
Field Typically Search Results


How To: Adjust the Alignment of Cabinet Doors
Poor alignment of cabinet doors will cause a kitchen to look run-down and may be embarrassing to the homeowner. Luckily, with a single screw driver and a little ambition, the door alignment can look brand new.

How To: Practice cricket bowling drills properly
Practice these cricket bowling drills to develop your cricket bowling. This video gives good information on some useful bowling drills for cricket players and those coaching.

How To: Make Young Sports Players Faster with Speed Drills
If you're a pee wee coach, you know that coaching kids is a tough job. Children can even be more difficult to work with than adults, but it's the best time to shape them into a great sportsman… and to get faster!

How To: Play scramble in golf
This video shows the viewer how to take part in a ‘scramble’ golf tournament. This type of event is typically for amateurs and is essentially played as a team sport, this is unusual for golf. The general principal is that everyone plays the first drive. The team then decides which drive was the best. They then move all the balls to this point and all play as if they hit that shot. They repeat the same procedure until one of the balls has been putted. This method allows amateurs to get a reaso...

How To: Change text styles in Brother P-Touch Editor software
In this simple video tutorial, you'll be learning how to change a label's font and text style using the Brother P-Touch Editor software (this applies to higher-end P-Touch Labellers and the QL series of label printers).

How To: Tackle in a game of rugby
Tackling in rugby leads to various consequences based on the style of rugby being played. Learn how to play rugby, including rules and skills, in this video rugby lesson.

How To: Do offensive scrum tactics in a game of rugby
Offense tactics are important in rugby, where the ball cannot be thrown forward. Learn how to play rugby, including rules and skills, in this video rugby lesson.

How To: Install additional shelving in an office closet
Home improvement expert Danny Lipford talks about additional closet shelving. See this video tutorial to see how to install additional shelving in an office closet.
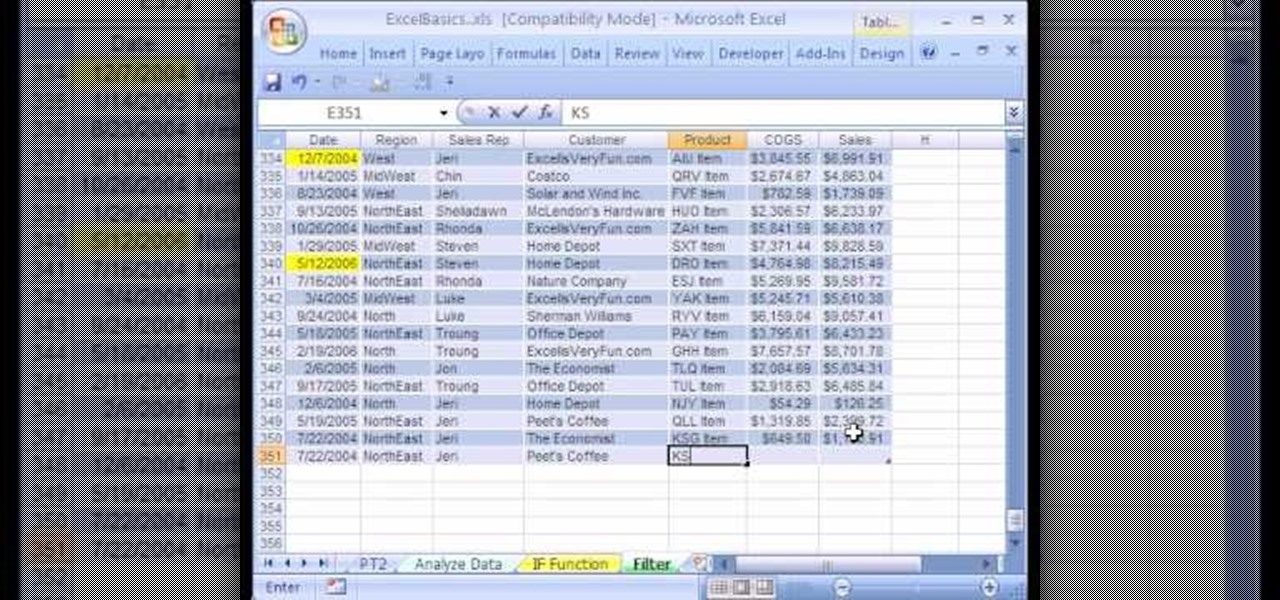
How To: Use Excel data analysis filter & dynamic ranges
We're on sheet, tab, filter. We want to talk about filter, but we also want to talk about an Excel table or list. It is simply a data set with field names at the top, records in rows, no blanks anywhere and no other data sets touching this data set. When we convert to a table, it does a lot of amazing things. The new keyboard shortcut is "Ctrl T". If data is set up correctly, it will work. Click Ok. You can build a function based on a column of data, i.e. "Alt =" which is the shortcut for sum...

How To: Use Genmoji to Create Custom Emoji That Work Just Like Regular Emoji in Messages, Notes, and More
There are thousands of emoji characters, but finding the right one can feel like a wild goose chase. Want a red panda? You can have a black-and-white one. Need a crying heart? You're out of luck. With Apple Intelligence, finding the right emoji for any occasion is now a reality.

How To: Unlock iOS 16.4's Hidden Skin Tones for the Pushing Hand Characters in Your Emoji Keyboard
Apple pushed out 31 new emoji with iOS 16.4 and iPadOS 16.4, but it somehow forgot to add ten of those — all skin-tone variations for the new leftward and rightward pushing hand characters — to the iOS keyboard. Here's how to unlock and use them.
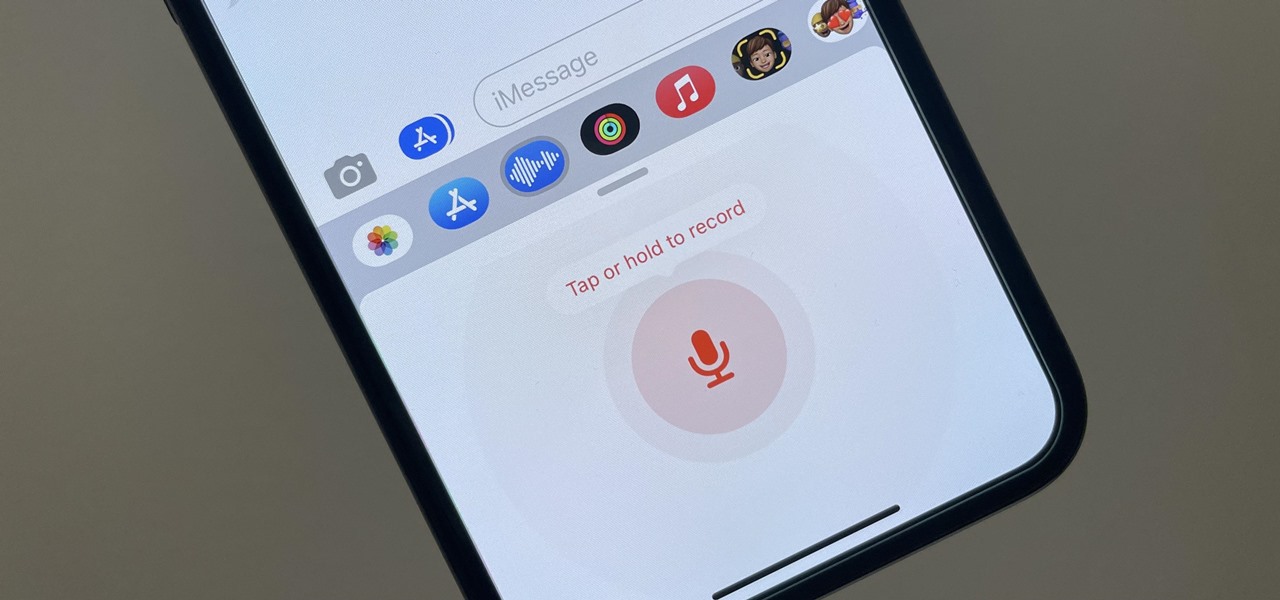
How To: iOS 16 Changes How You Record and Send Audio Messages on Your iPhone — Here's How It Works Now
To record an audio message in the Messages app on iOS 15, you would tap and hold the audio messages button in the text entry field of the conversation. Then, you could let go to preview it before sending it or swipe up to send it right away. That's no longer the case on iOS 16 for iPhone.

News: Facebook Makes Portal Portable, Upgrades Portal Plus, & Adds Microsoft Teams
With the arrival of Facebook Ray-Ban Stories smartglasses commanding the recent spotlight, the tech world acted like it forgot about Facebook's first foray in consumer hardware — the Portal line of video calling devices.

News: Deutsche Telekom Opens Early Access to Tooz Smartglasses via Dev Kit
If you're a developer working on the bleeding edge of augmented reality, or even an enthusiastic smartglasses early adopter, being first in line for new wearable hardware is a priority.

News: Microsoft Wins $21 Billion Contract to Produce Military-Grade HoloLens for US Army
After years of testing and modifications, the US Army is moving forward with its customized version of HoloLens 2 from Microsoft.

News: Epson & Spinar Bundle Smartglasses & Remote AR Assistance via Zoom for Enterprise Customers
The COVID-19 pandemic forced many businesses into remote work models, whether they were ready or not, making Zoom a household (or home office) name for its video conferencing service.
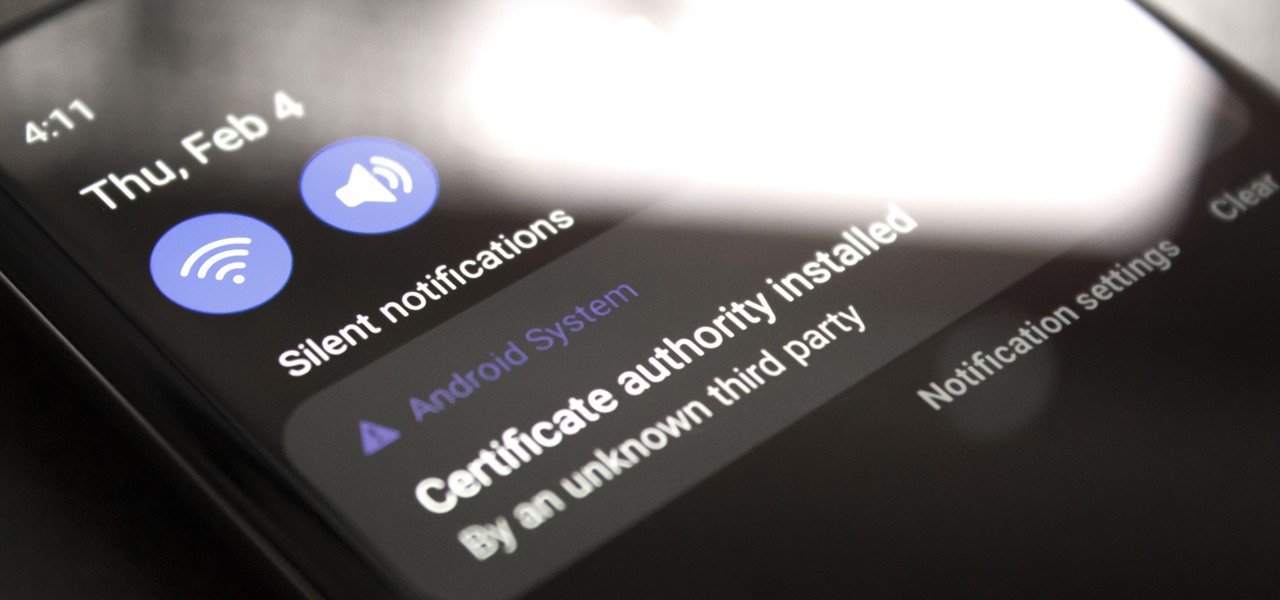
How To: Automatically Clear Nagging System Notifications on Android
If you're using a VPN-based ad blocker with full HTTPS functionality on a Samsung phone, you'll get a notification informing you there's a third-party security certificate in use. No big deal, except it shows up every time you restart the phone. Samsung isn't alone in this type of annoyance, either.

News: Lenovo Debuts Sleek ThinkReality A3 Smartglasses for Industrial & Office Use
Roughly a year and a half after unveiling the HoloLens-like ThinkReality A6, Lenovo is back with its take on enterprise-grade smartglasses, and the results look impressive. Then again, looks can be deceiving.

How To: Break into the World of Electrical Engineering with This Bundle
Tech-savvy programmers and developers usually apply their unique talents exclusively to creating apps and websites — two high-paying and exciting pursuits that can open countless doors and opportunities in multiple fields.

How To: Learn Everything You'll Ever Need to Know About IoT
The Internet of Things (IoT) is changing everything in our homes and at work, from security systems and lighting fixtures to smartphones and speakers. An estimated 50 billion devices are now hooked up to IoT.
How To: Tackle Python & AI with This Extensive Training Package
In a world that's becoming increasingly dependent on a variety of AI and machine learning applications, Big Data reigns supreme. As the primary forces behind everything from self-driving cars and surgical robots to home automation systems and even space exploration, Big Data and AI stand at the heart of today's most important innovations.

How To: Become a Six Sigma Black Belt with This $30 Training
Wherever life takes you, knowing how to successfully manage both large-scale projects and teams will undoubtedly serve you well. Whether you're eyeing a promotion at work or looking to switch to an entirely different field, having the skills to innovate products, inspire people, and solve problems will make you stand out to your current and future employers.

How To: iOS 14's Revamped Home Screen Search Can Help You Open Hidden Apps Faster
The ability to hide entire pages on your iPhone's home screen is an excellent privacy upgrade packed into iOS 14. That said, it can be a bit of a pain to find and open the hidden apps on those pages in a timely fashion. Luckily, iOS 14 has a solution that makes opening those apps, as well as any others, faster and more convenient — and we're not talking about the new App Library.

How to Hack with Arduino: Defeat VPNs & Track a MacOS Computer Remotely
The Digispark is a low-cost USB development board that's programmable in Arduino and capable of posing as a keyboard, allowing it to deliver a number of payloads. For only a few dollars, we can use the Digispark to deliver a payload to a macOS computer that will track the Mac every 60 seconds, even bypassing security like a VPN.

News: Full Galaxy Z Flip Spec Sheet Review — Samsung's New Clamshell Phone Is a Flagship Even Without the Fold
Samsung decided to jump into the foldable category early, announcing the Galaxy Fold in February 2019. After a major hiccup, Samsung released the phone four months later to praise. But Samsung's not finished with foldables, as the new Galaxy Z Flip is just on the horizon.
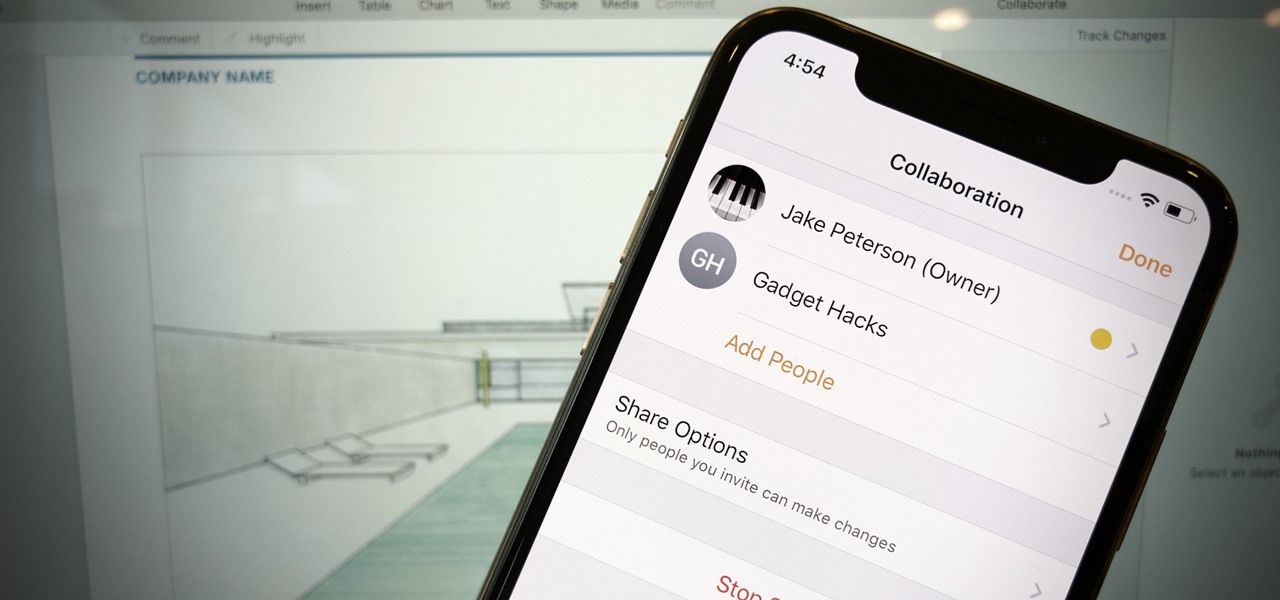
How To: Collaborate on Pages Documents with Friends & Colleagues
Google Docs is made for teamwork and collaboration, but Apple's iWork suite also comes with the same functionality. If you're working on a Pages document on your iPhone, and you want input from other members of your team, you can easily invite them to view, comment, edit, and more right alongside you.

How To: Beat LFI Restrictions with Advanced Techniques
One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

How To: Find Vulnerable Webcams Across the Globe Using Shodan
Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.

Hands-On: Niantic's Harry Potter: Wizards Unite Brings New Magic to the World of Augmented Reality
Can lightning strike twice? Niantic is betting that it can with its latest augmented reality game based on the best-selling multimedia franchise Harry Potter.

How To: Create Packets from Scratch with Scapy for Scanning & DoSing
By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

How To: Target Bluetooth Devices with Bettercap
An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

How To: Add 2-Step Verification to Uber for Stronger Overall Account Security
If you've ever received an email from a sketchy address purporting to be Uber, asking you to sign in with your credentials, you might be a phishing target. Hackers use a fake login page from real-looking domains to trick you into giving up your account information, and while it's been an issue in the past, Uber is making it more difficult on cyber thieves with the addition of two-step verification.
News: Everything You Need to Know About the Samsung Galaxy S10e
With Apple releasing the iPhone XR, it appears Samsung is looking to challenge this "budget flagship" option head-on. They brought their usual two phone releases this year, but also threw in another three for a total of five phones, including the Samsung Galaxy S10e. And for many, this might be the option to look at.

News: The 5 Most Innovative Augmented Reality Products of 2018
In 2018, augmented reality went from the vague promise of interesting things in the near future to tangible developments in software and hardware, proving that immersive computing is indeed the future.

How To: Control Your Apple TV with Just Your iPhone
So, you've lost your Apple TV remote. Maybe it's busted. What are you supposed to do now? You could go out and buy a new one, but they're expensive if you have a newer Apple TV with a Siri Remote, and wouldn't you rather spend that money on a movie? You might be without a working dedicated remote, but you likely have the next best thing already in your pocket.

How To: The 4 Best Apps for Downloading Movies & TV Shows
Streaming movies and TV shows on phones is more popular today than ever, but what about when you're on a plane, have a limited data plan, or will be in a no-service area? You'll want to download your movies and TV shows instead. While Netflix is excellent, you can't rent or download most of the latest movies and TV series. What you need is an app that lets you do just that.

How To: Unlock the Bootloader on Your OnePlus 6T
Before you can dive into customizing your OnePlus 6T, you must take the initial step of unlocking the bootloader to gain the ability to install TWRP, Magisk, custom ROMs, and other mods.

How To: Call Recorder Jailbreak Tweak Lets You Record iPhone Calls for Cheap
You don't need an obsessive ex stalking you to benefit from the ability to record calls on your iPhone in a pinch. Besides protecting yourself from nefarious intent, recording important conversations like verbal contracts and agreements can help you cover all your bases and ensure you're insulated from any potential liabilities that may appear down the road.

How To: The Easy Way to Use PGP for Encrypting Emails on Windows, Mac & Linux
In order to increase the security and harden the integrity of an email account and its content, you'll want to use PGP on your Windows, macOS, or Linux computer. This is usually the first thing security analysts do to protect communications with encryption, and everyone else should consider it too, especially since there's an easy way to incorporate PGP that anyone can follow.

