With every new Galaxy flagship release comes the age-old dilemma: do I choose great hardware or great software? For years, Samsung has given users the best components available on any smartphone. The problem is the software is an acquired taste. But there is something you can do about it.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

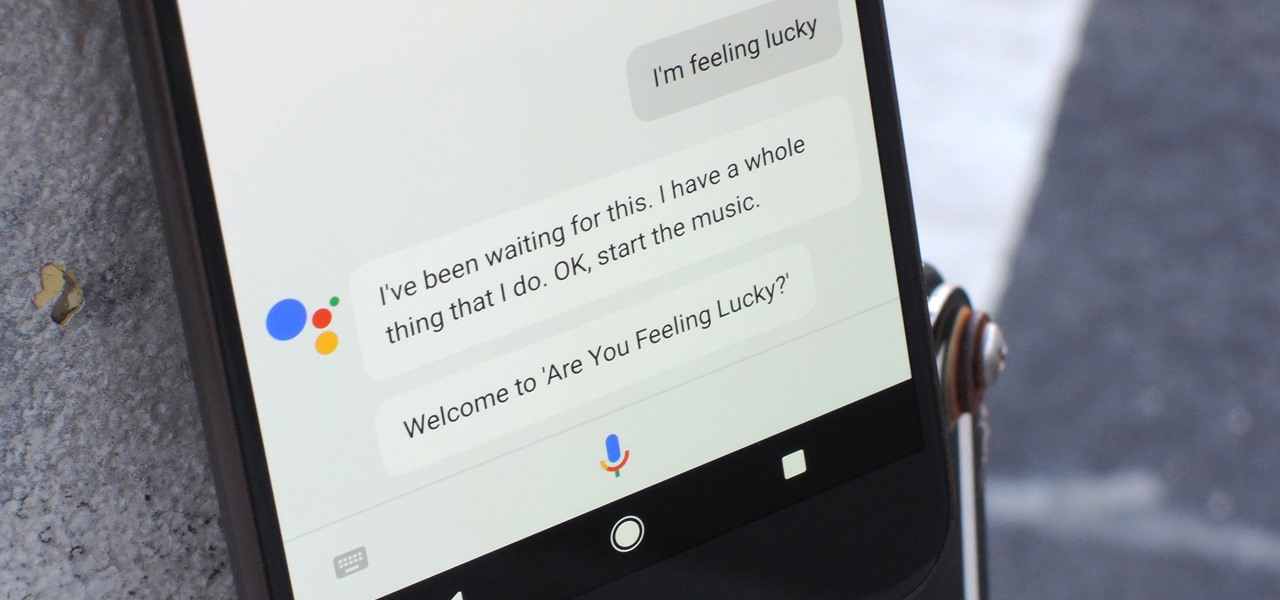
Despite a rocky start with plenty of feature disparity, the Google Assistant now provides a pretty consistent experience regardless of what device you're using it on. Be it Android, iPhone, or Google Home, the AI behind the Assistant is virtually identical — including its quirky commands and funny responses.

Whether scheduling meetings, events, tasks, or even keeping tabs on the weather, a good digital calendar can help you stay on top of your game in ways that a normal calendar could never do. Indeed, there are many calendars to choose from, but Google Calendar is one of the best due to Google's excellent cloud service, feature-rich web-client, and their easy-to-use Android and iOS applications.

If you're one who enjoys a good DIY project, or if you're just tired of paying exorbitant labor fees to have your vehicle serviced every 5,000 miles, changing your own oil can be a rewarding endeavor. Even though cars and trucks are becoming increasingly over-engineered these days, manufacturers generally see to it that the basic maintenance items can still be taken care of in your driveway with a few common tools.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

First of all you shall need a program called "Disk Inventory X". You can download this program from the link Once you have downloaded you have to install this program. Now launch "Disk Inventory X". This shall take some time to load because it processes your hard drive and looks at all the files and folders. This program provides you a visual representation of the files that are there in your hard drive. Therefore for every folder that is shown in this application it shows...

For furniture or wood projects, adding an aged wood look can give real character and interest to an otherwise ordinary object. With a little sanding, stain and lacquer to finish you can transform any wood object.

Bird watching is a great activity to do on your own or to spend time with the whole family. Look for the habitat, coloring, behavior and call of this beautiful bird and enjoy its beauty and soft cooing.

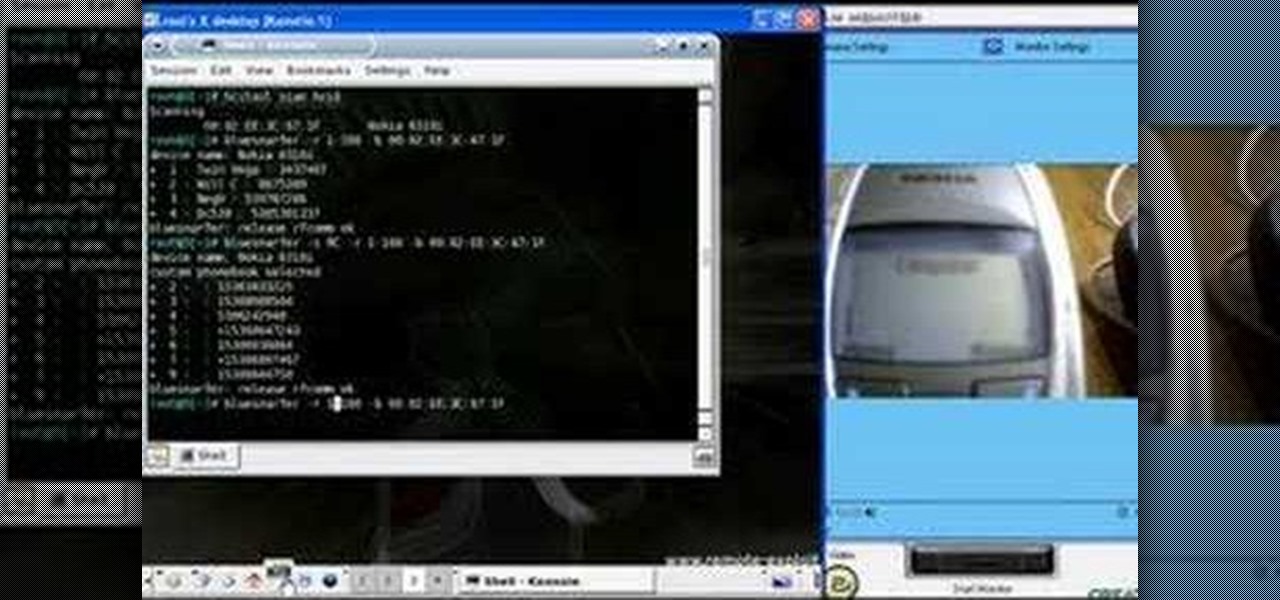
Check out this video tutorial to see how to bluesnarf a Nokia 6310i handset (cell phone). What is Bluesnarfing exactly?

The reeds, cover pins, keys and the bass are a few of the parts you'll need to identify and disassemble on your accordion. Learn more in this free video series that will show you how to safely and easily remove the different parts of your accordion.

In this video series, our expert will show you how to safely operate an electric stapler, how to identify its parts, and how to care for your electric stapler. Forget about trying to use an ordinary office stapler. Electric staplers supply all of the power, and as you'll see in these videos, they're easy to use!

In this video series, learn how to maintain a healthy iguana. Our expert, Nichole Bragg, gives you information to keep your lizard as healthy as possible. Learn how to clean an iguana's cage, and learn how to keep your iguana safe from other pets. Nichole shows you how to identify mites, ticks, dehydration, and respiratory infections in iguanas. So, if you have a beloved lizard that you want to keep healthy, learn how to care for iguanas today!

This series will teach you the basics of sewing machine operation. Our expert will identify the parts of the sewing machine for you, as well as explain some of the general functions and abilities of the machine. Tips include how to thread a sewing machine, winding and installing the bobbin, selecting the proper foot, and turning the fabric.

This series will focus on the basics of drawing landscapes. Our expert Neha Ahuja shows you how to draw a landscape in these free video art lessons, including what sorts of art supplies you'll need to make your drawings, where to find examples of landscape drawing, and how to identify the distinguishing characteristics and details that define landscape drawing.

In this video series, watch as expert kayaker James Sullivan teaches beginning kayaking tricks while playing in holes and waves. Learn how to find a good hole and identify a bad one, how to enter a hole from above and the side, how to move forward and backwards in a hole, how to get on a foam pile, how to find sweet spots, how to edge control in holes, how to enter a wave from above, how to avoid pearling, how to carve an edge, how to use the power stroke, and how to use forward and reverse r...

Fear not, proud homeowner! In this do-it-yourself home improvement video series, learn how to repair and maintain your wooden fence, with tips on identifying problem areas and using safety equipment. Get step-by-step instructions for repairing loose gate hinges, replacing rotten wood and removing chipped paint.

This video shows an updating of the famous Magdeburg experiment carried out by Otto von Guericke in 1654 using two metallic hemispheres to show the effects of atmospheric pressure - try it for yourself!

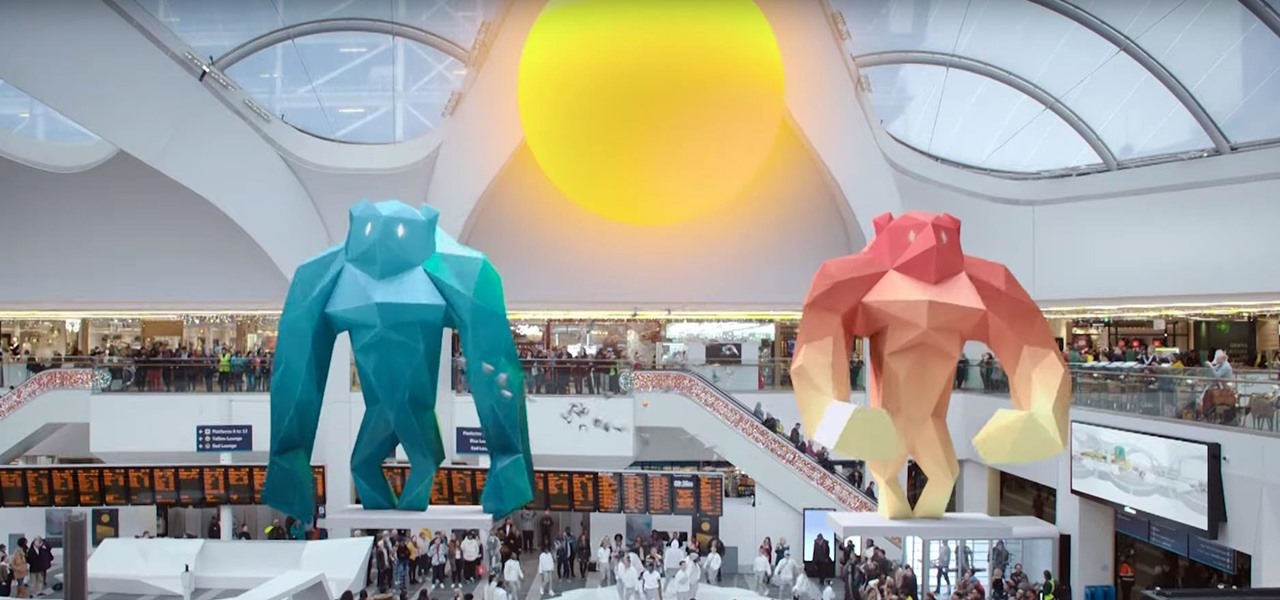
Since bringing augmented reality features to Search and Maps, Google has made them arguably the most useful augmented reality products in its portfolio.

In the three years since Snapchat launched Lens Studio, developers and artists have created more than 1.5 million AR camera effects with the desktop tool.

Google Maps Live View is already one of the more useful examples of augmented reality on smartphones that is available to the average consumer today.

While conducting an OSINT investigation, it's important to be able to pull in information based on any clue you uncover. In particular, license plate information can turn up everywhere, from photos to live data to on your own street. You could use that data to find the VIN, see if a Tinder date has hit anyone, find out who's blocking your driveway, and so on. Skiptracer can help get the ball rolling.

In many urban areas, GPS doesn't work well. Buildings reflect GPS signals on themselves to create a confusing mess for phones to sort out. As a result, most modern devices determine their location using a blend of techniques, including nearby Wi-Fi networks. By using SkyLift to create fake networks known to be in other areas, we can manipulate where a device thinks it is with an ESP8266 microcontroller.

Starting with Android 9 and 10, Google made privacy and security the main priorities for Android updates. Both versions brought numerous changes to help erase the notion that Android isn't safe, but Android 11 might even have them beat.

If you've tossed around the idea of turning your interest in white hat hacking into a career in cybersecurity or IT, now's as good as time as ever to invest some time and energy into improving your skill set.

Anyone who has used Linux long enough is familiar with sudo. Short for superuser do (or substitute user do, depending on who you ask), it allows users to run commands as either root or another user on the system. From a hacker's point of view, sudo is often all that stands between them and root access. We'll be exploring an older vulnerability in sudo that allows a user to run commands as root.

While the airline, casino, cruise, and hotel industries are asking for government bailouts during the COVID-19 pandemic, companies around the US are giving away its apps and services for a limited time. So while you're stuck at home, keep your mind off of coronavirus with free movies, TV, music apps, concerts, internet, fitness sessions, classes, and more.

On March 13, President Trump announced during a briefing in the Rose Garden that Google was building a COVID-19 screening website to help Americans understand if they might have the new coronavirus. If likely infected, the site would also include the location of a local drive-through testing site to visit. So how can you access the screening website?

If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been compromised.

Smartglasses startup Nreal enjoyed some highs and endured some lows this week, as the company landed a product placement with Kevin Bacon but then faced production issues related to the coronavirus outbreak.

After the lackluster update that was iOS 13.3.1, we beta testers were in need of some excitement. Thankfully, Apple delivered the goods with iOS 13.4 developer beta 1, introducing fun new features like fresh Memoji stickers and a new Mail toolbar. Of course, that update was for developers only, so we public testers are thrilled that Apple just released the first public beta today.

Does TikTok scare you? Trust me, I get it. It's a strange, unfamiliar place to those of us not accustomed to its ways, populated by teenagers and college students with their own subcultures, memes, and humor. But here's the thing: TikTok has something for everyone, you included.

Sudo is a necessity on most Linux systems, most of which are probably being used as web servers. While the principle of least privilege is typically applied, sudo misconfigurations can easily lead to privilege escalation if not properly mediated. Which brings us to SUDO_KILLER, a tool used to identify sudo misconfigurations that can aid in privilege escalation.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

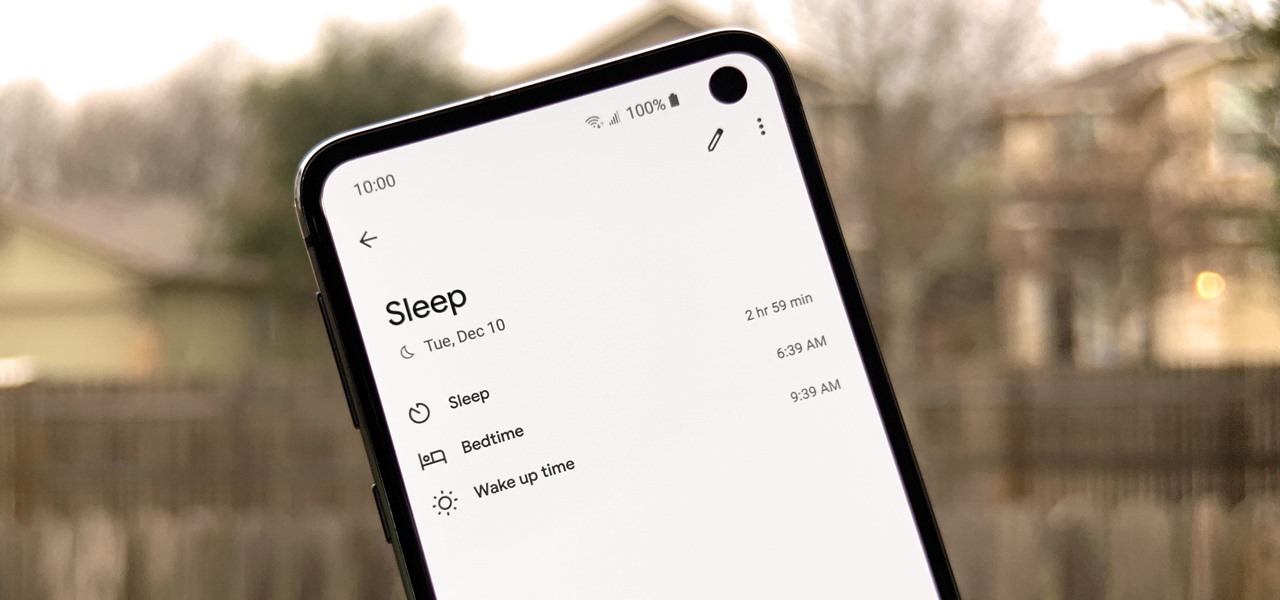
When trying to get fit, something that can easily be overlooked is your overall sleep quality. Your body needs sleep to recharge and it helps to maintain a healthy lifestyle, there's no denying it. Luckily, Google Fit can help you track your sleeping habits without having to jump through any hoops along the way.