In this instructional video series, learn how to play linebacker. Understand how the game works, with an introduction to the basic rules and objectives, as well as a rundown of the offensive and defensive positions on the field. Lessons also include skills and techniques for beginner offensive and defensive players: how to carry the ball, throw a pass, block effectively, punt, and make a solid hand off.

Whether you want to be a referee yourself or just want to understand what the heck all those hand gestures made on the field mean this is the video series for you. Throughout this series you will learn the correct hand gestures for fouls such as tripping, holding, intentional grounding and delay of game.

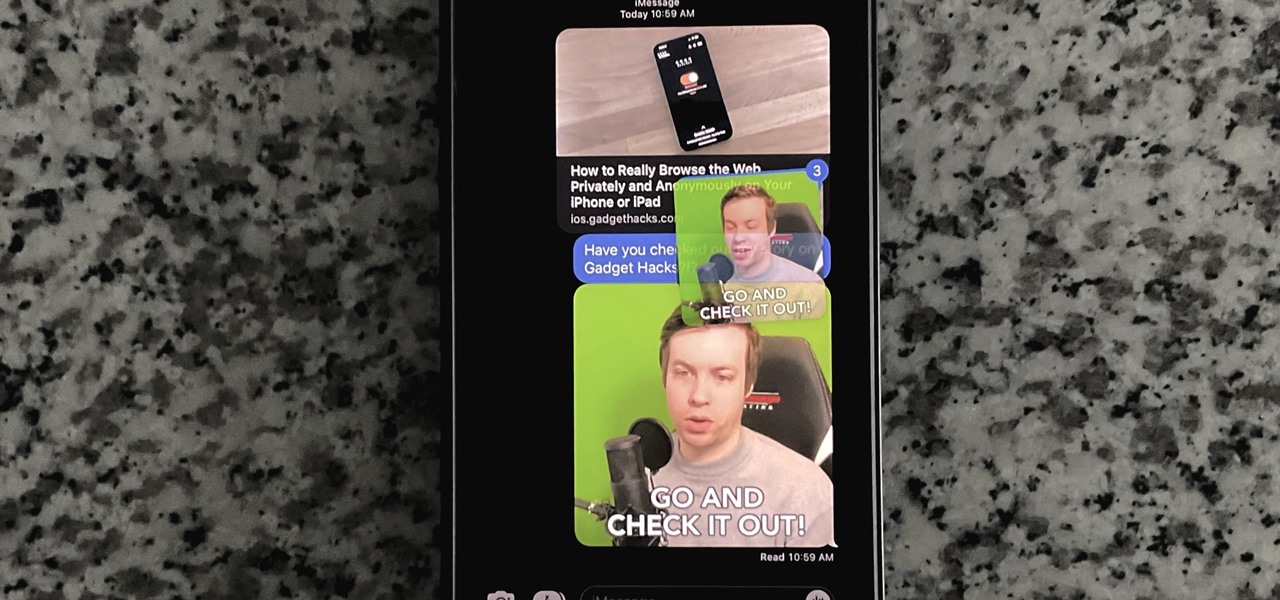
You could already schedule an email to send on a specific day and time in Apple's Mail app, but that functionality is now also available in the Messages app. What's even better is that scheduled messages sync across your iPhone, iPad, and Mac, something you don't get in the Mail app.

Seventeen years ago, Apple released iPhone, the first mainstream consumer phone with a touchscreen as its main typing input method. Apple has been perfecting its onscreen keyboard for almost two decades, and it's built with some fantastic features that make typing faster and easier. But it's easy to overlook some of these features, so here are some tips and tricks you need to be using if you aren't already.
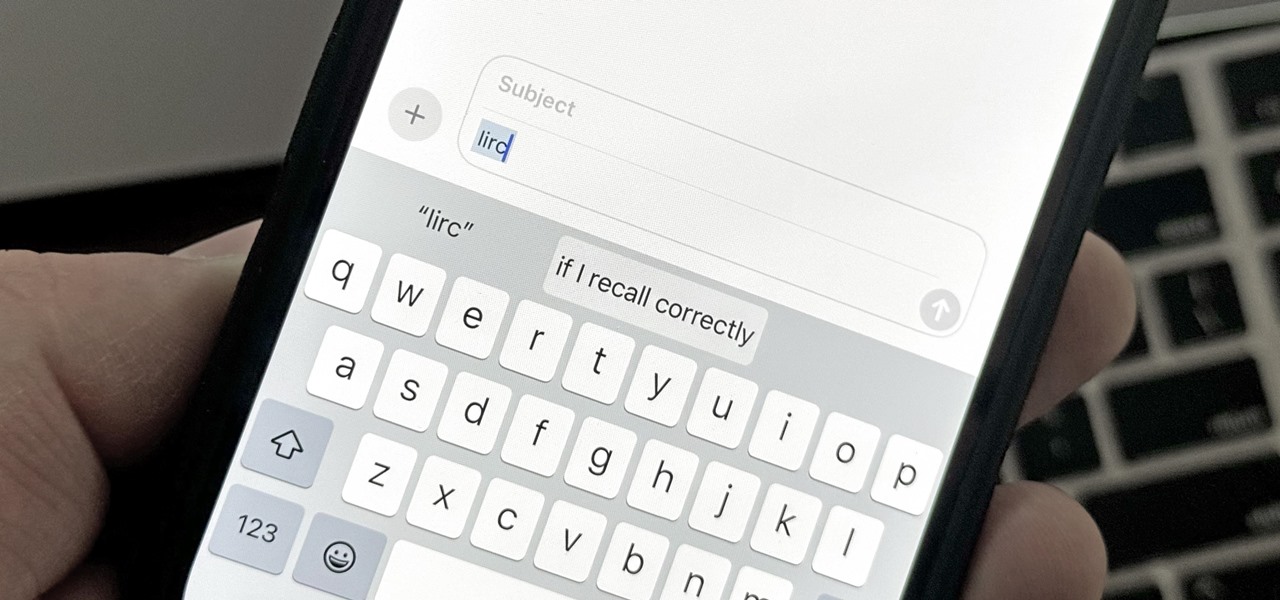
There are plenty of tools that'll help you type faster and more efficiently on your iPhone or iPad, such as Slide to Type, Dictation, and even a case with a physical keyboard. But one of the best tricks will help you type frequently used words, phrases, sentences, email addresses, and more faster, and you can sync your settings with your Mac so you can type more with less effort on all your Apple devices.
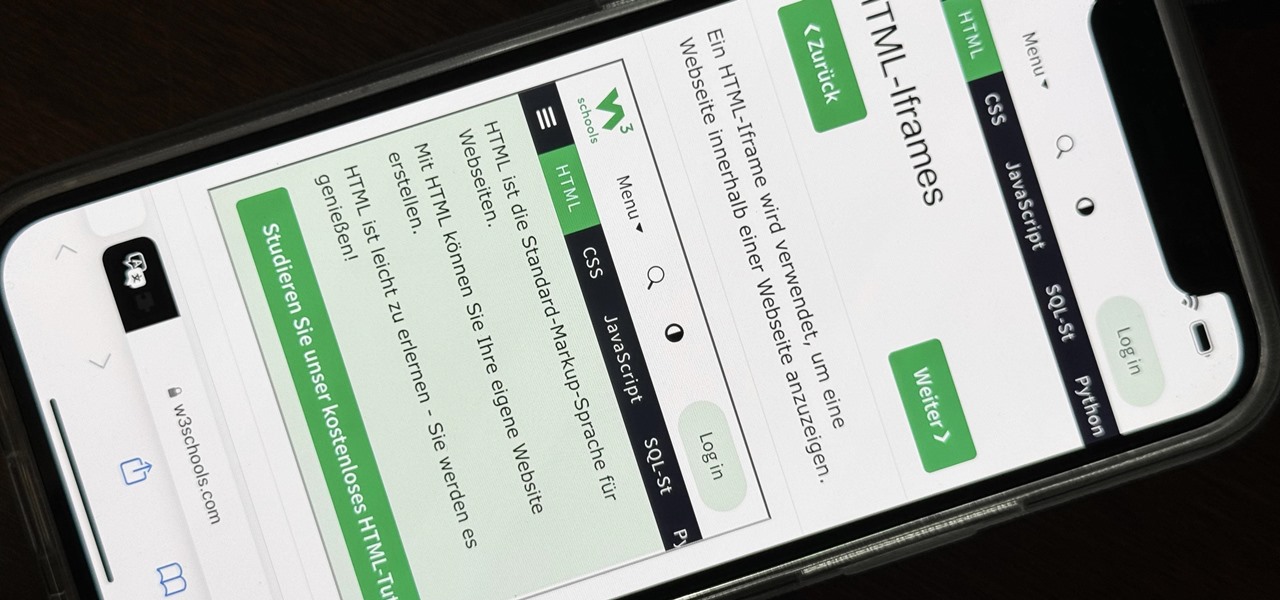
The latest 17.4 update for Safari includes a prompt for EU users to choose a different default web browser available in their region. It also gives us new ways to customize the Favorites Bar on an iPad. And Apple Cash virtual numbers are now supported as an AutoFill suggestion. But there are also some hidden changes in Safari 17.4 for iOS and iPadOS that you might not ever notice unless you keep reading.

The Messages app for iOS and iPadOS has a lot of hidden features, but one in particular can save you time and energy whenever you need to forward or copy and paste messages from within an SMS, MMS, or iMessage conversation.

Enter a password into a password field, and it's a sure bet that black dots or asterisks will obscure the characters. Nearly every website you visit in Safari on your iPhone will do it, but sometimes it helps to see what you're typing or what was auto-filled with iCloud Keychain, LastPass, or a different password manager.

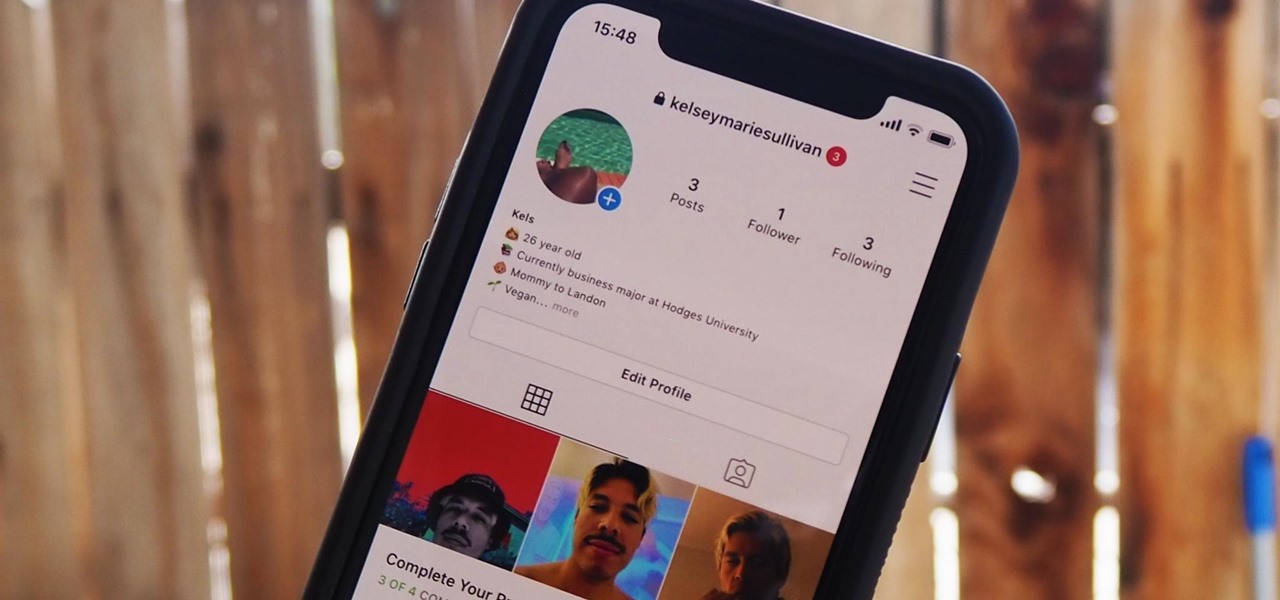
Everything you post on social media lives there forever — even if you delete it. Just ask anyone that's ever posted something stupid. Instagram does not provide built-in tools to save or download images and videos from other users, but there are workarounds. Third-party tools make saving other people's photos and videos easy, and there are always screenshots.

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

Twitter replies have traditionally acted like public spaces. Once a tweet is out there, pretty much anyone can reply to it. In some cases, that makes for good discussion. In others, it can lead to disaster, abuse, and harassment. Twitter's looking to change that by giving you more control over who can reply to tweets.

Starting Sept. 13, you can preorder the iPhone 11, 11 Pro, or 11 Pro Max from Apple, wireless carriers, and various e-commerce websites. However, unlike with Android smartphones, there is only one set of iOS phones that come out each year, so they're pretty hot items. That means being the first to get your hands on one could be a challenge, but we're here to help you out.

Apple CEO Tim Cook has said that augmented reality (or, AR for short) will "change everything." But what, exactly, is augmented reality?

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purchasing will work for Wi-Fi hacking.

With all the controversy around the Pixel 3 XL, the regular-sized Pixel 3 might be the phone of choice for most users. Thanks to the huge boost in screen size, the little brother is now an easier pickup for those who like a bigger screen. And once more, the internals are the same, giving you the same experience as the 3 XL without the display notch.

The "controversial" Pixel. No phone in the history of Google's Pixel lineup deserves this title more than the Pixel 3 XL. For some (including myself), the design is a welcome change that embodies the modern design of 2018 flagship phones. For others, it has an ugly huge display notch that destroys symmetry.

When I review apps, I'll oftentimes end up downloading at least one or two "bad" apps that either lied about their functionality or were riddled with ads. These apps, while not as harmful as malware, can still be a major headache. This got me thinking about the other bad apps on the Play Store and how to avoid them.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

In a surprising twist of expectation management, Magic Leap managed to not only ship but deliver the Magic Leap One I ordered on Wednesday by 4 p.m. PT on the same day.

Ever since 3D Touch's introduction in iOS 9 for the iPhone 6S and 6S Plus, a little-known trick for moving the cursor around and selecting text was built into Apple's stock keyboard. On iOS 12 or later, it works for all iPhone models with or without 3D Touch or Haptic Touch baked in.

There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

Web applications are becoming more and more popular, replacing traditional desktop programs at an accelerated rate. With all these new apps out on the web comes various security implications associated with being connected to the internet where anyone can poke and prod at them. One of the simplest, yet the most prevalent types of security flaws found in modern web apps are SQL injections.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

The LG G6 was officially announced by LG at Mobile World Congress 2017 in Barcelona and released in the US on April 7, 2017. The device is almost exactly what we've been expecting from all of the rumors and leaks building up to its release. The modular design we saw in the G5 is gone, taking the removable battery with it. However, we do gain waterproofing, an improved dual-camera setup, a larger screen with smaller bezels, and Google Assistant.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

While you may not have loads of secret files hiding on your computer, there might be one or two items that need a little extra security, like a file of website logins or a folder of risqué photos.

There are quite a few flaws with Apple's mobile products, and one that drives me crazy is their reliance upon iTunes for all your music syncing needs. If you want a song on your iPhone, you pretty much have to use iTunes to get it on there. Either that or buy it directly from the iTunes app on your device.

AppleScript is quite an easy scripting language to use. In this guide, I will be showing you several commands. Near the end, I will show how these can be used to create a fake virus that actually does no harm.

Improve your football game and your value to the team by memorizing and ready to execute your football playbook. Standard memorizing tools like flash cards and practice will help get you through any size playbook.

Music theory is a field of study that focuses on the intricate workings and mechanics of music. Learn about guitar music theory and intervals from a professional musician in this free guitar video.

In this instructional video series, learn how to play cornerback. Understand how the game works, with an introduction to the basic rules and objectives, as well as a rundown of the offensive and defensive positions on the field. Lessons also include skills and techniques for beginner offensive and defensive players: how to carry the ball, throw a pass, block effectively, punt, and make a solid hand off.

In this free instructional video series, learn how to make a tackle in football. Understand how the game works, with an introduction to the basic rules and objectives, as well as a rundown of the offensive and defensive positions on the field. Lessons also include skills and techniques for beginner offensive and defensive players: how to carry the ball, throw a pass, block effectively, punt, and make a solid hand off.

In this instructional video series, learn how to play center. Understand how the game works, with an introduction to the basic rules and objectives, as well as a rundown of the offensive and defensive positions on the field. Lessons also include skills and techniques for beginner offensive and defensive players: how to carry the ball, throw a pass, block effectively, punt, and make a solid hand off.

In this instructional video series, learn how to play offensive guard. Understand how the game works, with an introduction to the basic rules and objectives, as well as a rundown of the offensive and defensive positions on the field. Lessons also include skills and techniques for beginner offensive and defensive players: how to carry the ball, throw a pass, block effectively, punt, and make a solid hand off.

Garson Fields shows us how to apply basic BMX skills. Part 1 of 15 - How to Apply basic BMX skills.

Garson Fields demonstrates the basic freestyle tricks in BMX for this series of videos. Part 1 of 14 - How to Do basic BMX freestyle tricks.