook users' information without their consent, there are no doubt many of us considering that terrifying yet alluring endgame — deleting Facebook. While difficult to figure out, deleting your Facebook account is actually a quick affair. You just need to know where to look.
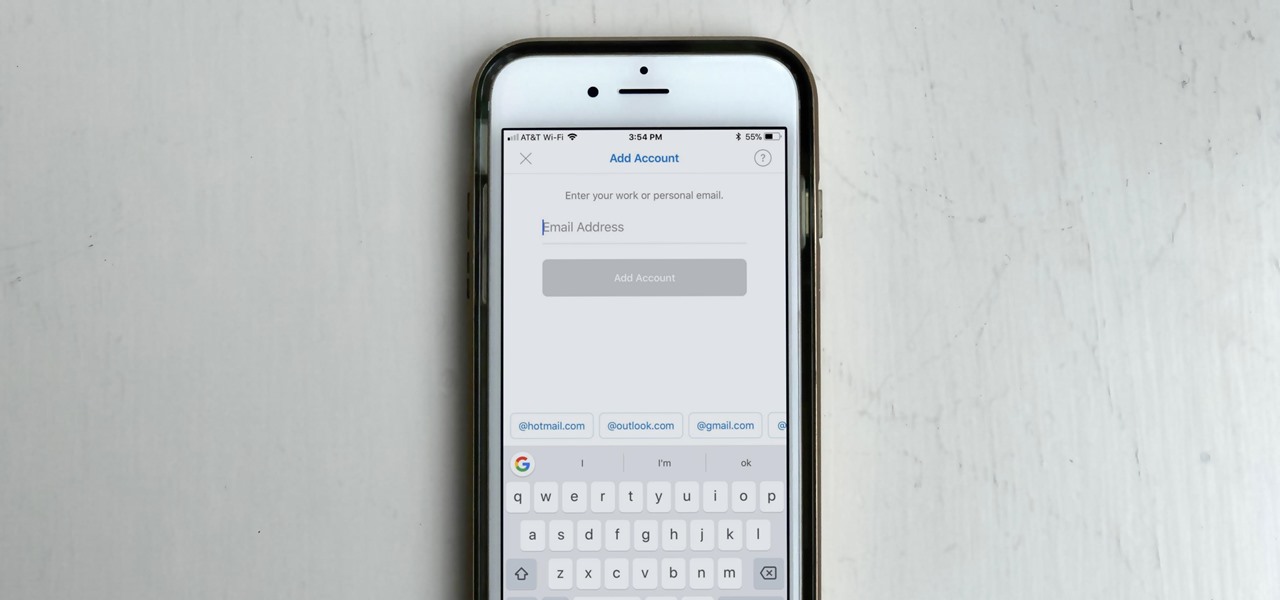
If you work with multiple email addresses, you need an app that can organize and declutter your day-to-day messages. Outlook is a great choice, but if you only have one account attached, it somewhat defeats the purpose. Lucky for you, adding additional email accounts is both quick and simple.

Coinbase sets itself apart from other wallet apps by making cryptocurrency transactions incredibly convenient. You can easily withdraw cash from the app and deposit it into your bank account within days — and now, if you want to cut the time from days to mere minutes, Coinbase has you covered as well.
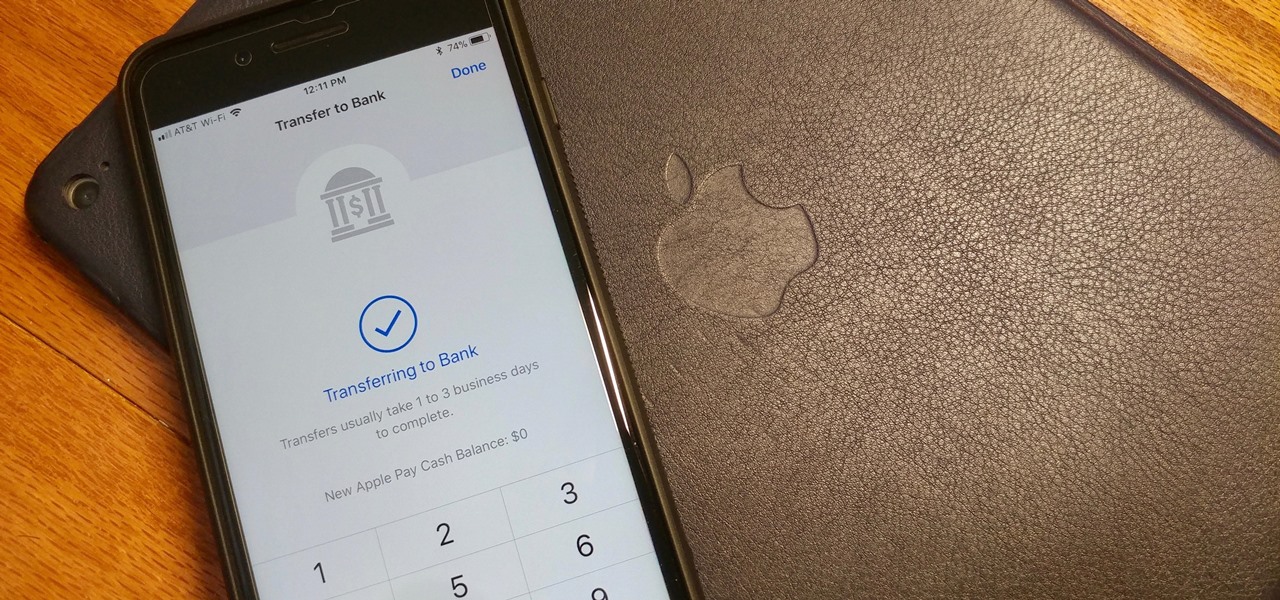
Let's say you receive $10 from a friend through Apple Pay Cash via an iMessage. You could spend that money in the App Store or at any retailer that supports Apple Pay using your Apple Pay Cash card. If you'd rather save it or use it for bills, it's easy to transfer that money to your bank account in iOS 11.2.
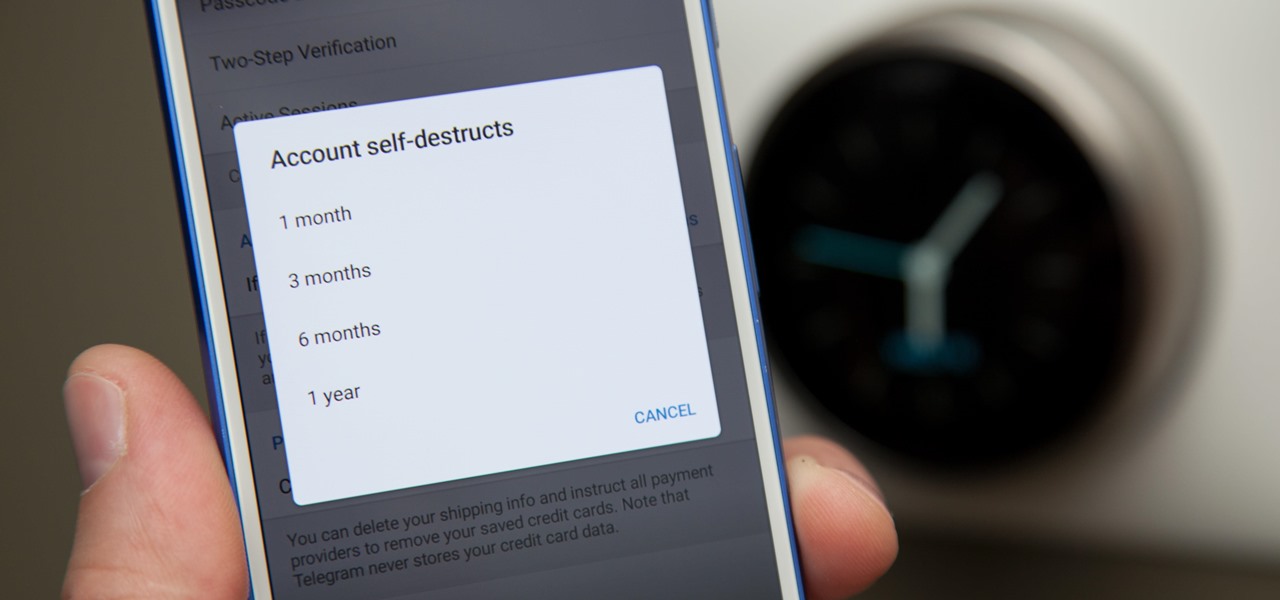
You can send self-destructing messages in Secret Chats, but that's not the only thing that can destroy itself in Telegram after a specified amount of time. Your whole account can disappear after a certain amount of inactivity, so it's important to adjust these settings to give you more time or to kill your account even quicker.
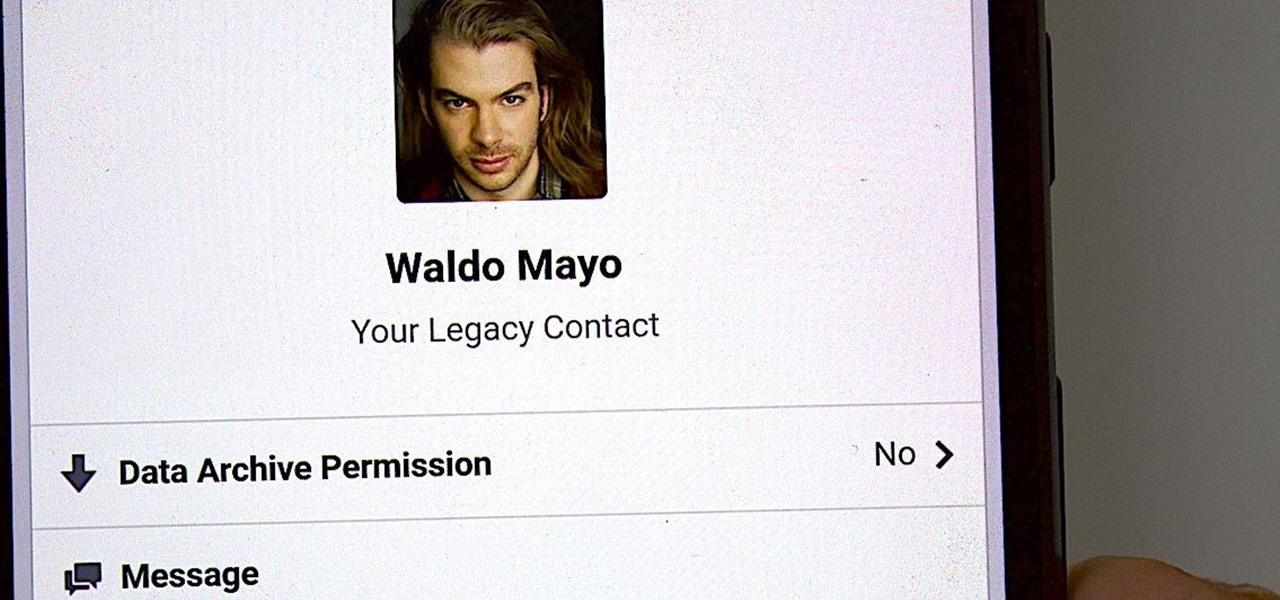
It's time to set your Facebook "Last Will and Testament" straight. Do you want to assign a contact to look over your account, or would you prefer to have all your online memories fade away the minute you die? It's a tough decision, but with a little time, you can set up at least one of these options to ensure that your account isn't left to sit pretty without you for the rest of time.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

For reasons unknown, Microsoft decided to change the way the Guest account feature in the new Windows 10 operating system works. In previous versions, the Guest account feature allowed you to set up a limited account for other users so they don't have access to your important documents and settings. Now, the process requires assigning an email to a new account and configuring share settings.

A recently discovered bug in iOS 8's Mail app by Jan Soucek can allow the maliciously-minded to quite easily phish your iCloud password without you ever thinking something has gone awry. Using a bug that allows remote HTML content to be loaded in place of the original email content, unsuspecting victims would be prompted for iCloud credentials in a popup that resembles the native one found on iOS.

Whether it's for handling your business's social media account or just for personal reasons, like trolling an ex-girlfriend's page (not that I've ever done that) or posting on behalf of your pup, there are instances where having two different Facebook accounts on one device is simply easier than switching back and forth.

It's time for another mobile prank. The classic pranks and practical jokes are always great, but let's hit your friends where it really hurts—their precious (and expensive) smartphones. And what better way to scare the shit out of them than making them believe their phone's been infected by malware?

This video will show you how to open multiple Google account in one Chrome browser. Generally browsers don't allow login multiple accounts simultaneously. But Google chrome has an add-on by which you could login multiple Google accounts simultaneously in Google chrome. So please watch the video.

Unless you're using something like 360 Vault to store photos and videos, people you lend your iPhone to can easily browse through the gallery without you knowing. It makes me anxious just thinking about it.

My friends can be pretty shitty sometimes, but they're my friends nonetheless. On various occasions, they've secretly taken my device and made me look foolish by posting crude and embarrassing posts to Facebook, Instagram, or Twitter. With friends like these, who needs enemies, right? And it's because of these types of friends that we need to substantially upgrade the app security on our devices.

Using a phone that hasn't been updated is like playing NBA 2K10 in 2013. Everything works fine, but you're missing all those new features and current rosters.

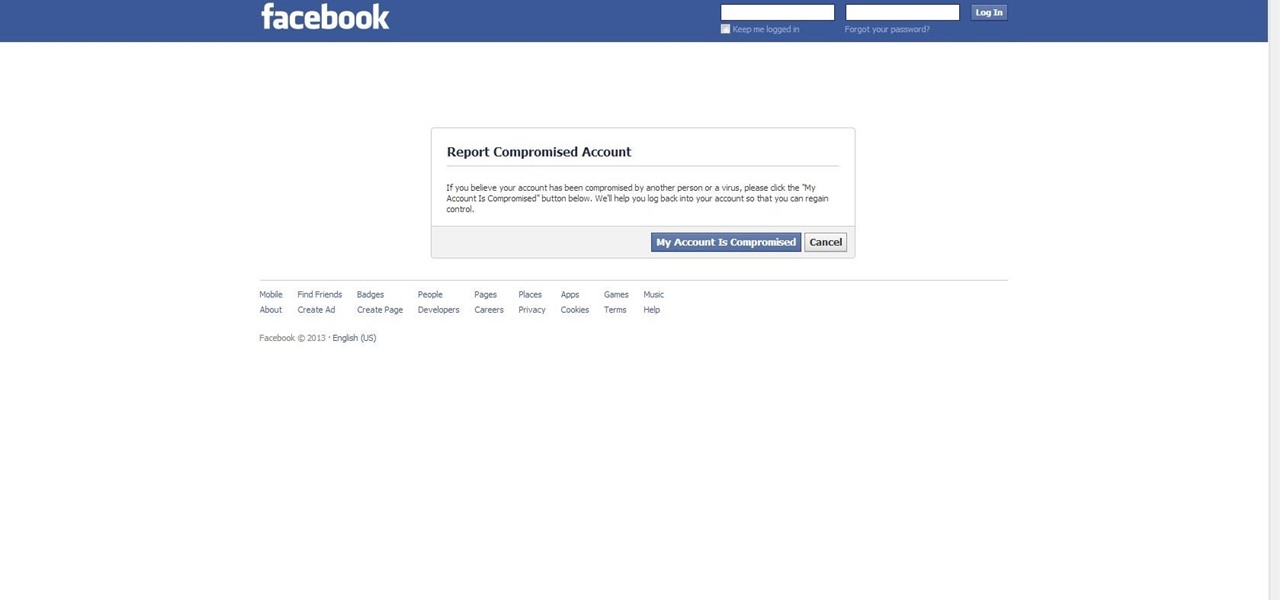
If your facebook account was hacked by someone and you really want it back this tutorial would help you get it back.

If you have an iPhone or iPad, but use a Google account for most of your communication, syncing your contacts just got a lot easier. Google recently announced that they added CardDAV support, an open protocol that lets you seamlessly integrate Google Contacts into other services. Google states that "Syncing via CardDAV is only available over SSL for Apple devices on iOS version 5.0 and above." So, if you're running an older iOS version, you'll have to use Google Sync instead.

Considering how often many of us fly on commercial airlines, the idea that a hacker could somehow interfere with the plane is a very scary thought. It doesn't help to learn that at Defcon, a researcher found that the Automatic Dependent Surveillance Broadcast (ADS-B), transmissions that planes use to communicate with airport towers are both unencrypted and unauthenticated.

If you would like to use Google AdSense on your website, in order to make money from your site, you will need to get a Google account. Click "sign in" on the Google home page: www.Google.com. Next, scroll down to the bottom of the page and click on "create an account now. Fill it out. It will send you an email to verify your account. You'll need to open your email to confirm.

In this video the instructor shows how to set parental controls for a user ID account in Windows 7. To do this go to the 'Start Menu' and go to 'Control Panel'. In the Control Panel window select the 'User accounts and Family Safety' link. There is an option called 'Set up parental controls for any user'. Select that link and it opens a window where it asks you to Choose a user and set up parental controls. There you are presented with some user accounts that are currently active on that syst...

Spotify is a free, ad-supported program that allows you to listen to music online for free. The music is everything from indie labels to the top 100 charts. This guide will help you learn how to listen to music using a Spotify account.

Learn how to create and configure a new email account on a BlackBerry Torch 9800 smartphone running version 6 of the BlackBerry OS. This clip will teach you everything you'll need to know. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this official video guide from the folks at Blackberry. For detailed information, including step-by-step instructions, take a look.

Want to know how to use Google's new multi-account sign-in feature? It's easy! So easy, in fact, that this video guide can present a complete overview of the process in about two minutes. For more information, including step-by-step on how to use this new useful feature yourself, take a look.

The iPhone 4 or iOS 4 has the ability to merge multiple e-mail addresses into one inbox. No more clicking from box to box for you, my friend! Save some time and energy by setting up multiple account on your phone. This clip will show you exactly how it is done and get you up and running.

Facebook is constantly changing, and with this latest updates they made a huge overhaul of their privacy settings. With this change, anyone on the Internet can see most of your information, without even having an account!

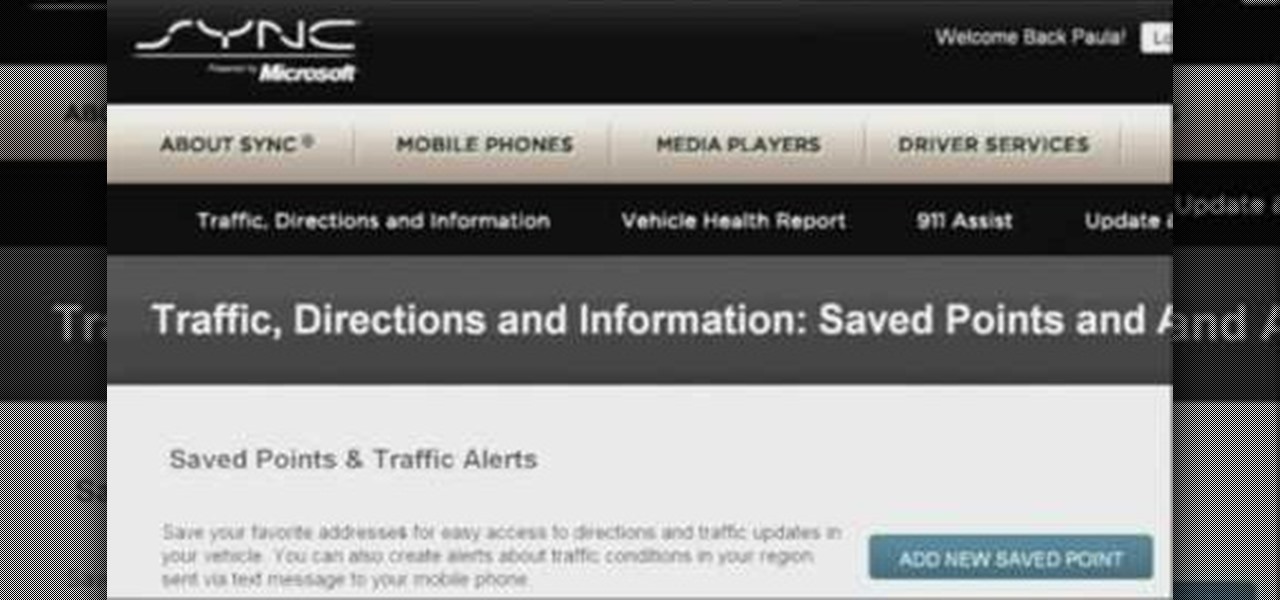
Customizing your user account online for Ford's new SYNC system is a cinch. Simply go to the website and customize news and sports, vehicle health reports, and your personal favorites. You can even start out by adding your favorite destinations for turn-by-turn directions later. Learn how to customize your Ford SYNC online user account.

Check out this informative video tutorial from Apple on how to use the basics of Mac OS X Mail. See how to set up mail with your email accounts, compose messages, add attachments, view attachments with Quick Look, and search through Mail. Mac OS X. It's what makes a Mac a Mac.

Using a MobileMe account and iPhoto, it's easy to publish your photos on the internet, whether to a webpage or a blog. NOTE: MobileMe is the replacement for .mac accounts.

With a MobileMe account and iPhoto, you can publish albums to the internet and allow your friends and family to subscribe to them using photocast sharing. Then, as you add new photos, iPhoto automatically updates the published albums for your subscribers. NOTE: MobileMe is the replacement for .mac accounts.

There's an epidemic on the Internet, and the disease—Facebook. It's an addiction comparable to a hot cup of coffee in the morning or a soothing cigarette throughout the day—in worse case scenarios, a hit from the crack pipe. If you're on Facebook, you know what I'm talking about. You're addicted to finding out what's going on with your friends and addicted to telling those friends everything you're doing. You can't stop, even when you're at work.

Your first bank account can be exciting and confusing at the same time. Check out this video and learn how to manage your money and accounts so you don't wind up in the red. You don't have to earn an MBA to make good financial decisions; this video offers plenty of suggestions to keep your accounts on track.

Learn how to delete your old Yahoo account from this video in simple steps. First open your web browser on your computer and go to the Yahoo home page. Now sign into your account using your username and password. Now copy and paste this link "http://edit.yahoo.com/config/ delete_user" in your address bar. Enter your password to confirm the deletion of your account. Finally enter the code to confirm and delete your account.

Learn how to set up Internet on iPhone clones with this video. *First thing you need to do is to make an AT&T GPRS data account.

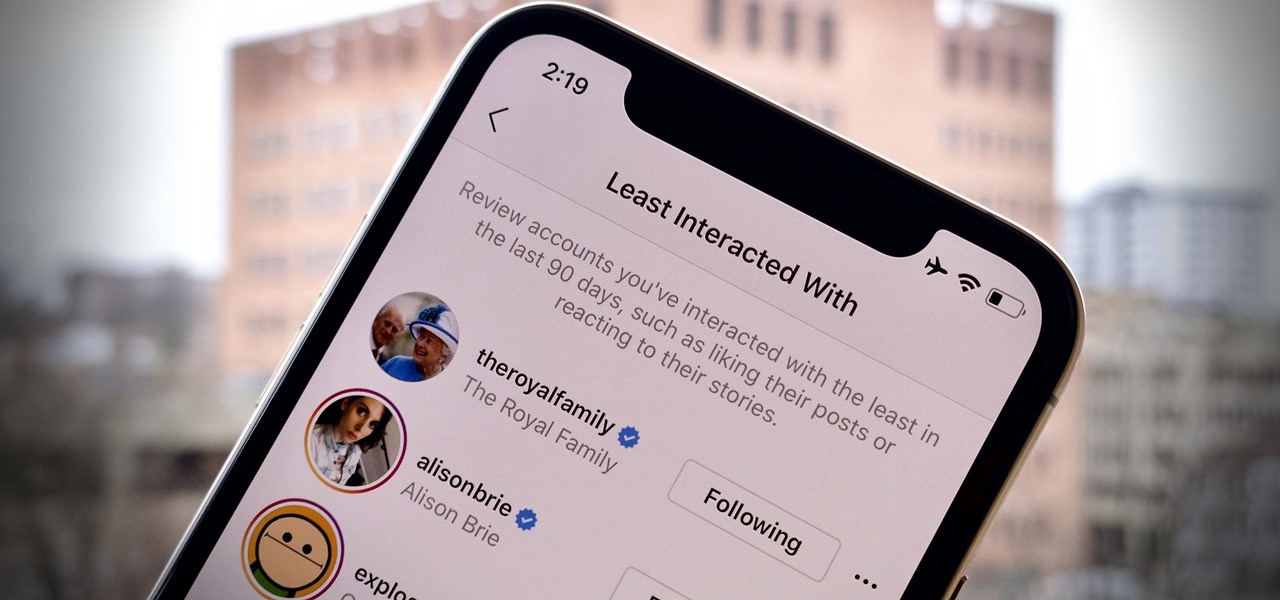
Is your Instagram feed a bit cluttered? Maybe you're seeing posts from people you don't even recognize. Perhaps the content isn't interesting. Whatever the case, it's common after years of having an account to follow too many users whose posts just aren't doing it anymore. Luckily, Instagram has an easy way for you to purge unwanted accounts from your following list.

If you've ever received an email from a sketchy address purporting to be Uber, asking you to sign in with your credentials, you might be a phishing target. Hackers use a fake login page from real-looking domains to trick you into giving up your account information, and while it's been an issue in the past, Uber is making it more difficult on cyber thieves with the addition of two-step verification.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

It's always a pleasure when your activity syncs across all of your devices. Herein lies another reason to use Samsung Internet — the app natively syncs with your open tabs on desktop Firefox. Anything you do on your computer can be easily accessible from your smartphone.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

Most of us have never put much thought into this, but the question needs to be asked — what exactly happens to all of our online accounts when we die? No, the internet won't just know and delete accounts for you, so you need to plan for life's one guarantee. Because without a plan, things become a lot harder to sort out.