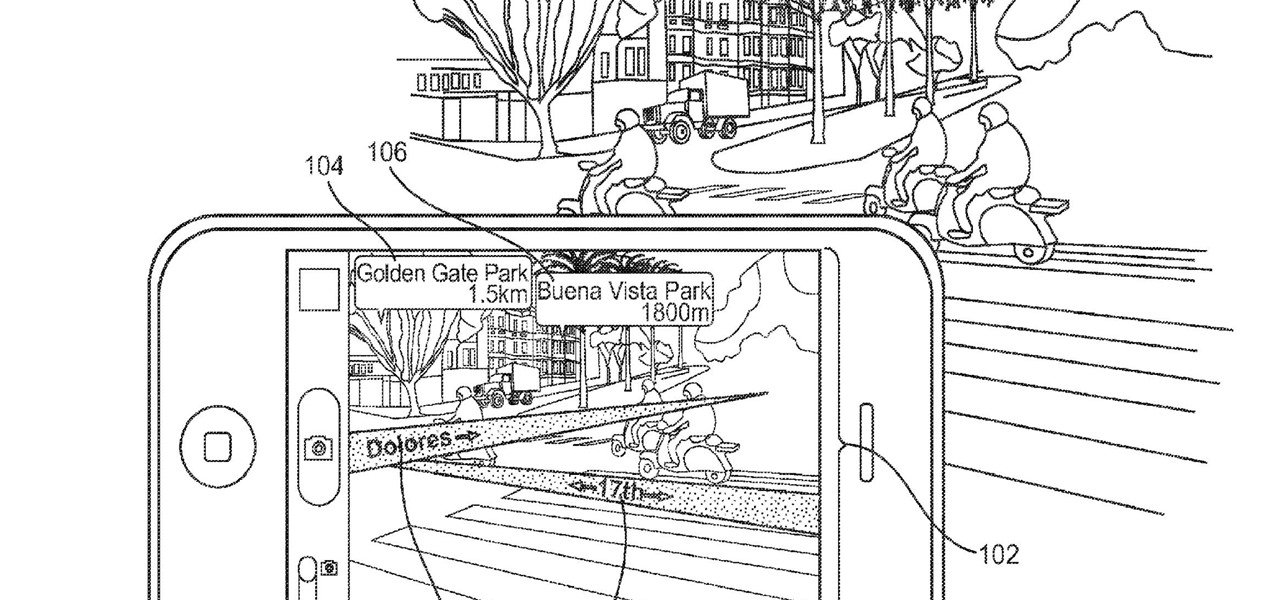
Apple is combining internal and external talent in an effort to give them in edge in the augmented reality market, though we still don't know what form their foray into alternative realities will actually take.

This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/

Thanks to a couple of photoshopped images that made rounds across Twitter last year, iPhone users were duped into thinking that iOS 8 included a security feature that would lock individual apps. Of course, none of it ended up being true, but we covered other features and apps that could accomplish roughly the same thing.

If you lend someone your phone, even if it's just for a second, there's a chance they can enter an app and see something you'd rather they didn't. Whether it's a personal email or a private photo, there are plenty of reasons why you'd want to keep snoops out of certain apps.

How can you tell if the pair of Ray-Ban Wayfarer sunglasses that you are about to buy online are not a fake? Follow these 9 simple steps to verify the authenticity of your purchase. Always ask the seller to use the youVerify app prior to purchase. It's Smarter Selling & Safer Shopping.

The stereotypical geek is not good at sports. Think about it, we’re known for spending time in dark basements doing weird stuff that has nothing to do with running around and being active. So we’re known for our inability to play sports, but I wouldn't call it an inability so much as a creative way of passing these challenges by the skin of our teeth. Examples:

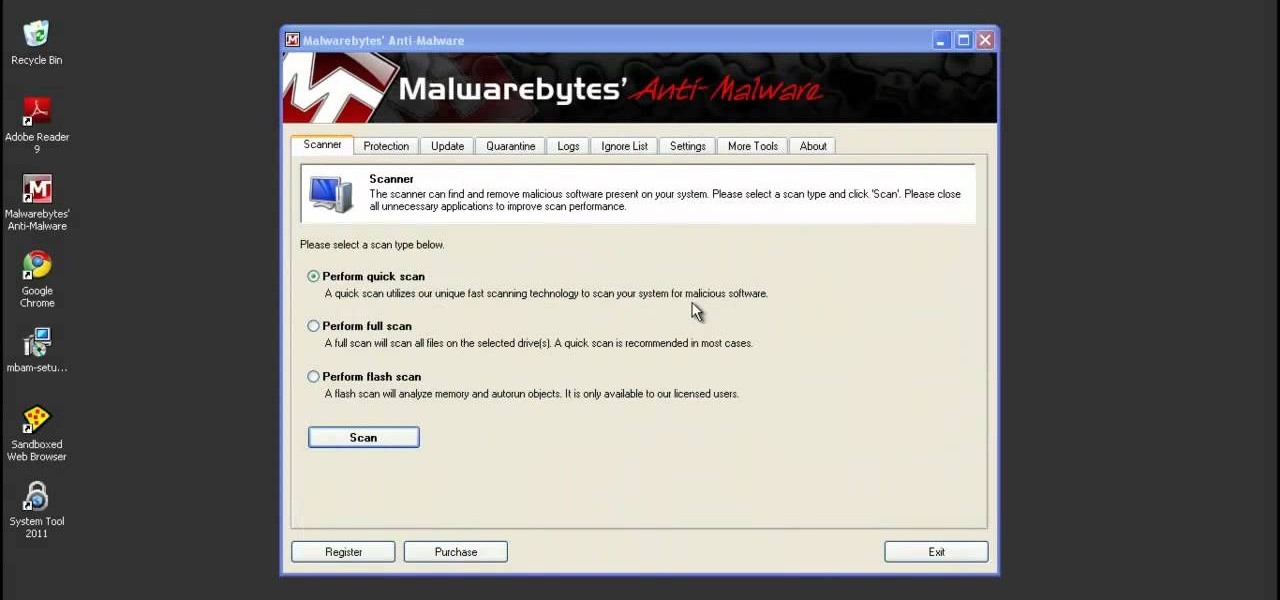
System Tool and System Tool 2011 are the most widespread fake-antivirus rogues on the internet today, infecting countless machines. This video will teach you how to uninstall both warez completely, returning your computer to blessed normalcy.

Remember Michael Jordan? He may not be in the news as much today, but he's still one of the greatest basketball players that ever existed — nobody can doubt that. Professional basketball just isn't the same without MJ, but if you'd like to see him in action again, all you have to do is prime your pencil and pick out your paper and DRAW!

This video speaks to everyone who has ever bought anything online, or in fact, anyone who has ever bought anything period. How do you know what you're getting is genuine? Is it a fake product? Is it stolen goods? Is it impure?

What's better than one prank? Five pranks! This video from the notorious Kipkay provides five fantastic, funny, and facile pranks to pull off on your friends and family… maybe even your enemies.

Release your inner wild thing with a costume based on the classic children's book. You Will Need

In this video music lesson, an expert jazz musician will demonstrate how to read through a fake book composition in B major. He will demonstrate how to play the various measures and sections of the fake book composition on piano, as well as how to improvise while playing.

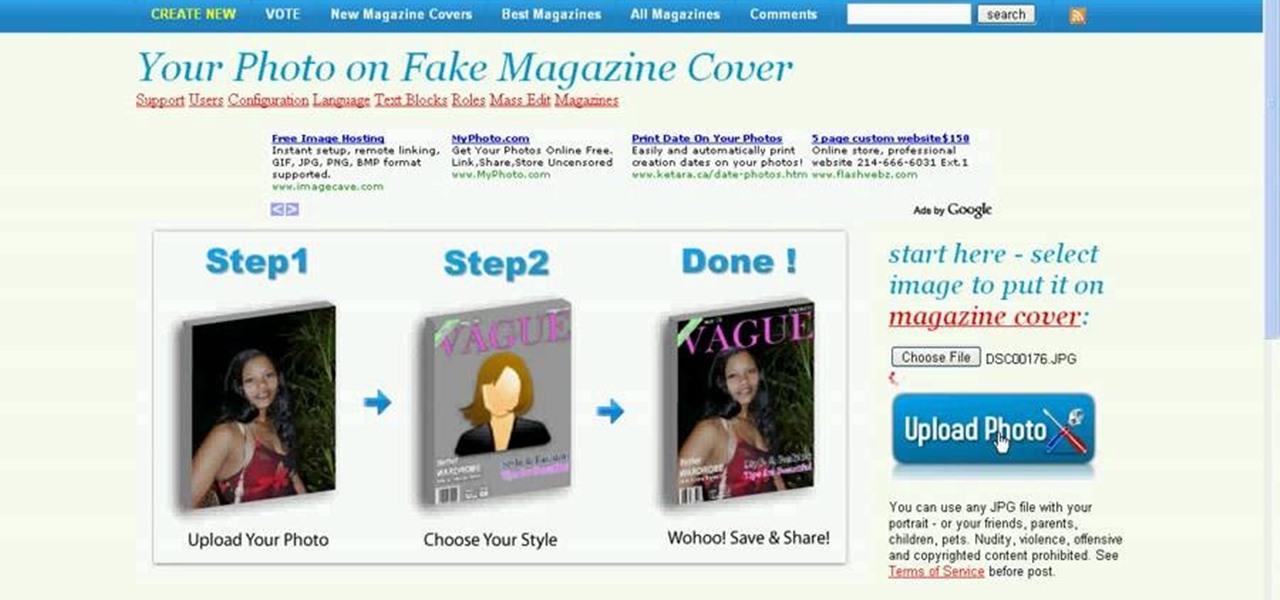
Want to impress your friends by showing that you're hot stuff? Put your face on a magazine. This short tutorial shows you how to create a fake magazine cover on the web, using your own personal pictures. Just go to MagMeNow.

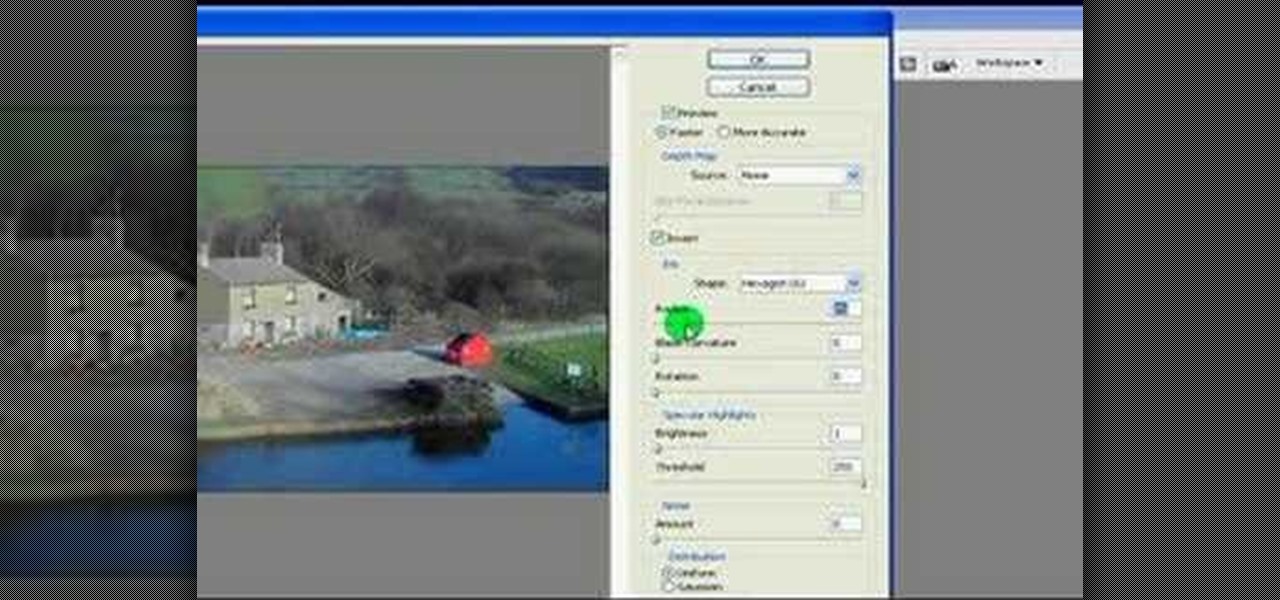
Learn how to use the Fake Miniature Or Tilt Shift Effect on Photoshop CS3.

Learn how to do a fake webcam on msn with Splitcam! Learn all the configurations. Easy and simple , can be use to play any video. Watch and learn.

Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tracking link, Grabify can even identify information leaked from behind a VPN.

The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.

If you're a small guard in basketball, paradoxically you often want to get a bigger man defending you so you can exploit their lack of speed. Watch this video to learn from Deron Williams how he uses a crossover / step back move from a screen to get the big man on him, then fake him out and take a wide open jumper.

This video shows how to make a cute vintage looking jewelery box. A cardboard cheese box forms the body of the jewelery box. Other items you will need include mod podge, white glue gesso, masking tape, ribbons, a mirror from a compact, some fabric, and some faux pearls and flowers. Begin my removing the labels from the box. Paint the inside and outside of the walls of the box and the lid. Paint the areas of the box that you just primed with gold metalic paint. Now use the box to trace three c...

1. To make tilt shift take one picture which is taken from high angle with any content like car and buses. Now open the picture in Photoshop and change it to quick mask mode to create and edit the selection.

LeBron is a threat, no matter what the defense throws at him. See how he uses the art of deception to find a way to score even when he's not shooting. First ask for the ball. Second make a move to draw the 2nd defender. Third pass the ball to the open man.

This will show you how to do the Lebron James Signature Move from Nike series on NBA superstars bball skills.

To apply a Megan Fox-inspired makeup is very simple if you work on the steps which is as follows. First, use a 'Maybelline' Quad in 'Chai' Latte and use the lid color and put into the crease of your eyelid (use a color slightly deeper than your natural skin color). Next, use the brow color in the quad and apply to your eye brows. Next, use Sally Girl eyeshadow in Champagne and apply to eyelid and near the tear duct. Take the lid color from the quad and apply under the lower lash line. Use E.L...

Poison Ivy is a villainess in the Batman comic books, a seductive femme fatale with poisonous blood and the ability to control plants. She makes excellent inspiration for a Halloween costume. Make you sexier and more beautiful. Hair: Poison Ivy is portrayed as a beautiful redhead, contrasting with the green of her outfit. Buy a red wig or use hair dye to dye your hair red. Body: Purchase a cheap green leotard, bodysuit, or swimsuit, along with 30 or so fake ivy leaves. Using a needle and thre...

Ms. Joni Marie Newman from Just the Food teaches us to make Bakin Bits without hydrogenated fats. She tells us that it's cheap, it's easy, and it only takes 10 minutes to make Bakin Bits. She starts by taking granules in a bowl. In another bowl, she takes liquid smoke and adds water and salt. Then, she takes the liquid smoke bowl and pours it over the granules. Then she mixes it all together with her fingers. At that point, she tightly covers the bowl with a plastic wrapper and keeps it in th...

In this video music lesson, an expert jazz musician will demonstrate how to read through a fake book composition in A major for beginners. He will demonstrate how to play the various measures and sections of the fake book composition on piano, as well as how to improvise while playing.

Before applying any make-up start by thoroughly cleansing the face and moisturizing after cleansing. Start with a good concealer to cover up and blemishes or dark spots. Apply liquid foundation with a stipple brush to ensure all over coverage of the entire face. Now using another brush apply your face powder, you can try MAC skin finish in your own personal skin shade. For the eyes, start with a white shadow and apply all over both lids. Now, take a medium-brown color shadow and apply to the ...

This video shows you how to get a jeweltone rhinestone look with your makeup. First, you take "Kryolan aqua color" and mix it with water, and apply the mixture to your eyelid. Next, you use "Jewel Blue" to cover your eyelid. It should look turquoise now, because of the base you applied. Next use the UV pink from the Kryolan UV Palette and apply that to your crease. Now blend the edges. Now you use fuchsia pigment and set it on the base of your crease. Next use a jewel tone purple eye shadow a...

Not exactly sure how to get a hold of a death certificate? Whether you need a death certificate to trace your family history or to make a legal claim, follow these steps to get the record you need.

Pull off this easy prank, and – without causing any permanent damage – watch your coworker squirm with frustration.

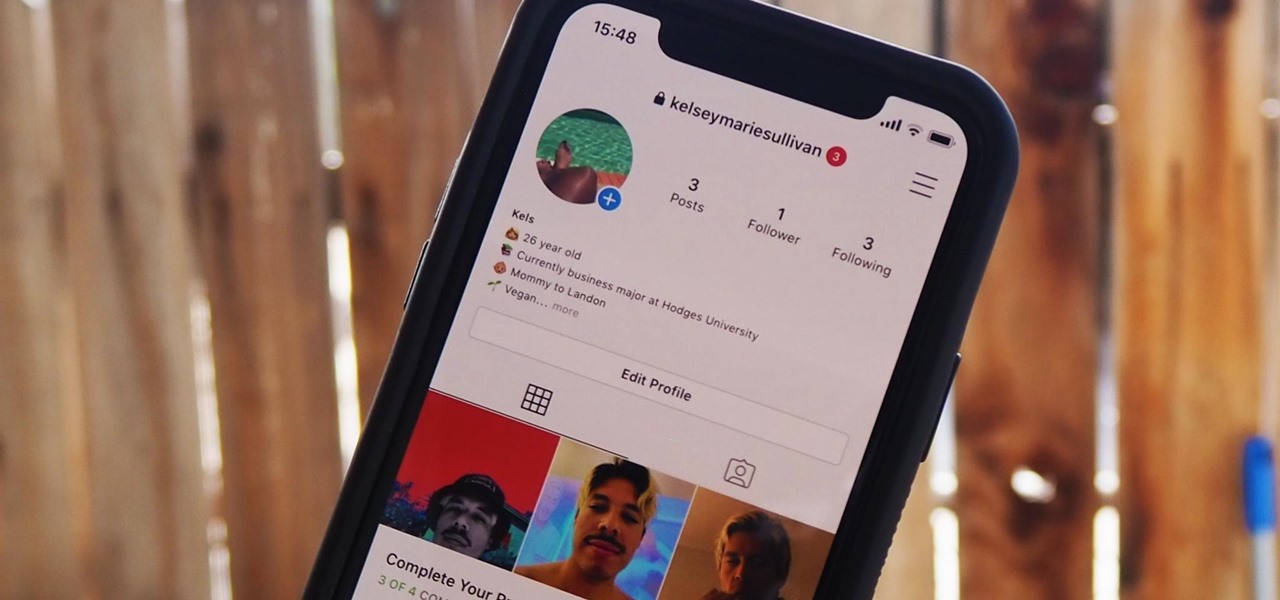
Everything you post on social media lives there forever — even if you delete it. Just ask anyone that's ever posted something stupid. Instagram does not provide built-in tools to save or download images and videos from other users, but there are workarounds. Third-party tools make saving other people's photos and videos easy, and there are always screenshots.

5G is undoubtedly the future of mobile networks, and there's a good chance your next phone will have it. But just like with 4G, as carriers race to get the best 5G coverage, the ones running behind are abusing marketing terms to make themselves seem further ahead than they actually are.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful.

When I see the words "free trial," I know I'm probably going to have to whip out my credit card and enter in the number to "not get charged." Then I end up forgetting about the trial and want to kick myself in the ass when I see my statement at the end of the month.

Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily active users.

Since it's October and Halloween is fast approaching, it's time for a series of articles on how to make the coolest Steampunk Halloween decorations for your home! In this installment, we'll look at some jack-o'-lanterns, skulls, and a few other things that are easy to Steampunk, but will still keep that "spooky" Halloween feeling.