People love emojis, it's a scientific fact. So an app that places poops, smileys, and ghosts into social media videos should, in theory, be the most popular app ever. That's likely the reasoning behind the new Holocam app, which is available for $0.99 in the iOS App Store. Sure, Snapchat and Instagram offer users editing tools to stick static text, emojis, and drawings on top of photos and videos. However, Holocam ups the ante by placing fully three-dimensional emoji, text, and drawings, as w...
As expected, Magic Leap closed a Series D round of equity funding, raising $502 million from new and existing investors. Less expected, however, were a fresh set of rumors that the company's first devices could ship within six months.

Have you ever been listening to the radio and a song comes on that you can't identify? But you're driving, so you can't open your phone and use your favorite app to find the song's name. Well, with a feature called "Now Playing" on Pixel phones, Google has solved this problem.

If you're a regular reader of this site, there's a good chance friends and family turn to you as their volunteer technical support staff.

When you take a screenshot on your iPhone in iOS 11, a thumbnail preview appears in the corner for a few seconds. Tapping on it will give you immediate editing and sharing tools, but not everyone digs the convenience.
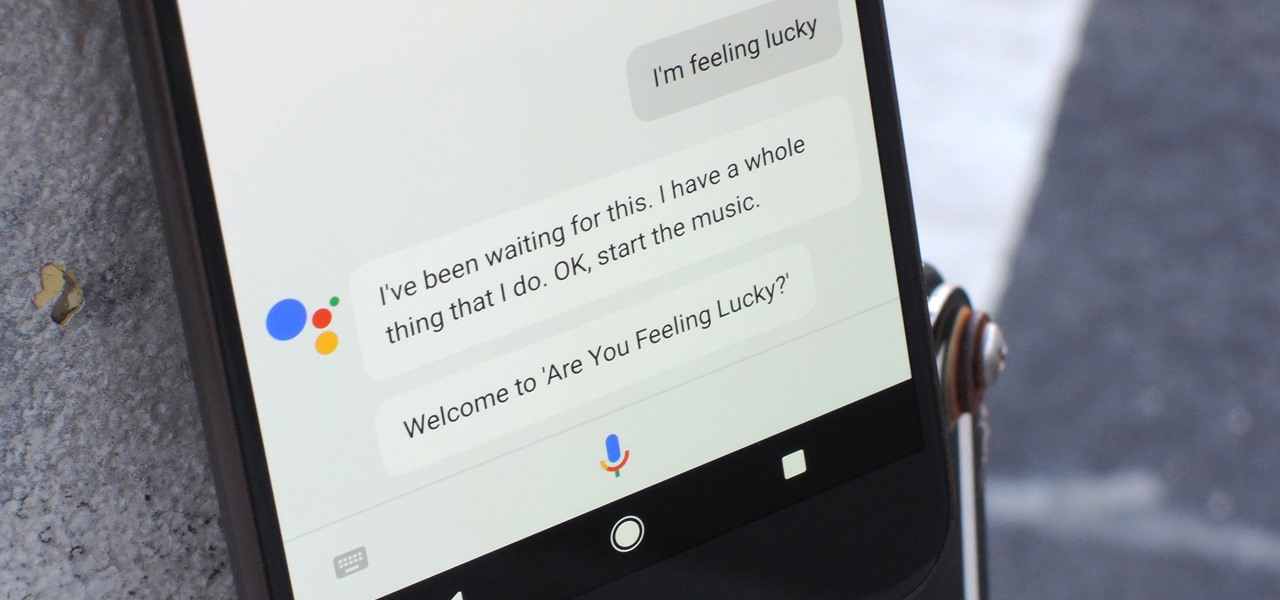
Despite a rocky start with plenty of feature disparity, the Google Assistant now provides a pretty consistent experience regardless of what device you're using it on. Be it Android, iPhone, or Google Home, the AI behind the Assistant is virtually identical — including its quirky commands and funny responses.

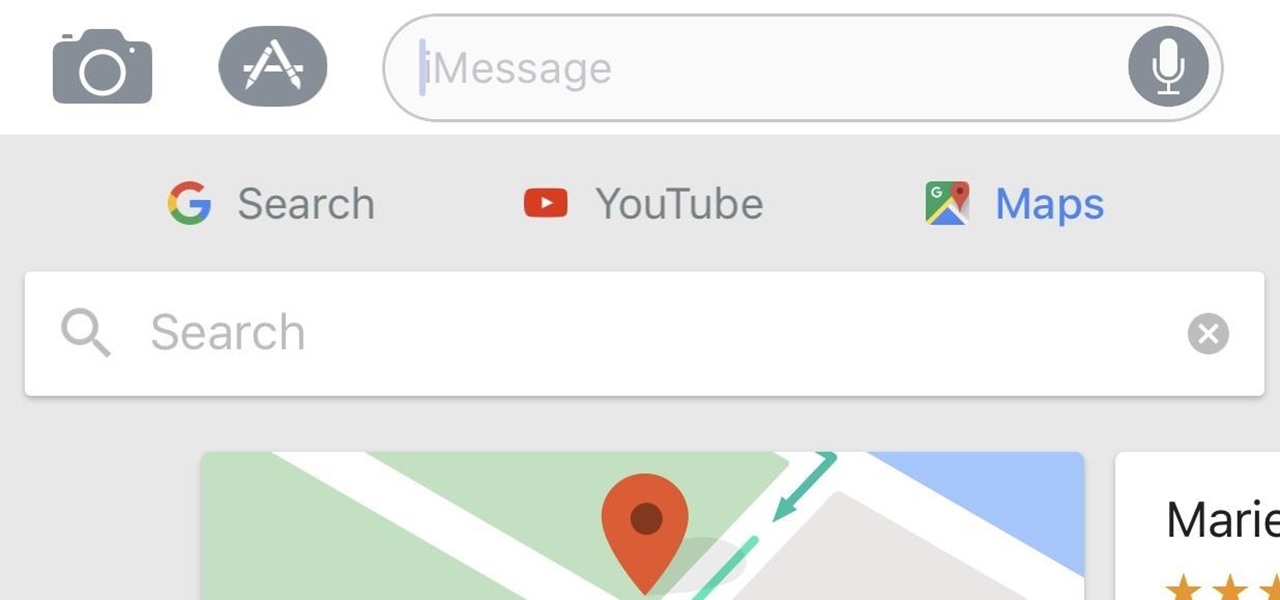
When Gboard was released on iOS in May of 2016, it gave iPhone users more control over their mobile keyboard experience. Unlike the stock Apple keyboard, Gboard lets you customize the look of your keyboard and search Google directly from the keyboard itself. Now, Google has added even more functionality, by providing users with Google Maps, YouTube, and doodling support — all without leaving your chat.

One of the most popular things to do on Snapchat is to earn a Snapstreak. This occurs when you and one other friend have sent snaps (not chatted) to each other within 24 hours for at least three consecutive days. One you've passed the three-day mark, then you and your friend will receive a fire emoji next to your names.

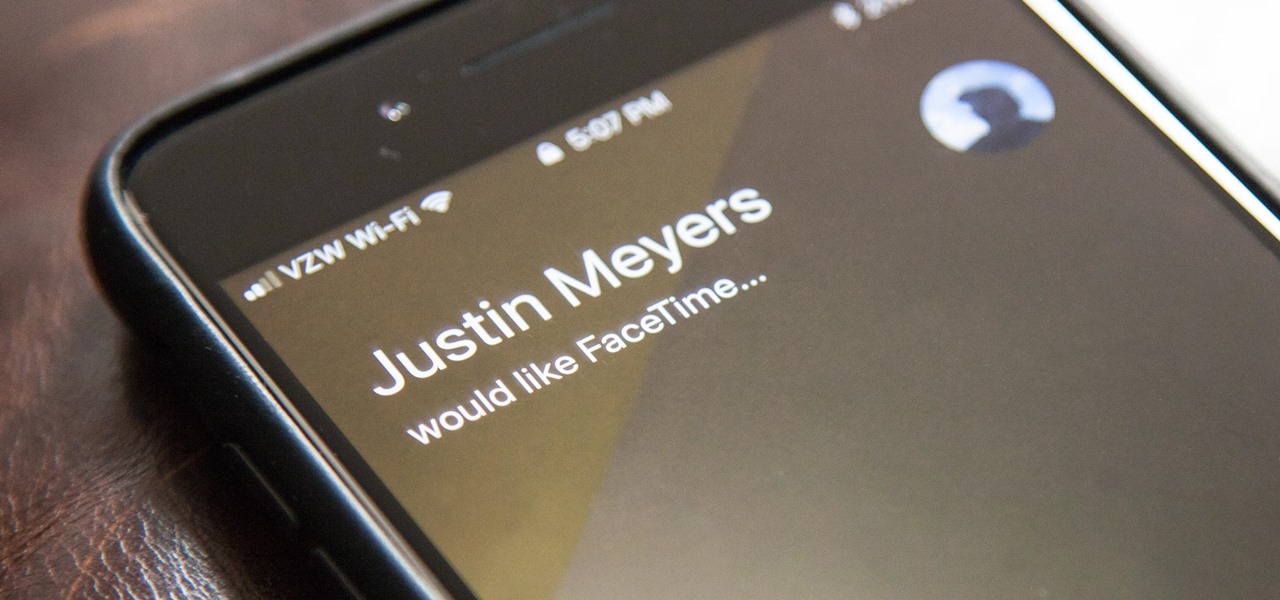
Whenever you make FaceTime audio or video calls from your iPhone, Apple automatically uses your phone number or Apple ID email address as the caller identification. So when someone that you're calling sees the incoming call, they'll see it's from your phone number or email address. But what if you'd rather it be a different identifier?

Are you looking for a get-rich-quick scheme? Need a way to buy that Tesla you lied about having? Well, I don't know how to get you that. But what I can tell you is there is an emerging market that pays pretty darn well, for work that's more than interesting. I'm talking, of course, about iPhone repairs.

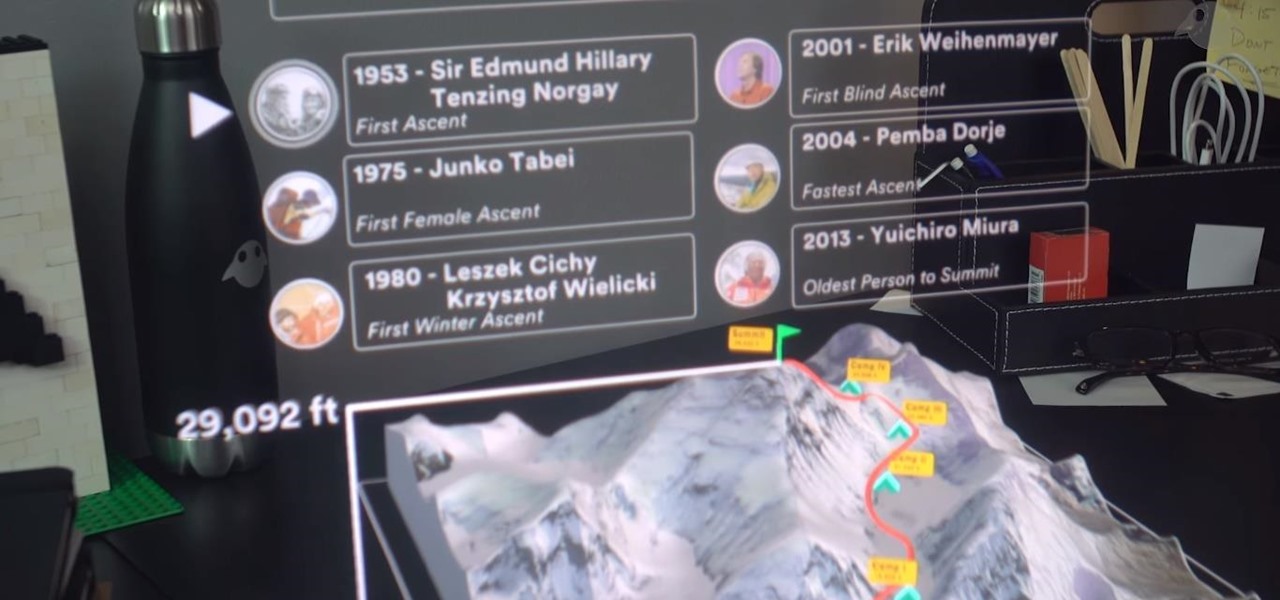
While two augmented reality companies were recently recognized for their innovative technologies, other companies have turned to augmented reality to innovate in their respective fields. Over the past week, use cases have ranged from selling snacks and video games to raising awareness for public health issues.

Thanks to a $100 million deal, you could be seeing more original shows on your Snapchat soon. Already, Snap has been producing super short shows in order to compete with social media outlets like Twitter and Facebook who have also been attempting to create their own content. While musical.ly has so far had the biggest success in this area, this deal with Time Warner is certainly promising for the beleaguered platform.

With Instagram's archive feature, we have the pleasure of hiding all our stupid photos of #gettingcrunk from back in the day. This wonderful new IG feature will still allow us all to cherish those embarrassing moments in our life, yet hide them from those people we hope would never scroll so far down.

Open your Spotify app, search for an artist, view its "Spotify Code," and display it to that friend lurking over your shoulder. Sound familiar? Probably not ... yet.

I.M. Healthy Original Creamy SoyNut Butter was recalled on March 4 after being linked to 16 Escherichia coli cases in nine states. Montessori of Alameda preschool in Portland is the latest victim in a multi-state E. coli outbreak caused by the nut-free butter.

Call them what you will—moss piglets, water bears, or by their real name, tardigrade—but these intriguing tiny creatures can come back from the brink of death. They can survive boiling, deep freezing, UV radiation, completely drying out, and even a trip to space—without the benefit of being in a spacecraft.

A rose by any other name may smell as sweet, but one annoying invasive weed may hold the answer to treating the superbug MRSA. Researchers from Emory University have found that the red berries of the Brazilian peppertree contain a compound that turns off a gene vital to the drug-resistance process.

Seriously, what's with all of the candy corn hate? I don't care what anyone says, candy corn is and always has been the perfect Halloween snack for me. Only recently did I realize that not everyone gets as hype as I do about small, sugary vegetables.

Google has already issued a few updates to Android 7.0 Nougat. There aren't many headlining features, as these minor updates are mostly bug fixes and performance improvements. But there's a few security enhancements as well, so staying up-to-date with the latest patches is important for a number of reasons.

In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using both in Shellter to create your undetectable Trojan. Part 4 is setting up your listener using Armitage.

Google kicked off I/O 2016 by debuting Assistant, a next-level version of Google Now. While you could search the web by voice before, now you'll be able to have a conversational interaction with Google. In short, it's a smart chat bot.

Video: . ?The following are 5 practical jokes you can set up on your friends and family, All these pranks involve sodas so make sure you have a few handy if you want to try out these pranks. Just a little warning, 4 out of the 5 pranks showcased in this intractable are pretty messy so prank at your own risk.

Don't Miss: How to Make Perfect Poached Eggs, Every Single Time

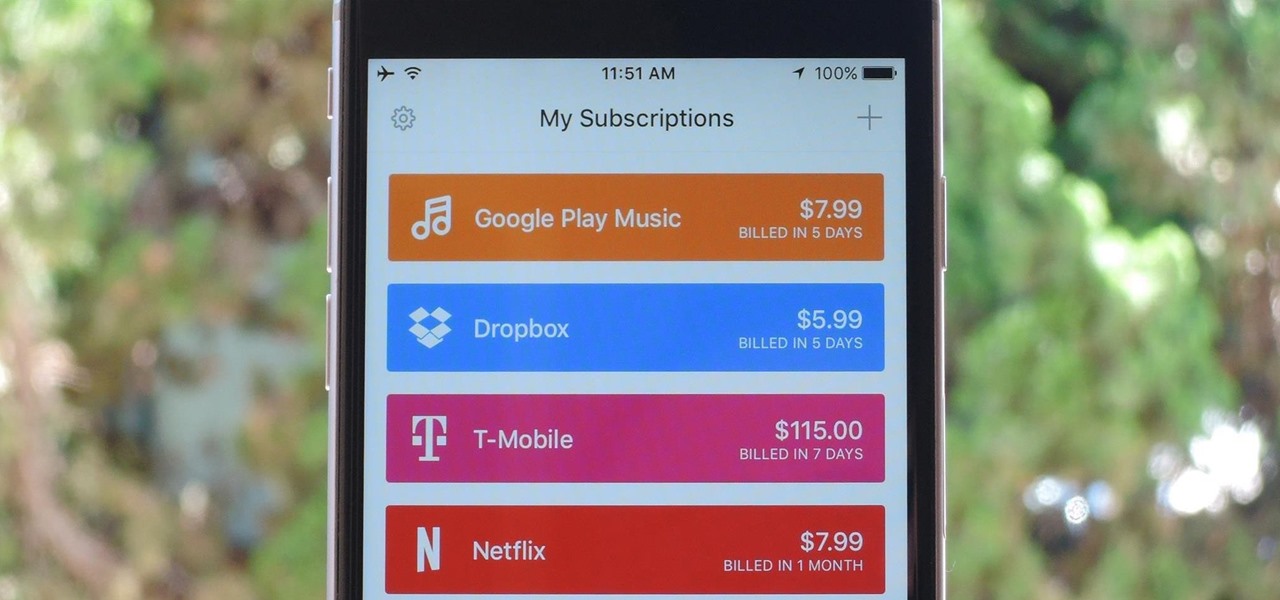
As the internet continues to become a bigger part of our day-to-day lives, we slowly but surely start to rack up a bunch of web-based subscriptions. These internet subscription services—Netflix, Hulu, and Amazon Prime, just to name a few—may seem innocuously cheap individually, but when combined, they actually comprise a significant portion of our monthly bills.

Welcome back, my hacker novitiates! If you have been following this new Snort series, you know that Snort is the world's most widely used intrusion detection/protection system. Now a part of the world's largest network equipment company, Cisco, it is likely to be found everywhere in one form or another. This makes a compelling argument for learning how to use it, as it will likely be a necessity in any security-related position.

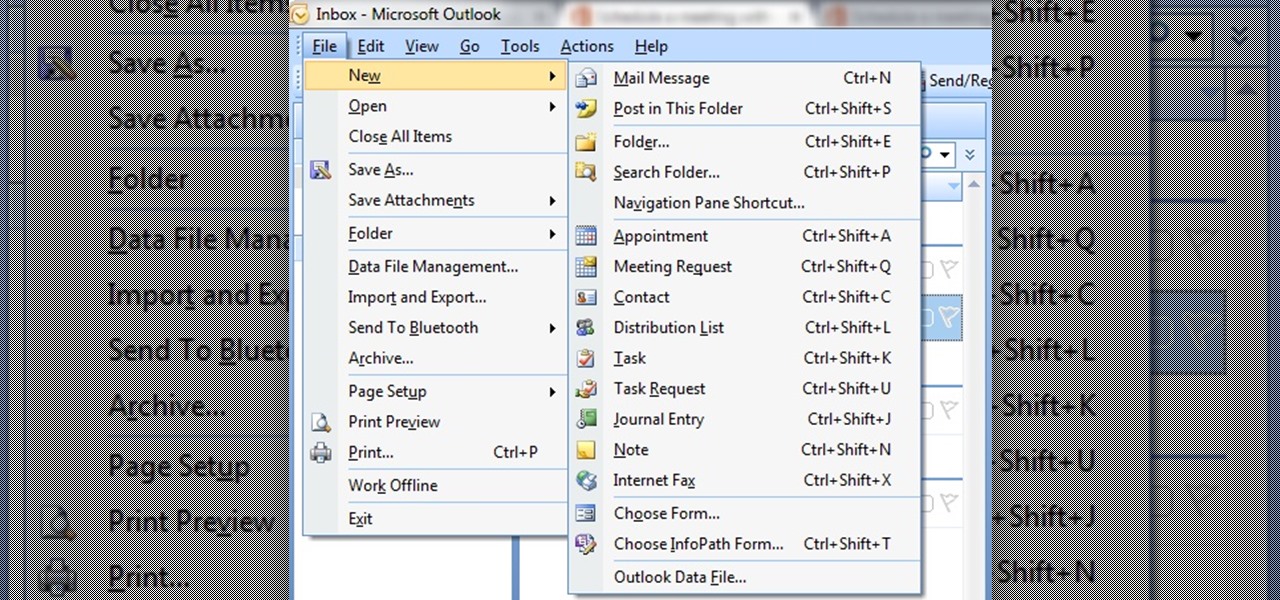
In this tutorial First, we will discuss what a meeting is, How can we schedule it in Outlook. A meeting can be defined as a mass of two or more people have a common motive. All the people present in a meeting can share their ideas and exchange information, to carry out the actions to achieve their goal. This tutorial helps those people who are looking for the steps to Schedule a Meeting in MS Outlook.

Video: . If you're in the mood to hide eggs this upcoming easter here are 10 places inside your house where you can hide them, I gotta warn you though, it will get very messy!

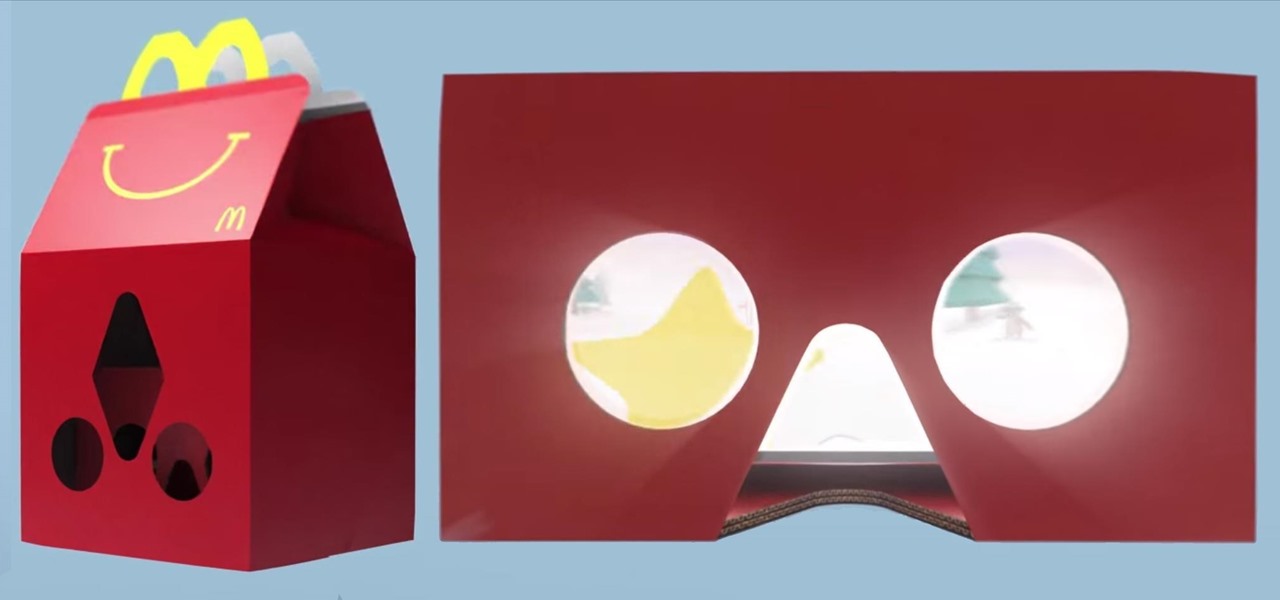
Another day, another company hopping on the virtual reality bandwagon. Today, it's fast food behemoth McDonald's, which is testing limited edition Happy Meal boxes that you can turn into a VR headset by punching out a couple holes and tearing along a few perforated seams. The resulting headset is a lot like Google Cardboard, with the lingering scent of fry grease.

By now, you've likely used or have seen friends and family use Face Swap Live on their phones. It's a fun little app for iOS (and soon to be Android) that harnesses current tech to—you guessed it—swap faces.

Welcome back to another episode of Java Tutorials, In today's tutorial, we'll be learning about what methods are, proper syntax when writing Methods, and why they are beneficial in a program's code.

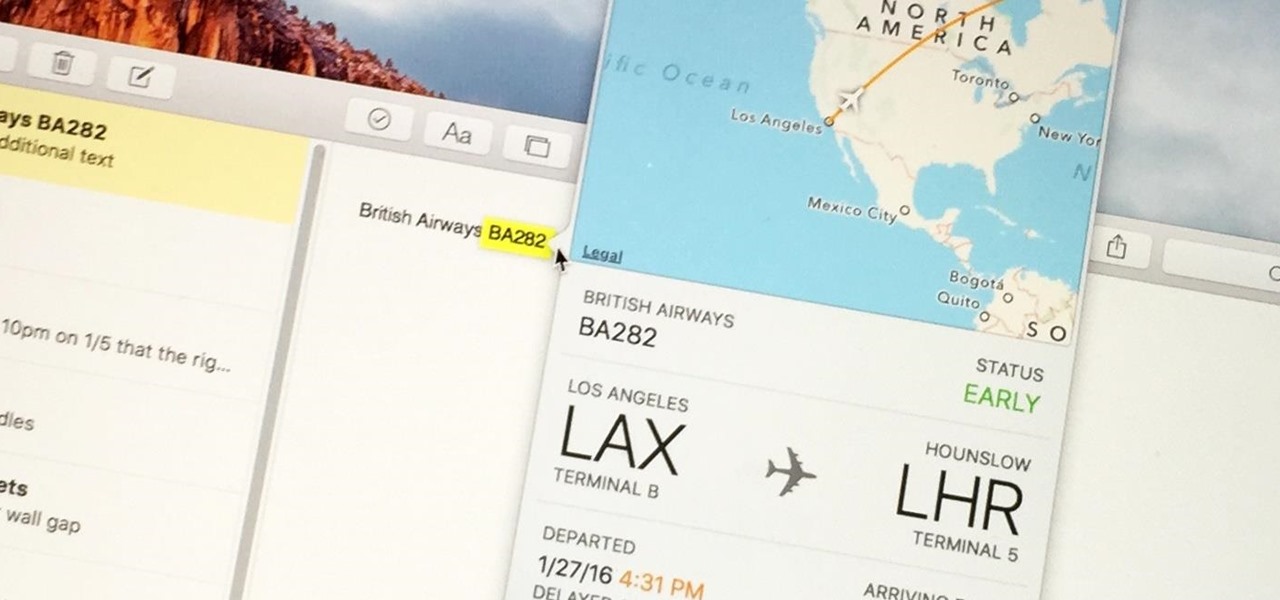
Turns out, you no longer need third-party flight tracking apps to get information on yours or others' flights—your iPhone and Mac can now give you flight details right from your Mail, Notes, and Messages apps.

Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, this is an excellent way to learn how to hack Wordpress, Joomla, and Dupral plus many more!

Now that Chromecast has taken the title of top-selling media streaming device and held onto it for well over a year, game developers absolutely have to take Google's $35 streaming stick seriously. As a result, we're starting to see big-time media and game companies throw their hats into the proverbial Chromecast ring, with new interactive offerings that pair your smartphone and your big screen in spectacular fashion.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - https://techkernel.org/2015/12/19/embed-metasploit-payload-in-apk-manually/
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...

Hello everyone. I've recently made the annoucement of the Null Byte suite of tools, and we've covered how to download and install it. Now it's time we cover how to submit a tool for inclusion into the suite. It's relatively simple, but we need to get a few ground rules out of the way.

Hello again, ***UPDATE: Adding links to the other Two articles****
Greetings null-bytians. Say you have been able to penetrate your neighbour's AP, and of course you had spoofed your MAC address. Now you go on and test to see with excitement if the password really works and the MAC is still spoofed. You login successfully and you browse the web forgetting to check what your current MAC is. Well, if you may do an ifconfig command, you will see that your permanent MAC is being used. Oh!! and guess what, ... your real MAC has been logged. Even though there is t...

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.

Google has finally released the next version of the world's leading operating system—Android 6.0 Marshmallow. This latest iteration isn't as much of a visual overhaul as Lollipop was, but it packs in more new functionality than almost any update before it. Awesome features like Now on Tap, granular permissions control, and a deep sleep battery-saving feature called Doze round out the highlights, but there is far more to it than that.