Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.

So cute, so furry, and so chock full of parasites. While raccoons are fun to watch, they are neither friendly nor clean — and they can make you sick in more ways than one.

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

Who said sports need parity to be fun? For the third year in a row, the Cleveland Cavaliers are facing off against the Golden State Warriors on the NBA's biggest stage, and basketball fans everywhere couldn't be more excited.

While no longer native to the United States, hospitalization from malaria occurs in this country more than most would believe. Why is that, and what can you do to protect yourself when you travel abroad to regions where malaria is active?

The office of your physician, or your local hospital, is where you go when you need medical care. But it could also be where you could pick up a life-threatening infection.

With a predicated increase in the number of Lyme disease cases in the coming spring season, new research endorses the use of bait boxes to control ticks on the rodents that serve as their hosts.

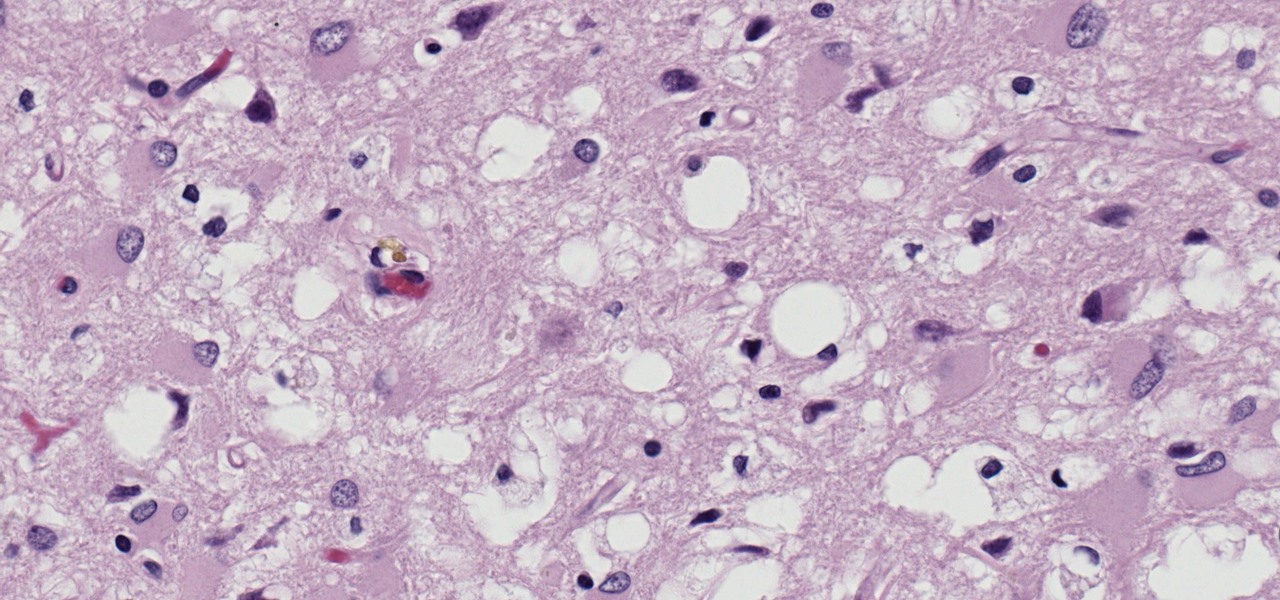
Prion diseases are a group of infectious brain diseases that causes extensive tissue damage, resulting in sponge-like spaces in brain tissue. Prions include Creutzfeldt-Jakob disease in humans, bovine spongiform encephalopathy (often called mad cow disease), and chronic wasting disease in hoofed ruminant mammals.

A recent study underscores a connection between climate change and infectious disease, raising concerns about our quickly warming planet.

Kuru is called the shaking disease, its name derived from the Fore word for "to shake." Caused by an organism that infects the part of the brain that controls coordination, people afflicted with kuru shake uncontrollably.

If you live with pets, you know where their tongue has been, yet you let them kiss and lick you all they want without even thinking twice about it. I've heard people say that a dog's mouth is very clean, and that their saliva, delivered by licking, can help heal wounds, but is that really true?

A terrifying antibiotic-resistant superbug, one thought to only infect hospital patients, has made its debut in the real world. For the first time ever, the superbug carbapenem-resistant Enterobacteriaceae (CRE) infected six people who hadn't been in or around a hospital in at least a year, and researchers aren't sure how they got infected.

WordPress did not become what is arguably the most popular blogging and CMS platform on the planet because it was difficult to use. Rather, its user-friendly and rich feature set led to it finding a home on somewhere north of 70 million websites—and that's just counting blogs hosted on WordPress.com.

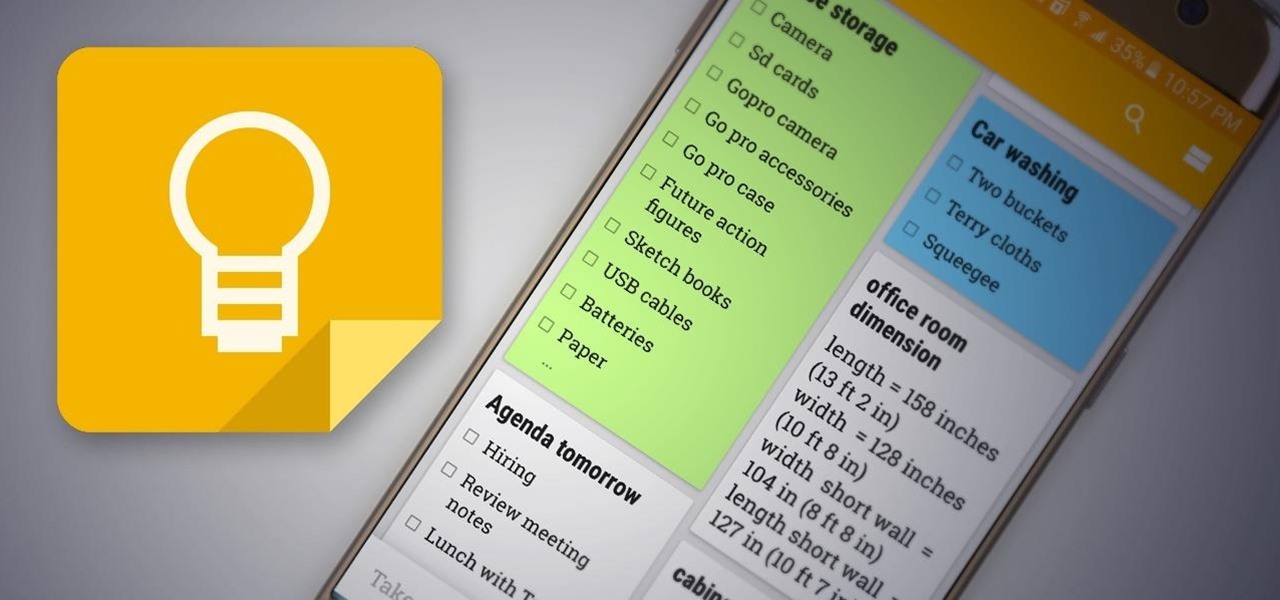
When it comes to note-taking, Google Keep is one of the most diverse and functional applications on the Android platform. Sure, there are a plethora of other note-taking apps to choose from, such as ever popular OneNote and Evernote, but Google Keep differentiates itself from the crowd with its user-friendly interface and Google Now integration.

When Microsoft release an update to the HoloLens Development Edition at the end of May, there were a bunch of cool new features added in. Among them: New voice controls that make working in the HoloLens operating system much easier.

With Passover soon upon us, many Jews are dreading a week (or eight days for Conservative and Orthodox Jews) of making matzo, the staple of their diet. Matzo is also known as "the bread of affliction," and I'm pretty sure it's because by day three or so you're convinced that matzo is the 11th plague.

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

Tonic water, seltzer water, club soda, and mineral water: these 4 types of "bubbly water" are often, erroneously, used interchangeably. But the truth is that each possesses unique qualities and uses that set them apart from each other.

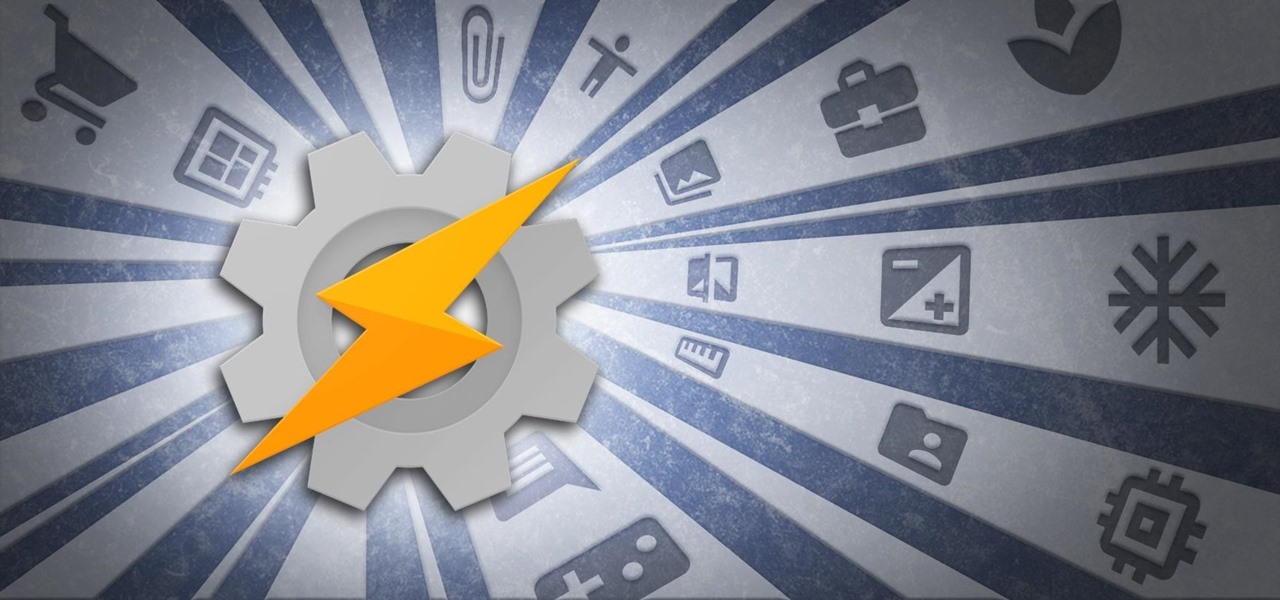
When anyone brings up Tasker, the first topic that always gets discussed is how powerful the Android automation app can be. But all of that power can be overwhelming for some people, so even if you're a Tasker pro, it's hard to share your awesome creations with friends that don't quite understand what's going on.

Video covering how to set up a Venn diagram. The video covers how to draw the diagram and then look at a set of data and place the data in the correct part of the Venn diagram. The sample problem is as follows.

Yes, screen savers are fun to look at for a few seconds, but those animations actually used to serve a purpose beyond simple entertainment.

In the last iteration of how to train your python, we covered if/else and conditional statements. We're going to diverge a little today and cover lists. Lists are simply that, lists. It is a set of values located under one variable. Now that we know the definition of a list, let's learn about them! List Basics

It would only make sense that Google is one of the most active app developers on the Android platform, particularly when you consider that they develop the platform itself. From my count, there are an astounding 117 unique apps that the search giant and its subsidiaries have published on the Google Play Store.

Is this what happens when lightning hits sand? It turns out that when lightning hits sand, it makes little holes in it. Sadly, this picture was part of an internet hoax that circulated in 2013.

In most cases, when the free trial of software is over, that's it—you're left to either pay for it or find an alternative. But what happens if the trial wasn't long enough to sell you on the product? It'd be nice if there was a way to test it out again without having to whip out your credit card.

Microsoft's new voice-enabled virtual assistant, Cortana, is a lot like a blend of Siri's personality and Google Now's predictive capabilities—but the best part is it's baked right into the taskbar in Windows 10.

One shrinks their nose when the name of Durian fruit is brought up but are you aware of all the health benefits it can provide? The Durian fruit on its own can help control Blood pressure, blood sugar, Anaemia and depression. Not only this, the fruit has the miraculous qualities that can prevent cardiovascular diseases, better the digestive system, better the Libido and provide instant energy. For all the skin conscious people, here's news for you! The fruit can delay ageing process and make ...

While you may not have loads of secret files hiding on your computer, there might be one or two items that need a little extra security, like a file of website logins or a folder of risqué photos.

To play Minecraft with mods you will need to install Forge. Most people think this is hard to do, not so. It is very simple and in less than 5 minutes you can be playing Modded Minecraft.

A man by the name of Marc Kerger is out to prove that he's the number one fan of the game TETRIS by building a playable TETRIS shirt for the game's 30th anniversary.

Welcome back, my aspiring hackers! In recent tutorials, I have made reference to the name and location of the Linux devices in the file system, such as sda (first SATA or SCSI drive). Specifically, I have mentioned the way that Linux designates hard drives when making an image of a hard drive for forensic purposes.

This is for people who are already proficient at doing basic pull-ups and chin-ups and want to take their training to the next level. It's also pretty funny for anyone who enjoys a bit of gym humor.

Learn how to make a paper origami teo flower instructions. This origami flower is my improvisation, and I haven't seen any similar flower from the nature. I named the flower to my wife Teofila (Teo) because i gave to her the first model of a complete paper flower :). The model is easy and the stamens make the flower looks one idea more beautiful :)

Say "hola!" to the independent Finnish phone company, Jolla, and its new eponymous smartphone of the same name.

Video: . Iconici Tv MMA Host Naiya Marcelo caught up with with Bellator middleweight fighter Brian Rogers "The Professional Predator" at Factory X Muay Thai/MMA/BJJ Gym in Englewood CO.

Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful.

This magical, glowing mixture is very strange, with an equally strange name (Oobleck), because it feels like moldable pizza dough in your hands one second, and like liquified goo the next.

Video: . How to Remove a Callous from your Feet.

Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes.