Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

If you have a taste for sweets, you have at least one thing in common with mosquitoes. While too much sugar is unhealthy for humans, a new product makes sweets deadly to mosquitoes.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

Mobile augmented reality developer Blippar has updated its mobile app for iOS and Android with an augmented reality face profiles feature based on the company's real-time facial recognition engine.

Windborne microbes shifting in the snows of the great ice sheet of Greenland may be able to neutralize some of the industrial contaminants oozing out of the melting ice.

As a part of the already crowded field of diseases transmitted by ticks, you may not know the disease babesiosis, a dangerous infection caused by a parasite that infiltrates blood cells.

Six people have died from fungal infections in Pittsburgh hospitals since 2014—that fact is indisputable. The rest of the situation is much vaguer. A lawsuit has been filed against the hospitals on behalf of some of the deceased patients, alleging that moldy hospital linens are to blame. While the lawyers argue over who's at fault, let's look at how this could have happened.

Humanity is standing on an infection precipice. As antibacterial resistant grows, we're running out of options, and a recent scary case of total antibiotic resistance is a frighting view of our potential future. In the end, it was septic shock that took the life of a 70-year old woman with an incurable infection. One of few such cases in the US, her death could nonetheless be the shape of things to come.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

There's nothing more maddening than opening the office fridge and discovering your lunch is gone. Put an end to the stealing with some of these strategies. This video will show you how to deter coworkers from stealing your lunch.

Step 1. Understand that opening a coconut requires a considerable use of precise force. Because you are using a knife or cleaver, it is very important that you keep your fingers and other body parts away from the blade. Step 2. Clear off a stable cutting surface. Step 3. Begin scraping off the white, sinewy upper layer around the pointed top of the coconut, using your knife. Scrape off the top layer until a brown ridge is revealed around the base of the pointed top. Right where this brown lay...

Identify the proper time to throw a knee kick. If you are grappling with an opponent, look for an opening where you can knee-kick him in the ribs or side of the thigh. If an opponent is trying to tackle you around the waist or take you down by grabbing your legs, introduce his face to your knee. If the opponent is standing in front of you and there is not enough room to throw a fully extended kick, grab him and try a knee.

Got school spirit? The cheerleading squad's the perfect place for you. Here's how to make the team. Step 1

Learn how to mingle. If the idea of walking into a room full of strangers strikes fear into your heart… welcome to the club. But there are ways to overcome this common social phobia.

Looking to get extra distance from your swing? Who isn't? In this video golf tip, Mel Sole identifies five keys to help you tap into your power, and provides a drill that focuses on the center of your power source: hip rotation.

Did you get duped into buying fake MAC cosmetics? Don't let it happen again. This two part how to video teaches you to identify real MAC makeup from the fakes.

This video is a demonstration of the most fundamental DJ technique, beat matching, by DJ Magic Wong. A demonstration of how to count and identify a phrase, how to match beats and crossfade.

Salad isn't everyone's first choice for a main dish, but when you try out this shrimp salad, you're sure to start making it your entrée instead of your side.

In this tutorial, Betty shows you how to make her sister's famous lasagna. This meaty, cheesy pasta is very filling and the perfect dish to make for large gatherings or family dinners. Follow along and make this easy recipe that is full of flavor. Delicious!

In this super sized 16 part tutorial, you will learn how to draw and color Lara Croft aka Tomb Raider. Lara Croft is one of the most famous and sexiest characters in video games and this clip will show you exactly how to create this Manga character.

Start out playing the piano by learning one of the most famous pieces of music in the world. That song would be "Clair de lune" by Claude Debussy. And this video starts you out with playing and learning the clefs, flats, key signatures, and black keys that will help you begin playing this work of art.

Do you like music? How about the acoustic guitar? How about Brenda Lee? How about a Willie Nelson, Elvis Presley, or the Pet Shop Boys? Well, this video tutorial will show you how to play "Always on My Mind," most notably by Elvis Presley. This instructional guitar lesson will teach you a few tips and tricks for playing an arrangement of the famous song.

Have you ever had a great meal at your local restaurant and wondered how to make it yourself? Or perhaps you've found yourself stumped at what to make for dinner based on the random provisions in your kitchen? Now, you can discover solutions to these food-based problems via Snapchat's computer vision wizardry.

Who's ready to let future Facebook augmented reality smartglasses read their brain? Well, ready or not, the tech giant is making progress in the area of brain control interfaces (BCI) by funding research.

In recent years, unwanted calls have become a top priority for the FCC. In 2016, analysts estimated that US customers received over 2.4 billion robocalls per month. As a result, the FCC has provided carriers new tools to combat this problem.

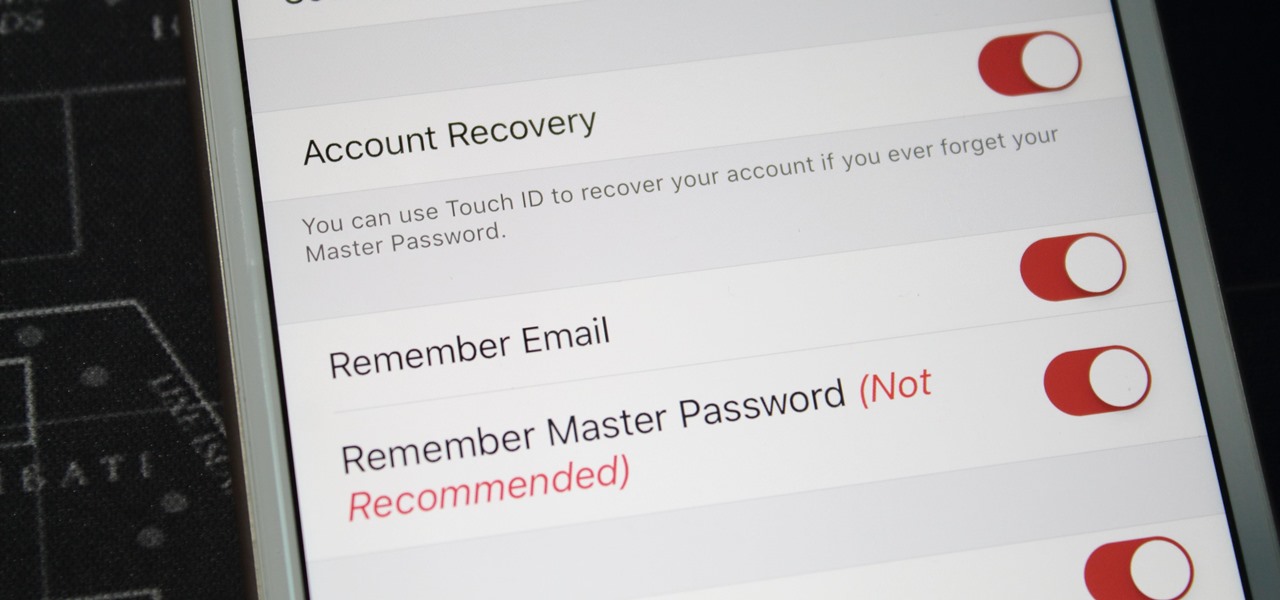
With any password manager, the only password you need to remember is the master password that locks the vault from both hackers and the company. This makes the master password very important. But what happens if you forget this password? Well, LastPass has you covered.

Augmented reality startup Nreal was a hit at this month's CES event, with some even calling the device a worthy challenger to the Magic Leap One.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

Now that we've had a chance to jump into the Lumin SDK documentation at Magic Leap's Creator Portal, we now have much more detail about how the device will function and utilize software than any single piece of content released by Magic Leap to date.

This is a tale about microbes, a man who became a hermit, and the parchment that carries both of their stories.

Love is the spice of life — it is also the microbes that couples share through sickness and in health, through the bathroom and in a hallway.

Montezuma's revenge, the runs, the trots, or just diarrhea — everyone gets it sooner or later. What exactly is diarrhea good for, if anything?

The Deepwater Horizon oil spill that began on April 20, 2010, was the largest maritime oil spill in history. Killing 11 people and discharging 4.1 million barrels of oil and natural gas into the Gulf of Mexico, the event was an unparalleled personal, environmental, and business disaster. It was also the first major oil spill to take place in the deep ocean.

Add breathing in your house as another possible danger to your health. If your home is sick, it's possible you could get sick too.

Tesla hopes high-level personnel changes will help it gain an edge in neural network knowhow for its models' self-drive features, following the replacement of its Autopilot chief and the appointment of a recent Stanford grad to head its AI and Autopilot vision research.

As summer heats up, new maps from the Centers for Disease Control and Prevention (CDC) gives us our best guess at where Zika-carrying mosquitoes could be hanging out this year in the US.

Citrus greening disease — caused by a bacteria spread by psyllid insects — is threatening to wipe out Florida's citrus crop. Researchers have identified a small protein found in a second bacteria living in the insects that helps bacteria causing citrus greening disease survive and spread. They believe the discovery could result in a spray that could potentially help save the trees from the bacterial invasion.

Breastfeeding is the ultimate in farm-to-table dining. It is sustenance prepared just for the baby and delivered with a very personal touch. Along with bonding, breastfeeding provides powerful protection to infants and young children in the form of beneficial bacteria, hormones, vitamins, protein, sugar, and antibodies manufactured on site to support infant health.