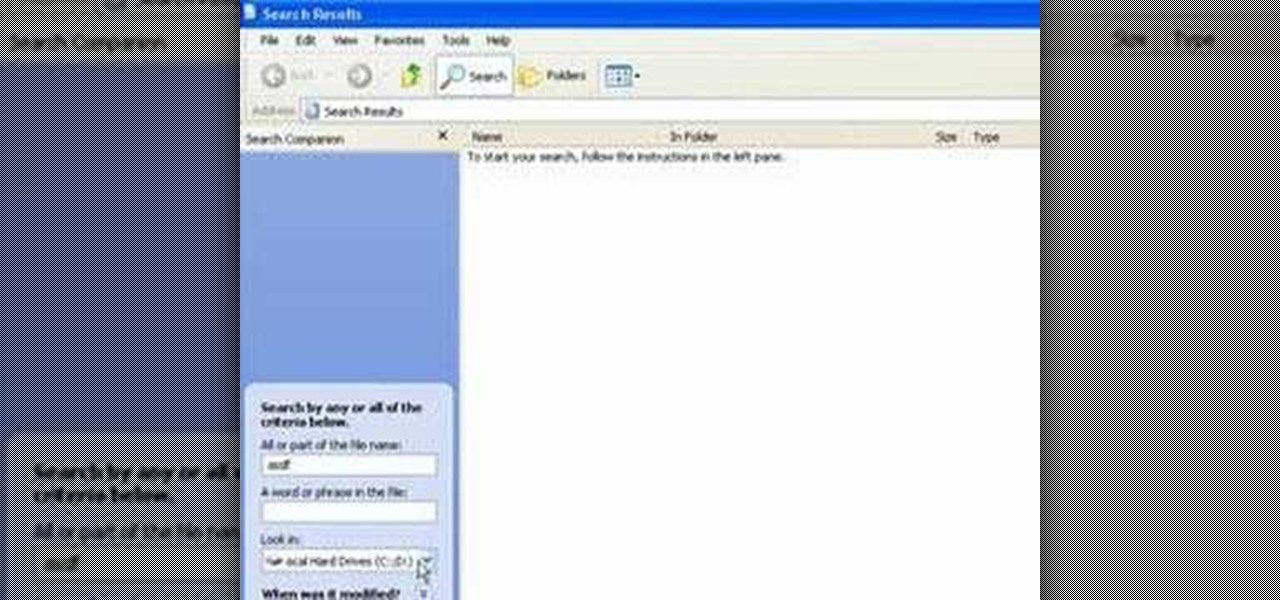
In this video tutorial, Mike shows how to find a missing file in Windows XP and Vista with three different options. In the first option, open Windows Explorer or My Computer. Then open the recycle bin to check for your missing files. If you don't see your file there, close the recycle bin and go to Start and then Search. Look for your file by searching for the file by name to find the location of your missing file. You don't have to know the entire file name to do a search. If that does not w...

Yorkshire pudding is an English side dish that is traditionally served with roast beef. But don't let the name fool you, it isn't a pudding at all, but a gorgeous fluffy bread / muffin.

Learn how to tie an Anchor Hitch (also known as a Bucket Hitch) - A very secure means of attaching a rope to an anchor or any other object that you can't afford to loose (like a bucket down a well, I suppose - thus the alternate name). I actually do use this hitch for temporary anchor attachment (preferring to permanently splice instead) as well as for my bucket lanyards when washing down my boat's deck.

We jumped on the bacon explosion bandwagon! The name says it all, it combines two of America's favorite things: bacon and explosions. This is the most unhealthy meal you can ever eat. It is made with bacon, ground beef and sausage, then deep fried.
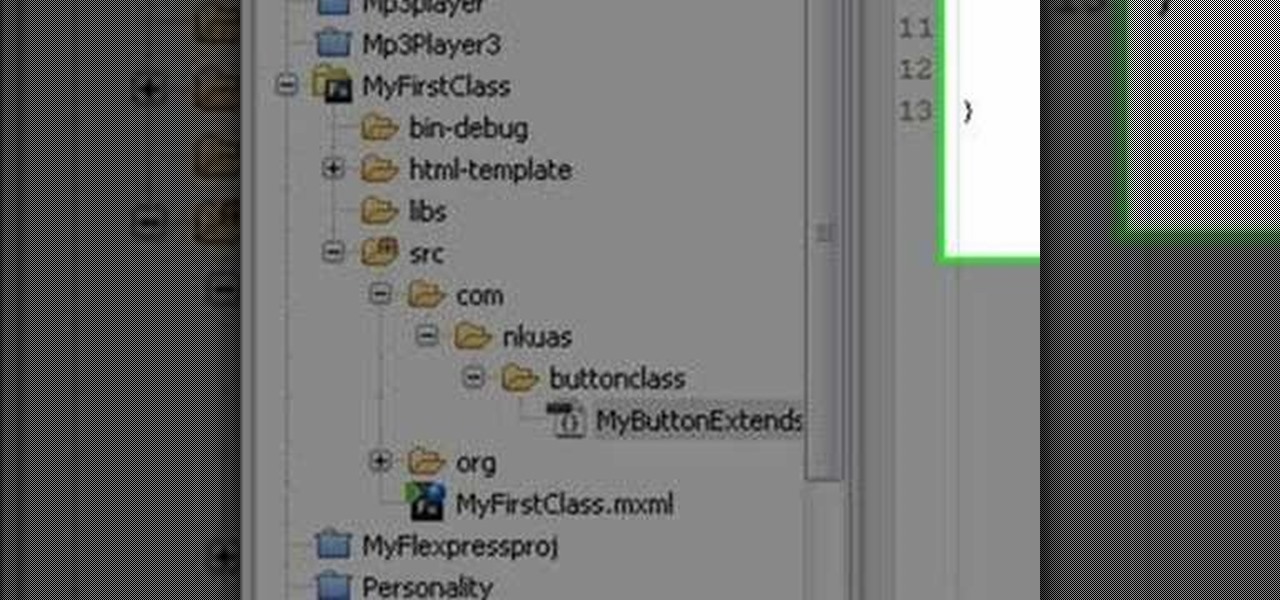
In this programming tutorial, Mike Lively of Northern Kentucky University explains the six parts of a Flex 3 class. He demonstrates how to create and extend a class using Flex 3, and how to bring that class into a Flex project using xmlns name space. Learn how to work with custom classes in this beginners Adobe Flex Builder 3 tutorial.

What are the names of basic picks? How do you use them? Check out this instructional con video that provides an overview of the basic pins used in lock picking. All picks can be put into two basic categories, raking picks and single pin picking picks. Learn the names of the various picks and how to use them with this tutorial video. Learn the basics and start lock picking like a pro!

Learn how to apply a makeup look inspired by Keira Knightley from the premier of Pirates of the Carribean: Dead Man's Chest. The products used for this look are Dark Brown Shadow (the palette's so old, the name's rubbed off... any dark brown shadow will do), Gold Shadow from the Profound Palette, Champagne Shadow from the Profound Palette, Maybelline Define-A-Line eyeliner in Ebony, MAX Factor Volume Couture Waterproof Mascara in Rich Black, Sonia Kashuk blush in Royal Rush, and Covergirl Lip...

This Zbrush 3.1 tutorial covers using layers and Alpha Shapes and a plugin named imageplane3 by Marcus at Pixologic.com to create a shield in Zbrush. You should already know the basics of working in Photoshop.

The buttonhole stitch is used in many types of hand embroidery - general surface embroidery, crazy quilting, whitework and cutwork, Mountmellick embroidery, needle lace, filet work - you name it, buttonhole stitch fits in somehow. It's a super versatile stitch, and once you have the basic stitch down, it's just a matter of applying it in a variety of ways. Watch this video from Needle 'n Thread to see how it's done.

The original daiquiri, a lime-and-rum drink invented in Cuba in the late 1800s, is named after a beach near the city of Santiago. Ah, what those sun-baked bathers would have given for this frosty version of the Cuban classic!

This will show you how to make a desktop icon that instantly shuts down your computer. If you change the picture and name of the icon it can be a great prank as well!

Watch to learn how to say the names of the days of the week in French. lundi - Monday

Elephant toothpaste is the name given to the catalyzed decomposition reaction of 30% hydrogen peroxide that uses soap to collect the oxgen gas that is produced. It is a favorite of most students at chemistry shows.

Learn how to say some basic expressions in French, including "what's your name?" and "I don't know." The instructor is a native French speaker.

When it comes to powerful punches, sangria—which takes its name from the Spanish word for "blood"—packs a truly wicked wallop. But don't take our word for it; mix up a batch and let the fiesta begin.

This tutorial teaches you how to manipulate character stats in Mugen - the custom PC game engine - including how to adjust a character's health, defense, attack, and change their name.

If you don't have one of those fancy brand name stain removers you could always use 100 ml of milk to get rid of that red wine stain on you shirt. It works on white clothes as well.

Board game enthusiast Scott Nicholson reviews a new game each week showing you the pieces and rules of play, as well and demonstrating the game with friends. This weeks game, Mah Jong, is an ancient Chinese game about collecting sets. Don't confuse this with the tile picking game on your computer of the same name!

Sosh and Gina continue your Lindy Hop education. This clip will teach you how to communicate with your partner. The front to front, the sling shot, the scissor kick, the swing out, the big turn, are all dance moves distinct to the Lindy Hop. It was named for Charles Lindbergh and his Atlantic crossing in 1927. Black communities invented the moves, and the popularity spread throughout the world.

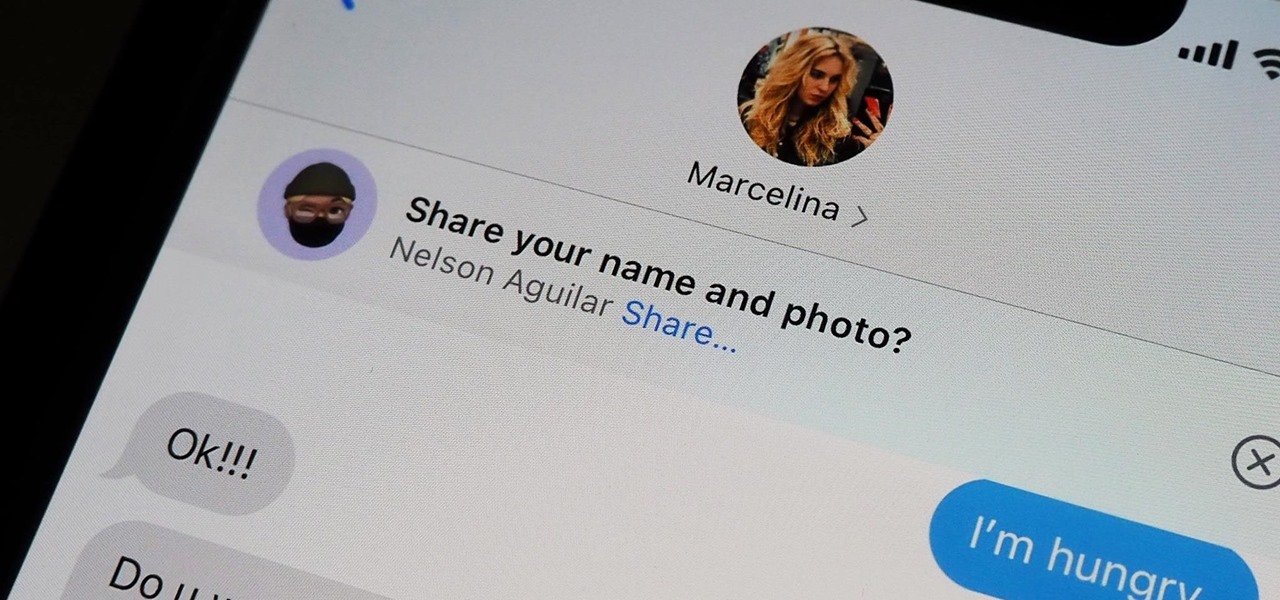
Your iPhone comes with a feature that allows you to share your name and photo with anyone you iMessage in Messages. It's a useful feature if you want people to see a customized name or fun image that you pick, but seeing all those "Share your name and photo" alerts in conversations can get real annoying quickly. There's a way to stop that from happening, thankfully.

When you have a personal Instagram account but also manage other profiles — like ones for work, your entrepreneurial startup, an alter ego, or your famous pet, to name just a few examples — how do you manage them all from the same device?

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

With the growing list of products Apple offers, the number of devices connected to your Apple ID can get quite extensive. Having all those devices connected to your Apple ID helps you keep track of them, but when it comes time to part ways with an Apple TV or Apple Watch, those devices can still be attached to your Apple ID. In some cases, this could affect the overall security of your account.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

Playlists are a vital feature for any music streaming service. For many, the ability to add and organize songs into the perfect order is a deciding factor in which streaming service to choose. The folks at Tidal (including owner Jay-Z) certainly recognize this, as they've provided users with the tools to not only create perfect playlists, but edit them as well.

On your iPhone, your phone number and Apple ID email address are the default ways in which somebody can contact you on FaceTime. While you can't remove your phone number as an option, you can withdraw your Apple ID email account. More importantly, you can add any other email addresses you'd like to the list, so you never have to worry about a friend, family member, or coworker not being able to audio or video chat with you.

Rumors that Apple is honing its automated car technology have skyrocketed. Thanks, now, in no small part to some enterprising members of the media who leaked the names of Apple's self-driving car team to the public.

Sophisticated hackers have been exploiting vulnerabilities in Chrome and Firefox to trick even the most careful internet users into logging into fake domains for sites like Apple, Google, and Amazon.

Welcome back, my budding hackers! In this series, I have been trying to familiarize you with the many features of the world's best framework for exploitation, hacking, and pentesting, Metasploit. There are so many features, and techniques for using those features, that few pentesters/hackers are aware of all of them.

Even those of us most comfortable in the kitchen can be daunted by the idea of cooking for a whole houseful of people. Whether you have a large, well-equipped kitchen or a small one with just the essentials, it can prove to be quite a task to prepare food for a dozen or so people. It takes a certain type of recipe that allows for mass production, in respects to both technique and ingredients. And what I've provided below includes several recipes that you might normally make for just a family ...

Hello everybody Joe here. Today I will be demonstrating how you can find XSS vulnerabilities in a website and what you can do with them

You've probably used Google to search for recipes, or to find out what the heck that mystery food on the ingredients list is. But with all its built-in features, there are plenty of other ways the search engine can help you out in the kitchen.
This how to will show you how to program a fairly simple Hacking bat file. First open notepad.

It's nice to have the family together for Thanksgiving dinner, but having so many people together can make it tricky to figure out what you can do after dinner. Here are a few good ideas you can use for family friendly activities.

In order to add a Next or a Previous buttons in Photoshop, you will need to begin by selecting a photo. Double clip into MasterclipMC. Create Films Layer and make a new layer. Name it Next and previous. Create a rectangle. Use the Polystar options. Adjust the size to the appropriate size. Make a triangle. Place it in front of your rectangle. This is your arrow. Make a copy of it. Rotate one to point in the opposite direction. Name them Previous and Next. Drag them into position. Rename the bu...

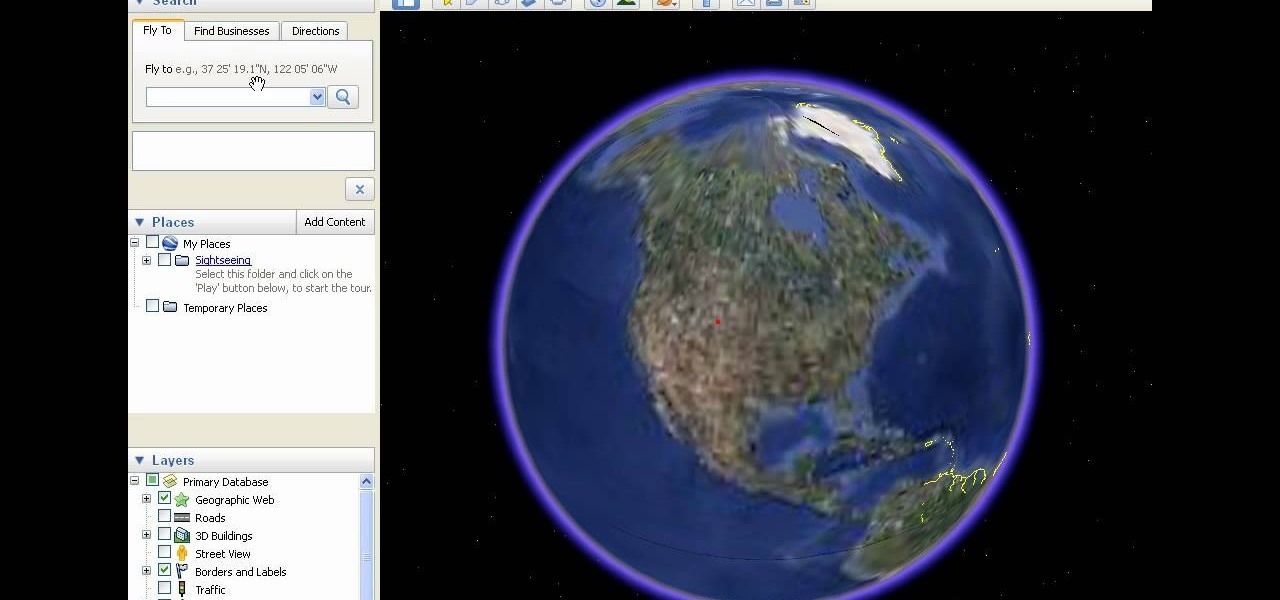
This video shows how to download and use Google Earth. To download it, go to earth.google.com and click “Download Google Earth”. Then follow the directions according to where you want to save it, and it will automatically be installed. You will see an icon pop up on your desktop. Double click on the icon to open Google Earth.

Gus and Geoff show you how to get the achievement of Negotiator Bronze Trophy in Heavy Rain. You will be playing as Scott Shelby. Your goal is to convince the store robber to leave without resorting to violence. Take the left aisle; in the center aisle there is a bag of chips on the floor that will cause too much noise. Raise your hands, and don't tackle the robber. Choose "name" and tell the robber your name and ask for his. Choose "reason" and tell the robber that "It isn't worth it.". Choo...

Stay tuned for the always enjoyable Cooking With Dog. This cooking show is hosted by a DOG named Francis! The show demonstrates how to make popular Japanese dishes.

Stay tuned for the always enjoyable Cooking With Dog. This cooking show is hosted by a DOG named Francis! The show currently focuses on how to make popular Japanese dishes. This video demonstrates how to make Sweet Potato (Dessert Made from Sweet Potatoes), a Japanese dessert.

Stay tuned for the always enjoyable Cooking With Dog. This cooking show is hosted by a DOG named Francis! The show currently focuses on how to make popular Japanese dishes. This video demonstrates how to make Yakibuta Ramen (Japanese Noodle Dish with Roasted Pork Ribs).