Welcome back, my tenderfoot hackers! Those of you who have been reading my posts here for awhile know how much I emphasize good reconnaissance. Novice hackers often jump into a hack/exploit without doing proper recon and either fail or get caught. Experienced and expert hackers know that 70-80 percent of a good and successful hack is dependent upon successful and accurate reconnaissance.

I've previously shown a few ways to make your iPhone a little more unique by customizing app icons on the home screen, and while those processes did not require a jailbreak, they were a pain in the ass. Thankfully, there's a better way to customize app and shortcut icons that's a lot less convoluted.

Complete silence or a non-stop Pandora playlist? People are often divided on what type of work environment they prefer. Whether you're a frequent loud music listener or you can't stand any kind of background noise, chances are you're pretty set in your ways.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

Because of Android's massive array of supported smartphones that carry vastly different display sizes and resolutions, the operating system uses a value known as DPI to determine the size of icons and visual assets that will best suit a given screen.

One of the best things about summertime is that there's lots of outdoor cooking, whether you're on a camping trip or grilling. And what better way to end your meal than with the classic dessert, s'mores?

Canvas fingerprinting is the web's trickiest privacy threat, but it's not impossible to stop. With all the media attention it's gotten lately, it's time we lay out exactly how to detect and prevent this invasive tracking technique.

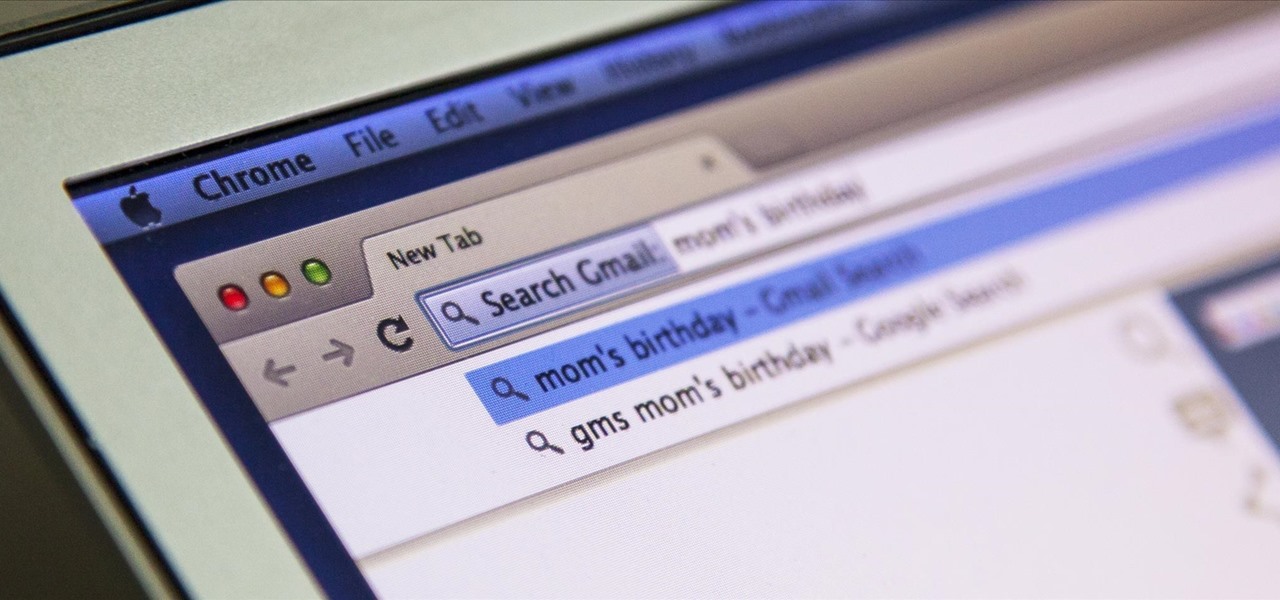
I'm all about saving time. If there's a quicker way to do something, I'm going to find it. For this reason, whenever I need to search through old emails or compose new ones in Gmail, I do it directly from Chrome's address bar, or as Google likes to call it, the omnibox—and you can, too.

I'll give Samsung credit where it's due—the stock keyboard on the Galaxy S5 is actually pretty nice. There's a dedicated number row that resides at the top (something that the Google Keyboard needs a hack to achieve), and various settings exist to make switching between languages a breeze.

When the Nexus 5 debuted, one of its coolest features was the fact that you could say "OK Google" any time you were on the home screen to launch a Google Voice Search. This feature was ultimately made available for other devices by way of the Google Now Launcher.

Update, November 12, 2014: Android 5.0 Lollipop is officially out now. If you haven't gotten the OTA yet, check out our new guide on installing the official Lollipop builds on any Nexus for download links and instructions, for Mac or Windows.

Update: June 19, 2014 Android 4.4.4 has been released, fixing a small security bug in 4.4.3. The factory images have already been made available to all current-generation Nexus devices, and I've linked them out below. This does not affect the process depicted, you can still use these same steps to bring your device up to date with this latest release.

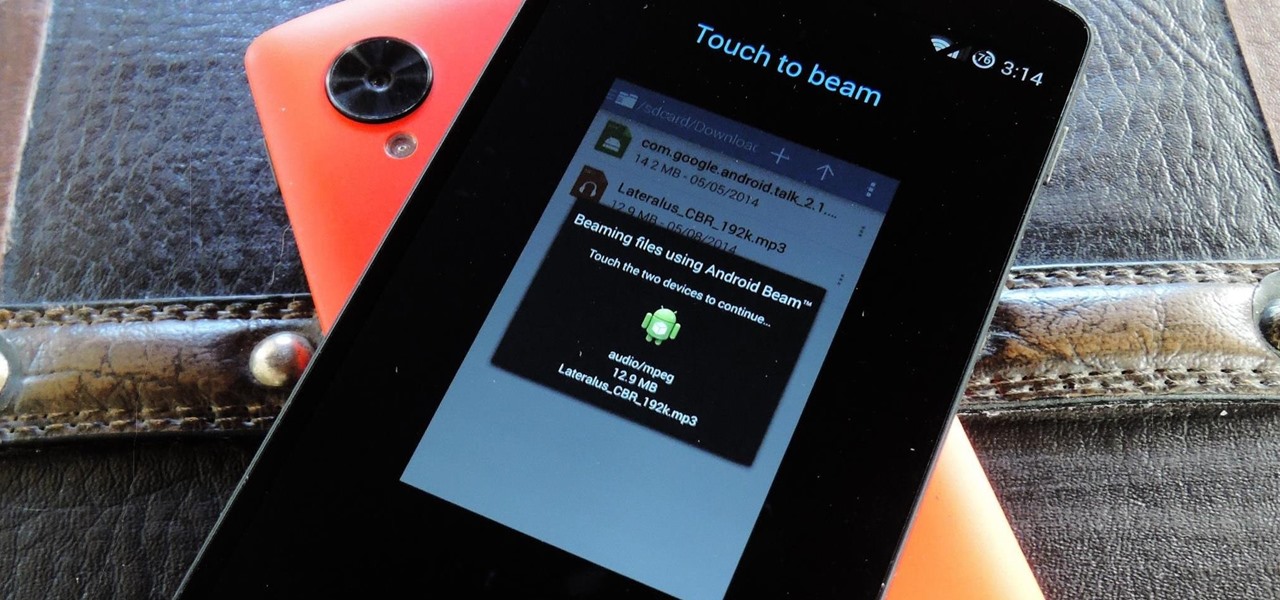
Your Nexus 5 comes with a pretty cool feature baked in called Android Beam. Using NFC, or Near Field Communication, this functionality allows you to send information to another compatible device by simply touching the two together. Most flagship devices have NFC built into them these days, so there is a broad range of devices that your Nexus 5 is capable of sharing information with wirelessly.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

LastPass is a password manager that's been around for some time, and has finally made its way over to Android for use with apps, not just websites.

After much hype and even more leaks, the HTC One M8 has finally been unveiled at the company's New York release announcement.

As softModders, the first thing we do after updating to the newest version of Android is to root, install a custom recovery, and install a superuser app. By doing this you open up your HTC One to a vast quantity of new apps and tweaks you can use to truly make your phone One of a kind.

After many beta builds, Apple has finally released iOS 7.1 to the public. It includes bug fixes for the old iOS 7.0.6, along with UI enhancements and even some new features.

The Samsung Galaxy S5 was just officially announced at Mobile World Congress. The new flagship device will be available worldwide beginning April 11, 2014, including all major U.S. and international carriers. With over 200 million Galaxy devices sold to date, the S5 doesn't stray too far from the trend, at least not aesthetically. We've still got a high-grade plastic shell with perforated back covers, and four color choices at launch. Our highlights of the release event are as follows.

There are much better things that can go in your iPhone's status bar besides an always-on indicator displaying what carrier you're shelling out money to every month. While it would be nice to get rid of the carrier name altogether at the top of the screen, an even better option is switching it out with something else to better personalize your iPhone.

Welcome back, my rookie hackers! A short while back, I began a new series on database hacking, and now it's time to continue and extend your education in that field. As you know, the database contains all of the most valuable info for the hacker, including personally identifiable information, credit card numbers, intellectual property, etc. So, it's the ultimate goal of cybercrime and the APT hacker.

Last week, I highlighted 5 of my favorite free interactive live wallpapers that you could use on your Android device. But where do you go from there? What's the next step up?

Welcome back, my hacker novitiates! Many of you have written me that you're having difficulty installing and running Metasploit on a variety of platforms. No matter if you're using Mac, Linux, or Windows, I strongly recommend you install BackTrack as your secondary OS, a virtaulization system, or on an external drive. This particular Linux distribution has many hacking and security tools integrated—including Metasploit.

Parking. Ugh. Parking is about as fun as running through a swarm of bees while being chased by a pack of wolves from The Grey.

A few days ago, Russian hacker Alexy Borodin found a way to get free in-app purchases on an iPhone or iPad. In-app purchases include things like items and power-ups for iOS games, as well as subscriptions and "premium" memberships for certain apps.

This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria:

Valentine's Day is almost here, and if you're like me, you're scurrying to do something special for your mate. The standard chocolates and flowers just isn't cutting it anymore, and you can only make so many homemade cards before it becomes banal and meaningless. So, what can you do that shows you put some work into it, while not breaking the bank?

Building a DIY Alarm System: The Concept So, you want to protect your property, or maybe a room, car, or even your backyard. The concept of an alarm system is to notify the "alarm administrator" that there is an intruder entering the previously designated boundaries. The triggers for this boundary could be as simple as a pressure sensor, or as complicated as a laser network. They all do the same thing, but some work better than others.

It's already Halloween and the night is fast approaching. You swore to yourself last year that you wouldn't wait until the last minute again for a Halloween costume, yet here you are on Samhain without a costume… again. All of the costume shops are sure to be crammed with last-minute shoppers, and you don't feel like spending a lot of dough anyway, so what are your options?

Whenever a new hard drive is purchased for a computer, it needs to be formatted to work with that computer. Formatting a hard drive on a Macintosh computer is a fairly easy process.

In this video series, learn how to do advanced bmx tricks. Garson Fields shows you step-by-step instruction to turn you into an avid BMX rider. He shows you the basic steps of the bunny hop, and he offers ways to spin some variety on this traditional trick. Garson also shows you how to get bigger 180s on your BMX bike. Learn how to do bmx tricks like 270s, fullcabs, and nollies.

In this video series, our expert Sean Hobson will teach you how to play the defensive end position in American football. He will tell you about the job of the defensive end, how to get into a good stance, and how to fire off from both a three point stance and a four point stance. He will also teach you how to swatch the snap so as not to get drawn offsides, how to make contact with the opposing player after the snap, and how to do various moves on the football field like a spin move, a bull r...

In this instructional video series, learn how to play a 6-2 defense. Understand how the game works, with an introduction to the basic rules and objectives, as well as a rundown of the offensive and defensive positions on the field. Lessons also include skills and techniques for beginner offensive and defensive players: how to carry the ball, throw a pass, block effectively, punt, and make a solid hand off.

In this video series, watch as sports enthusiast and football fan Kenny Saylors teaches how to watch and understand the sport of American football. Learn what the different players and positions are, the different penalties, how long the game lasts, and how the field is set up.

Generative AI, or GenAI, is the hottest thing in tech at the moment, particularly for its ability to create content,p including essays, images, and videos. After Microsoft added its own GenAI tool to its Bing web search engine, Google is eager to follow suit, and you can be one of the first to try out Google's new GenAI search tool.

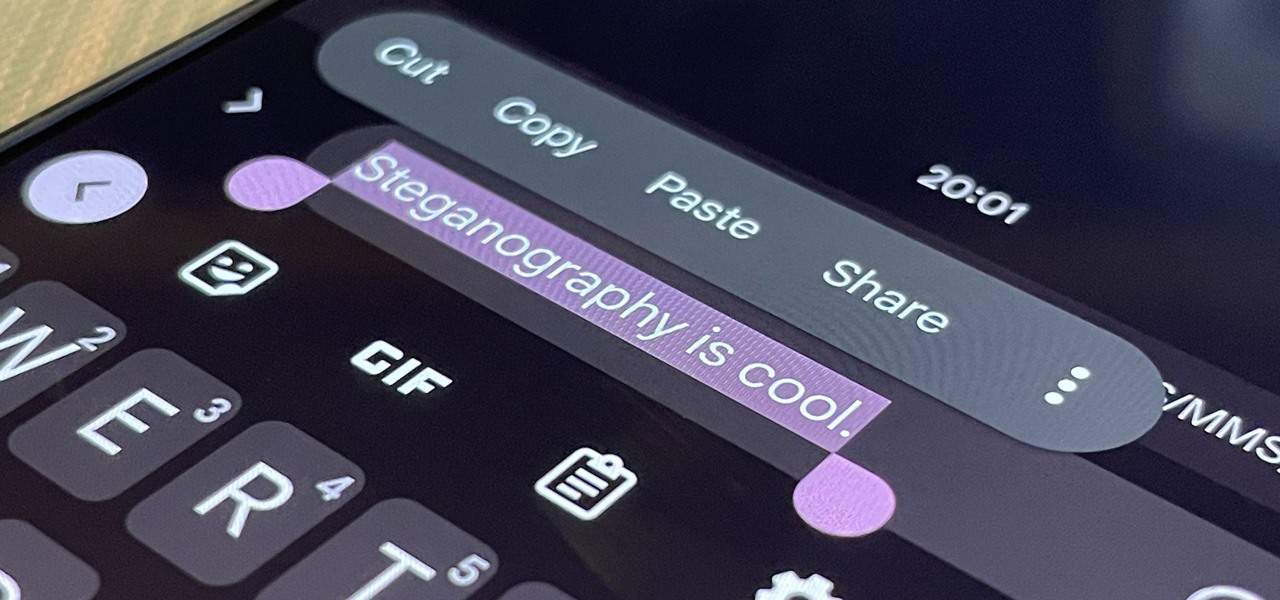
With a simple web-based tool, you can hide secret messages for family, friends, and fellow spies inside of plain text communications, and anyone that intercepts the messages will be none the wiser.

The standard way to sort your notes and to-dos in Reminders has always relied on you putting them in the correct list and group. Then came smart lists for flagged and scheduled tasks, followed shortly by a smart list for tasks assigned to you. In iOS 15, Apple brings yet another way to find your reminders more easily — tags.

Samsung and Google have done some amazing work together in the past, particularly with Android related projects. But after years of an inexplicable lack of interoperability, the primary smart home hardware divisions from both companies are finally on the same page — starting right now.

Bloatware is a problem on Android, and it's not just a Samsung thing. Removing apps that have the Uninstall or Disable button grayed out in Settings has always involved sending ADB commands to your phone from a computer, which itself was always such a pain to set up. Thankfully, that has finally changed.