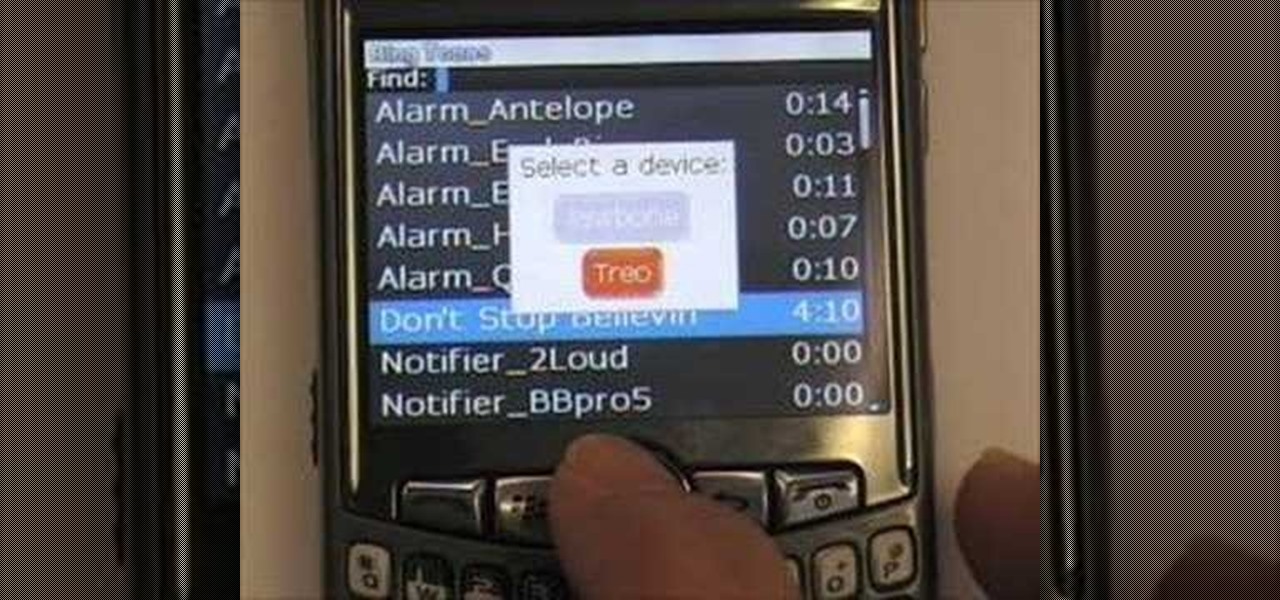
Can't make it to a computer to open up some important documents? Fortunately, the BlackBerry is basically a mini-computer that can get those open for you. BlackBerry can be a little tricky while trying to send and receive files through Bluetooth, but with the right help, you can get the hang of it. This video cell phone tutorial shows how to do it step by step.

If you have your own domain, odds are you do things from FTP from time to time. In this tutorial, you'll learn a technique for making FTP shortcuts with the Windows HOSTS file, which will allow you to simplify the process. The time you save will be your own.
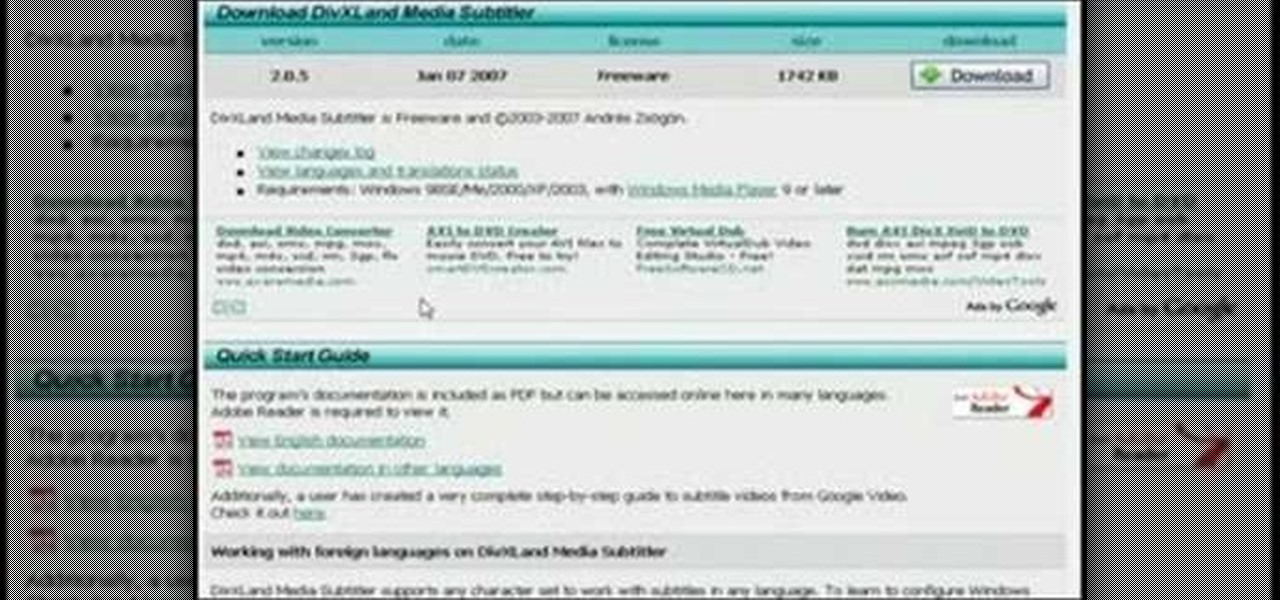
This video will show you how to embed subtitles into video files using the free softwares VirtualDub and dvXLand. Embedding subtitles with VirtualDub and dvxland allows you to add subtitles to your videos without having to keep two separate files.
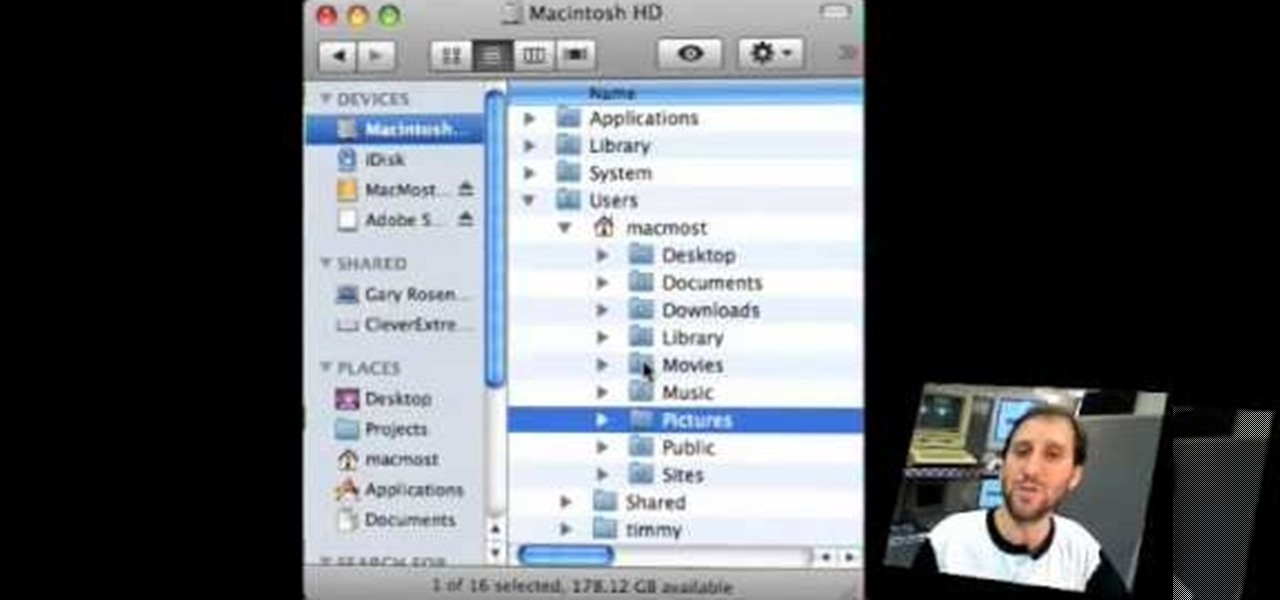
Suffering from a cluttered desktop? In this tutorial, Gary Rosenzweig takes a look at the basic structure of Mac OS X, especially the user folder, and gives suggestions on how to organize your files. Take a look!
MP3 provides great quality compression for about a 10th the file size of uncompressed audio. And most people can’t hear the difference between the MP3 and uncompressed audio. Any computer or portable player can play an MP3 file, so it’s a universal file format that makes it perfect for podcasting.
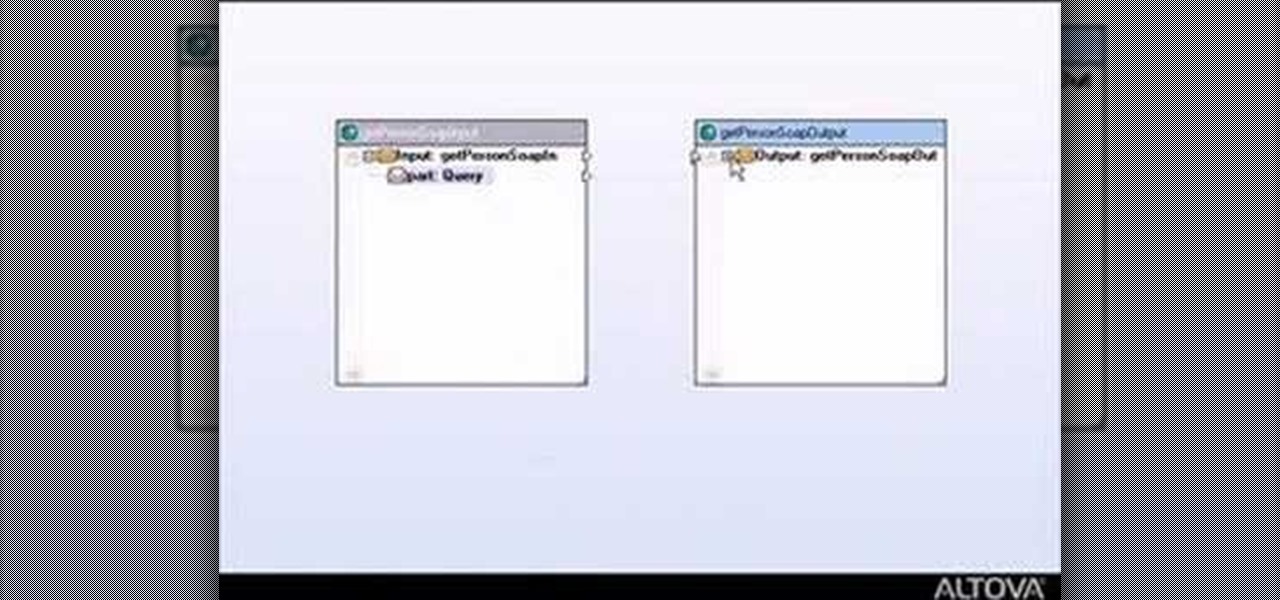
This tutorial shows you how to build web services with MapForce. Load an existing WSDL file and build a complete web service by retrieving data from databases or XML files and using a visual function builder. It's easy to build web services in MapForce as this tutorial shows.

In this instructional video, learn how to transfer files from your Windows PC to your iPhone or iPod Touch using DataCase. Datacase basically converts your iPhone or iPod Touch into a wireless drive that you can access your information on the Mac, PC, or Linux.

Check out this tutorial and learn how to encrypt Microsoft Office files to help prevent unauthorized people from opening a workbook, document, or presentation. Watch the video to see how easy it is to set a password to help you control who can open or modify the Office files you create.

This is an older method but it's still a viable method for a quick and easy master. Get your wav file ready for CD with this FL Studio quick master tutorial.

You never know when your computer could eat up all of your work, but you can backup your important files on the music player you already own!

Learn how to cut Camtasia Flash file sizes in half with this tutorial from Bill Myers. Save space on your hard drive and make it easier to load higher quality videos on your site or any website.

Do you want to use Apple iPhone's Video Recorder for free, without paying to release the filming length restriction? Well, check out his video tutorial to see how to hack the iPhone Video Recorder version 1.2.4 for non-stop movie recording.

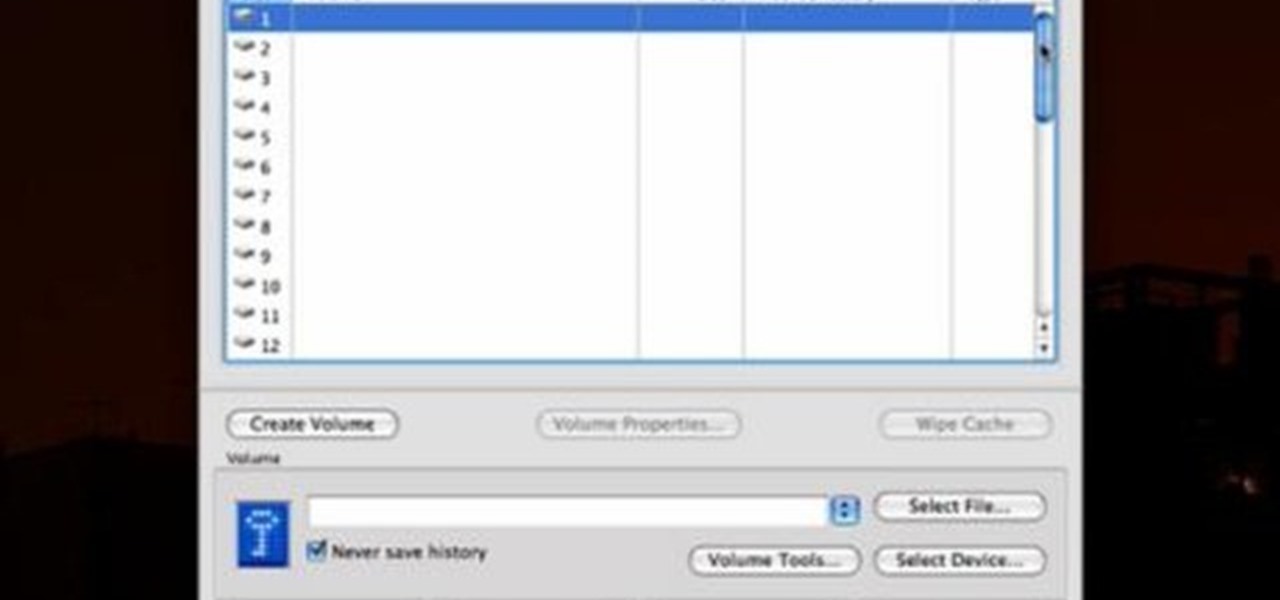
Check out this video tutorial to see how to keep your private files private, even if you have to email them to yourself at your office? TrueCrypt, an open source piece of software, lets you encrypt your files so they remain accessible only to you. This works on any platform; Windows, Linux, or Mac. So, watch this video to see the TrueCrypt download process, how to install it, and how to create an encrypted volume on your hard drive.

This actually works and you don't need wifi or you don't have to put a source in your iPhone/iPod Touch that doesn't work. You get 960 NES ROMs. As long as you follow directions you it should work perfectly. I will also have a tutorial up soon on how to use the program i mentioned in the video called Limewire on how to download various things. And i should will have a tutorial on how to get SNES working on iPhone/iTouch very soon. Warning: Limewire can give you a virus, so be careful when dow...

Overcome hardware differences in just a few simple steps- share files between your mac and PC and make your network truly seamless.

This tutorial shows you how to write text to a text file using C#.

Being organized and using good formatting in your CSS files can save you lots of time and frustration during your development process and especially during troubleshooting. The multi-line format makes it easy to browse attributes but makes your file vertically very long. The single-line format keeps your file vertically short which is nice for browsing selectors, but it's harder to browse attributes. You can also choose how you want to group your CSS website statements. Do you do it by sectio...

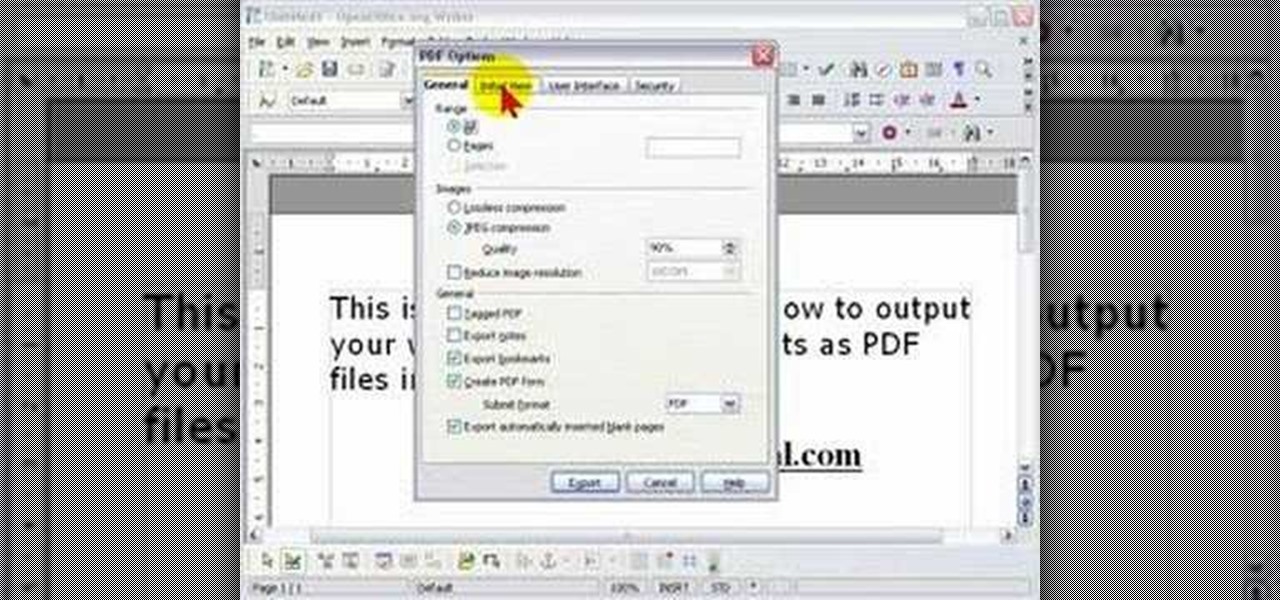
In order to protect your word processed documents, it is a good idea to export them for distribution as PDF files, which allows you to encrypt, and add password protection to your work.

John Hendron demonstrates keyboard shortcuts and the "Sidebar" in Mac OS X Tiger with tips on keeping files organized. This 7.5 minute video includes how to "tell where you are" in the file system, how to set desktop preferences, and how to customize the toolbar in Finder windows. John is an instructional technologist for Goochland County Public Schools (VA).

Gary Rosenzweig looks at various methods for printing lists of files in folders in Mac OS Leopard: downloadable applications, using the Terminal, and simple copy and paste methods.

Gary Rosenzweig from MacMost looks at one method to protect a set of files with a password on a Mac. It involves using Disk Utility to create an encrypted disk image.

Learn how to create PDF and XPS files directly from Microsoft's Office 2007.

This tutorial will show you ways to read, edit, and create PDF files without spending any money. It requires 3 different pieces of software:

A how-to on how to share files and folders from Ubuntu to Windows XP and XP to Ubuntu.

DNS spoofing - how to use the hosts file in Windows XP to block unwanted spyware/popups/etc, block programs from reporting to a site, filter/block/redirect websites, and locally create forward lookups (IP to name resolution in network)

This tutorial covers gathering up all of your data. In AE: Collect Files. You can do the same in CINEMA 4D. If you're not familiar with collecting files in After Effects, the video hits the rough outline.

The introduction of transparency has been quite controversial in print production over the past few years, though the fact is that for most transparency in Adobe files works just fine. However, those of us out there with older RIPs may have issues printing transparency. In this video you'll see how to flatten transparency in your PDF files before you ever hit the Print command.

Many Photoshop users have no idea ImageReady is there or let alone what it's used for. In this video we will take a look at how to create web rollovers from a Photoshop file. ImageReady is a web optimization tool as well as a good tool for creating animations from your layered Photoshop files.

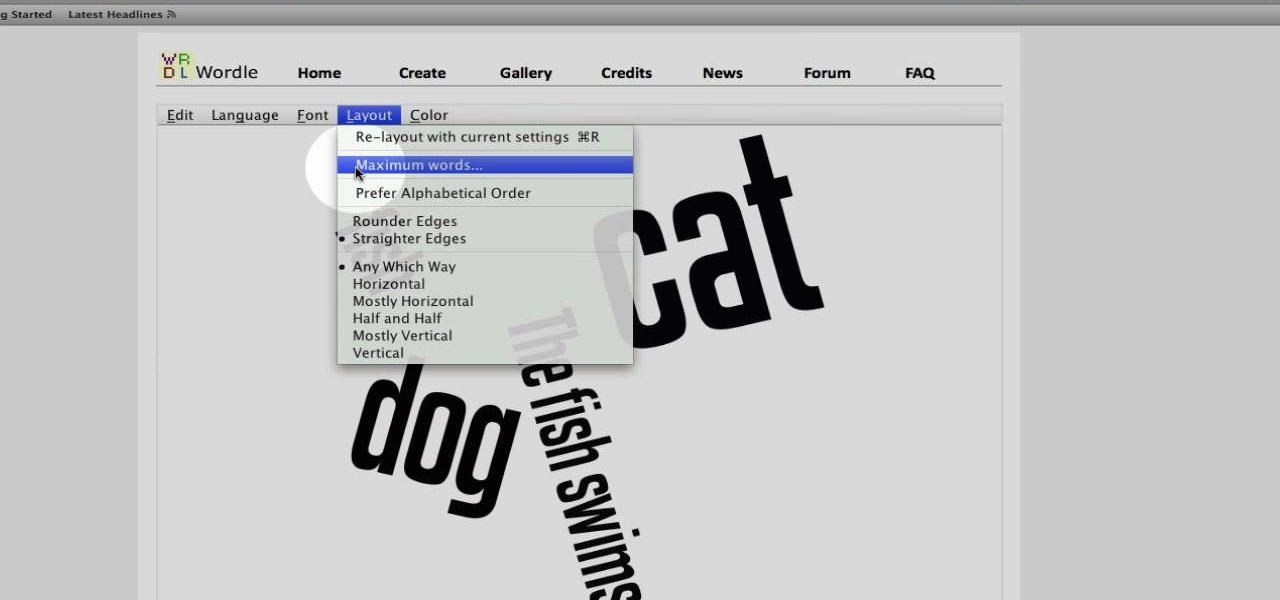
This video tutorial belongs to the Computers & Programming category which is going to show you how to use Wordle to create word clouds. Go to Wordle and click on the 'create your own' link. In the first box, type in your text, and in the second box enter the URL of any blog, blog feed or any other web page that has an Atom or RSS feed. In the 3rd box enter your del.icio.us username, if you have one. After typing in, hit 'go' and you get your Wordle file with the words written in different sty...

This how-to video is about how to use the Ribbon and Backstage view in Microsoft Office Excel 2010.

It's easy to find yourself drowning in a pile of papers and nick-nacks if you're not armed with a good organization system. By taking the time to set up a system where everything is condensed and has a place you'll find it much easier to keep it that way.

Losing your important data can be more painful than losing the hardware the data was stored on. Precious memories, files you don't often access but always want to have, there's so much you store on impermanent devices that you can't live without. Backing up your information to a secure, cloud-based location is the best way to stave off disaster here. Polar Backup Unlimited Cloud Backup Storage will give you an unlimited amount of cloud storage while making the process super easy.

The memories on your devices are precious, even if you don't often get a chance to revisit them. The worst thing in the world is when something happens to your computer or phone, and you end up losing some of those memories because your files weren't backed up or your microSD wasn't fireproof.

If you need to share something online but don't want your personal information attached to the file, use an anonymous file hosting site. By uploading files anonymously, you keep your IP address safe and won't need to create any kind of account that could provide further logging. You can do this in a web browser, but it's much easier to do using a shortcut on your iPhone.

Everybody knows not to store sensitive information in unencrypted files, right? PDFs and ZIP files can often contain a treasure trove of information, such as network diagrams, IP addresses, and login credentials. Sometimes, even certain files that are encrypted aren't safe from attackers. That's where Zydra comes in — a tool for cracking RAR files, ZIP files, PDF files, and Linux shadow files.

The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to root another.

If you have an Android device that Netflix does not support, you can check the Play Store and it simply won't be there. But just because you're unable to download it through official means doesn't mean you have to live without Netflix since there's a way you can sideload it manually.

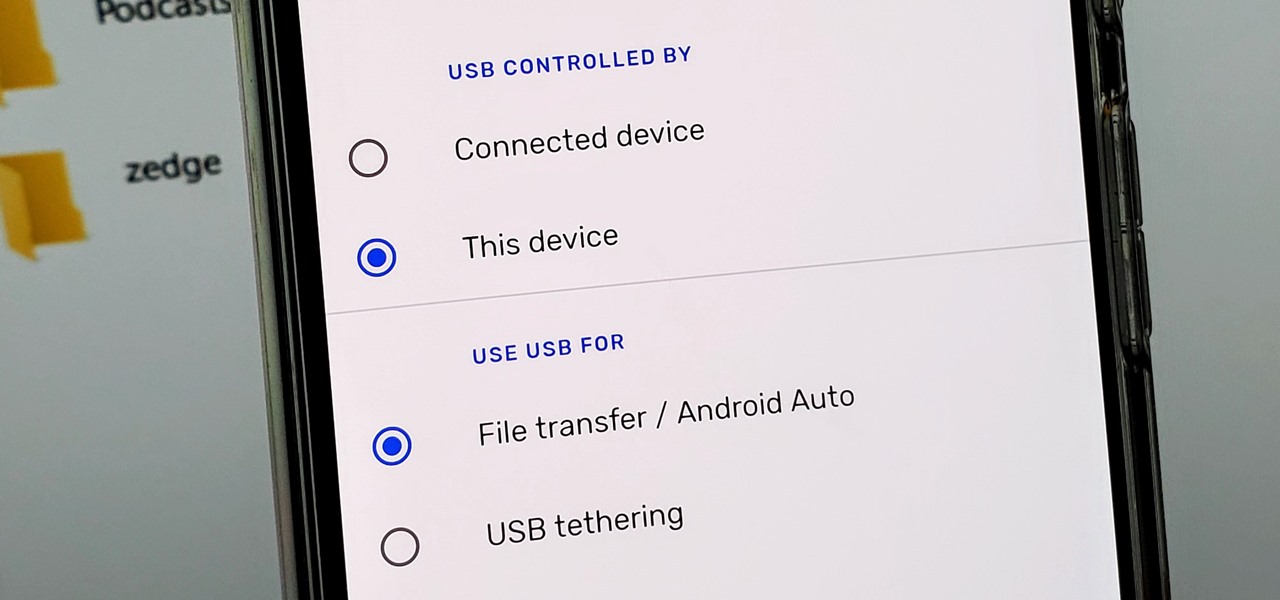
Back in the earlier days of Android, you were able to connect your phone to a computer, and it would mount automatically. This meant once the USB connection was made, your internal storage would pop up on the computer and you could go about your business. But recent versions of Android changed that to help increase security.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.