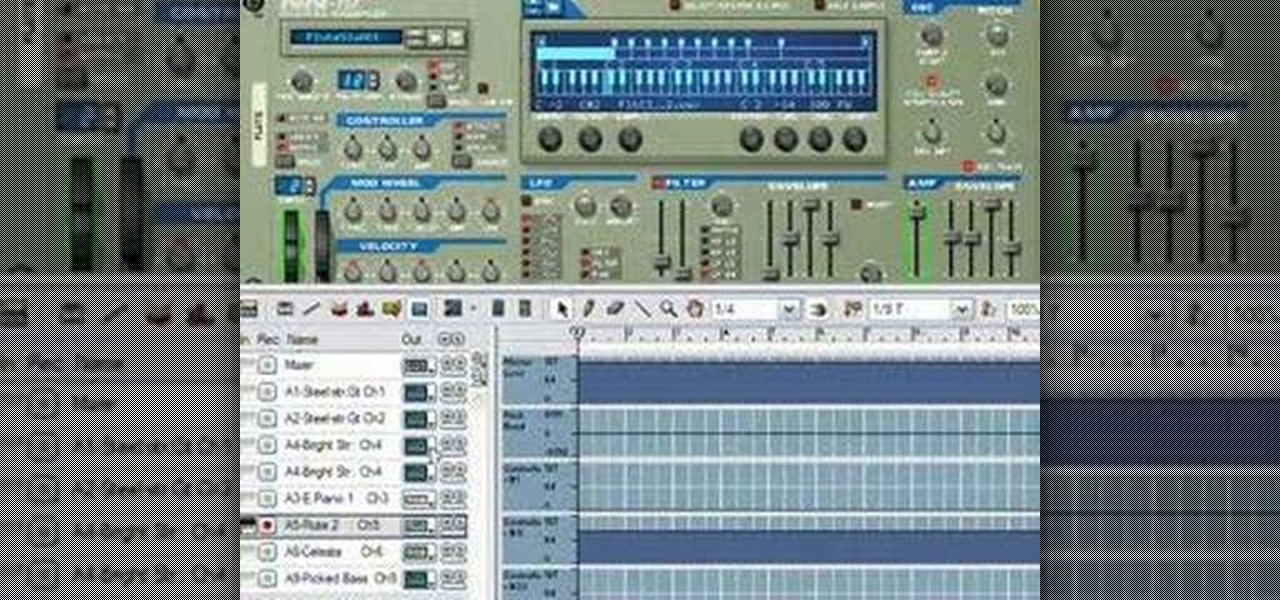
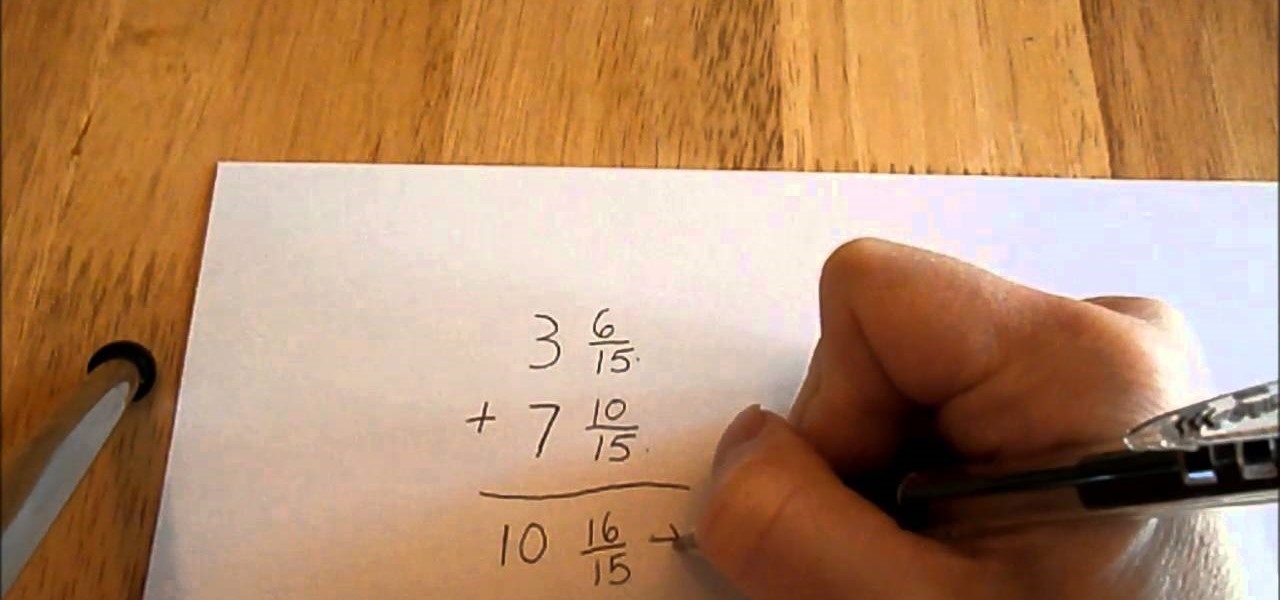The docking accessories available to owners of the Motorola Droid Bionic unlock several different functions dormant in the Android smartphones. The Vehicle Navigation Dock allows you to easily access Verizon's GPS system on the go, or give vocal commands so that you stay safe and handsfree with the Droid Bionic. The HD Station Dock allows you to connect your smartphone to a TV and view photos or use applications on the big screen. This guide by Motorola shows you how to access the different f...

After a convenient way to synchronize your files and folders on a Win 7 PC? With Copy Changed Files, it's easy! So easy, in fact, that this home-computing how-to from the folks at TekZilla can present a complete overview of the process in just over two minutes. For more information, including step-by-step instructions, take a look.

Need to eliminate those pesky leg hairs but want to bypass the credit card bill? Then read below for a homemade sugar wax recipe and watch the video to learn how to rip off your hair!

In this clip, learn how to root your Motorola Droid phone. By rooting your device, you will be able to access new files and apps as well as create your own ROMS and enable WiFi tethering. This process is super easy and should take no more than 5 minutes to do.
Backing up your files is very smart and important. You'll want to make sure that you copy your files somewhere external just in case something happens to your PC. The easiest and most convenient way to do this is to use a blank CD and burn your programs and files to it. In this video, learn exactly how to do this and keep your documents safe and sound.
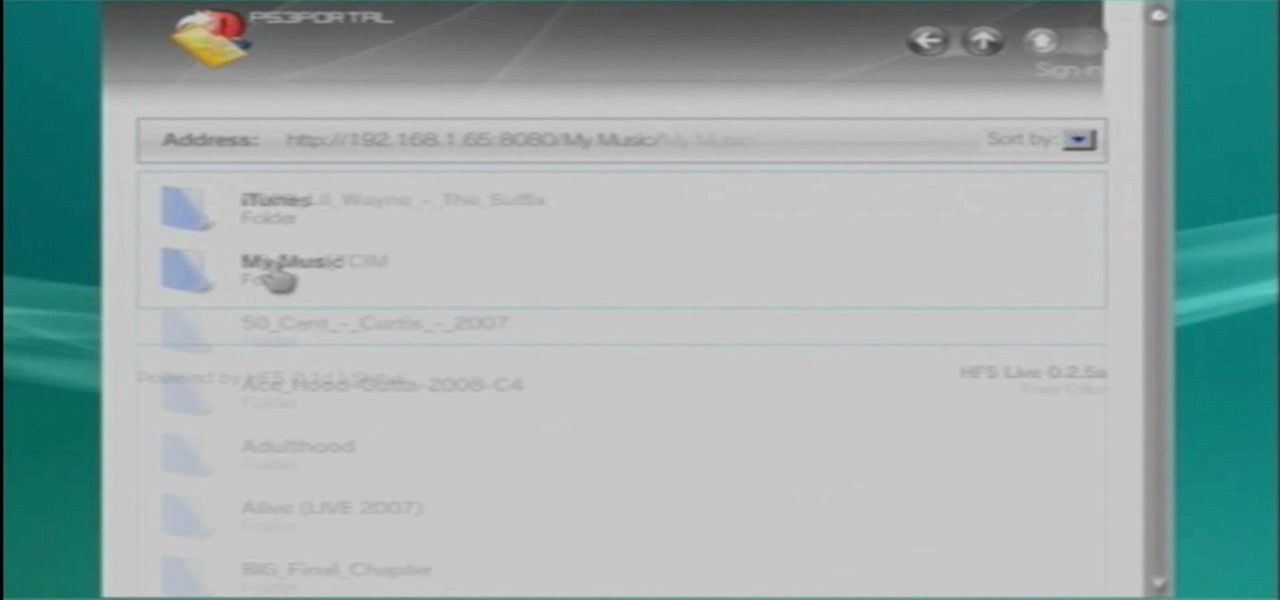
Most Playstation 3 models have massive hard drives, just begging to be filled with the media files from your computer. This video will show you a cool trick for transferring files from your PC to a PS3 over the web. All you need is the simple free program here. Why plug anything into anything else to send files when this is so much more elegant?

Mac or PC? PC or Mac? The debate rages on? Unfortunately, this can mean a lot of headaches for you when dealing with different file formats. If you work on both types, you might very well have to open the same file type on different computers. This can be a problem if you are using .rar files. But this video can help you. This tutorial will show you how a simple download can enable you to open .rar files on a Mac.

If you've ever had to work with documents written in other languages, you know how painstakingly difficult it can be if you're not a fluent speaker of the language. But now, with the help of Office 2008 for Mac, translating those documents is easy. You can know easily translate a PowerPoint presentation in almost any language to almost any language! And you can also translate Word documents, Excel spreadsheets, and even emails in Entourage! This translator is available right in the reference ...

1. First of all you need go to the 'view' button at the top bar menu. From the drop down click on 'view options'. Then click a 'check mark' against the 'kind' and then click 'ok'.

How to use Home Sharing in iTunes 9 to transfer music files to another computer. First make sure both computers have iTunes version 9 installed. To check this go to the iTunes 9 menu next to file in upper left and select the about item. On windows machines this will be in the help menu. In the computer with the music files we need to make sure the iTunes library is nicely organized. Again go to iTunes menu, this time open the preferences menu, and advanced icon. Check mark both sections "Keep...

ZurplusFaction shows viewers how to pick a lock easily using 2 paper clips. First, you need to take your first paper clip and fold one end out. Fold it out again and straighten this out. Next, take the folded out in and fold in again so it forms boomerang shape with the paper clip. Now, take your pliers and squeeze this folded part together tightly. With a bigger paperclip, and use wire cutters to cut of a straight piece of the paper clip with a curve at the top. Now, you are ready to pick yo...

In this web TV presentation the host is talking about Grub 2. In Grub 2 you can mount an ISO file like a device with the loop back function. In Grub 1 you can use tack tack mem to mount iso files if the files are not fragmented by using the map command. Grub 2 is an application available for download that will be available after download as a chain from Grub 1 to Grub 2 to your operating system. Grub is a program that compresses all of your favorite boot programs into one.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episodes from this Revision3 show.

Hack Mafia Wars. Mafia Wars hacks, glitches, cheats. Mafia Wars is a popular facebook app / game. Watch this video tutorial to learn how to easily manage your Mafia Wars player updates.

This Reason 3.0 tutorial explains use of the Import Midi function and some of ways to use it for practice or remixing a popular song. Also, get tips on spicing up flat MIDI files while learning MIDI remixing and EQing in Reason 3.0

Learn how to automate tasks in Windows using batch files. Learn basic commands that can be used in batch files and how to use commands from other programs to create batch files.

The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to root another.

In the last decade, the number of people working remotely in the US has increased dramatically, and so has their need for technology and software to supplement that remote work. Whether you work from home or a coworking office space, the requirement for highly compatible and helpful productivity apps is a must if you want to get things done successfully.

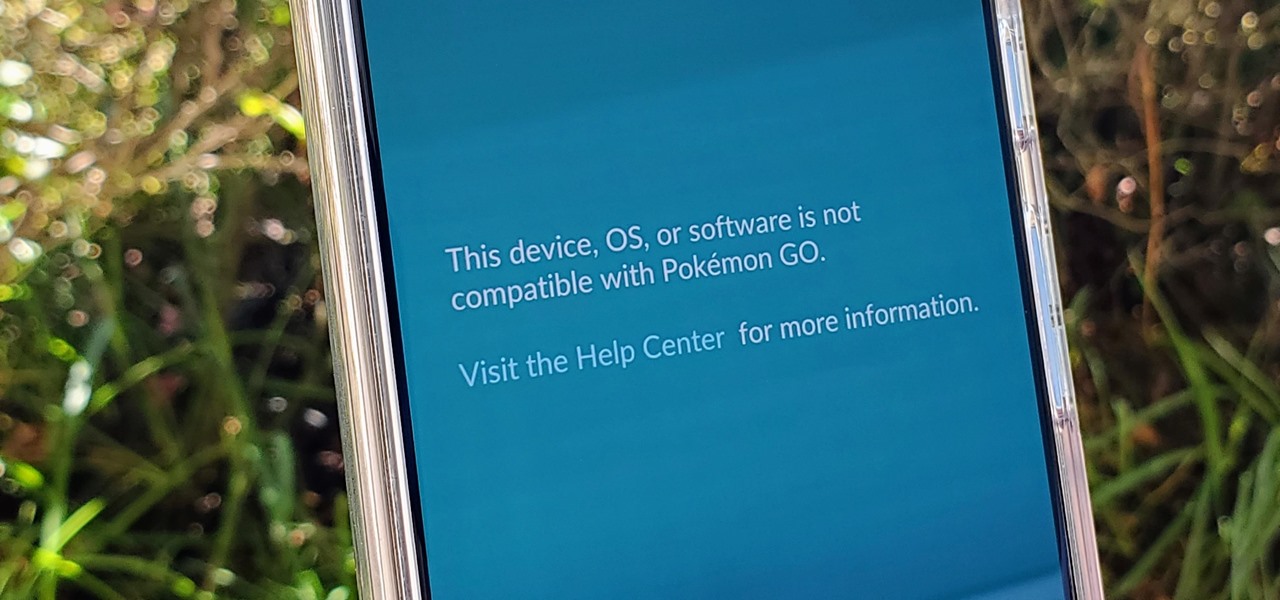
If you're a root user who has played Pokémon GO over the years, then you're probably familiar with the detection methods used to spoil your fun. The game's developer, Niantic, has publicly mentioned their ongoing battle with rooted Android phones and are unwilling to let up. They have a no-nonsense approach to try and keep you from playing, and they've stepped their game up once again.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

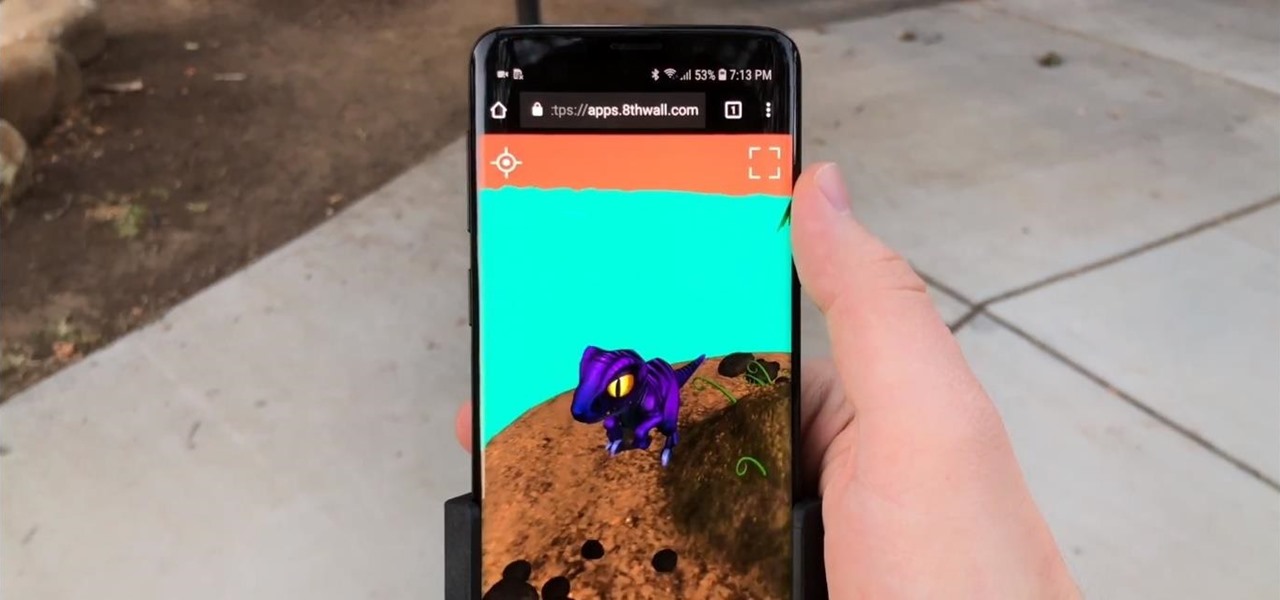
In the past few years, augmented reality software maker 8th Wall has worked to build its platform into a cross-platform augmented reality toolkit for mobile apps, as well as web-based AR experiences.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

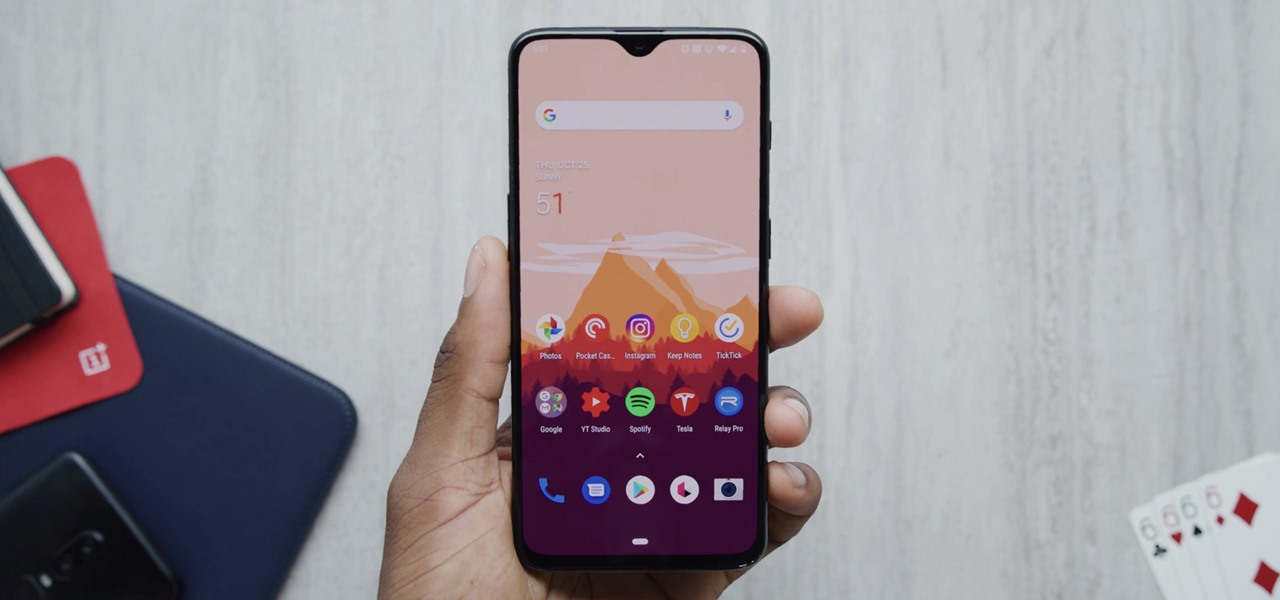
With the same starting price as its predecessor and a nice list of improvements, the OnePlus 6T is a great buy for a number of reasons. But for many Android users, the main selling point for the latest OnePlus flagship is how easy it will be to root and mod the device.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

Using Hydra, Ncrack, and other brute-forcing tools to crack passwords for the first time can be frustrating and confusing. To ease into the process, let's discuss automating and optimizing brute-force attacks for potentially vulnerable services such as SMTP, SSH, IMAP, and FTP discovered by Nmap, a popular network scanning utility.

Apple first added a "Drag and Drop" feature to iPads in iOS 11, but your iPhone can do a little of the magic, too. It's just not so obvious. While you can't drag and drop items from one app to another like you can on an iPad using Split View and Slide Over, you can move things around in certain stock applications. And it works the same whether you're using iOS 11, 12, or 13.

Keystroke injection attacks are popular because they exploit the trust computers have in human interface devices (HIDs). One of the most popular and easily accessible keystroke injection tools is the USB Rubber Ducky from Hack5, which has a huge range of uses beyond simple HID attacks. The USB Rubber Ducky can be used to attack any unlocked computer in seconds or to automate processes and save time.

SSH local forwarding is a must for covering your tracks and getting out there to do your work. Also called SSH tunneling, this process will put one or more steps between your machine and the machine you're working on, for security and other purposes. It can be a bit daunting for newbies to get down, and that's where Punchabunch comes in.

Seems like everyone in the world loves ice cream so therefore you can easily set a few pranks and booby traps on those friends and family members of yours that love eating ice cream.

In this cardmaking project I make a gorgeous and very elegant card using the DCWV Jet Black stack. I create a large card with embellishments all made fro m the stack with a touch of gold card to give it a touch of luxury.

This step by step video teaches how to add mixed numbers AKA mixed fractions easily!

Learn how to easily gap a spark plug for a car,truck,ATV, motorcycle, lawnmower or pretty much any vehicle. This tutorial will show you hoe easy it is to do.

I have used the DCWV Ocean Breeze stack to make this gorgeous card.I have used a couple of the card sheets from the stack and the borders as well as one of the sentiments.

The following are 5 simple household pranks you can set up on friends and family this upcoming april fools's day! Watch the video tutorial for further details and demos!

Yes, I understand some people may consider this a repost. However, I have been searching for this answer for 3 weeks and after reading numerous reddit post, Kali Forums post and Null byte post I finally have gotten it to work for me. I would like to compile and share this information with you guys.

Learn how you can easily prep a pumpkin using fake blood and a few plastic bugs to scare the living hell out out someone before they start carving their Jack-o'-lantern for Halloween!

Like the majestic mountain structure it's named after, Apple's latest version of OS X, El Capitan, goes a little deeper to expand on the foundation laid by Yosemite. While the update may not be as monumental as some have hoped, it is an improvement and includes tons of useful new features you don't want to miss.

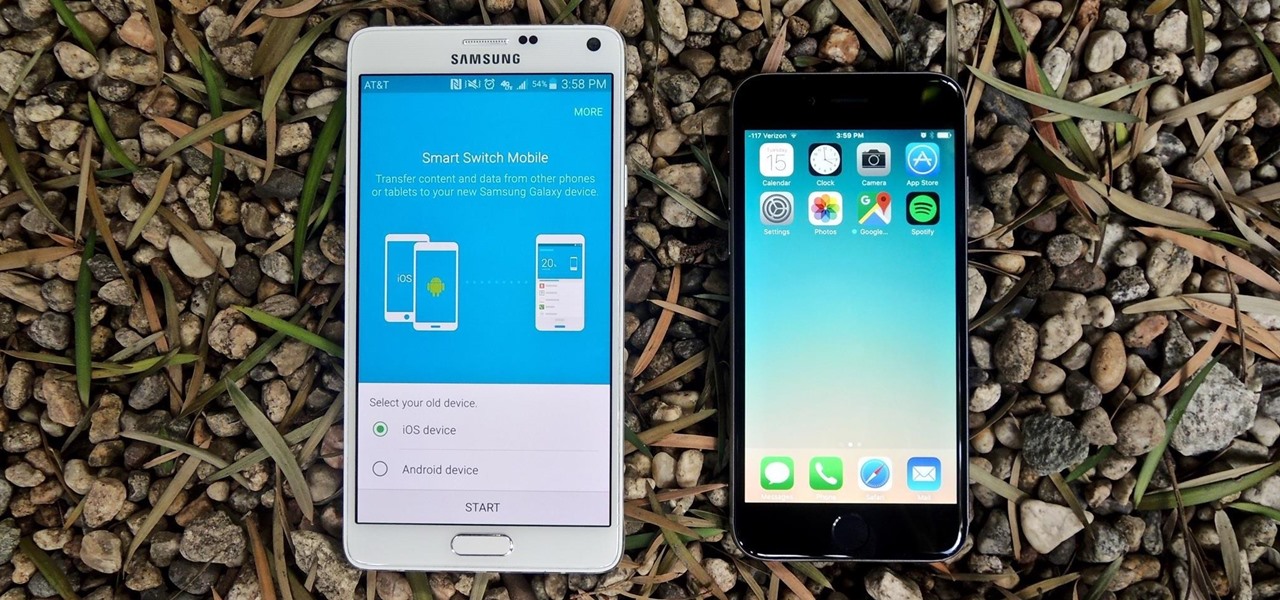
Thanks to Smart Switch, it's easier than ever now to ditch your iPhone for a brand new Samsung device, like the Galaxy S6 Edge+ or Galaxy Note 5.