Watch the full gameplay for Castlevania: Lords of Shadow on the Xbox 360. Lords of Shadows is yet another video game in the popular Castlevania franchise, which has been around since the days of the NES. In this lengthy walkthrough, you'll see all the vampire killing action, set in the Middle Ages, with protagonist Gabriel Belmont. This is a handy video guide if you ever get stumped on a level.

Self disclosure forms friendships with active listening and sharing, telling others about yourself, your thoughts, fears, and goals. Learn how to improve self disclosure and trust in this free communication video series.

If you want to invoke that fear this Halloween, watch these videos and learn how to dress in a vampire costume.

In this video series, watch as trash talker extraordinaire Ryan Tapp teaches how to talk trash. Learn the objective of trash talk, how to verbally and physically smack talk, how to use technology, general media, broadcasting to talk smack, how to use verbal and physical imitation to humiliate your opponent, how to incite others to trash talk, how to use sports and gaming terminology to talk trash, and how to insult mothers and significant others as a part of trash talk. Your friends will prai...

Fear not, proud homeowner! In this do-it-yourself home improvement video series, learn how to repair and maintain your wooden fence, with tips on identifying problem areas and using safety equipment. Get step-by-step instructions for repairing loose gate hinges, replacing rotten wood and removing chipped paint.

Two of the three entities behind Pokemon GO, the reigning champion in mobile augmented reality gaming, are joining forces again to see if lightning can strike more than once.

While most established media brands are satisfied with copying Pokémon GO to jump into augmented reality gaming, at least one property is taking a slightly different approach.

Your iPhone's almost out of battery power, there's no wired or wireless charger in sight, and you left your portable power bank at home. You don't want your battery to die, but you still need to use your iPhone. This is when Low Power Mode comes in handy, but you could be wasting valuable time and power if you're activating it the wrong way.

Android has not had the best reputation for privacy and security, though Google has made strides in those departments in recent years.

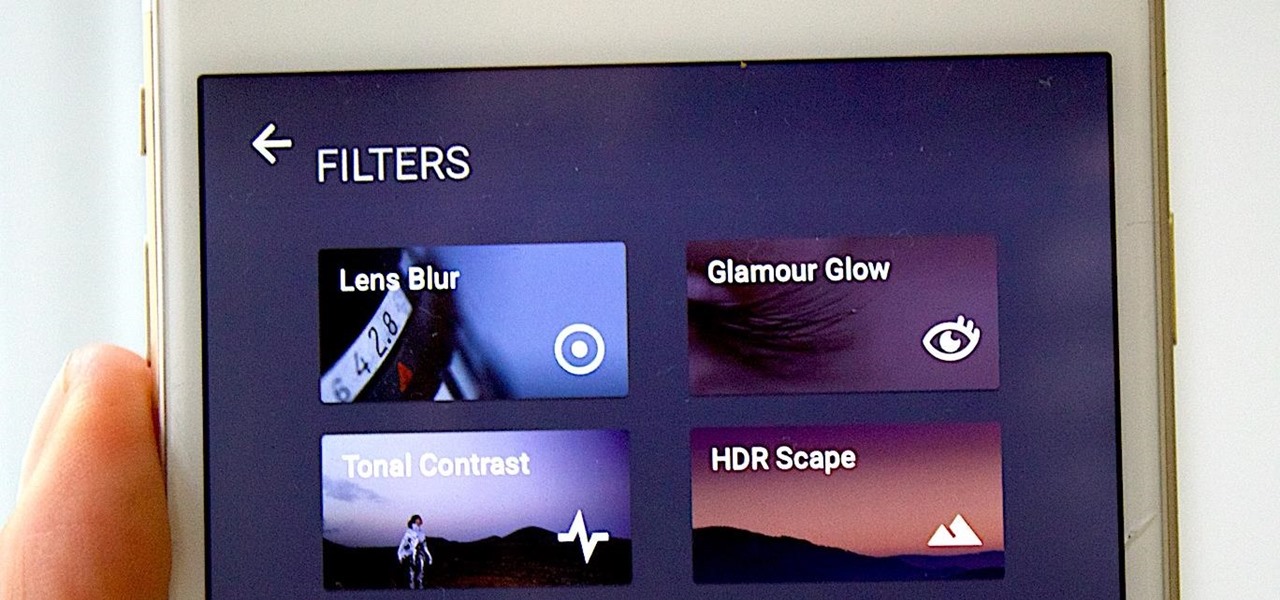
Whether you're trying to become an influencer or just want to share better photos and videos, the best camera to start with is your smartphone. It is likely the only camera you always have on you and it's probably capable of excellent pictures and video capture. But with a little help, it could definitely be better.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

It's that time again. Snow days, Thanksgiving dinner, holiday presents ... and great Black Friday deals. Starting the Friday after Thanksgiving (or sometimes a few days before), millions of items will go on sale, including your next Android phone.

TWRP won't be ready for the Pixel 4 and 4 XL until months after release. But since you can already root with Magisk and tinker with the OS, you might find yourself in a situation where your phone won't boot, yet you don't have a custom recovery installed to fix it. Luckily, there's still a way around this.

This time last year, Snap CEO Evan Spiegel and his company were faced with an erosion of its user base that cratered its stock price. This year, on the strength of Snapchat's AR camera effects, the company has reversed course. And that's why Spiegel tops the NR30, our annual list of the leaders in the AR industry.

The streaming content vision from Magic Leap recently underwent a quiet but major update, courtesy of AT&T.

TWRP is a name many are familiar with since it allows your Android device to install any custom file of your choosing. You can create a NANDroid backup to keep your data safe or even use Magisk to achieve full root access. In fact, TWRP is often seen as the gateway to modding your system for creating a unique user experience.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

In this era of smartphones, we all know very well how easily we can get addicted to our devices. Spending hours each day doing the endless scroll through Facebook and other social media sites just because we feel like we'll miss something if we don't. Both Google and Apple are aware of this and are trying to help control smartphone addition in their own way for Android and iOS.

When it comes to rooting and modding any Android device, ADB and Fastboot commands will quickly become your two new best friends once you realize the power they have. From unlocking your bootloader to flashing any file you could ever want — if you're serious about the modding and customization game, you'll want to become acquainted with these commands as soon as possible.

Update: The LG G8 ThinQ has been announced. You can read all of the official specs at our full article on the new phone.

If you salivate at the idea of waking up to the Jarvis-powered smart window from the opening minutes of Marvel's Iron Man, then connected home appliance maker CareOS is here to make your playboy billionaire philanthropist dreams come true.

When flashing files through TWRP, ADB, or Fastboot, there's a slight chance for things to go wrong. Whether it's user error related or something else entirely, it's always good to have a backup plan. In most cases, you'll be dealing with a semi-brick or soft-brick, which can usually be solved by wiping the data of the device using TWRP. However, it can be more severe than that in some cases.

The main draw for Google's Pixel series is the software. It rocks a clean version of stock Android instead of a heavy OEM skin like TouchWiz, it gets frequent prompt OS updates, the camera software is downright amazing, and it has perhaps the most fluid UI of any phone. But an understated advantage of the software is how dead-simple it is to modify with root-level tweaks.

The march towards mainstream adoption of eSIM technology got a massive boost with the arrival of the iPhone XS, XS Max, and XR. We're now one step closer to ditching physical SIM cards altogether. If you're on the fence about this new technology, you may be surprised by the benefits it brings to the table.

With the announcement of ARKit 2.0 at WWDC 2018, Apple is bringing some powerful new capabilities to mobile augmented reality apps this fall.

UPDATE April 4, 2019: We had high hopes for the ZTE Axon 9, but it won't be releasing in the United States. If you're in another area of the world, you can look into the ZTE Axon 9 Pro, but we cannot recommend this device to American readers due to carrier incompatibility. Below, we've saved the early rumored information on the Axon 9 for posterity.

Safari for iPhone is generally a good mobile browsing experience — except when it isn't. Popup ads are a real issue, and they cause both great annoyance as well as concern over iOS security. How do you stop these nuisances and return to a web without fear of popups?

Last week, augmented reality startup Proxy42 released Father.IO, a multiplayer game that turns any indoor or outdoor space into a laser tag arena.

Karen Gillan must have had an absolute blast chewing the scenery as Nebula in Guardians of the Galaxy Vol. 2, seeing as how Nebula is a ball of pure, seething fury pretty much 24/7. Combine that larger-than-life personality with her iconic blue and silver cyborg look, and you have a guaranteed hit for cosplay or Halloween.

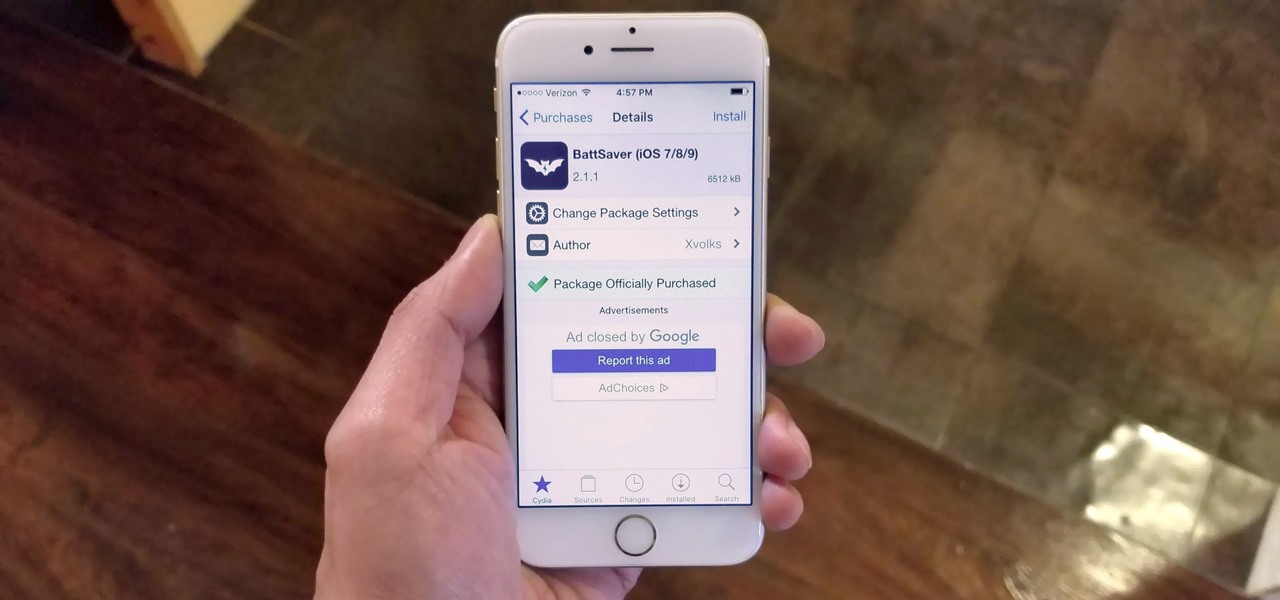
While widely known for its massive collection of free apps and tweaks that let you fully personalize your jailbroken iPhone, Cydia also comes laden with packages that can be purchased to take customization to a whole 'nother level. Similar in function to the iOS App Store, buying an app in Cydia is simple and relatively safe.

Regarding foodborne pathogens, eating fish is not as hazardous as it was a few years ago — but if fins are on the menu, it's good to have a heads-up about what's good and what's bad these days.

There are many different ways and many different apps that allow you to censor a racy photo and then share it to Instagram or Facebook. If you're in a time crunch and don't have the time or the patience to deal with something like Photoshop, then Snapseed is a great and easy app that will blur out your raunchy images in a quickie.

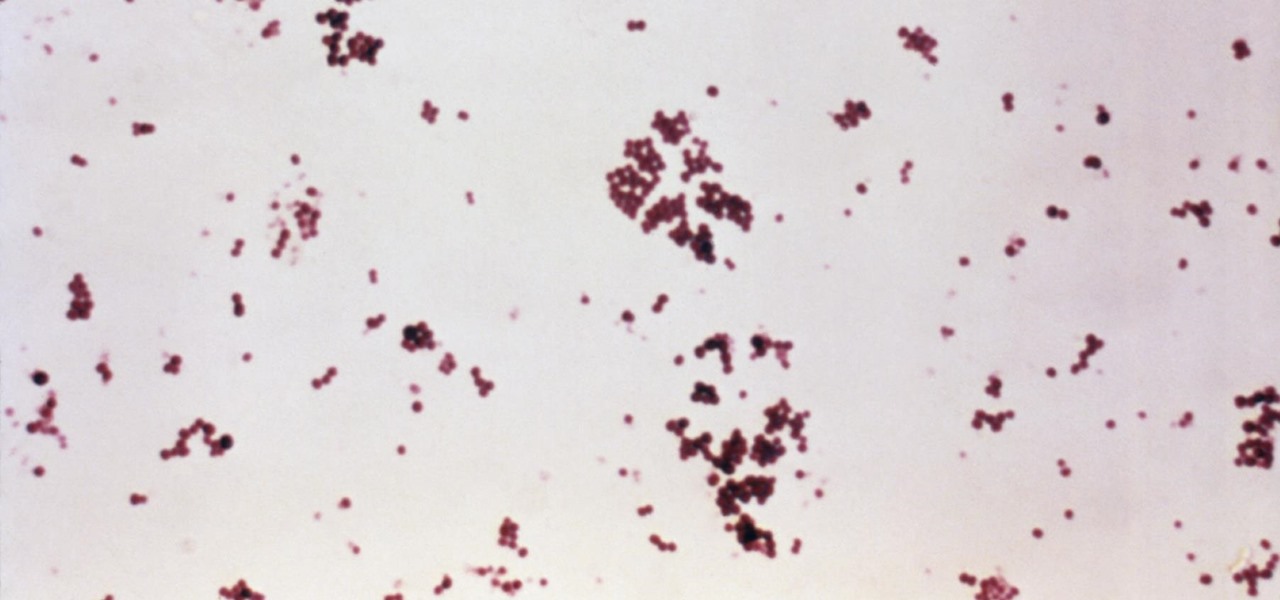
Infections with group A streptococcus, like Streptococcus pyogenes, claim over a half million lives a year globally, with about 163,000 due to invasive strep infections, like flesh-eating necrotizing fasciitis and streptococcal toxic shock syndrome.

New research explores how the bacteria on the penis can leave men more susceptible to infection with HIV.

During the millions of years they've been on earth horseshoe crabs have developed a trick that can save our lives even now — and may be especially useful in the fight against healthcare-associated infections.

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.

By connecting the dots between theory and real-life effect, two new studies offer more proof that neonicotinoid insecticides are causing extensive damage to honeybee colonies.

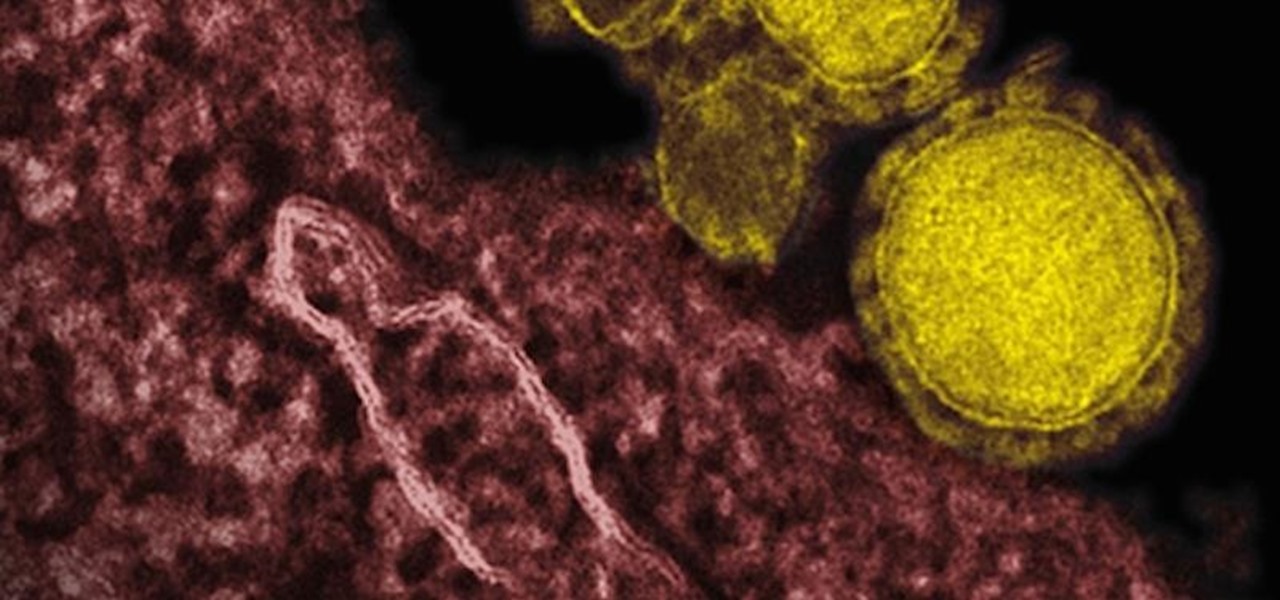
Coronaviruses are common viruses, and most of us catch one at some point — they cause about 30% of all common colds. A new accidental discovery could help fight these viruses, even the deadlier, emerging ones.

Tell the truth. The bat picture creeps you out. You are not alone. But in reality, bats truly are some of our best friends. They gobble thousands of disease-spreading bugs a night. But they also carry viruses that can be deadly to humans. So, bats — friend or foe?