Interested in completely customizing the look and feel of your Windows XP desktop? Could you go a lifetime without seeing the standard Windows cursor? If so, you're in luck: This video tutorial offers pointers for finding, downloading and using custom cursor sets in Windows XP. To get started installing your own custom cursors, take a look.

World Fusion Drumming combines the energy and feel of rock, Latin, and world music with the technique and improvisational skills of jazz. In this installment from his video tutorial series on the rudiments of world fusion drumming, Berklee College of Music professor Skip Hadden will walk you through several Brazilian-style drum fills that will help you in approximating the sound of Brazilian percussion session.

Having a hard time sliding your coffee maker out from the corner every morning? Then watch this how to video and see how easy it is to make your coffee maker come out in the mornings. All you need are a few felt pads to help it glide easily across the counters.

Babies have no way of communication other than crying. = Touch is one of a baby's most highly developed senses at birth. Holding, caressing and cuddling your infant is crucial to helping her feel safe and secure. There are a number of tips demonstrated in this instructional video to help calm a crying baby. Watch this video child care tutorial and learn how to comfort a baby.

You've tried the beginning level yoga poses, now to an intermediate level pose. In this yoga how to video we show you how to do the lotus yoga pose. The lotus pose is also known as padmasana. To try this at home you have to make sure that your hip muscles are open enough. If you feel any resistance while in the lotus position pull back.

Feel beautiful from the inside out with targeted exercises, like these exercises for your feet. This how-to video has a few simple exercises that will strengthen your toes and relieve some foot discomfort. Keep your feet in good shape so you can wear those high heeled shoes all night.

This how to video explains the blues scale, as well as how to express emotion and feeling into your playing. Playing with emotion is very important to master in order to produce compelling music. Watch this tutorial and you will be playing piano passionately in no time.

Make your own motorcycle camera Mount for less than five bucks! You won't believe how easy it is. This video tutorial will show you how to make one hell of a motorcycle mount. I wouldn't put a Canon XL2 on this or anything, but it's sure good enough for you palm-sized digital cameras, for a cheap look and feel to your new motorcycle gang film.

Learn how you can achieve this astrological sign inspired Scorpio look with this how to video. This makeup tutorial uses the following products:

Learn how to improve your position on the golf course with the help of this swing plane drill. You can really feel what that club is doing!

Yossarian the Grammarian dispels the fog surrounding copulative (linking) verbs and explains why you probably never mean to say, "I feel badly." Great English grammar lesson for ESL students.

A Grand Theft Auto 4 walkthrough for the "Hostile Negotiation" mission. Nico goes to save his cousin Roman. Many henchmen feel like getting shot along the way.

The swiss army triplet is a unique one-way rudiment that can be played in both right and left hand leads. Unlike most of the other rudiments, this rudiment isn't designed to alternate. As its name suggests this rudiment has a 'triplet' feel.

The flam accent is a powerful drum rudiment that uses the basic flam within a triplet feel. The pattern is great for creative drum fills and solo patterns within a wide variety of musical genres.

Watch this video for a demonstration of how to give a shiatsu release down the back. Feels great and helps the tension to melt away- nice to start a massage with.

Safety means something different to everyone, but everyone wants to feel safe. For many, the best way to feel safe is to have something external that offers that sense of security, whether it's an alarm system, a friend on standby, or just something that helps you feel in control.

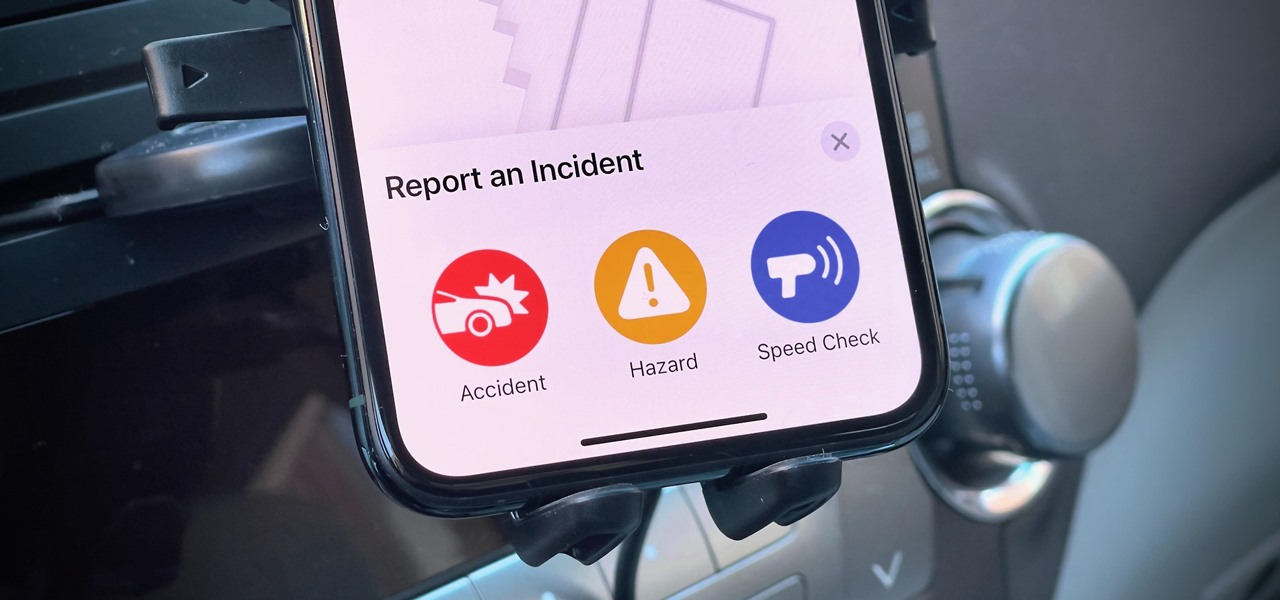
Driving is anything but problem-free. Speed traps, accidents, and other hazards can appear at any time, requiring motorists to be attentive, quick, and prepared for anything. If you see something dangerous on your route that you want to warn others about, there's an easy way to do so in Apple Maps.

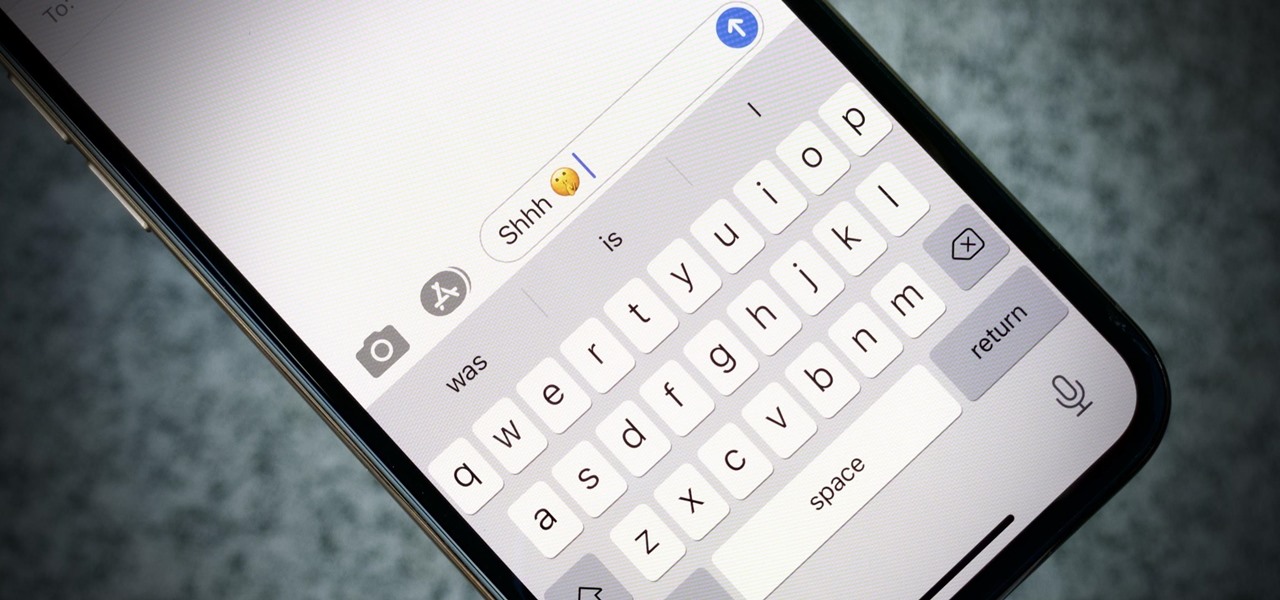
If you're in an active Messages chat, writing a large email, or have a lot of notes to jot down, you might be acutely aware of just how loud your iPhone's keyboard can sound — especially with AirPods or other headphones on. "Click, click, click, click, click, click." If the fake keyboard sounds are driving your crazy as you type, there's something you can do about it.

Are you thinking about upgrading your iPhone this year? Apple sure wants you to. Of course, that's no different than any other year, but Apple really wants you to upgrade this year. How do we know this? The rumors point to not three, not four, but five brand new iPhones in 2020, with two very different release schedules. All this begs the question what the hell is Apple thinking?

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

One of my favorite perks of this job is the opportunity to try out all the big flagship phones each year. Whether it's rating their suitability for a particular use-case or just entering their specs into our comparison tool, we have to get our hands on all major phones released in the US. We pride ourselves on being fair in our reviews and roundups, but that doesn't mean we don't have preferences.

Spam calls are one of the most annoying things to happen in the world of smartphones for more than one reason. Not only are they bothersome, but they can also be dangerous to people who don't know any better. Google has come up with a crafty solution known as "Call Screen" to let the Google Assistant handle the call for you while you listen in on the caller like a stealth ninja.

If you've ever needed to prove you have remote access to a device, or simply want a way to convince someone their computer is haunted, SSH can be used to make a device begin to show signs of being possessed.

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

QR codes are everywhere, from product packaging to airline boarding passes, making the scanners that read them a juicy target for hackers. Thanks to flaws in many of these proprietary scanning devices, it's possible to exploit common vulnerabilities using exploits packed into custom QR codes.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

OnePlus always seems to offer affordable yet powerful tools for videographers of all kinds. The camera hardware itself is crucial, but what's hardware without good software to highlight its real potential? It doesn't matter which version of the smartphone you have, they're all powered by the very same OnePlus camera app.

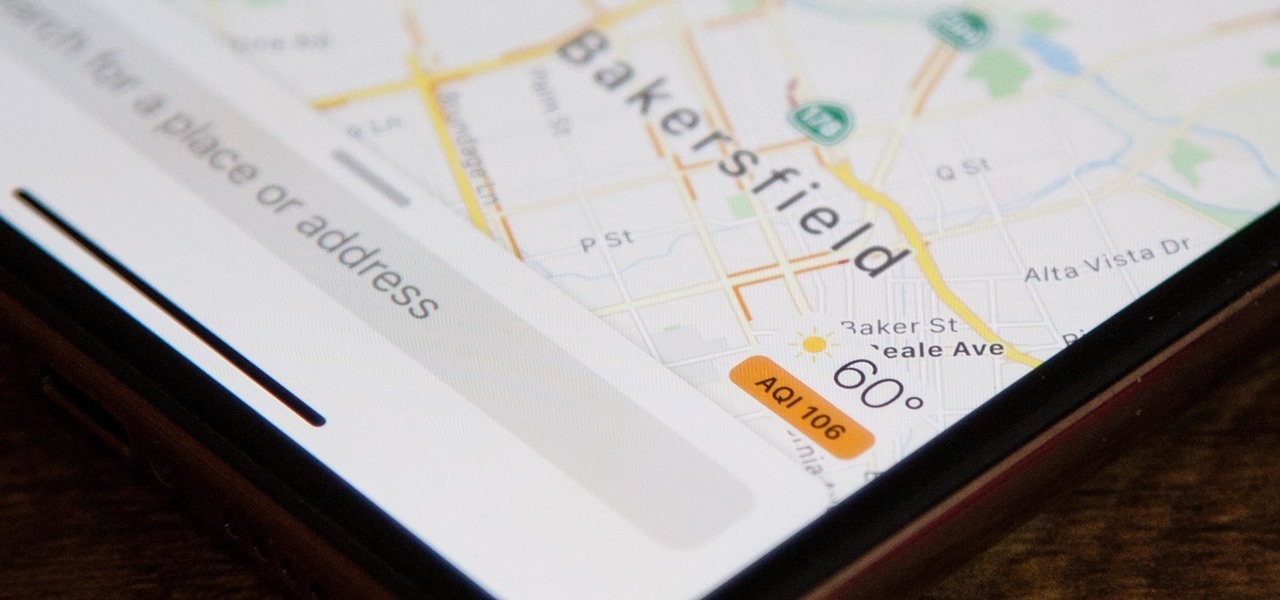
While the United States, in general, doesn't have the worst overall pollution, the air quality can drastically change from one day to the next. If you're particularly sensitive to pollutants in the air, there are apps that show how clean or polluted the air is in your area, as well as in cities you plan on traveling to, but Apple's making those apps less relevant with a new feature in Apple Maps.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

The OnePlus 6T is easily one of 2018's best value phones for many reasons, especially when it comes to rooting and modding. But like many new phones, it's plagued with the single bottom-firing speaker that left us wanting more in the sound department. The speaker is decent on its own, but it appears to have some hidden potential at the same time.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.

Have you been noticing SpaceX and its launches lately? Ever imagined how it would feel to launch your own rocket into the sky? Well, imagine no longer!

We know Android 9.0 will have the formal designation of Pie, following Google's age-old tradition of naming their OS after items you'd normally find on a dessert menu. And thanks to a slew of new features that centers around your overall security, P could also stand for Privacy.

The Galaxy S9 is now in the hands of millons of excited users. Getting a new phone is always fun, but it's important to think about protecting your device. Perhaps the most popular cases for the Galaxy S9 are the official OEM options from Samsung. There are a plethora of cases, whatever your preference and needs may be. Let's take a look at each case individually, along with the pros and cons.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

When traversing the web, you'll regularly come across websites that require you to create an account. With the majority of these accounts, protection is limited to a simple password. Despite this, many people are still using weak passwords such "123456." For these reasons, you really need a password manager, and our research has shown that LastPass is still your best bet.

Code execution in Microsoft Word is easier than ever, thanks to recent research done by Etienne Stalmans and Saif El-Sherei. Executing code in MS Word can be complicated, in some cases requiring the use of Macros or memory corruption. Fortunately, Microsoft has a built in a feature that we can abuse to have the same effect. The best part, it does so without raising any User Account Control security warnings. Let's look at how it's done.

As the fish farming industry struggles to become more environmentally friendly, it just gained another problem. Fish food loaded with antibiotic-resistant genes.