How To: Relieve constipation naturally
Learn how to relieve constipation naturally. When ya gotta go, ya gotta go. But what if you can't? Unburden yourself with these tried and true natural remedies, which really get things moving.


Learn how to relieve constipation naturally. When ya gotta go, ya gotta go. But what if you can't? Unburden yourself with these tried and true natural remedies, which really get things moving.

Abdominal thrusts—also known as the Heimlich maneuver—can be used to expel a foreign object lodged in a choking victim's windpipe. Watch this video tutorial to learn how to perform the Heimlich Maneuver (abdominal thrusts).

Invented in 1896 at the Waldorf-Astoria hotel in New York City, this is America's most famous fruit salad. One taste of this crunchy, juicy, sweet, and tangy salad, and you'll know why it's such a favorite.

This video is a demonstration of how to paint a traditional Japanese Sumi-e subject in the plum tree. Plum or ume blossoms tells us the spring has come. "Plum blossom, recall me, When it blows in the spring ---" 9th century politician and poet, Michizane Sugawara recites in his famous poem or tanka.

There's a simple reason this tangy bread is famous – it's delicious! You Will Need

Do plants wilt at the sight of you? With these tips, anyone can keep a houseplant alive, even you! You Will Need

Before you throw your next steak on the barbecue, see what grilling experts do to ensure that it turns out tender and juicy. Watch this video to learn how to grill the perfect steak.

Staying inside during the coronavirus pandemic isn't easy for most of us. As important as it is to keep away from others, it can be challenging to keep to ourselves day after day. That's why mobile game developers are stepping in to help; many are making their games free for a limited time, to provide some much-needed fun during scary times.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

Metadata contained in images and other files can give away a lot more information than the average user might think. By tricking a target into sending a photo containing GPS coordinates and additional information, a hacker can learn where a mark lives or works simply by extracting the Exif data hidden inside the image file.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

Your childhood "social networking" may have been to go outdoors to the neighbor's — and outdoors is a great place for kids to be. But these days, the terms educational, digital media, entertainment, and toddlers don't have to be mutually exclusive. Like most things in life, it's about balance, and these apps can aid your child with social-emotional development when not playing with friends.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.

As you're surely aware, your phone can be used against you. Thanks to our cameras and microphones, a clever hacker can obtain access to your device and invade your privacy. But spying isn't limited to just these two sensors — gyroscopes, proximity sensors, QR codes, and even ads can be used to paint a very clear picture about who you are and what you're currently doing.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

Fast food is a guilty pleasure in which we all indulge. When you're short on time and long on hunger, being able to whiz through the drive-thru or run 'in and out' of a fast food joint can be a real lifesaver.

All kinds of people pretend to be someone they're not on the internet, including scammers, people attempting to wind others up, hackers and web predators. Almost all of these people will leave bases uncovered and they're all easy to expose when you understand how to. Here are my favorite ways of finding out when somebody is lying quickly. Image Search

If you've ever been in the kitchen making your grandma's famous cookie recipe and when it comes time for the brown sugar found yourself stuck with an unmalleable, rock-hard chunk instead of measurable granules, then you will appreciate this tip.

These drills are named after the moves of the famous basketball player Michael Jordan. In this sports how-to video, Farmington HS boys basketball coach Shane Wyandt and team demonstrate the 2-spot Jordans drill. Watch and learn how to shots basketballs like Jordan himself with these 2 spot drills.

Learn how to play probably the most recognized melodic licks in bluegrass banjo with this tutorial. This lick is based on a Bb pentatonic scale. You can hear this lick in a lot of Ben Eldridge's playing though it may date back farther than the 1950's. Watch this how to video and you will be able to play this famous lick based on the Bb pentatonic scale.

This dance tutorial teaches you how to do swing dance routines from great classic films.

Learn how to do the ace transportation magic trick made famous by David Copperfield. With this easy to learn step by step tutorial you to can become a magician.

Learn how to play the most famous of ALL ancient Jewish melodies on King David's Lyre; "Hatikvah" - "The Hope" This ancient melody was later to be made the official National Anthem of Israel.
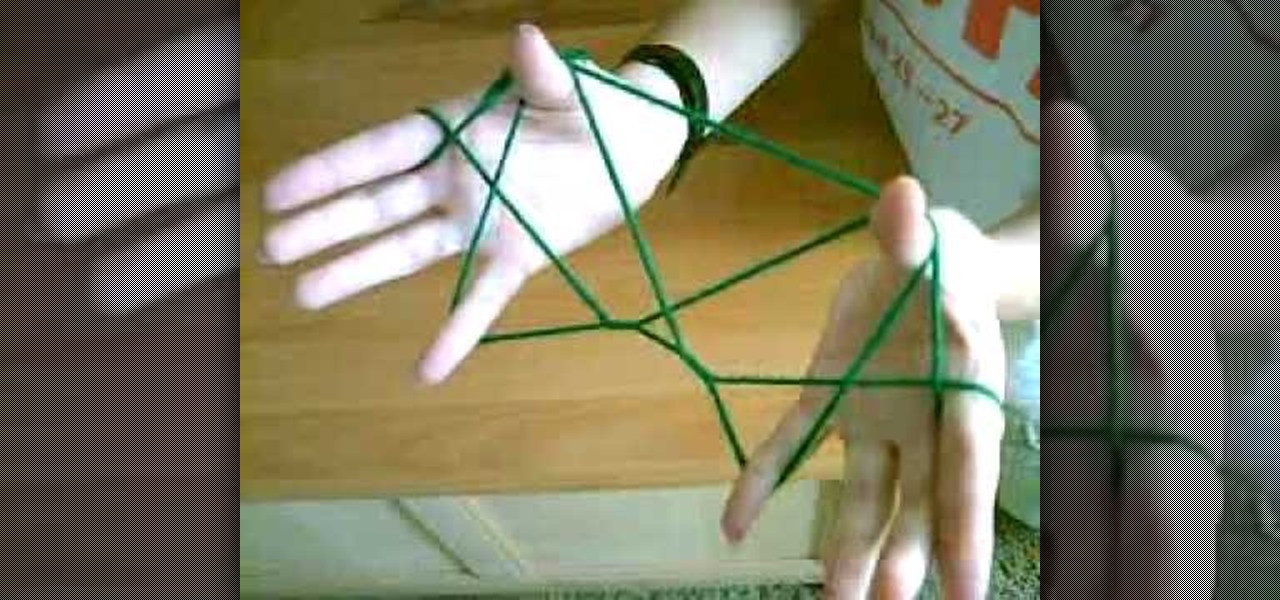
Jacob's ladder is a famous string game that most people don't know how to do. Here's how!

This video demonstrates the finger style used in the famous Beatles song "Hey Jude".

In this article, I'll be explaining the basics of how microcontrollers work, physically and virtually. First off, microcontrollers are no simple thing, so don't be discouraged if you find it mind-boggling! The world of microcontrollers is fascinating, engaging, and an awesome hobby; it never gets boring. I'll be focusing more on I/O and analog based microcontrollers, such as those running Arduino, and using Atmel chips as examples (these are most commonly available, and easy to program).

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

In a new update, the iPhone 16 lineup is finally getting Visual Intelligence, a feature that lets you instantly gather information about anything around you just by snapping a picture.
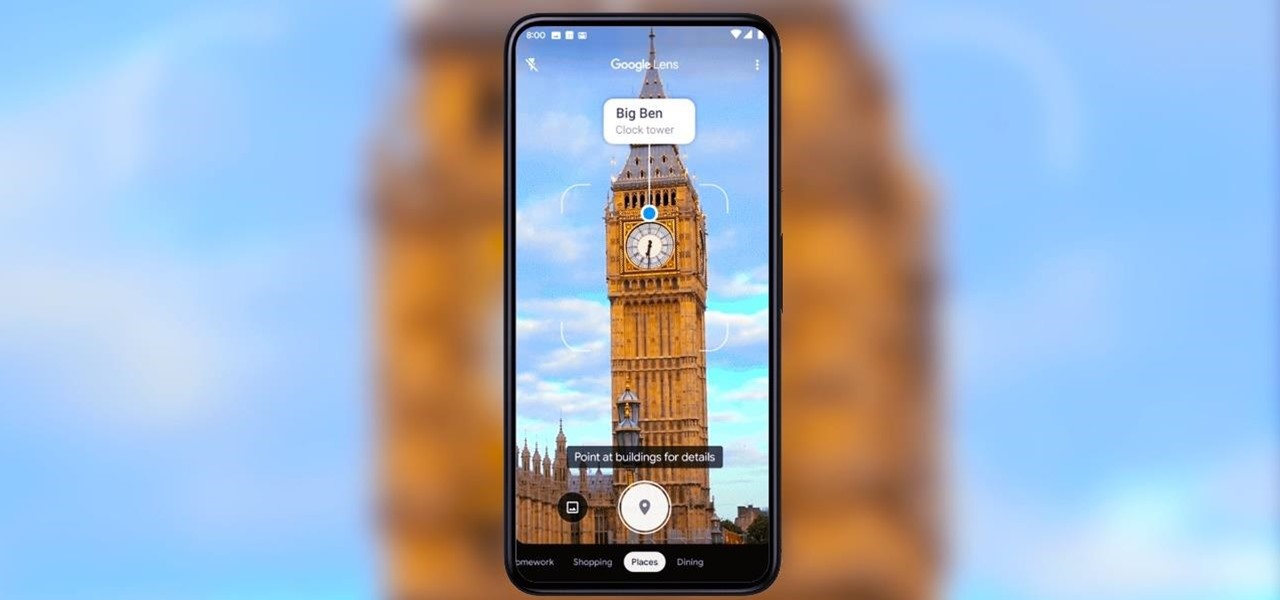
This week, Apple unveiled its own version of Google Lens in the form of Live Text. In response, Google just hit back with a new feature for its visual search tool called Places, a new search category that can recognize landmarks and return information on them within the camera view, which Apple touted as a capability of Live Text during its WWDC keynote.

If you've recently built a Wi-Fi spy camera out of an ESP32-CAM, you can use it for a variety of things. A baby monitor at night, a security camera for catching package thieves, a hidden video streamer to catch someone going somewhere they shouldn't be — you could use it for pretty much anything. Best of all, this inexpensive camera module can perform facial detection and facial recognition!

Wireless headphones are convenient, comfortable, and more common than ever before. With the massive proliferation of wireless earbuds, it's hard to identify which ones are good and which ones just want to look like they're worth the price. Avanca T1 Bluetooth Wireless Earbuds are high-quality wireless earbuds with excellent functionality and a low price of $29.95 now that they're 50% off.

The gold standard in any business is reaching the front page of Google. You need to get your brand in front of audiences. While it can seem daunting, it's not impossible when you master SEO best practices.

For the average consumer, augmented reality is a fun way of dressing up photos and videos for social media. However, AR is also gaining momentum as a medium for storytelling, particularly in sharing powerful messages.

Every single photo you take carries with it a considerable amount of seemingly "invisible" yet important information known as metadata. Although metadata is usually helpful to sort your photographs by location and date, that same information could potentially be used against you, especially if the pictures are taken during a precarious situation.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

I've covered augmented reality apps for about three years now and the most useful mobile app I've encountered over that time is Google Lens.