Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes.

Over the past several weeks, I’ve had the pleasure of test driving Samsung’s next big thing, the Galaxy S4. After putting the GS4 through its paces, I have a clear picture of what this device is capable of. I’ve covered the features of the device before, and now I’ll tell you why I believe it's currently the best Android phone on the market. Initial Impressions

In my last article, I explained why text adventure games are some of the most Steampunk computer games out there. I even shared a free Steampunk text adventure game that I'd made myself!

First off, don't be frustrated. YOU CAN DO IT! Contrary to the message in the image above, it's NOT over. It's just beginning. And when it comes to solving the New York Times crossword puzzle, the old cliche does apply: practice makes perfect.

Paula Deen whips up a decadently rich peanut butter no-bake pie. Watch and see how easy it is to whip up this peanut butter pie recipe. The original cooking how-to video from this article was part of Paula's Home Cooking show hosted by Jamie Deen, Paula Deen. Paula Deen, owner of Lady and Sons, a famous Savannah restaurant, is Food Network's resident southern chef.

Two years ago, the 50th anniversary of the moon landing gave flight to a handful of Apollo 11 augmented reality apps and experiences, including one from the Smithsonian Channel.

A good smartphone can be the perfect workout companion. You have music for motivation, videos for pushing through boring cardio sessions, GPS to keep you on course, and even an array of sensors for gathering data about your workout. But not all phones are created equal when it comes to helping you stay fit.

Smartphone technology has become as ubiquitous as automobiles. In Austin, Texas, a city that is widely known as the "Live Music Capital of the World," smartphones have been embraced by the music community not just as a way to document and promote, but to create music.

Since we wouldn't have Android without Google, everyone has come to realize that the Pixel smartphones are a prime example of what an Android smartphone should be. With so many unique software related features, no wonder people want that Pixel experience.

I noticed the neon yellow sign at the new location of Pho Bar in Chinatown right away. The sweeping cursive yellow letters spell out "Crazy Rich Broth"; the same phrase printed on the back of servers' shirts. It's the kind of minimalist but colorful design feature that is especially popular on Instagram at the moment — shots of patrons in front of a glowing sign.

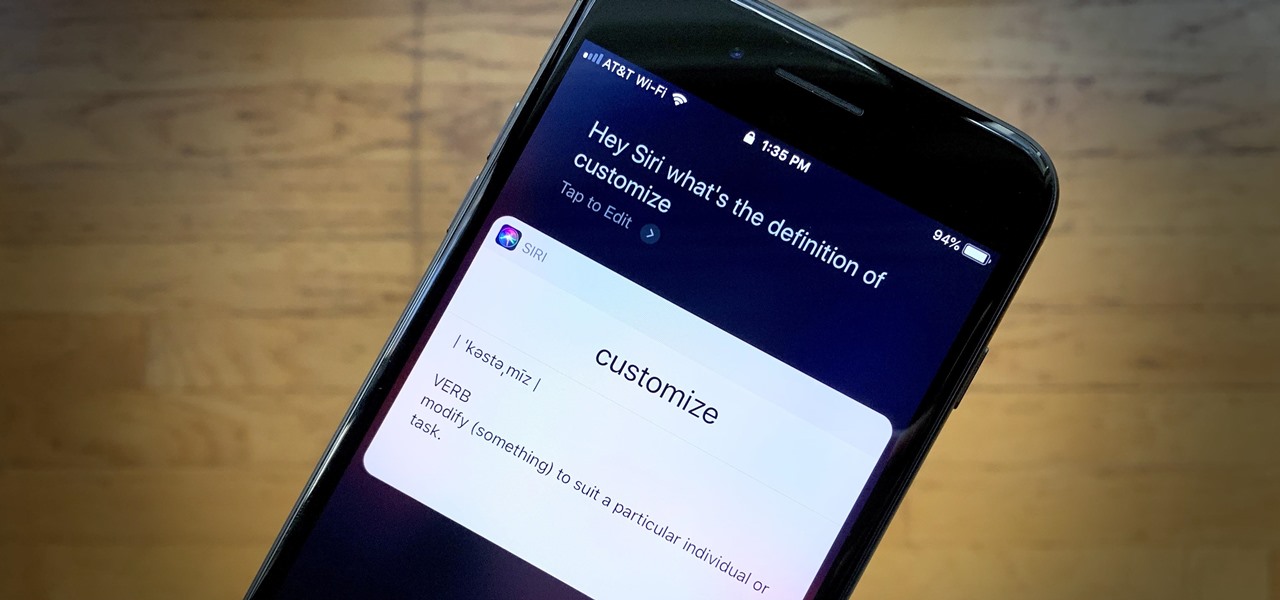
Out of the box, Apple's digital assistant could be a godsend or a nuisance, depending on your daily interactions it. No matter which camp you fall into, Siri can always be better suited to your personal needs with a little customization. You can make Siri a powerhouse not to be reckoned with, or you can minimize its presence if you only need Siri help sometimes — all without any jailbreaking.

Overall, iOS is more impressive than ever with its stability enhancements, security tools, suite of apps and services, and intuitive user interface. With each passing update, things just get better and better for iPhone users. But don't think for a second that this is all because of Apple's genius — many of these features were at least partly inspired by tweaks made by the jailbreak community.

Hackers can be notoriously difficult to buy gifts for, so we've curated a list of the top 20 most popular items Null Byte readers are buying during their ethical-hacking studies. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2017 selection of hacker holiday gifts — just in time for Christmas.

Word games can expand your vocabulary skills in all sorts of exciting and creative ways. Because of this, both the iOS App Store and the Google Play Store are awash with word games, making it hard to differentiate between good and bad titles. This is especially troublesome if you're looking to purchase a game, as everyone hates to waste hard-earned cash.

There are a lot of Android phones out there, and chances are that someone in your life is looking for one this holiday season. Well, there also happens to be a lot of Black Friday deals on Android phones this year. So we've rounded up the best deals taking place on Black Friday weekend to help you save big.

Throughout this NR50 series, we have talked about the incredible growth the augmented and mixed reality space has seen in the last year. More devices, software, developers, and use-cases seem to arrive daily. For this growth to have occurred, it took the work of many people, from many different backgrounds and skill sets — and Next Reality wants to recognize them for all that they have done and are doing.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

Hi, everyone! Recently, I've been working on a pretty interesting and foolish project I had in mind, and here I'm bringing to all of you my findings. This guide's main aim is to document the process of building an Android kernel, specifically a CyanogenMod kernel and ROM, and modifying the kernel configuration to add special features, in this case, wireless adapter Alfa AWUS036H support, one of the most famous among Null Byters.

It may sound irrational, but I bet a lot of you actually avoid doing any work at work—but not on purpose. You might be simply struggling with motivation, or you might just be overdosing on the caffeine. Whatever the issue, getting focused takes lots of time and effort.

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.

Apple has yet another new game for Apple News+ subscribers on iPhone, iPad, and Mac. With the latest software updates, Sudoku officially joins Crossword, Crossword Mini, and Quartiles in the News app's Puzzles section.

When you download files from certain apps like Safari and Chrome on your Mac, those files are tagged with the "Where from" metadata attribute. Depending on where the file was downloaded from, this attribute may refer to the host's URL, a sender's email address, or another piece of identifying information. While not obvious, you can delete or even change this attribute.

Apple's built-in search on iPhone is an incredibly valuable tool you shouldn't ignore or underutilize, and we're here to show you why. So, buckle in because this list covers hidden and lesser-known Spotlight features that will leave you wondering how you ever lived without Spotlight Search on iOS.

Lidar, a technology first used by meteorologists and aerospace engineers and then adopted in self-driving vehicles, has slowly crept into consumer electronics over the last five years. If you have a Pro model iPhone or iPad, there's a good chance it has a lidar sensor, and you're likely using it whether you know it or not.

What started as an accessibility setting for hearing aids turned out to be a super helpful tool for anyone with a good set of Bluetooth headphones. The problem is that most iPhone and iPad users still don't know about it. If you're one of them, you need to see what this underrated gem in iOS and iPadOS can offer you.

There's a tool on your iPhone that can help you with your overall emotional well-being, one that can help you be more aware of your emotions throughout the day and build resilience against the stressors in your life.

There are some important new features in the Photos app on iOS 17 and iPadOS 17 that will streamline editing, give your pets more recognition, help you learn about the world you've captured, and even add a bit of fun to your day. There are even a few hidden tricks that may surprise you.

Generative AI, or GenAI, is the hottest thing in tech at the moment, particularly for its ability to create content,p including essays, images, and videos. After Microsoft added its own GenAI tool to its Bing web search engine, Google is eager to follow suit, and you can be one of the first to try out Google's new GenAI search tool.

Apple's upcoming iOS 17 is expected to include many new features first seen on Android, but there are also some exciting, unique features that Android needs to steal pronto.

Gaming just got easier, thanks to Apple. A secret feature on your iPhone or iPad makes it so much easier to beat that level or opponent you can't seem to defeat, and it can even help you learn to play a new game faster.

Whenever you're on a FaceTime call, you can use SharePlay on your iPhone or iPad to screen share, watch TV or movies together, work out with each other, and even listen to the same music at the same time. SharePlay also recently received a new skill that turns FaceTime into a portable gaming platform.

Now that Bard — Google's response to the revolutionary ChatGPT generative AI chatbot — is out in the wild, it's beginning to let its freak flag fly.

You may not realize it, but most of your apps include third-party tracking services that monitor your activity in other apps and websites to serve highly-targeted ads to you. But now you can stop the creepy behavior on an iPhone and Android phone.

If you haven't been using Spotlight Search on your iPhone, we've got ten reasons for you to start. Apple's made some significant improvements to the search interface available on the Home Screen and Lock Screen, and it's more useful than ever.

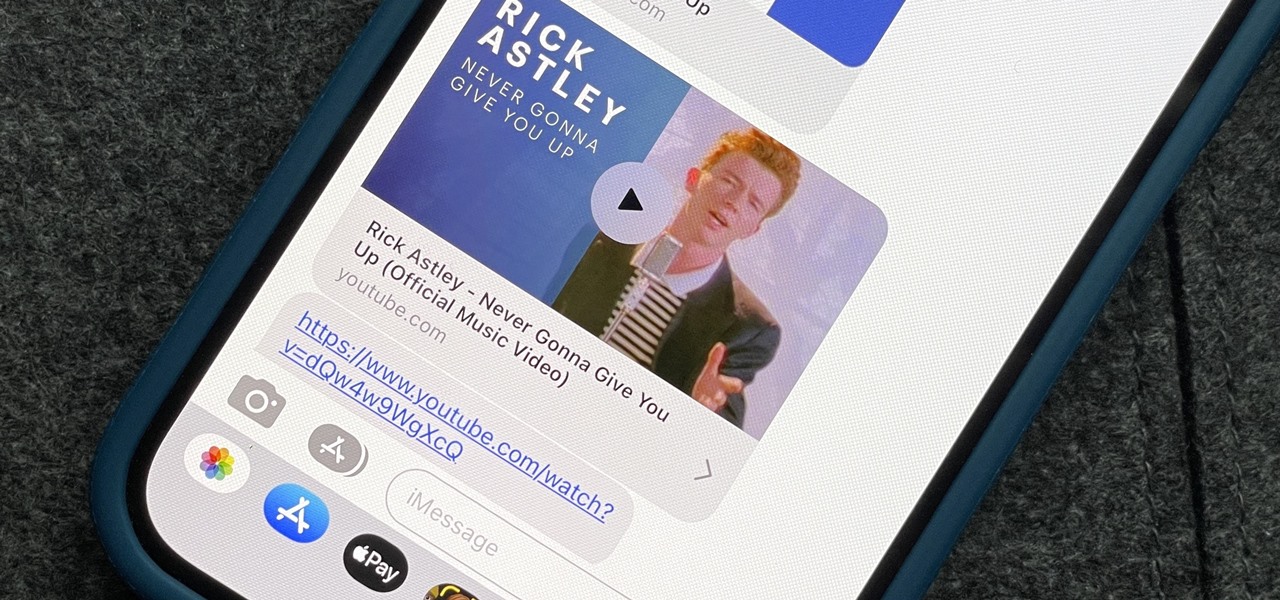
Apple automatically converts most URLs in the Messages app into rich link previews, but they aren't always pretty, and sometimes you just want to see the full URL instead. While there is no setting on iOS, iPadOS, or macOS that disables rich link previews in the Messages app, there is an easy way to show the URL complete with the scheme, domain name, and path.

Most of you have probably wondered at least once who has been checking out your social media profiles. While most platforms prohibit you from seeing who's viewed your profile, such as Facebook, Instagram, and Twitter, TikTok is one of the few places that lets you track profile visitors. And unlike with LinkedIn, you don't have to pay for the privilege.

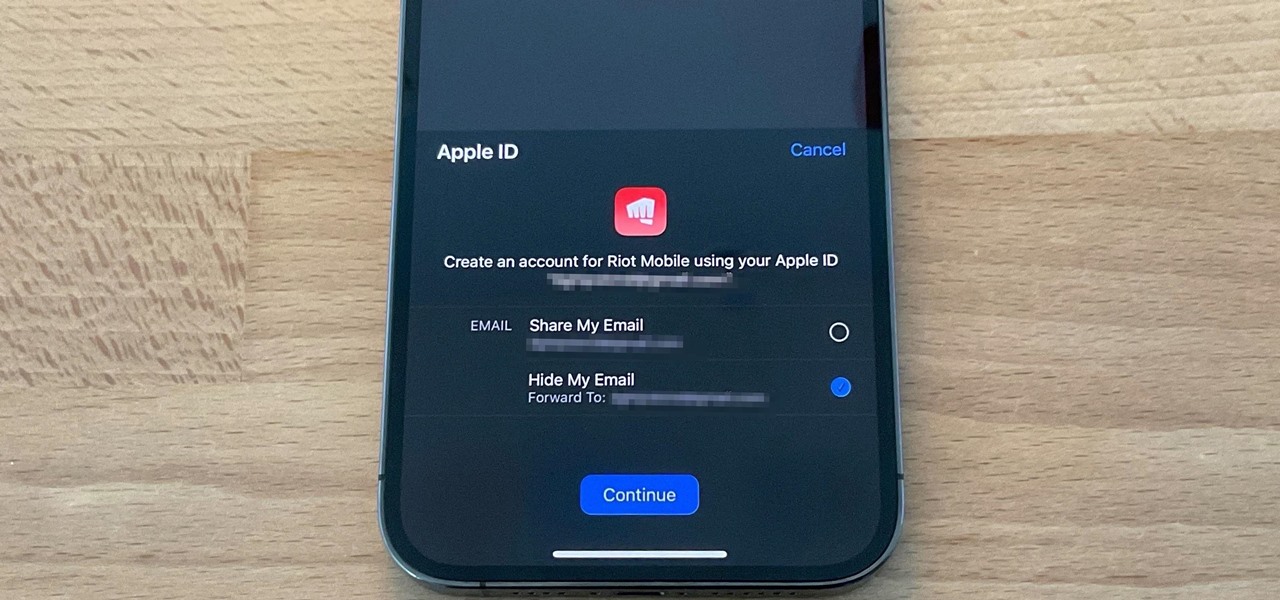
The "Sign in with Apple" service lets you create accounts with third-party apps and websites more easily using your Apple ID. More importantly, it can hide your personal email address using auto-generated disposable email addresses. However, it's easy to lose track of the accounts you use with Sign in with Apple, as well as any throwaway email addresses you used to hide your actual address.

I drop my smartphone a lot. Like an absurd amount of times. Practically multiple times a day. So it's surprising that my iPhone 12 Pro has lasted nine months without a cracked screen yet. Part of that has to do with the late-2020 model's durability, and the other part is thanks to my protective case.

The close of the second quarter of 2021 brought about a flurry of merger and acquisition and financing activity in the augmented reality industry, headlined by the acquisition of Ubiquity6 and JigSpace's new multimillion-dollar funding round.

A man-in-the-middle attack, or MitM attack, is when a hacker gets on a network and forces all nearby devices to connect to their machine directly. This lets them spy on traffic and even modify certain things. Bettercap is one tool that can be used for these types of MitM attacks, but Xerosploit can automate high-level functions that would normally take more configuration work in Bettercap.