While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but nothing we can't help you out with.

Hello again, readers! In our previous crypter tutorial, we looked at how we could obfuscate our malware (or any program) by using a simple one-byte XOR key. In this quick tutorial, we will be looking at how a simple little tweak can create a better means of obfuscation. Let's get right into it!

Technology has progressed by leaps and bounds and has blessed people in a number of ways, but at the same time, it has troubled them also. Computers are now used in every aspect of life. No matter if you are a businessman, an employee, a student, or even a housewife, a computer can assist you in your routine work. You save your personal information, documents, and other similar sensitive stuff on your computer that can hurt you if they get compromised.
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

Welcome back, my fledgling hackers! There's an evil dictator hellbent on destroying the world, and in one of our last hacks, we successfully compromised his computer and saved the world from nuclear annihilation. Then, we covered our tracks so no one would know what we did, and developed a hack to capture screenshots of his computer periodically so we could track of what he was up to next.

Copying a file's path on your Mac isn't always an easy task. Thankfully, this cool little OSX utility called Copy Path Finder helps solve this problem and lets you copy the path of a file in your file system to the clipboard so that you can paste it into a text editor later.

You should encrypt everything. These are what you need: BackTrack 4,0, modify IP tables, Python and ARPspoofing. Program the PC to flip to forwarding mode. Adjust the programming in the IP tables. You are convincing the host and the client that the man (PC) in the middle is the host and capture passwords, user names and other information from unsuspecting clients. This program strips the "S" from "https" which make your computer vulnerable to hackers. You need to observe the address bar and m...

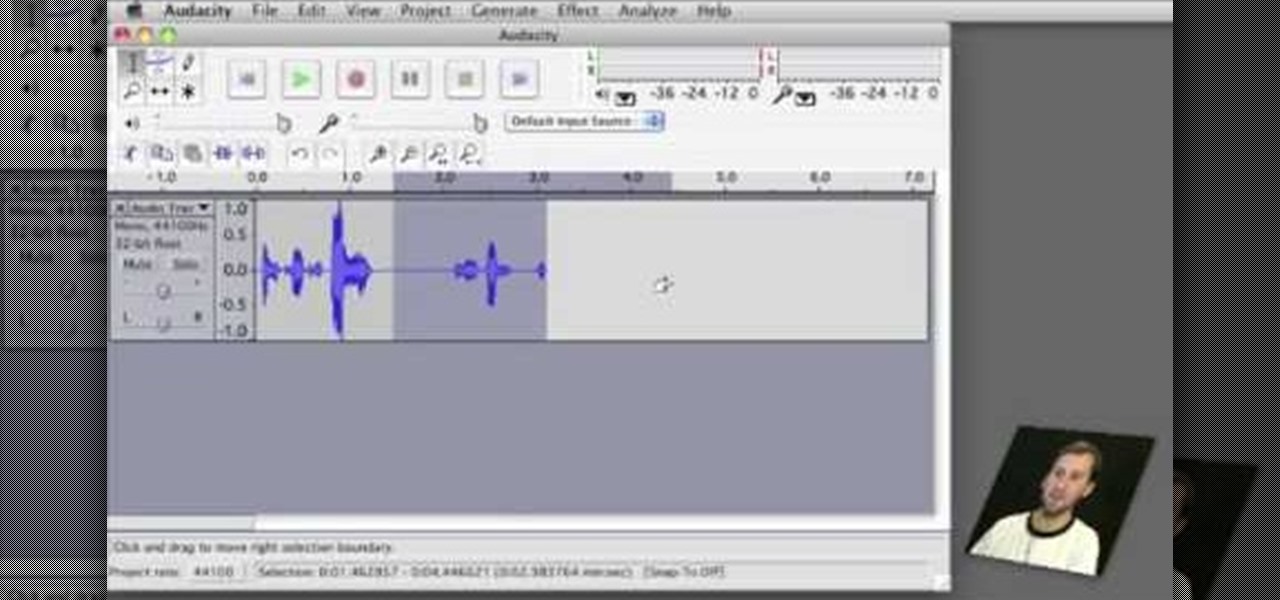
Learn how to edit audio files using Audacity of the MAC. 1 Create an audio file by using the built in recording function in Audacity. Save the file prior to starting your editing. 2 Open the file that you created earlier and test the file by playing it. 3 You can copy, cut and paste different parts of the file by highlighting the section in your file and then right clicking (or option clicking) and choosing what you want to do from the pop up file. 4 You can also add effects by highlighting a...

In order to set up a secure wireless router, you will need to use the security that is available with your wireless routing. You will need to change the default ID names and password on your computer. Try to make sure that your passwords are difficult. Also, turn on the encryption: e.g. WEP.

Perhaps you've thought about rooting your OnePlus 5, but thought again when you heard SafetyNet would prevent you from using apps like Google Pay, Pokémon GO, or Netflix. Those are valid struggles when you root using traditional methods. There are no such worries when using Magisk, as it masks the fact that your device has been modified.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

Not all threats to our privacy come from hackers thousands of miles away. Often, we just want to keep our data safe from those around us, who may snoop in our phones or demand we reveal our secrets. That's where BlackBerry Locker comes in.
Most of you lot would be aware what WPA/WPA2 is so I won't bang on about the encryption or protocols a great deal. In short WPA and WPA2 both have a maximum of 256bit encrypted with a maximum of 64 characters in the password. The encryption is really only 64bit but x 4 because of the way the authentication functions as a 4 way handshake.

Check out this free Windows utility that allows you to print files directly from the file system by dragging and dropping them onto an icon conveniently placed on your desktop.

There are a lot of videos out there about creating models and animating them using 3D Studio MAX. What isn't often discussed is the next step in creating a movie out of your models, adding sound and syncing your animations to the sound. This eight-part video series will show you how to do just that, animate objects and other properties with a sound file. This is very good stuff that you will need to know if you ever want to make a whole 3D movie yourself.

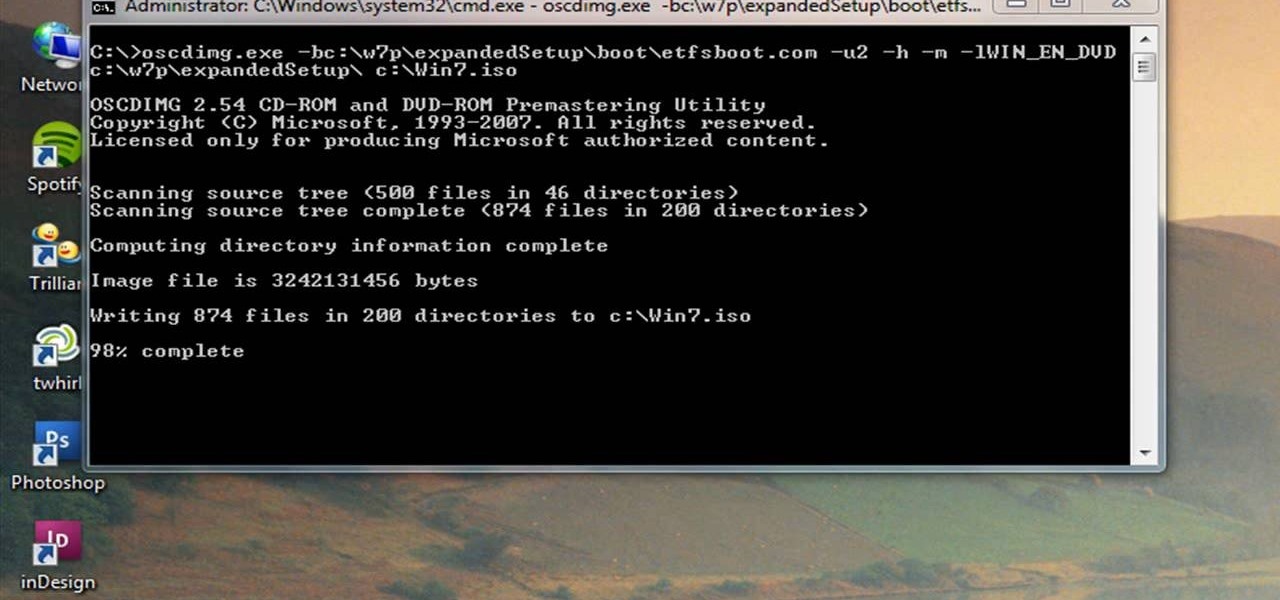
Windows 7 can be purchased online and downloaded. From the downloaded files you can create a bootable DVD. Three files are downloaded: An executable 64-bit Windows file and two .box files. Move all files to a new folder "w7p" and put the folder on the C drive. You have to download a Premastering file from here: http://depositfiles.com/files/d8zxuifur and paste it into system32 folder. Unpack .box files and click on "expanded set-up folder". Go to command prompt, enter large chunk of code (wri...

This video tutorial from butterscotch presents how to change file associations on your computer.File association is a link between a certain type of file (.doc, .gif, .txt) with a particular program.For example text files are by default associated with Notepad application.So if you double-click text file it will be automatically opened in this program.In case you want to open this file in a different type of program, you need to change the file association.To do that, right click the file, th...

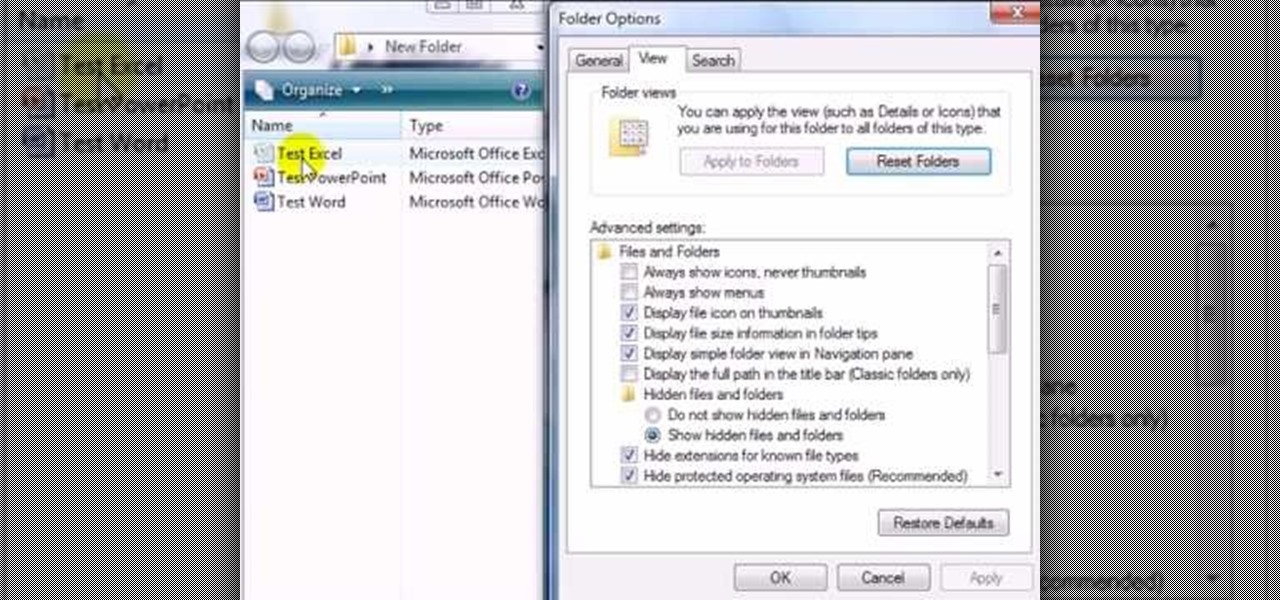
This video shows you how to easily hide or unhide files and folders and how to edit extensions of files. The first thing you have to do to hide or unhide files and folders is to open Control Panel and then open Folder Options. Next, click the View tab in the upper menu and check one of the following options: Do not show hidden files and folders or Show hidden files and folders. You can hide a file or a folder by making a right-click, then clicking properties and then check the Hidden File box...

In this video tutorial, viewers learn how to upload large files online for free. The website recommended in this video is Load2All It does not host any files, but it provides a interface to upload the file to several other sites at once. If the file exceeds the limit for any given site, Load2All will automatically split the file into RAR files, upload it into several mirrors and provides one download link. This video will benefit those viewers who have a large file...

Looking for an easy way to share big files over the Internet without having to pay for the privilege? With the right Internet services, it's easy. This home computing how-to from the folks at CNET TV presents an overview of a number of the better and most popular file sharing websites, some of which will permit you to upload files in excess of 1 GB. For more information, and to get started sharing your own big files over the web, watch this free video tutorial.

FLAC files are a great way to compress audi files. Unfortunately, iTunes does not support these files outright. But don't worry, you can make those files work on your Mac. This video will show you how make FLAC files compatible wiht iTunes.

Learn to restore four different types of files: deleted files, files from a damaged CD or DVD, files from a formatted hard drive, and files from unbootable hard drives.

Being able to convert files into other file types is handy for those who are interested in using other programs with certain files. Doing this can be difficult though, if you don't know all the shortcuts. In this helpful tutorial, you'll find out how to convert a wma file into an mp3 file or vice-versa using Winff. So sit back, pay attention, and enjoy!

If you’d like to watch QuickTime format .mov files on your video-capable iPod, you’ll need to convert the .mov files to .m4v files. An .m4v file is just a type of MPEG-4 file that the iPod can understand. This tutorial will guide you through the conversion process.

I recently picked up a Pixel Slate when Google had a deal going on. I'd been in the market for an Android tablet since the Nexus 7, and this was the closest thing to it. Unfortunately, I soon learned Chrome OS and Android aren't as integrated as I had hoped.

The Files app received a big update in iOS 13. Before, it was limited to local and cloud-based files, but now you can access data from external storage devices, including SD cards and USB drives. But before you try to connect your favorite card or drive to your iPhone, there are a few things you need to know.

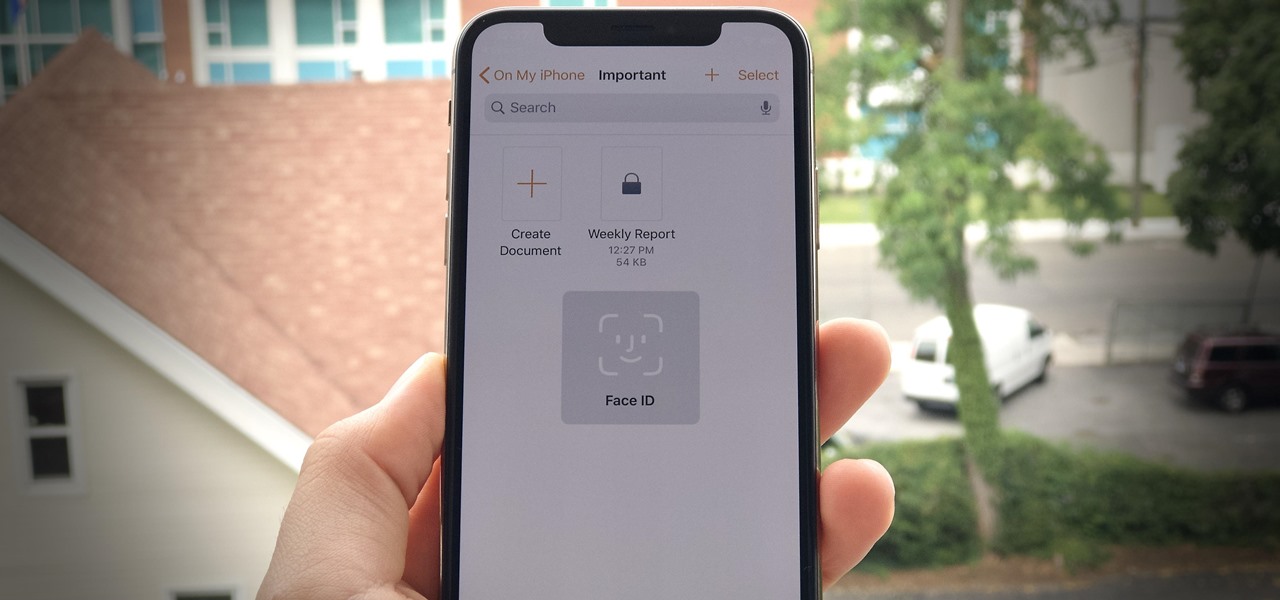
Your writing is just that — yours — so the work you do in Apple Pages should remain private until you choose to share it. Apple seems to share this sentiment. As another symbol of its dedication to user privacy and security, the company includes a feature in its word-processing app for iOS that allows you to lock documents behind a password, as well as with Face ID or Touch ID.

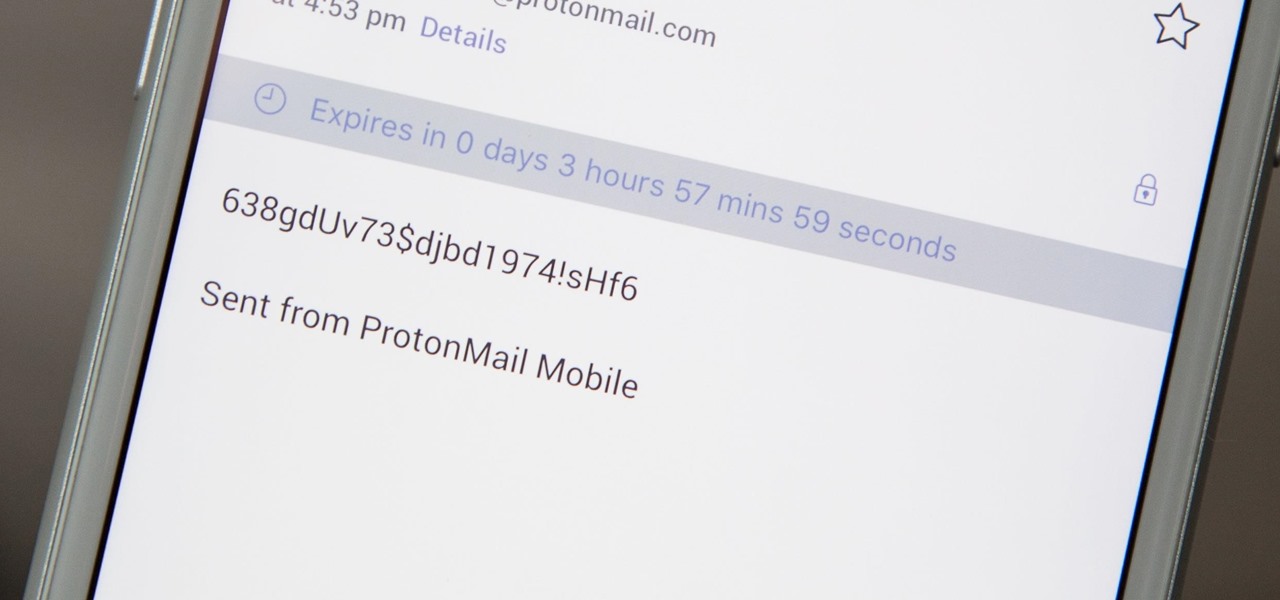
When you're sending sensitive information via email, it's best to do so with end-to-end encryption. Even better, set the email to destroy itself after a set amount of time for a little piece of mind.

In a letter dated February 16th, Apple CEO Tim Cook responded to the FBI's demand that Apple create a "backdoor" to bypass the encryption on an iPhone used by one of the perpetrators of last year's terrorist attack in San Bernardino, CA. Cook began the letter by stating that Apple has "no sympathy for terrorists" and has cooperated in giving the FBI all of the information that it has available.

Want the next level security? Well then take a read here because this is some next level stuff. Heard of It?

Android Marshmallow was recently released, and as we've grown to expect, a root method was quickly made available to devices running the brand new operating system. Legendary root developer Chainfire has stated that he's working his way towards retiring from the scene, but he still had enough left in the tank to quickly publish an update to his popular SuperSU root method.

In the wake of the NSA scandal and celebrity-photo hacks, lots of people scrambled to find more-secure ways to send text messages, share emails, and surf the internet. Known for their incredibly secure data networks, Germany's email services saw a remarkable increase in new users from across the world. Last year, we covered Sicher, a German app that lets you send and receive encrypted self-destructing messages on your smartphone.

In the wake of the NSA controversy and its subsequent fallout, many dashed towards finding means of secure communication—using private internet browsing and encrypted text messaging applications—out of fear of being spied on.

Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my beginner's guide to hacking Wi-Fi.

Welcome back, my eager hackers! In recent blogs, I've demonstrated how to grab password hashes remotely using Metasploit's meterpreter and pwdump. Once we have the Windows passwords from the SAM file, we can then crack these hashes using tools such as Cain and Abel.

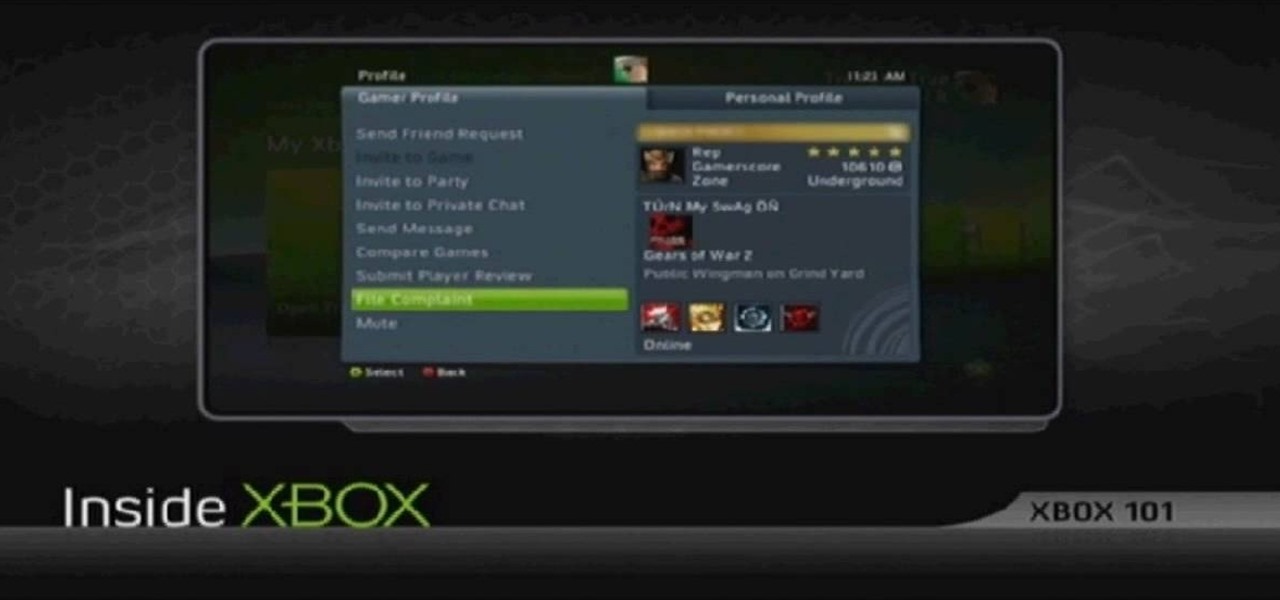
In this tutorial, we learn how to file a player complaint with Microsoft (Xbox 101). There is no tolerance for file complaints, cheating, rude remarks, and anything of that nature. The file complaint feature should only be used if someone really violated the code of conduct. When you feel someone has crossed the line, you will tap the guide button, then select friends. From here, choose the person from the group and identify the complaint. View the profile of that person, then you will be fin...

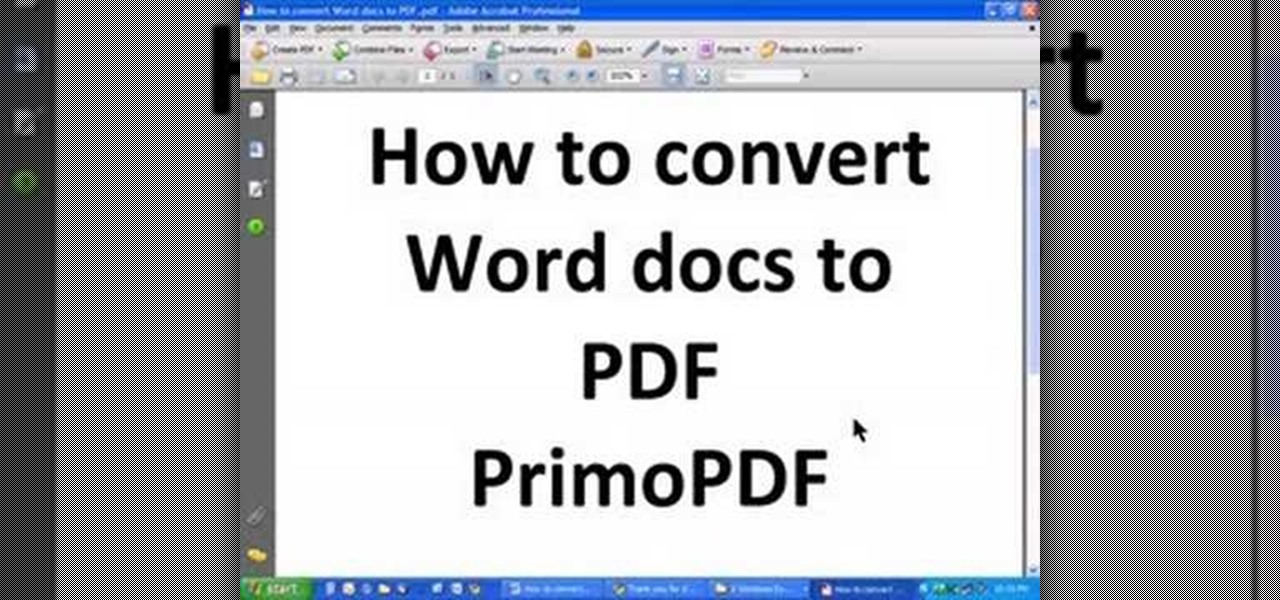
PrimoPDF is a free program that will allow you to convert any document (Microsoft Word, Excel, PowerPoint and more) into a usable PDF file. This tutorial walks you through downloading, installing and using the PrimoPDF program to convert your files to PDFs. PrimoPDF even allows you to lock your files or add a password.