Timely costumes for Halloween are awesome—especially really obscure ones—because they're indicative of social awareness. In 2010, I remember seeing several Chilean Miner costumes, which I thought were great. 2012 brings new stories, new characters and more importantly...new Halloween costumes.

Until recently, brainwave-reading devices have pretty much only existed in science fiction. Sure, electroencephalography (EEG), the technology that powers these devices, has been used in medicine and psychiatry since the late 1800s, but diagnosing people's brains and reading their minds are two totally different things. The first EEG headsets available to the public were used mostly in gaming and even in fashion, but in the last few years, they've gotten a little more sophisticated.
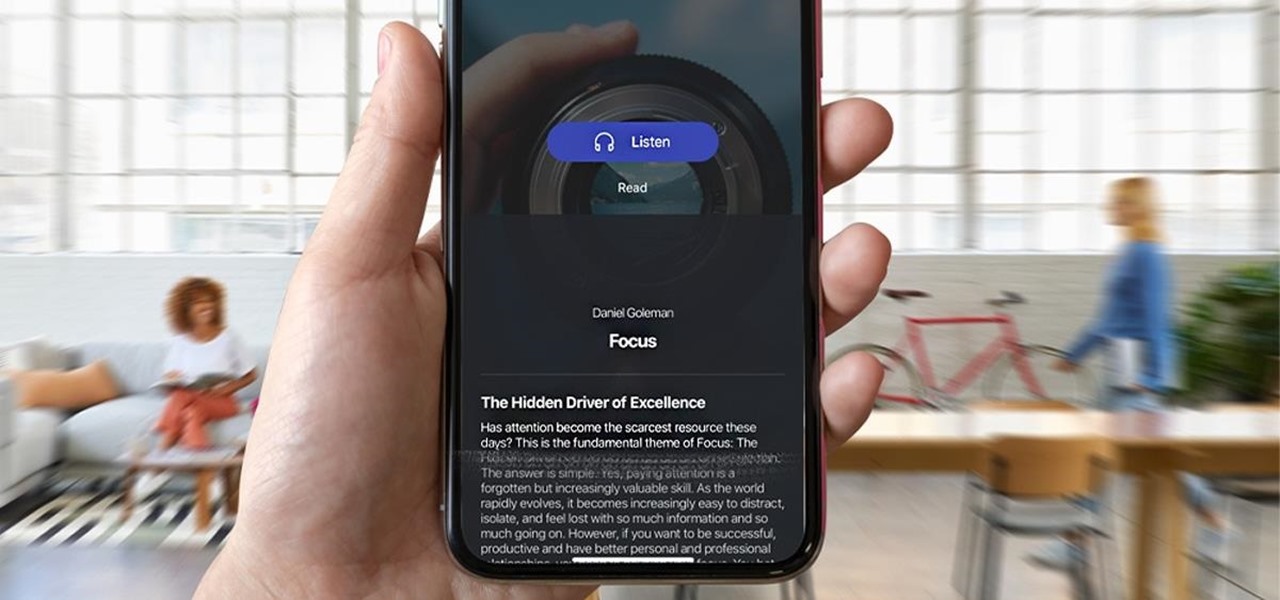
Reading is as gratifying as it is time-consuming, the more you put it off, the bigger your to-be-read stack gets. Eventually, that stack will become a shelf, then a case, and then even if you want to read, who has the emotional fortitude to pick just one from all those unread books. With 12min Micro Book Library: Lifetime Premium Subscription you can read an entire book from start to finish in 12 minutes without losing any of the meaning, and it's on sale now for $39.
Learning to code is difficult, but the potential of a little expertise in a few programming languages grants you is worth the effort. Learning to code won't just put you on one career path; many fields, from game design to data science, use coding languages. The All-in-One Coding Skills Bundle can be your start toward mastery of some of the most useful coding languages around for $29.99.

For a long time, digital creators have had to make do with clumsy mice that don't capture the minute movements they need to do their best work. Unless you were willing to spend potentially over $600 for a drawing tablet with a high-resolution screen, you were stuck with a mouse. Creators who work with audio or video were just out of luck, period.

Microsoft has plenty of products that you're likely familiar with, especially if you work or dream of working in IT. One of the most important now and in the future will be Azure, the company's cloud computing service. You might not know it, but a significant portion of the internet runs on Azure, and that share of the web is projected to keep growing in the coming years.

2020 has been a rollercoaster of a year for all of us, the type of year that makes you feel like you're not sure if you're upside down or right side up. But as the holidays arrive, it's time to get your bearings back and find the good in the world — the type of good that we could use more of right about now.

Google Drive has been a gamechanger in the business world. First launched in 2006, Google Sheets has become much more than an alternative to Microsoft Excel. The powerful spreadsheet program is a boon for efficiency that's accessible wherever you have an internet connection—or when you have time edit offline.

Linux has been one of the most popular desktop operating systems for nearly three decades, ranking fourth in the world behind Windows, macOS, and Google's Chrome OS. The open-source operating system is loved for its quick, powerful, text-based interface and efficient communication tools.

Snapchat popularized personalized stickers for social media and messaging with Bitmoji, followed by walled-garden versions from Apple with Memojis and Samsung with AR Emojis. Even Google has gotten into the game, integrating an emoji generator for Gboard.

Anyone who has used Linux long enough is familiar with sudo. Short for superuser do (or substitute user do, depending on who you ask), it allows users to run commands as either root or another user on the system. From a hacker's point of view, sudo is often all that stands between them and root access. We'll be exploring an older vulnerability in sudo that allows a user to run commands as root.

Apple has implemented a new sensor on the rear camera of its fourth-generation iPad Pro, and it's pretty exciting. It's called the LiDAR Scanner, a scanning "light-detection and ranging" sensor, and you may very well be acquainted with it if you follow any driverless car news. Will we also get it on the upcoming iPhone 12 Pro?

If you have an Android device that Netflix does not support, you can check the Play Store and it simply won't be there. But just because you're unable to download it through official means doesn't mean you have to live without Netflix since there's a way you can sideload it manually.

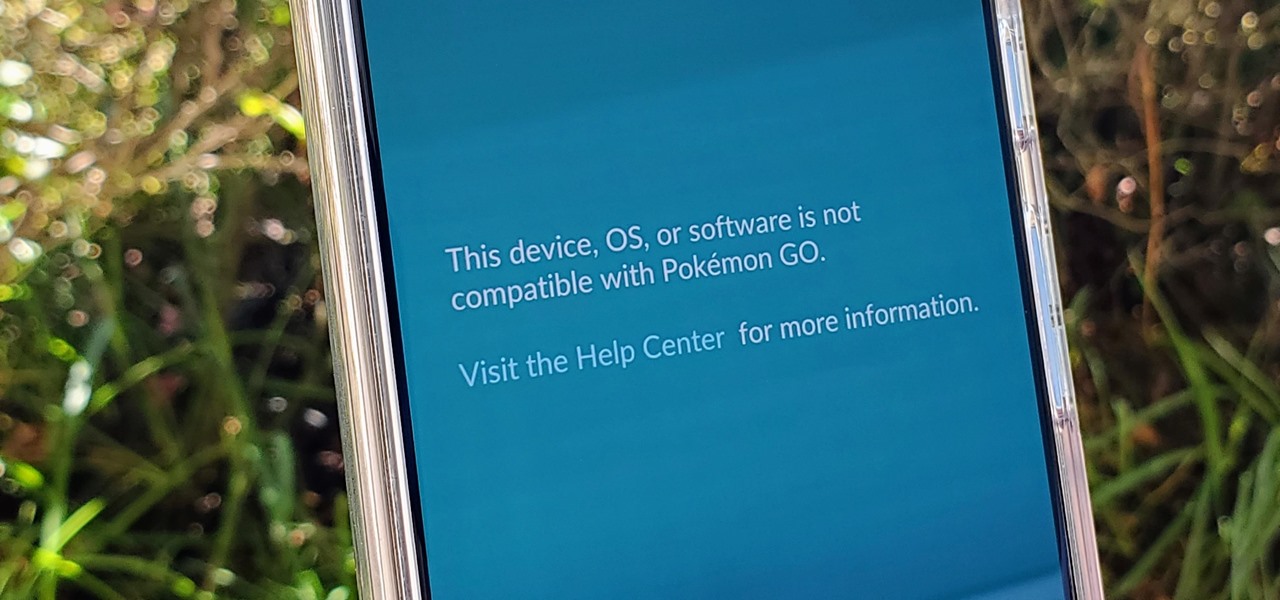
If you're a root user who has played Pokémon GO over the years, then you're probably familiar with the detection methods used to spoil your fun. The game's developer, Niantic, has publicly mentioned their ongoing battle with rooted Android phones and are unwilling to let up. They have a no-nonsense approach to try and keep you from playing, and they've stepped their game up once again.

Investment in augmented reality remained robust in 2019. For the third consecutive year, we looked back on the biggest funding deals in the AR industry this week, and a familiar name came out on top.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

On iPhones, the share sheet is a powerful yet largely underestimated tool. For the uninitiated, the share sheet is the menu that opens whenever you tap the share button (the box with the up-arrow). This menu features sharing options to first and third-party apps, as well as extra functions like saving, copying, duplicating, and more. Best of all? It's surprisingly customizable.

Is the augmented reality magic fading down in Plantation, Florida? That's the first question some may be asking following a casual revelation over the weekend that Magic Leap, the maker of the Magic Leap One, has assigned much of its patent portfolio over to JP Morgan Chase as collateral.

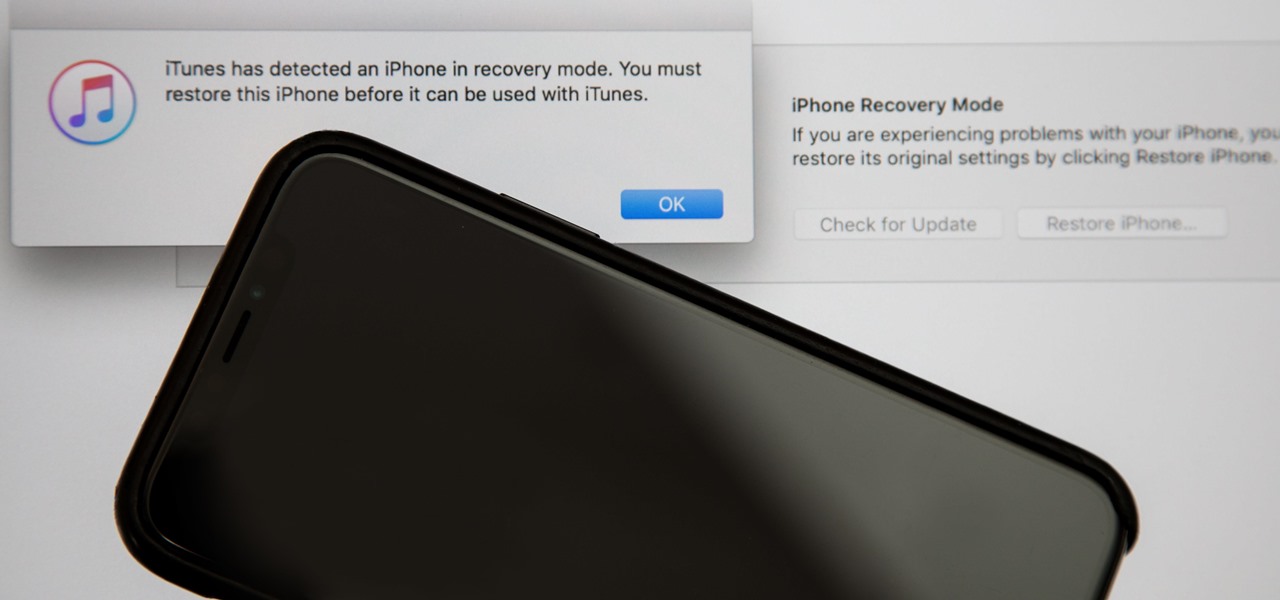
Apple's innovations often involve more taking away than adding on. The company has released seven iPhones that omit the home button, the latest batch including the iPhone 11, 11 Pro, and 11 Pro Max. If you recently picked up one of these devices for the first time, you might be a little confused on how to enter DFU mode when your iPhone acts up.

Move over, Star Wars. You're not the only Disney property that can play in the Lenovo Mirage AR headset anymore.

In this era of smartphones, we all know very well how easily we can get addicted to our devices. Spending hours each day doing the endless scroll through Facebook and other social media sites just because we feel like we'll miss something if we don't. Both Google and Apple are aware of this and are trying to help control smartphone addition in their own way for Android and iOS.

The enterprise sector is where the money is for augmented reality at the moment, and remote assistance apps are the go-to app for many enterprise customers. We took a look at the leading apps and platforms from this category, from the top contenders to the underdogs with unique features.

Niantic's Harry Potter: Wizards Unite offers players an augmented reality look into the world of witchcraft and wizardry. The Wizarding World and Harry Potter novel series is full of unique and interesting characters, which is why it makes sense that Wizards Unite offers you to take the role of one of three "Professions" — Auror, Magizoologist, and Professor. The question is, which one do you pick?

Google's has expanded ARCore support to numerous Android flagships like the Galaxy S10, so if you have a compatible device, you get access to all the cool new apps that can augment the world around you. One of ARCore's most sought-after features, AR Stickers, is normally exclusive to Google's Pixel lineup, but by sideloading the Google Camera app, you can try it on any ARCore device.

Over the past two years, the tech industry has formed a series of symbiotic relationships that are now converging in the augmented reality space. This week, we took a look at these interrelated technologies and how they are shaping the future of AR.

When Stardew Valley launched back in 2016 on Steam for PC, it was instantly deemed a success for steering the RPG farming simulator genre back on the right track. Before its release, we hadn't seen too much in this particular field of games that caught the eye of the general public. Since then, the mega-hit Stardew Valley has made its way to the mobile world of Android and iOS.

The era of AT&T and Magic Leap has quietly entered a new phase that ramps up the mainstreaming of the cutting edge augmented reality device.

Reading the augmented reality news lately has felt a bit like reading a John Grisham novel, as the business side of things has dripped with legal drama.

Update February 25: The new Sony Xperia flagship has been announced, and it has a new name: The Sony Xperia 1. You can read all of the official specs and details at our full article on Sony's new model.

It wouldn't be iPhone season without a new controversy. Chargegate, Apple's latest PR nightmare, is the name being used for charging issues on some iPhone XS and XS Max devices. If you plug in your iPhone at night — or whenever — then wake up or come back later and see that your iPhone has even less battery power, you're affected. But there is a fix you can implement right now.

Following in the iPhone X's footsteps, the iPhone XS and XS Max, as well as the iPhone XR, have all ditched the iconic Home button last seen on the iPhone 8 and 8 Plus, which is one giant leap toward Jony Ive's ultimate vision of an iPhone that's a clean slab of glass. However, without the Home button, a lot of tasks have changed, most notably, entering and exiting DFU mode in iTunes.

After months of beta testing, Siri Shortcuts has finally arrived on all iPhones that support iOS 12. Anyone familiar with Workflow will understand how useful it is to set custom Siri commands for your favorite apps. Of course, your favorite apps need to be compatible with Shortcuts in order to take advantage of the new feature.

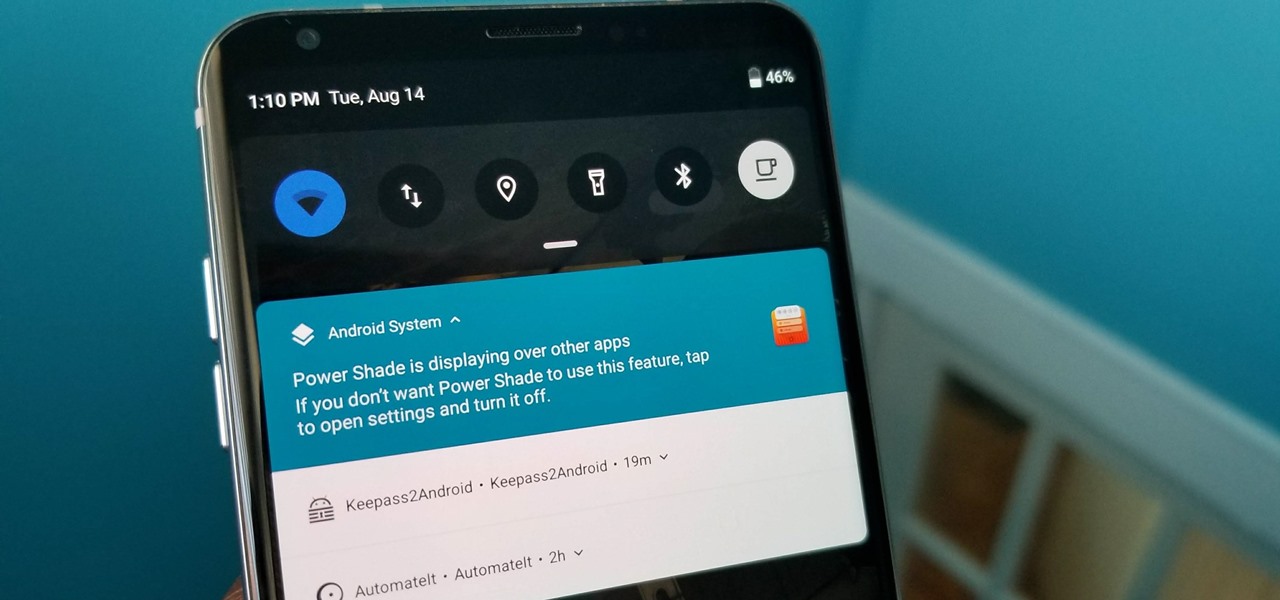
With all Android updates, there's a considerable wait before most phones get the new version, and Android Pie is no different. Until then, most of us are stuck just looking at videos of the newest update. Well thanks to developer Trey Dev, we can enjoy the new notification shade and Quick Settings menu while we wait.

It's no secret that Android has a messaging problem. iPhone users can turn to iMessage as a one-stop shop for all their messaging needs — features like read receipts and the ability to text from a computer have been standard with Apple products for quite some time. Android has no such solution, but Google's looking to fix that with a huge update to the Android Messages app.

During an event in Moscow earlier this year, Nokia announced a refresh to their Nokia 2, 3, and 5 series phones. While there is no official confirmation of a US release for the updated Nokia 2 and 5, we do know that as of July 2nd, you'll be able to snag a new Nokia 3.1.

As Magic Leap prepares to ship the Magic Leap One later this year, the company is putting its focus on mentoring developers and creators to build a content ecosystem for the spatial computing platform.

Before starting any drive where you're using Google Maps for directions, it's vital to make sure the app is functioning correctly, specifically, navigation prompts. After initiating turn-by-turn directions on your Android or iPhone, the last thing you want to worry about is Google Maps not audibly telling you where or when to turn, especially in an unfamiliar area.

The "Up Next" feature in Apple Music helps you control which songs you want to listen in the order that you want. However, this list can become messy fast, quickly becoming a collection of songs you never wanted to listen to in the first place. Luckily, Apple has built a way for you to clear Up Next, it's just not very obvious.

Kali Linux is known as being the de facto penetration-testing Linux distribution but can be a pain to use as an everyday OS — even more of a pain if that means carrying around a second laptop or the constant frustration of using the finicky Wi-Fi on virtual machines. But there's another option: installing a Kali subsystem on your Windows computer as a convenient compromise.

Google collects an enormous amount of personal data. While some of this data is used for targeted ads, others tidbits of info such as our location are used to improve our mobile experience. While it is natural for us to distrust Google's intentions, by allowing their data collection, we can add new functionality to our favorite apps.