Google's version of Android is best described as AOSP with extra features. But while the Pixel's UI is rightfully praised for its simplicity, those "extra features" aren't as numerous as they are on other OEM skins like Samsung's One UI. Case in point, there's no real system-wide audio EQ.

Smartphones are more like computers than actual telephones. Unfortunately, thieves, hackers, and other bad actors know this and are always looking to make money off your personal data. Thankfully, your Galaxy S20, S20+, or S20 Ultra has tools to combat these threats — as long as you know where to look.

It feels strange to be walking through an open field in a small village in the English countryside. There's no one else around — just the four of us: me, my husband, my 12-year-old son, and my adult niece. The day is spectacular, particularly for England. The sun is shining, and the temperature is in the low '70s.

Mystery is a tricky thing. Used correctly, it can give onlookers the impression that wondrous and perhaps valuable things are afoot. However, once the veil of suspension of disbelief is removed in any significant way, that same mystery can quickly turn into not just skepticism, but outright anger at what may have seemed like an attempt to dupe trusting onlookers.

For the uninitiated, it can be difficult to buy that special hacker in your life a perfect holiday gift. That's why we've taken out the guesswork and curated a list of the top 20 most popular items our readers are buying. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2018 selection of hacker holiday gifts.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

There are a lot of Android phones out there, and chances are that someone in your life is looking for one this holiday season. Well, there also happens to be a lot of Black Friday deals on Android phones this year. So we've rounded up the best deals taking place on Black Friday weekend to help you save big.

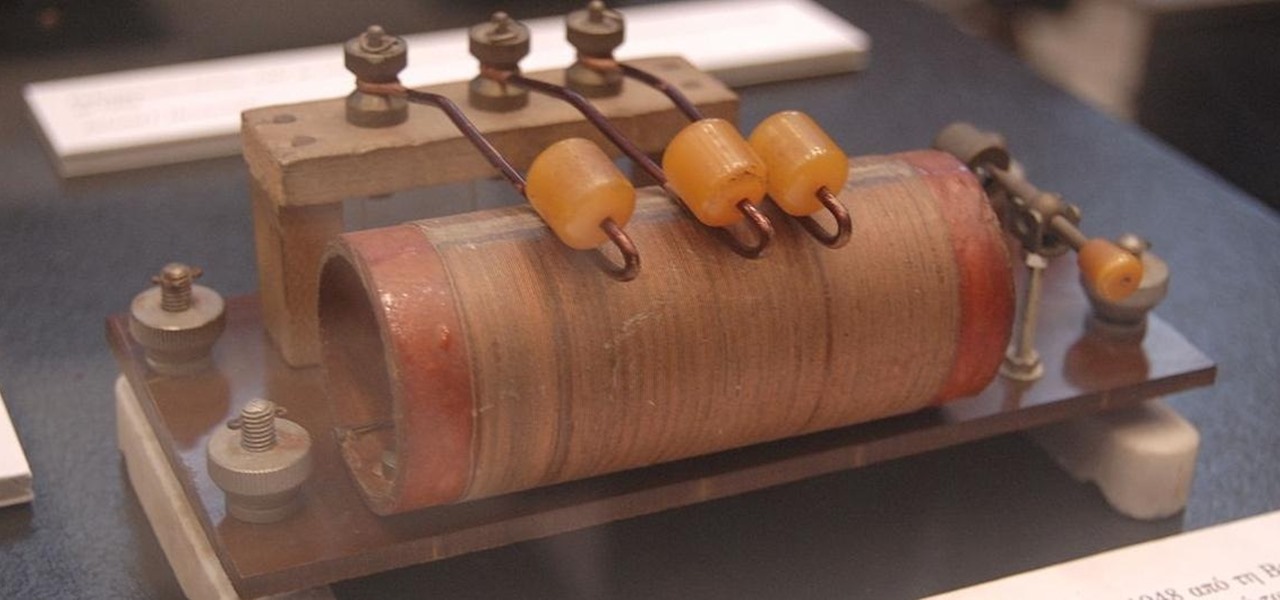
There's a lot that goes into making a nice crystal radio set, so this is going to have to be broken down into two parts. The first part is the actual making of a functional radio, and the second part is making the whole arrangement look nice. In this part, I'm actually going to tell you more than just how to make a crystal radio, but I'm also going to explain how and why they work. Crystal radios are pretty Steampunk in and of themselves, since they were first developed in the late 19th centu...

It’s called Urophagia—the art of consuming urine. There could be any number of reasons for having the desire to drink your own urine (or somebody else’s). There’s the so-called term “urine therapy,” which uses human urine as an alternative medicine. In urine therapy, or uropathy, it’s used therapeutically for various health, healing, and cosmetic purposes. There’s also those people who drink urine as sexual stimulation, where they want to share every part of each other. And then there’s the o...

Growing up, I was told that hard work could get me anything I wanted. But with Apple's Image Playground, I can create almost any illustration or drawing imaginable just by typing or selecting a suggestion. This groundbreaking feature in Apple Intelligence lets you generate images from simple prompts, opening up exciting possibilities for creativity.

Siri has long relied on basic sources like Google and Wikipedia for answers, but with iOS 18.2 and iPadOS 18.2, Apple is taking its virtual assistant to a new level by integrating ChatGPT. Now, you can use Siri to generate text and images with ChatGPT — and that's not all. ChatGPT is deeply integrated into Apple Intelligence and goes beyond just Siri.

At first glance, Apple's Messages app has always seemed pretty basic when it comes to text formatting options. However, there were and still are hidden ways to format text in your messages. But Apple's latest software updates give us even more ways to dress up text in messages, including more text effects.

Your iPhone is fairly secure by default, but Apple's Lockdown Mode takes it to Fort Knox levels of protection. If you're a high-value target for spyware, phishing attempts, and other sophisticated cyberattacks, it's an essential feature. But for almost everyone else, it's an extreme move. If you simply want to verify someone's identity when chatting, Contact Key Verification is a more practical option.

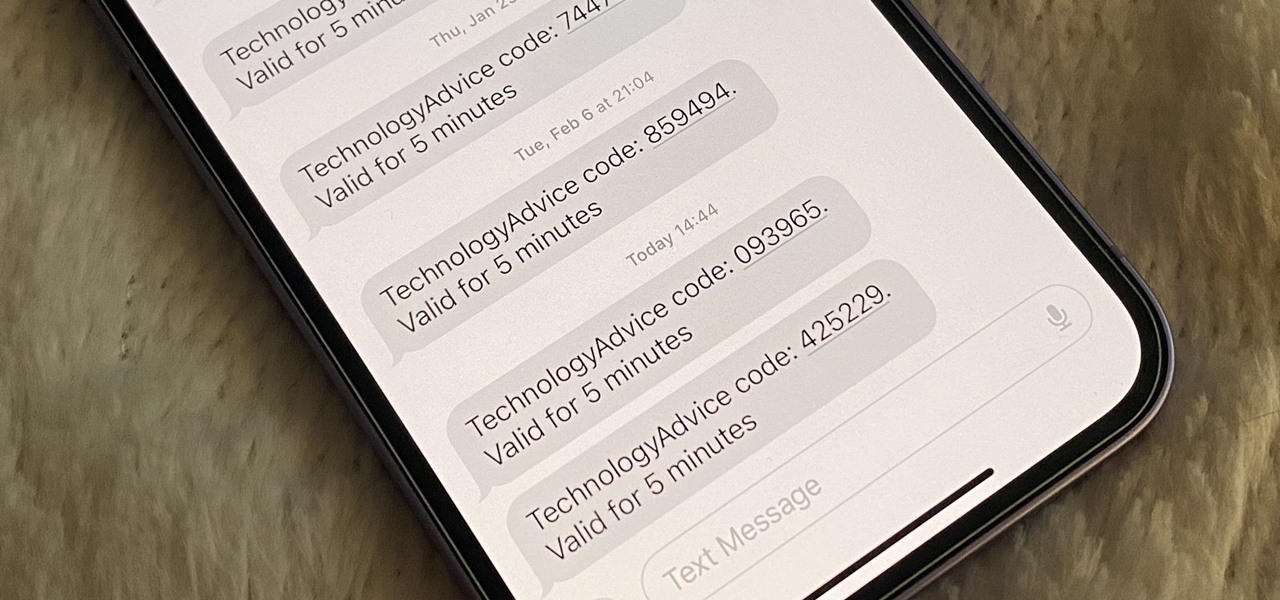
Many of your accounts online likely require two-factor authentication (2FA) or two-step verification (2SV) to confirm your identity when logging in, and there's a good chance the second factor or step for each is a one-time email or SMS verification code. If you get a lot of email and SMS codes, it can clutter your Mail and Messages apps with junk if you don't delete the messages after signing in.

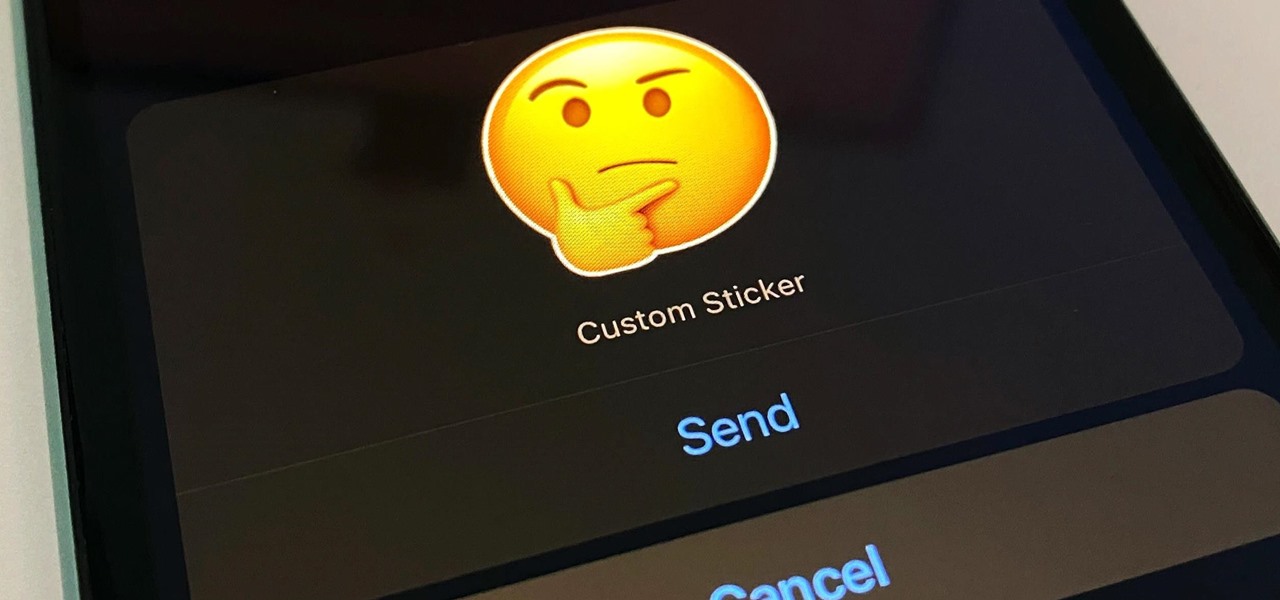
WhatsApp has a new sticker-making tool in the iPhone app that lets you create custom stickers directly in chats using your own images, eliminating the need to rely on third-party apps to make them.

Handwritten notes are no doubt useful at home, work, and school, but digitizing them with your smartphone will make them easier to edit, organize, and review. You'll also always have a digital copy ready if your handwritten notes get lost or erased. And Google Keep for Android, iOS, or iPadOS makes the conversion from physical form to digital a cinch, especially when it comes to checklists.

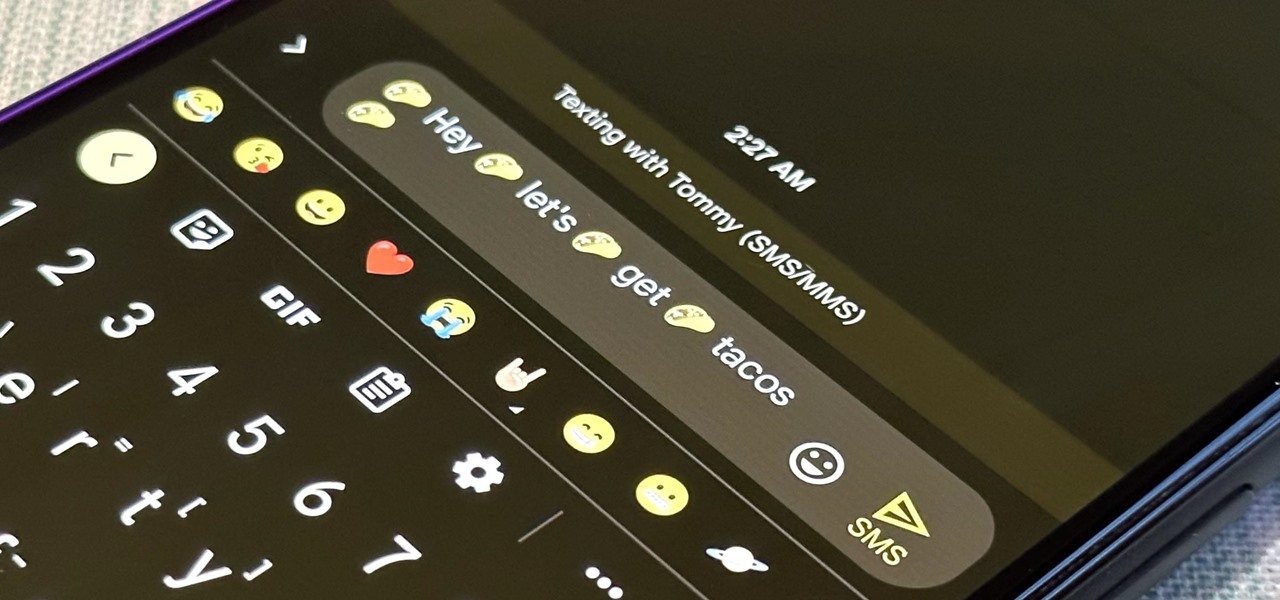
Emoji characters make messaging more fun, and Google has continuously added convenient and fun ways to insert playful symbols into your conversations using Gboard. After getting Emoji Kitchen in early 2020, we now have Emojify, a tool that automatically adds emoji to your message drafts.

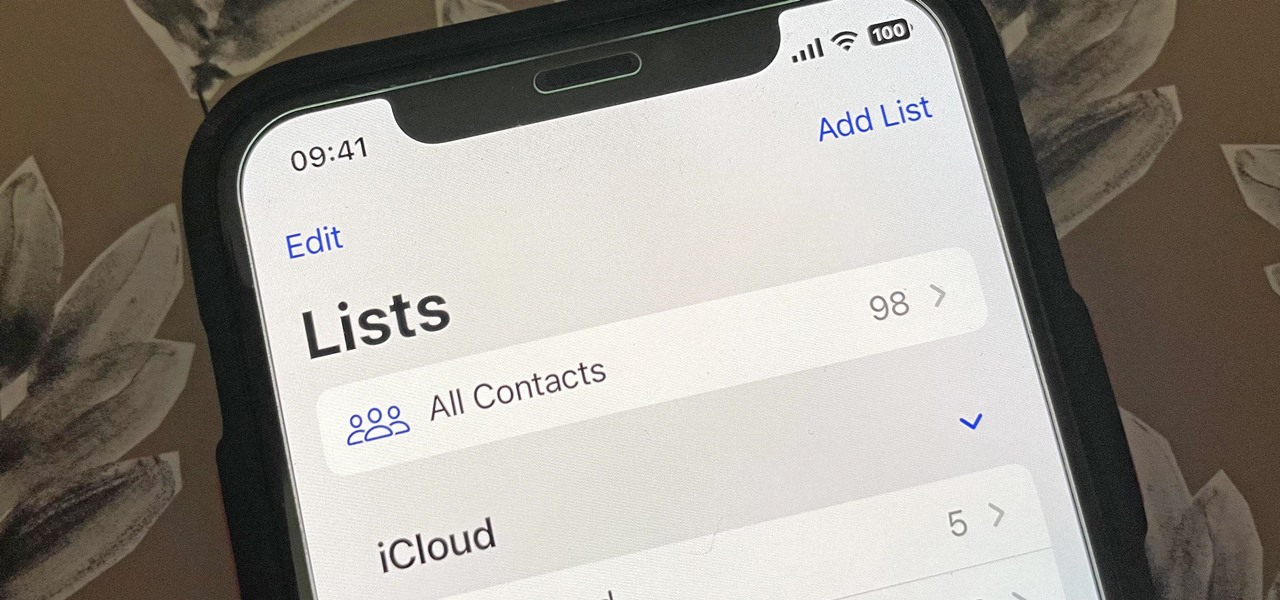
Apple's Contacts app just got its biggest update ever. Since the first iPhone in 2008, there have only been minor upgrades here and there to how you manage and interact with contacts. That changes with iOS 16.

Whenever you need to type out a fraction on your iPhone, whether in a message, word document, presentation, math problem, recipe, or wherever else you need it, it's easy to use numbers and slashes. But there's a way to make fractions look more professional and easier to read straight from your keyboard.

Whenever you need to digitally share large bodies of real-world text, you'd likely show a photo of it or manually type everything into the document or chat. But iOS 15 has a much better way for your iPhone.

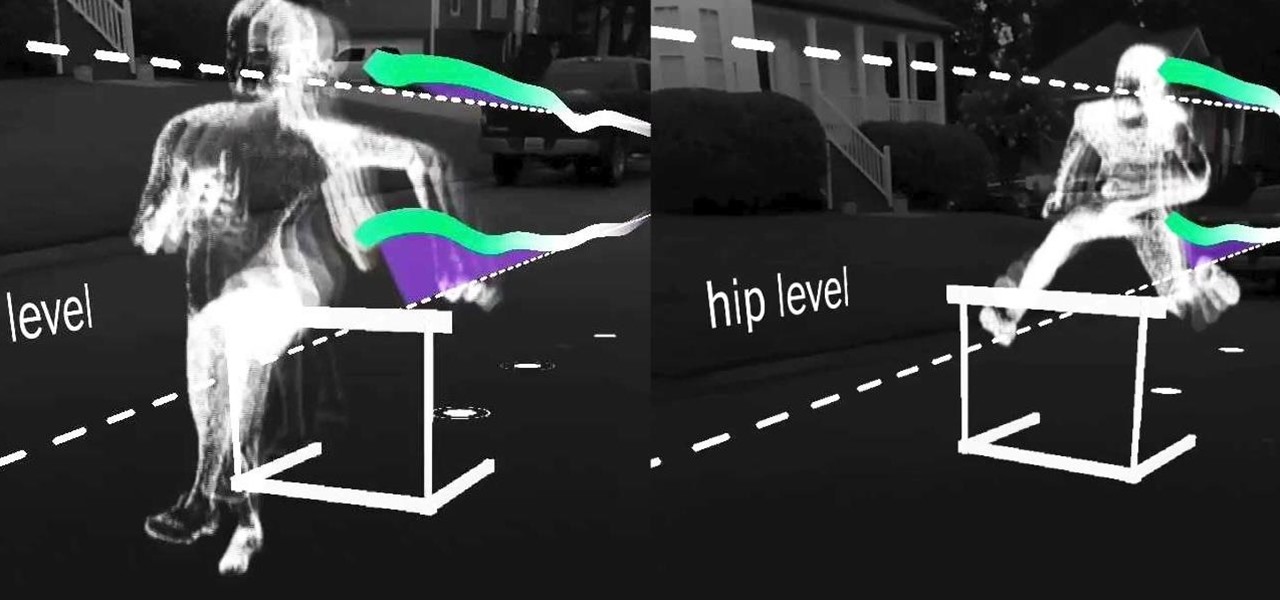
The enterprise-focused category of augmented reality doesn't often get the headlines due to its relatively sedate profile as a mostly factory floor and training-based tool.

Old school media stalwart The New York Times launched its augmented reality news content in 2018 with a feature on the athletes of the Winter Olympics.

After receiving $100 million in funding in 2018, smartglasses maker Rokid is going the crowdfunding route to finance its latest product.

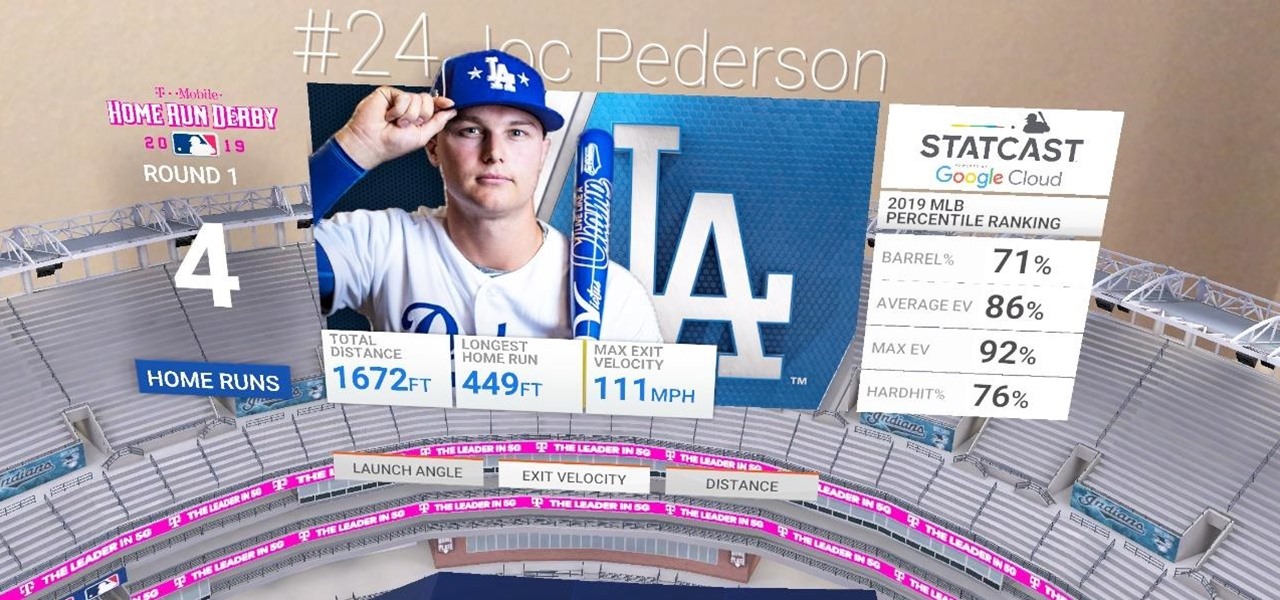
The 2021 season of Major League Baseball (MLB) is in full swing, and now that vaccines are widespread in the US, major baseball stadiums are allowing fans back in at full capacity.

It's all fun and games until the technology is actually put into use and you realize augmented reality is now part of Death Star.

While Apple was one of the first to integrate LiDAR into mobile devices for depth sensing, headset maker Varjo has developed a truly remarkable feat with its implementation of the sensor.

During the Tuesday launch of Google I/O, the company's CEO, Sundar Pichai, pulled off a Steve Jobsian "one more thing" move near the end of his keynote address that was simply stunning.

The progress Tooz has been making in the smartglasses space has been mostly kept under wraps, but the company is slowly giving us a deeper look at what it has in store for smartglasses wearers.

After the mobile augmented reality platforms of ARKit and ARCore moved Google's previously groundbreaking Project Tango (the AR platform that gave us the first smartphones with depth sensors) into obsolescence in 2018, we've seen a bit of a resurgence of what was then a niche component for flagship devices.

If you've been thinking about changing careers and you have just a little bit of time, The Ultimate 2021 Web Developer & Designer Super Bundle may be just what you need. This is also the perfect time to get it because it's on sale for $34.99, which is 98% off the regular price of $1,886. You'll get 14 courses that offer 39 hours of content on HTML, JavaScript, CSS, and more.

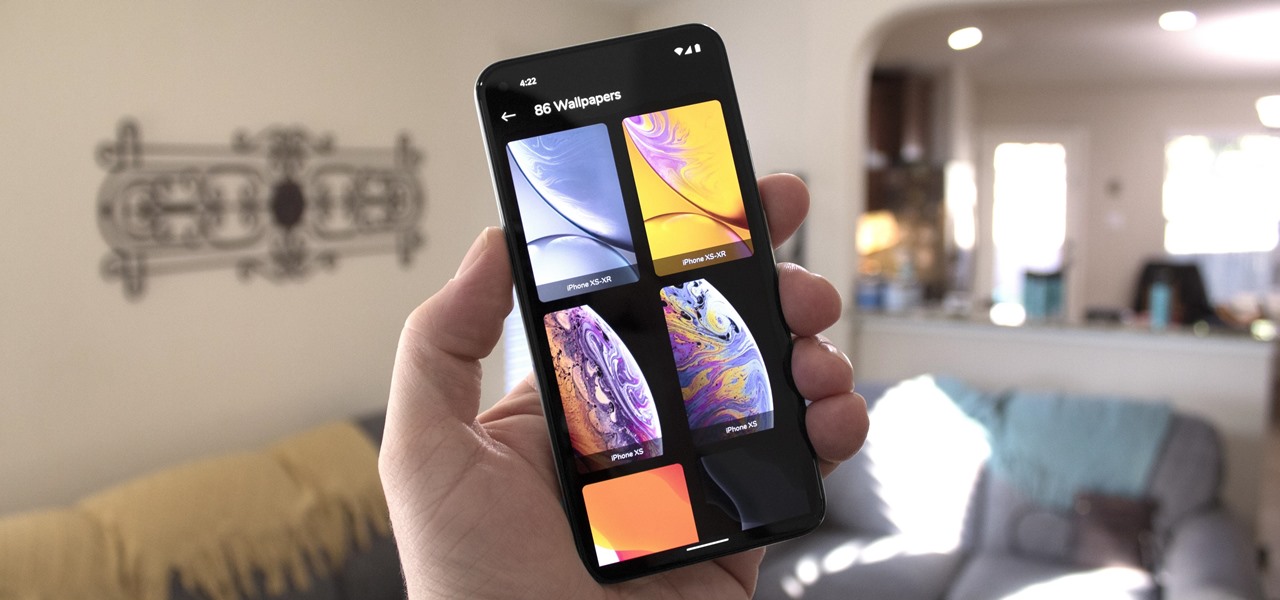
These days, the only thing your eyes view more than your phone's home screen is the backside of your eyelids. So it goes without saying that whatever picture you have as your background gets old pretty fast.

Frequent readers of Null Byte are no strangers to the basic elements of app and web development. Whether you're a seasoned programmer who works extensively on front-end designs or an aspiring app-builder who's working on expanding your portfolio, you're likely familiar with at least a few go-to programming languages and platforms that are popular within your field.

This week, developer Niantic began rolling out a new feature called AR Mapping to Pokémon GO that has bigger implications on the realism of augmented reality in mobile gaming and beyond.

Anyone looking to have a complete set of design tools at their fingertips needs to look no further than Adobe's Creative Cloud. This suite of applications is the go-to platform for creative software and is, in many ways, a must-know in fields like graphic design, video editing, and photography.

Dreaming up the next big business is easy. Running day-to-day administrative tasks is not. The tedious nature of entrepreneurship is the barrier that holds many people back from realizing their full potential.

If you're an aspiring or even well-established web or app developer, the good news is that there's a virtually limitless number of lucrative opportunities waiting for you, regardless of whether you're looking to work for a company or as a freelancer.

Now that more people are working from home on unsecured networks and personal devices, hackers are having a field day accessing everything from private browsing histories to personal banking information. A virtual private network (VPN) is the first and most important line of defense when it comes to protecting all of your devices from digital intrusions, but not all VPNs are created equal.

Regardless of whether you're an aspiring or established coding pro, knowing just one or two programming languages and platforms is no longer sufficient if you want to be truly competitive in an increasingly popular and lucrative field. But before you spend an excessive amount of time mastering six new platforms, do yourself a favor and master Linux.

Good communication is essential when managing teams and overseeing complex projects. Whether you're developing the latest and greatest app or trying to get ahead of a large data science project, effective communicators are always in high demand.

You don't need to work as an executive at Google to understand and appreciate the importance of large-scale data analytics in today's world. Whether you're interested in joining the ranks of a major tech firm or want to improve your company's marketing campaigns through consumer analysis, knowing how to work with large sets of complex data is paramount.