When Kaci Hickox, a Doctors Without Borders nurse, returned to New Jersey from working with Ebola patients in West Africa in 2014, she was surprised by her reception. Instead of a quiet return to her home in Maine after four weeks on the front line of Ebola treatment, she was quarantined by the State of New Jersey in Newark. She later filed a lawsuit in U.S. District Court for violation of her civil rights, false imprisonment, and invasion of privacy.

If you were a particularly good little girl or boy this year, Santa might have finally brought you that cool new smartphone you've been wanting. Or perhaps you just took advantage of a great sale and treated yourself to a new gadget this holiday season—totally justifiable, and surely a well-deserved gift.

Last week, a new Kickstarter campaign arrived for a completely untethered, augmented reality headset for under $300 called Okularion. While at first glance, this unit looks very much like a Samsung Gear VR, one thing that sets it apart (aside from being untethered from a nearby computer) is that it does not require a smartphone. Well, that and it's an augmented reality headset as well.

With the recent news that New York County's District Attorney's office is trying to get into over 400 locked iPhones for use in criminal investigations, you can see why it's important to keep other people away from your personal data. The fact that it can and will be used against you in a court of law is just one reason to protect your phone, because even if you make sure to stay above the fray, identity theft and bank fraud are still very real threats.

A new hack has reopened an 8-year-old iPhone security loophole that Apple thought it had fixed back with iPhone OS 2.2. This is not one of those times when a theoretical attack gets identified and blocked quickly by Apple. On the contrary, it's a hack that actually exists right now, and it can have some serious real-world repercussions, so this is something all iPhone users need to be aware of.

Apple released 10.2 to developers yesterday, which contained some new features that you'll probably want right now on your iPad, iPhone, or iPod touch. Lucky for you, the Public Beta is pushing this same update out today.

Whether or not The Purge franchise will be as successful as Friday the 13th, A Nightmare on Elm Street, Halloween, or even the Saw movies remains to be seen, but it's definitely winning in the Halloween costumes department.

This morning, Google opened a pop-up showroom where anybody can visit to get a hands-on look at the new Made by Google hardware lineup. At 10 am the line at 96 Spring st, in the SoHo neighborhood of New York City, was growing but still manageable. As we waited to be ushered in, Google representatives came by to offer us coffee drinks prepared by a pair of baristas in the Peddler Coffee cart parked on the curb. "Now that's latte art," said the guy in line next to me when he saw that the foam-t...

Virtual reality, along with its siblings, has the opportunity to profoundly change the way we interact with all things digital. As a visual medium, we often don't think about the impact on audio, but it plays a significant role nevertheless. When it comes to music—and music videos—the possibilities are enormous.

Hello guys, I recently made a how to about whatsapp but the problem with that script is that it is way to long and you need to copy and paste it so many times so I made a new one that works just fine and is more easy to use lets get into it (Here Is How The Code Supposed To Look)

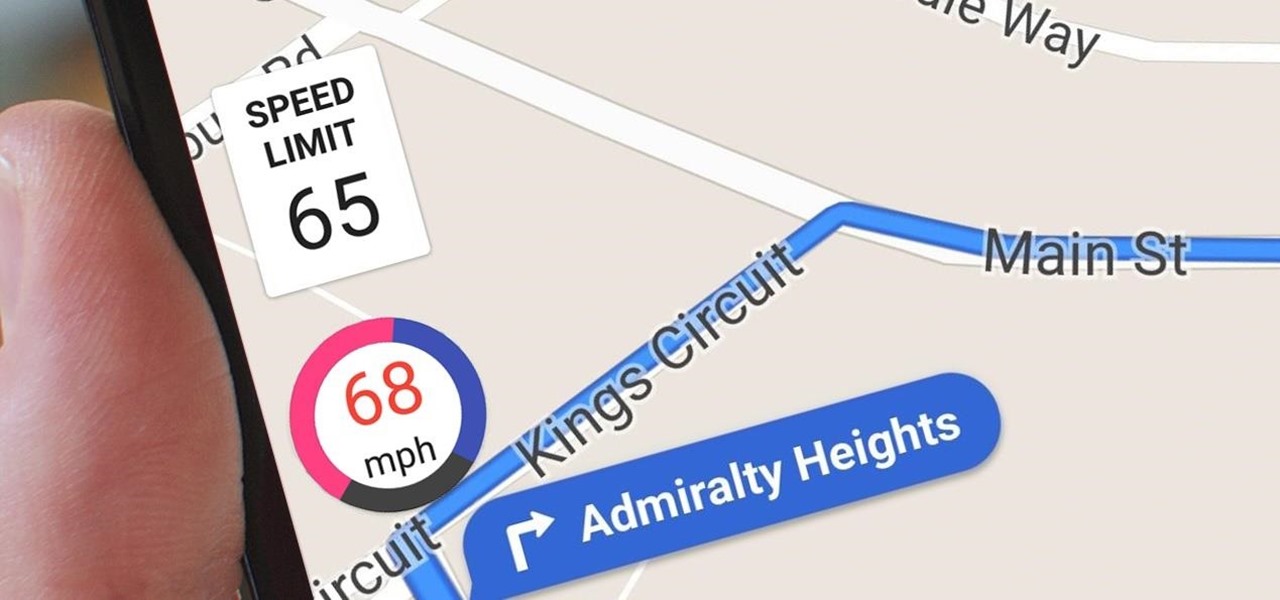
Google Maps does a lot of things well, but one feature it's always been lacking is an on-screen speedometer. Well, now you can add one with Velociraptor, and you can even set it to alert you when you're traveling above the speed limit.

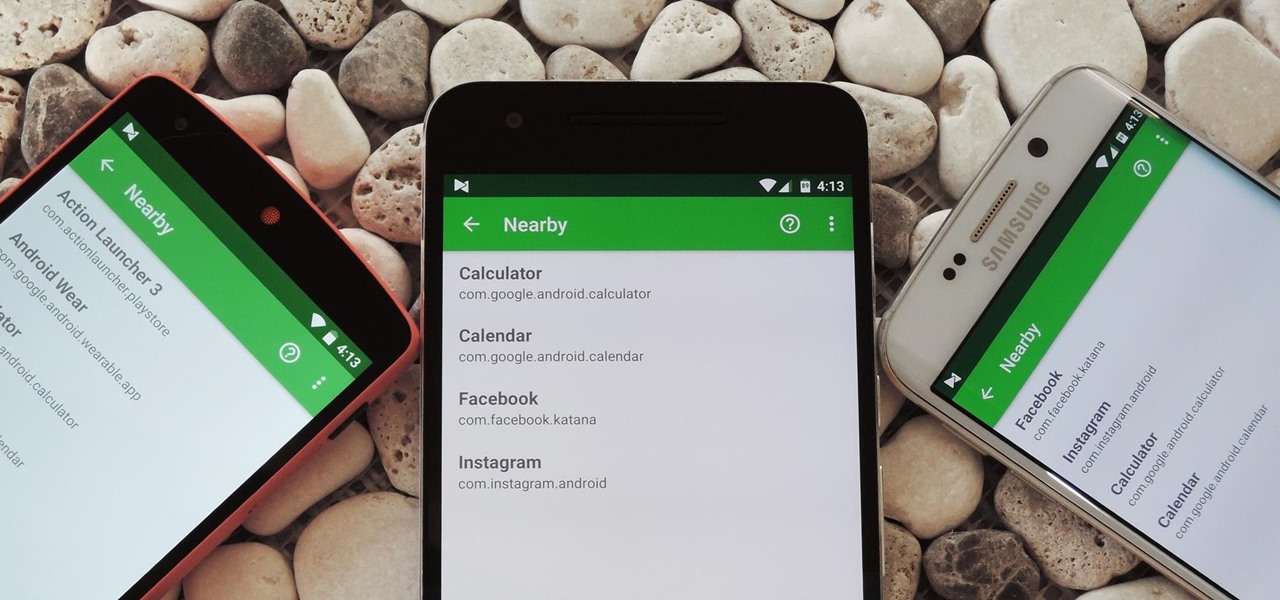
Google has an intriguing feature called Nearby that lets users share content without being on the same Wi-Fi network, or without even exchanging contact info first. Instead, the function uses an array of standard smartphone features, as well as subsonic sound, to identify other devices that are in the room, then makes a secure connection to transfer any data.

Greetings comrades! Great leader has ordered that we gain intel on a website owned by the opposition. For all general purposes we will be scanning nmap.org because they really don't care if Big Brother decides to perform a whois on their IP. We will be using Dmitry for the scanning.

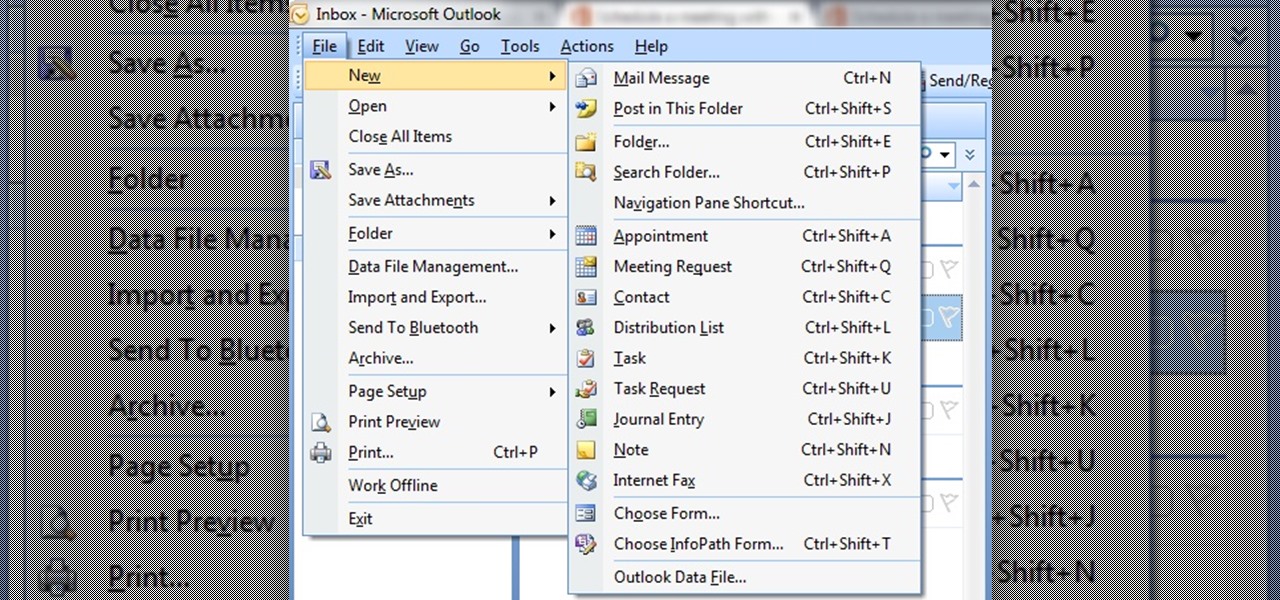
In this tutorial First, we will discuss what a meeting is, How can we schedule it in Outlook. A meeting can be defined as a mass of two or more people have a common motive. All the people present in a meeting can share their ideas and exchange information, to carry out the actions to achieve their goal. This tutorial helps those people who are looking for the steps to Schedule a Meeting in MS Outlook.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

Ever been in an argument, only to have the other person cop out by saying "I never said that," when you know full well they did? Or how about one of those times when you're sitting in the lecture hall, half dozing off to your professor's monotone ramblings, when your ears perk up because they somehow know you missed something important that was just said?

In my household, we are frugal and somewhat picky eaters, so we have to be a little creative with the things we buy. We like to purchase items that can be used in multiple dishes to reduce cost—and because it's just more practical. Pancake mix is a favorite because it can be used in various dishes where any type of breading may be involved. To help inspire you, here are some of my favorite ways to use pancake batter at home.

The first time a friend or family member asks if they can borrow your phone or tablet, you probably just hand it over without a second thought. But the second, third, and fourth times? Now it's starting to become a habit, and something probably needs to be done about it.

Smartphones have become such a big part of our lives these days that they're now closely associated with our personal identities. No longer is it Ford versus Chevy, rock versus rap, or PC versus Mac—now, you're either an Android person or an iOS person.

My daughter moved into her first apartment last year, a huge rite of passage in any young person's life. With a mother and two grandmothers who are good cooks (to say the least, in the case of the latter), it's not surprising that she turned to us for some advice about how to improve her own skills in the kitchen. Without question, the single best piece of advice we have given her is to employ mise en place each and every time she prepares a meal.

Before you sell or give away an old iPhone, Find My iPhone, which works in conjunction with Activation Lock (Apple's anti-theft system) needs to be deactivated from your iCloud account. This also applies if you've lost your passcode and are locked out of the device, if you're restoring to a previous iTunes backup, or just want to remove it from your list of iCloud devices.

Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post.

Pop-Tarts are a pretty iconic breakfast food. And while I'm more of a bacon, eggs, and toast person myself... sometimes a sweet, gooey, artificially-flavored treat is just what you need in the morning. Yet, despite the fact that I do enjoy Pop-Tarts, I've always found them a little bit bland. Therefore I decided to make them better—by cooking with them.

In the tech world, it's all too common to slap a fake label and packaging on a lower quality product, especially SD cards. If you've ever bought an SD card on the cheap from a slightly-less-than-reputable source (or even a reputable source, in some cases), how do you know if it's the real deal?

Want the next level security? Well then take a read here because this is some next level stuff. Heard of It?

With a slab-style touchscreen device, butt dialing is always going to be a problem. While you're moving about, your phone can unlock itself and give your most recent contact a ring, leading to an awkward one-sided conversation where the other person gets to eavesdrop on everything you're doing or saying at that moment.

Any other person can make plain pancakes... but only the most awesome of cooks can make stuffed pancakes. Luckily, this isn't a tough technique—in fact, it's so easy that you'll find yourself getting bored of the run-of-the-mill pancakes and dreaming of all the things you can stuff pancakes with, instead.

With new messaging services being pushed out constantly, it can be a pain trying to keep track of them all on your Android device. We had previously shown how to stay on top of them all with a unified "inbox" app, but that still requires you to have each individual app installed. While looking for a true one-stop messenger, I came across Disa.

Frosting, for many, is the best part of the cake. There's not much to dislike about it, after all—there's a type of frosting for every person. Whipped frostings for those who like it light, dense buttercream for indulgent sugar fans, cream cheese frosting for the tangy crowd... and so on. But I'll bet you've never made or tried frosting made with Jell-O packages before! Infusing your frosting with the sweetness and bright color of Jell-O changes both its taste and appearance, and using Jell-O...

Since the release of Windows 8, Microsoft has been heavily encouraging users to use Windows with a Microsoft account. According to Microsoft, the main benefit of using a Microsoft account is the ability to sign in and sync your information across various Microsoft devices and services. Furthermore, you have access to a singular cloud storage solution which can contain documents, pictures, settings, and more on whatever system you're using with the Microsoft account.

In this tutorial I am going to look at what services are running on our Metasploitable machine and setup firewalls. This is more basic scanning of our machine to get an idea of how to get in. Obviously in a real engagement you would want to do research on Google and whatnot to find out as much as you can about your target but this series isn't about all of that.

When you finally turn the privileged age of 21 in the U.S. (or 18 in most other countries), the first thing you'll probably do is sprint to the nearest pub, order a drink, and revel in your new freedom. Congratulations, you've survived two decades on Earth, you've earned that drink.

There are a few key ingredients that you always need on hand when baking cookies and other desserts, but when you run out, you run out. You either have to stop what you're doing and go to the grocery store, find a good substitute, or scrap the project entirely. Chances are, you'll never accept defeat, and why go to the store if there's a good substitute on hand?

Welcome back, my rookie hackers!

Hello fellow grey hat hackers, as hackers it becomes necessary for us to be able to send emails anonymously. Whether for whistle blowing or pranks or social engineering or whatever, it just is necessary for us to do that.

It's a rare person who enjoys swallowing pills—and equally rare to find those who can toss a pill back easily and effortlessly without gulps of water and coughs. The transition from liquid medicine to pills, tablets, and capsules can be a rough one, and some of us still struggle well into our adult lives. Yet the reason your pills are getting caught in your throat may not be the medication's fault—it's all in how you swallow.

You can make a pretty strong case for pancakes being the ultimate breakfast food. They taste like a treat for a special occasion, yet they're not bad for you (presuming you don't share my whipped cream and maple syrup habits). They can be customized and accessorized, and they cook up in just a few minutes.

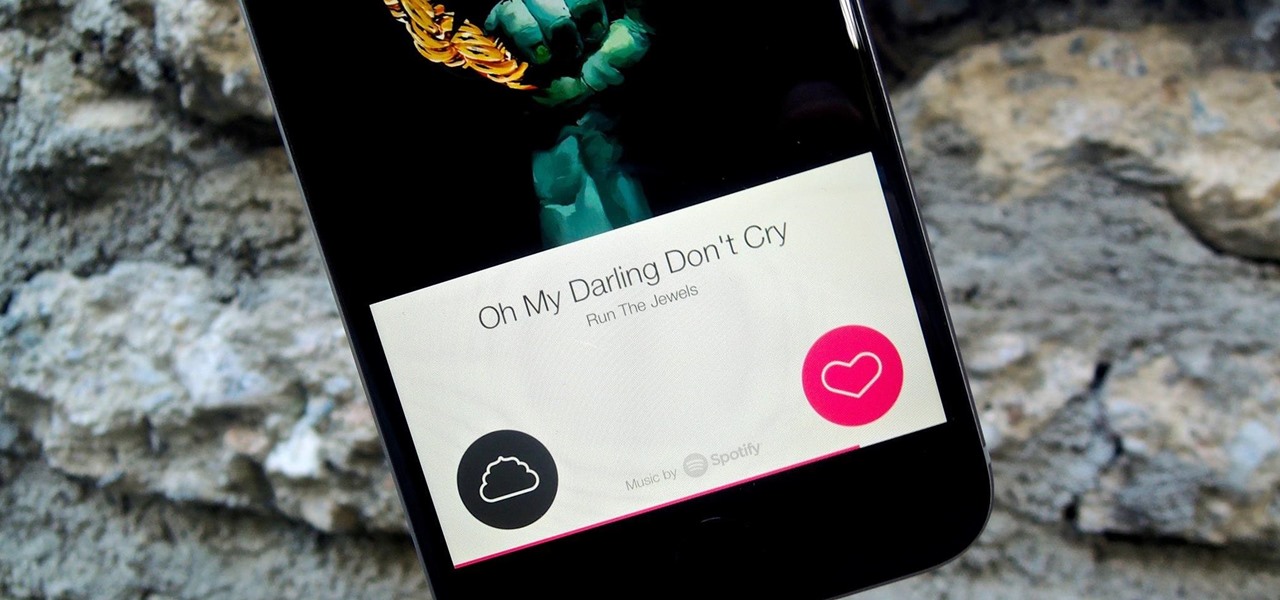
Everyone's a music aficionado these days. Whether you're having a party or on a road trip with friends, someone is always complaining about the music. There's no possible way to satisfy everyone, so instead of having your music drowned out by persistent nagging, turn Spotify into a democracy, allowing the consensus to pick what plays.

Smartphone users often wish for a privacy, where no one is able to poke his/her nose in their personal stuff. Unfortunately, none of the smartphones have been able to guard their privacy in this fashion. Smartphones usually come up with none or almost negligible built-in security to serve your purpose.

At any moment, you can open up Meerkat and start live-streaming a video from your smartphone, available for anyone to watch. Thanks to its popularity at SXSW and the backing of several big Hollywood players, the app just announced that it's receiving $14 million in funding.