Applying foundation is one of the most basic and most important makeup skills a girl needs to know, yet for many women this is the hardest step. Problems with application, such as not matching the foundation color with your skin color, not choosing the right formulation, and not applying correctly result in foundation that looks fake and caked on.

Have you ever wanted Pantene commercial hair? You know, those glamorous shampoo and conditioner ads showcasing beautiful women with beautiful hair so devoid of common hair woes like split ends, raggedy texture, and frizz that it almost looks fake? We've always lusted for hair that brilliant, but thought up until now that such perfection was only achievable through having a hairstylist on call 24/7. But not anymore.

It's pretty common to get a YouTube makeup tutorial inspired by a character from a movie, but to get one inspired by the movie itself?

DaBartist teaches you how to braid hair extensions into your own hair. Start off with hair in the front of your head, as it's easier to control. Grab a strand of hair and then wrap the braid around it once. Your hair should be in the middle now. Twist all the strands once and start going to the left and on top, then to the right and on the bottom with the hair. You can do this until you reach the end of the fake braid hair. Then pull it back and tie it to other strands on your head.

A breakaway chair is one of the best pranks, or one of the easiest effects for your indie film project. A breakable chair can be made out of simple household items, and is very cheap. The biggest material needed is cardboard. So basically, you'll make a cardboard chair, that breaks. Watch this video tutorial to learn how to make a fake movie prop brick.

Everybody has that destructive feeling sometimes, when you just want to smash your computer to bits due to a glitch or virus or freeze up. If you're making a film, it's a little more plausible that the computer would actually get smashed, considering it would be a fake prop computer. Watch this video tutorial to learn how to make a breakable prop computer.

Craving candy but have no change? Then listen closely to this hack. This con how-to video shows you how to hack a candy machine by creating fake quarters. This hack trick should also work on parking meters. Never pay for candy or meters again. Watch this video tutorial on YouTube and learn how to hack a candy machine with a paper coin or cardboard.

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM), and NEM (XEM) to name a few.

Instead of suffering through long, dull meetings with your supervisors and coworkers, you can turn those office table sessions into your very own psychological experiment.

Ah, Halloween—the funnest, but scariest day of the year. You don't just dress up and go door to door asking for candy—it's the best day to pull off scary/spooky pranks.

Are you always afraid to apply lashes by yourself, or that you never get it right? Do you find that your false lashes fall off in the middle of the day? Watch to find out how to apply fake eyelashes or falsies! This is a live step by step tutorial, perfect for beginners!

Step 1: Tie a Ponytail Use clear elastic to tie a ponytail and divide the ponytail into 2 segments.

In this video clip series, our expert will explain the use of fake (false) eyelashes, how to apply them, the types of glue needed for false eyelash application, as well as tips and techniques for trimming false eyelashes.

Did you get duped into buying fake MAC cosmetics? Don't let it happen again. This two part how to video teaches you to identify real MAC makeup from the fakes.

With so much money on the line, it's no surprise that cryptocurrency exchanges are prime targets for cybercriminals. Because of this, the importance of keeping your personal account as secure as possible cannot be overstated. Binance is one step ahead in this regard, as it requires you to enable two-factor authentication to keep your bitcoins and alt-coins safe.

Well, we have some potentially good news for those wanting to experience Magic Leap. The ultra-secretive company seems to be planning a big year in 2017.

Whether or not The Purge franchise will be as successful as Friday the 13th, A Nightmare on Elm Street, Halloween, or even the Saw movies remains to be seen, but it's definitely winning in the Halloween costumes department.

If you are anything like me, you have a knack for taking silly selfies of yourself, i.e., taking scotch tape and wrapping it around your face to make yourself look like the blob, or perhaps you like taking selfies of yourself in weird or unusual situations doing weird and unusual things.

In the weeks before Apple officially released iOS 8, consumers were abuzz over rumors that a new feature would password-protect your photos and text messages from prying eyes. Unfortunately, this ended up being untrue, though we did cover some alternatives to protecting your important information using some built-in features and a third-party app. Now, there's a new iOS app that can do it all.

Every year, some overly ambitious neighbor down the street amazes the crowds with his DIY illusion costume. While these costumes certainly require more work than pulling a mask over your head, they do have that wow factor that others lack.

We live in a time where privacy is rare and our files can be easily accessed by just about anyone. Having your phone protected by a passcode is great, but if someone figures it out, they can easily access anything on your phone.

April Fool's Day, aka National Screw with Your Friends Day, is finally here. You can always pull a conventional prank, like strategically placing a whoopee cushion on your mom's chair, but that joke has been exhausted generations before smartphones were around. We live in a day and age where smack cam is the new level of pranking, so it's time to step your game up, novices.

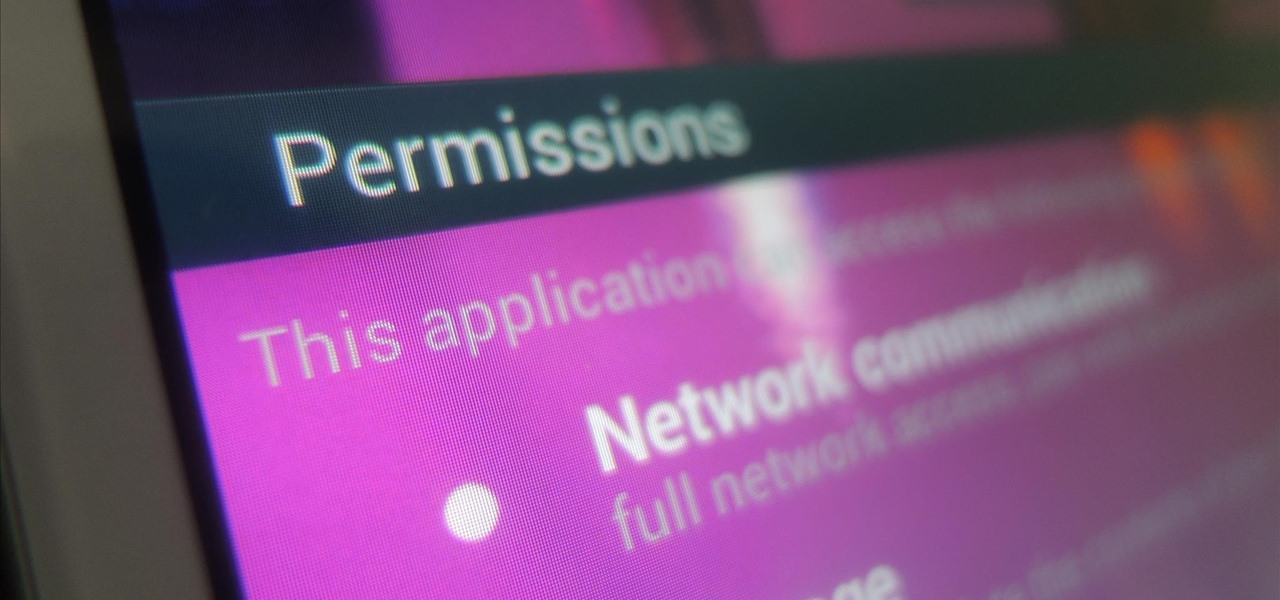
While we're usually responsible for leaking our own private information through mediums like Facebook, there are other times when we mistakenly and unwillingly allow certain applications to scour through our personal data. Some apps may have enabled permissions for internet access, thus allowing it to share said data with its external servers.

It starts innocently enough, with a nosy friend hovering over your shoulder to see what you're texting. Somehow, that doesn't satiate their inexplicable thirst for curiosity, so the first chance they get, they're rummaging through all of your super private photos—even though you told them not to.

In this great video series our expert Ryan Larson, a great jazz pianist, shows us not only how to instantly better our improvisational skills but also how to read and write music on paper. He even ventures to teach us a to play a song walking us measure by measure through it. You are only able to improvise with as much as you know so make sure the next time you're jamming with your friends you wow them with how well you know your instrument, whatever it might be!

Learn the best way to fake a shot and make yourself open to shoot a three pointer by practicing this shot fake to lateral slide to shoot the three drill.

In this series of spooky videos about how to scare the heck out of your friends and neighbors, our haunted house expert tells you everything you need to know about setting up your own haunted house. Matt Cail, designer and director of the University of Washington's campus haunted house, shares the tips and advice he gained from putting the fright to university students. He begins by discussing goals for a haunted house then tells you how to achieve them with the seasoned advice of someone who...

When you look at the top corner of your phone, what do you see? Upon upgrading to Android 11 or iOS 14, you'll see either "5G," "5G+," or "5G E" if you're connected to the right network. But what exactly do these symbols mean? They indicate not only if you're using 5G, but also what type you're connected to.

If running out of battery while out and about weren't bad enough, the experience is a lot more painful if your iPhone has a semi-untethered jailbreak. With that kind of jailbreak, when the iPhone dies, all of the mods will be disabled after the device powers back up. Fortunately, instead of restoring your jailbreak and tweaks manually after recovering from a critically low battery, you can avoid it altogether.

With all the talk about privacy concerns recently, Google's name keeps coming up because they are a very data-driven company. As an Android user, they know basically everything about you based on your device usage. That can easily scare some people off who are worried about their privacy and security. You do have some say in what personal data Google controls, but what if you want total control?

The prospect of loss or theft is something we constantly live with. Stolen iPhones fetch a premium price on the black market for parts like OLED display assemblies, frames, and charging ports. Making matters worse, if someone were to steal your phone, they could simply turn it off to avoid anti-theft features like Find My iPhone.

Increasingly, cutting-edge platforms like blockchain technology and augmented reality are overlapping, forging new digital frontiers that promise to change the way we interact with the virtual and the real world.

Even in augmented reality, Wile E. Coyote still can't catch the Road Runner. The latest AR experiment from developer Abhishek Singh brings the classic Looney Tunes duo into the real world.

Mobile wallet Curve just released a new feature that lets you correct past mistakes. Sounds incredible, right? Unfortunately, the mistakes you can erase aren't things like forgetting to do an assignment in school, screwing up a job interview, or, well, your ex. However, you can switch the card you want to use to pay even after you've paid with Curve, and that's still pretty cool.

According to a new study from the Reuters Institute and the University of Oxford, people are getting their news from ... unexpected sources. Put away your CNN app and stop checking the New York Times because a familiar app is now keeping you up to date on current events: WhatsApp.

Update: Twitter user Benjamin Geskin (@VenyaGeskin1), known for his iPhone renders, tweeted on Monday alleging that the leaks are fake:

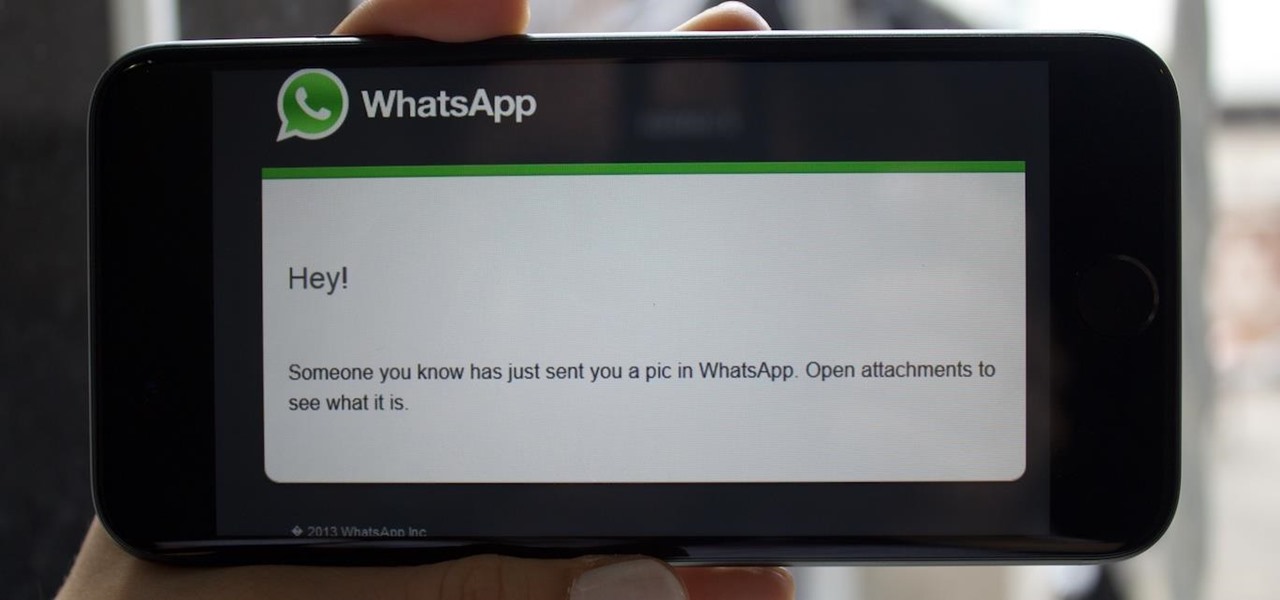
If you ever get asked to update your WhatsApp to your favorite color, don't. It's probably spam. According to Reddit user Yuexist, a new WhatsApp adware is going around disguised as an update.