After two years of poor sales, LG decided to shake up its mobile division. New executives are at the helm, and changes to their flagship lineups are already underway. Specifically, the V series is expanding, as LG announced the second new device in the series, the LG V35 ThinQ.

Augmented reality developers are rapidly bringing science fiction tropes into the real world, with the latest example leveraging the TrueDepth camera on the iPhone X to emulate the cloaking technology made famous by movies like Predator and Marvel's The Avengers.

So you want to do Kendrick Lamar's "HUMBLE." in Animoji Karaoke, but you need the lyrics. Well, now you can see those rhymes spit out in augmented reality.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

If you own a Pixel or Nexus device, Project Fi is a great alternative for cellular service outside of the four major US carriers. Project Fi is a Google-managed MVNO, providing service primarily through the T-Mobile and Sprint networks. One of the biggest mysteries on Fi is which network you're connected to at any given time, but there's a simple solution.

If you have a taste for sweets, you have at least one thing in common with mosquitoes. While too much sugar is unhealthy for humans, a new product makes sweets deadly to mosquitoes.

The future is here with a new demo made with Apple's ARKit and LeapMotion. Typically, since ARKit works through your iPhone, in order to move augmented reality objects that are appearing on your screen, you have to drag them with your finger. However, developer Arthur Schiller is now playing around with how you can move augmented reality objects on your phone with gesture recognition, rather than by touching.

That soil under your feet is not just dirt. It is teeming with life that may not change as fast as we would like when challenged by global warming.

The release of Unity 5.6 brought with it several great enhancements. One of those enhancements is the new Video Player component. This addition allows for adding videos to your scenes quickly and with plenty of flexibility. Whether you are looking to simply add a video to a plane, or get creative and build a world layered with videos on 3D objects, Unity 5.6 has your back.

The Great Barrier Reef in Australia is the largest living system on the planet. Yet more than 90% of the reef is bleaching because of the loss of a tiny algae that lives within the coral.

Princess Cruises' Coral Princess voyage disembarked in Fort Lauderdale on Saturday, March 18, after a 10-day cruise in which 182 people were sickened with symptoms of vomiting and diarrhea. According to federal health officials, a norovirus is suspected for the outbreak.

It's the bane of many a tech geek's existence that the customizability of Android software cannot be combined with the sleek design of the iPhone. A new Kickstarter project titled Eye, however, is looking to change that with a new iPhone case that allows you to combine the two.

Phuket, the island in Thailand typically associated with paradise and most recently, illegally-run hotels, now has a different problem—a stray cat with the claws of death.

LG announced their latest high-end device on September 6 and its specs are pretty amazing: The new V20 sports three cameras, two displays, three microphones, four DACs for high-end sound, and it's all powered by a removable battery.

Hello everybody. I'm back with Part-2 of this series. In this part we will be programming in C our server and i will be explaining one more "key concept" so everybody got a better understanding on this.

Hello NullByte, it's mkilic! This time I'm here with the C.H.I.P from NTC. Although it is not too popular, the C.H.I.P is a brand new micro computer. It is very similar to the Raspberry Pi or Beaglebone Black. The key difference with this particular board is its cost and size. The C.H.I.P only costs $9 and measures 2.5 x 1.5 inches. In addition to this, the C.H.I.P has built in 802.11 b/g/n Wifi and Bluetooth 4.0. Considering these great specs, what could a Hacker use this for? Step 1: The In...

When people get accustomed to something, any type of change is typically met with resistance or disdain. So when Twitter decided to swap stars for hearts, the internet wasn't exactly receptive to the new aesthetic.

Mockingjay - Part 2, the final film in the Hunger Games series, hits theaters next month, and what better way to celebrate one of the series' most fabulous characters than with an over-the-top costume this Halloween?

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

Welcome back, my tenderfoot hackers! In this series, we are exploring the myriad of ways to hack web applications. As you know, web applications are those apps that run the websites of everything from your next door neighbor, to the all-powerful financial institutions that run the world. Each of these applications is vulnerable to attack, but not all in the same way.

Microsoft's new voice-enabled virtual assistant, Cortana, is a lot like a blend of Siri's personality and Google Now's predictive capabilities—but the best part is it's baked right into the taskbar in Windows 10.

According to George Gjoka, a professional Paintless Dent Repair (PDR) technician, when you attempt to take a dent out of your car, you're probably doing it wrong.

With the release of various new and updated Samsung Galaxy S6 apps and features, like Smart Switch, Smart Remote, and wallpapers, something that's a home screen staple for most Android users was still missing.

After installing an app from the Google Play Store, its icon will appear on your home screen, creating a shortcut for you to easily access it without needing to look very far. But if you've installed as many apps as I have, these shortcuts begin to add up and eventually make your home screen look like an iPhone, turning it into just another app drawer.

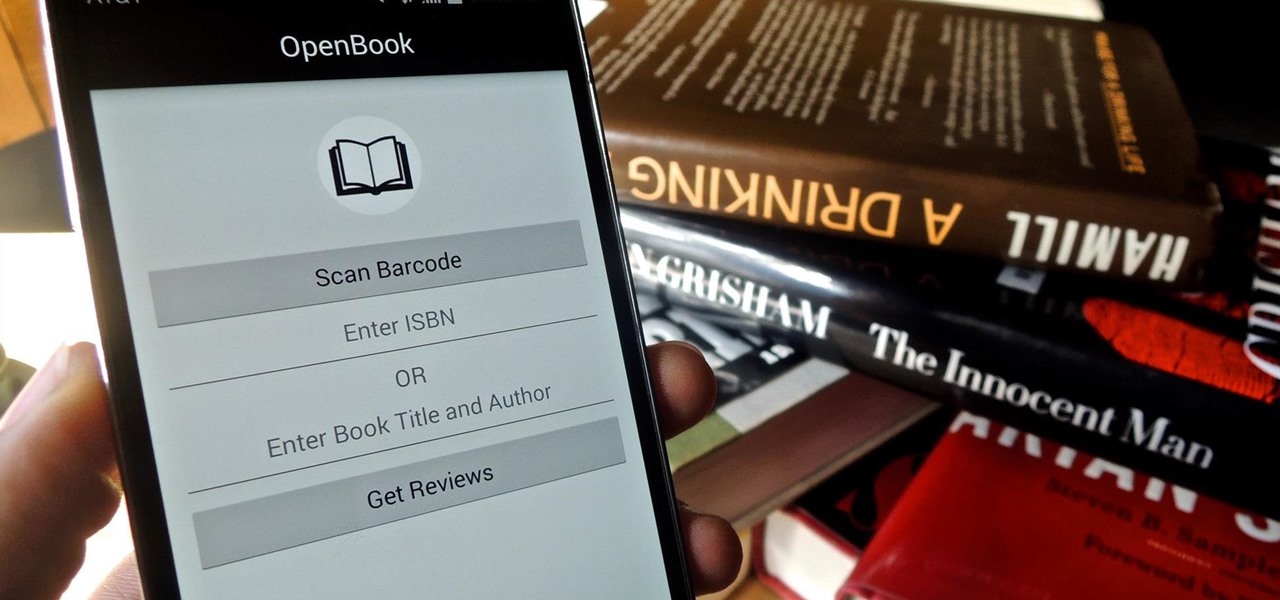
Purchasing an actual book from a brick-and-mortar store is becoming increasingly less common for people to do, but it hasn't completely gone out of style just yet. There's something about entering a bookstore and viewing all the potential great stories and epic tales just sitting on the shelves, waiting to be discovered.

Left-handers only make up about ten percent of the world, which means they typically have to use things made for the majority, i.e., right-handed people. If that wasn't annoying enough, there are studies that show that lefties actually get paid less.

Bearded women are typically more freaky than scary—yet when it comes to American Horror Story, nothing is as it seems.

Looking for a costume that breaks the mold of skimpy and clinging fabrics? Stay warm on Halloween and impress at any spooky event by turning yourself into a perfect recreation of the apes in Dawn of the Planet of the Apes.

Reminding a spouse or roommate to pick up some last-minute groceries is typically done with a quick message that can easily go unnoticed or unseen. Your feeble attempt of a reminder won't work unless it's conveniently sent at the right moment, like when they're on their way home. Chances are, you'll forget to text them and they'll forget the earlier reminder you sent.

We don't typically cover games here on softModder, unless they have some special feature to offer like unlocking your device, but sometimes you've just gotta game. When you've only got a few minutes to do so, you've gotta choose the right game, and I've got just the thing for you.

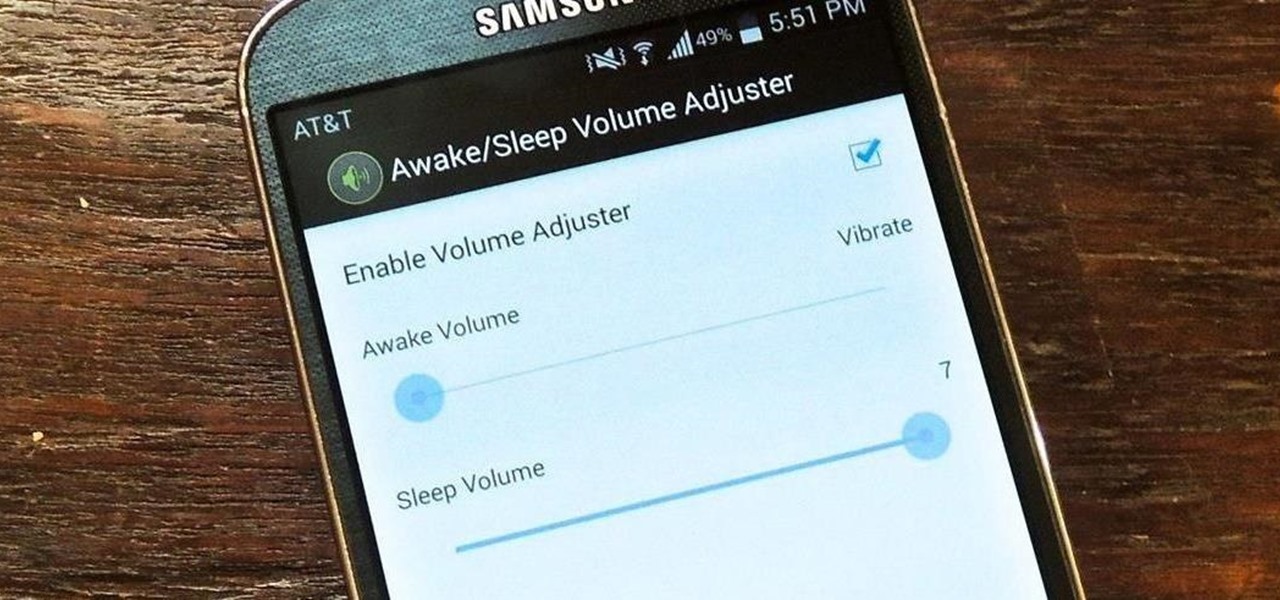
When I'm not actively using my Samsung Galaxy S4, I typically crank the volume up all the way so I can hear it in my pocket or if I'm in another room. But when it's in my hands and I'm using it, I don't want the ringer to blast at full volume, or any volume at all. Either I'll see a notification come in, or a quick vibrate will call my attention to any pertinent alerts.

Have you ever looked at your iPhone dock and wished you could place an extra, essential, or highly utilized app on there? Currently, with the basic settings you can only place four, but there's always that one that you wish could add to the mix.

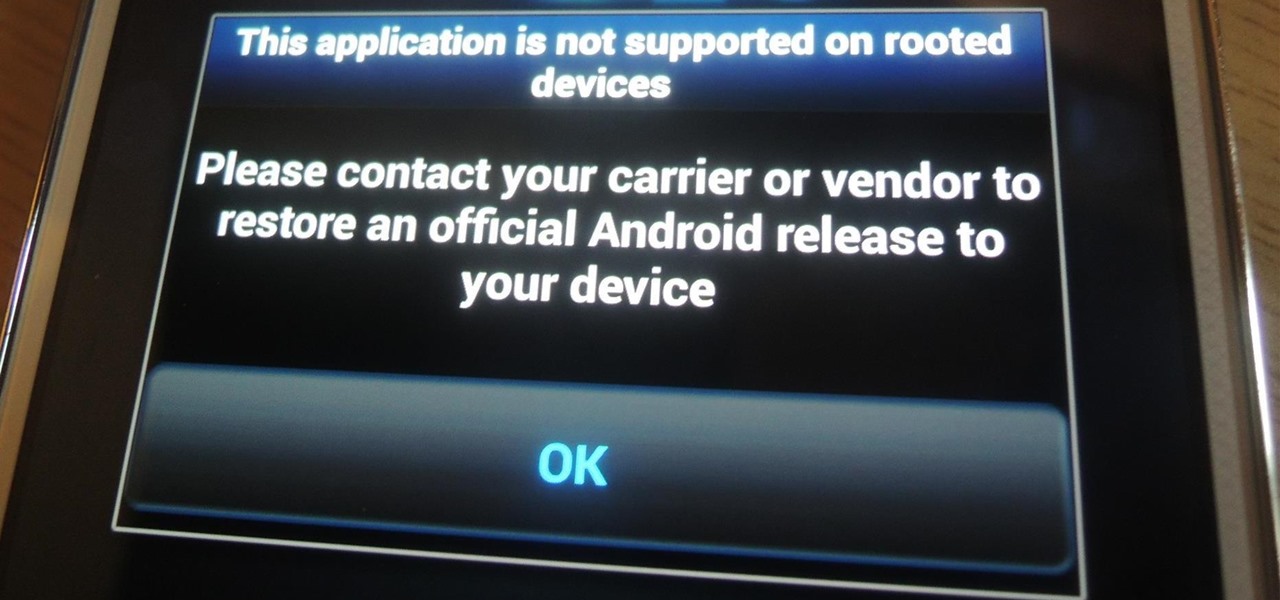
As a preventative measure against exploitation, certain Android applications won't work if your device is rooted. Opening one of these apps that detects root will typically end up with a warning and an inability to access its features, like in the picture below. AS IF!

Ladies and gentleman, it's official—"Selfie" has been named Word of the Year by Oxford Dictionaries.

The following video demonstrates and explains a classic physics experiment called a vacuum cannon. Typically these cannons are made on a much smaller scale to fire ping pong balls, but I wanted to keep things interesting with this 4" diameter monster.

A lot of my hacks use salvaged parts from an old microwave, with the microwave oven transformer (MOT) being the most useful component.

Recently I was working outside forming a driveway in the rain. Working in and around the wet sand was not friendly on my tools, especially my tape measure. About halfway through the day my tape measure would need "encouragement" in order to retract to the closed postion. Not too much later, with force applied, it would remain standing out at 1ft. and the problem progressively got worse.

Forgot the passwords to your email or your other favorite websites? If you typically store your passwords in Internet Explorer (IE9 or other versions) it can be tricky to get your passwords back -- but this tutorial makes it really easy!

It's September 1st, 1859, and the Earth looks more or less like something out of an apocalyptic movie or Sci-Fi novel. All communications have failed, it's so bright outside at midnight that people are getting up and making breakfast, and people all over the world are seeing auroras. The solar storm that produced the electromagnetic pulse and caused all this mayhem is known as the Carrington Event, and storms like it happen about about once every century.

This video gives viewers an overview on how to use the manual settings of your DSLR camera. Aside from the Auto setting, your DSLR camera has the P-mode which is the program mode, S-mode which is the shutter priority mode, A-mode which is the aperture priority mode and finally the M-mode which is the complete manual mode. P-mode or program mode is more like the Auto-mode in your camera. You can't control your shutter speed and f-stops (aperture) however; you can manipulate the other settings ...