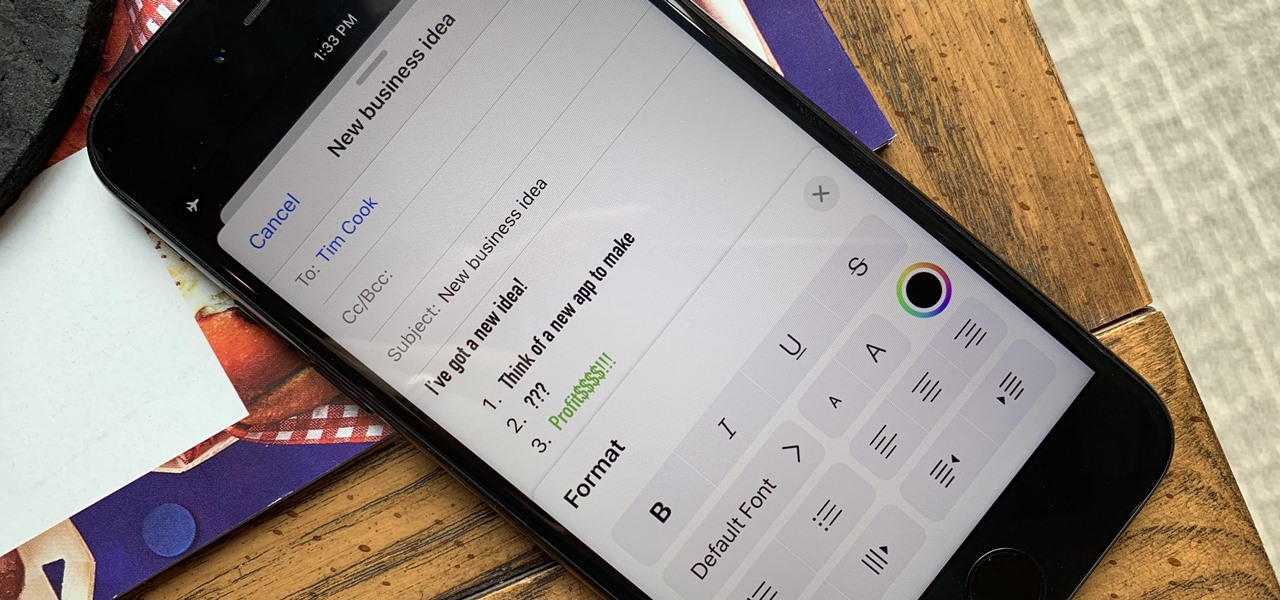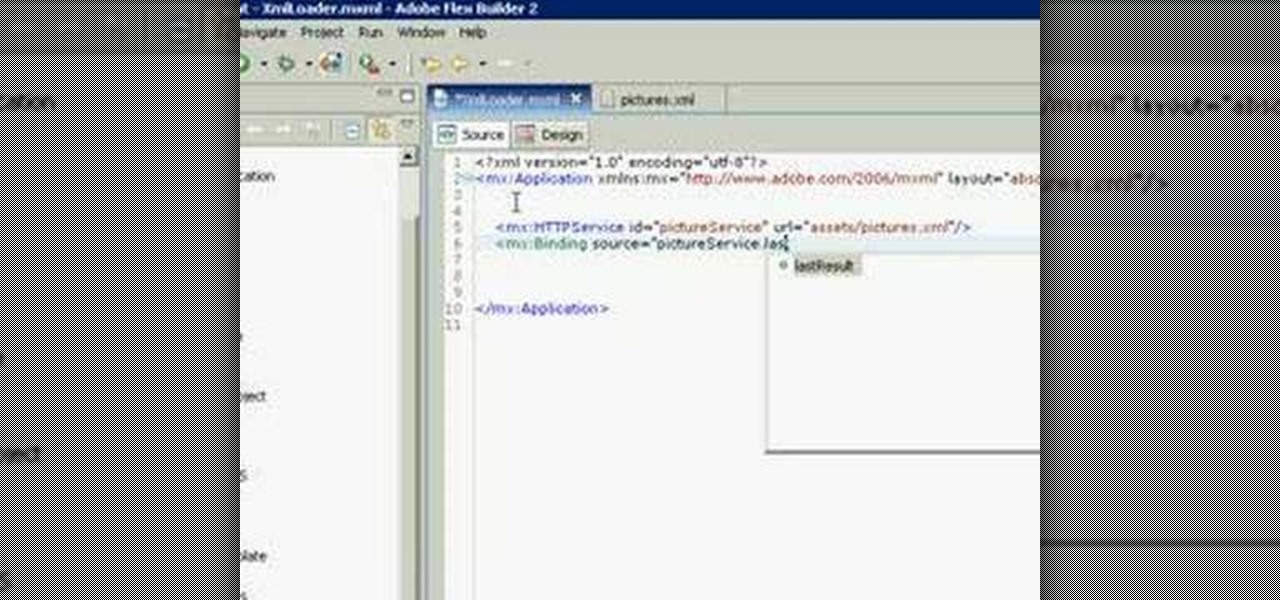
This XML video tutorial will show you how to bind an XML file in MXML in about ten lines. First you'll want to create a Flex project in Adobe Macromedia Flex Builder 2, then create an assets folder and a new XML file in MXML. Coding doesn't get any easier than this. Just watch and learn.

This video tutorial shows how to download .cut files onto Cricut software to design cards. Learn how to use this card making software, and get instructions for how to make a strawberry greeting card.
Learn how to get started in Photoshop Elements by importing digital photo files from your files and folders or off of CDs.
There's an easy way to get huge files with very little degradation to the file by using a little known secret in photoshop. Check it out in this video.

This walks you through how to create an animated GIF image file that can be used in websites, as avatar's, as icons, etc. You'll be using Microsoft Paint to create each frame of the animation, and an application called Unfreez (found here) to animate them together.

This is a tutorial on how to edit type in a layered file and a flattened file in Photoshop.

In this video, you'll discover how to upload files to your own website or blog using FTP.

In this video tutorial we will take a look at how to import files into DVD Studio Pro. Do note that it is recommended to render your movies into a compatible format before importing to DVD Studio Pro. The author suggests to use Compressor to do the job.

Gmail uses TLS, or Transport Layer Security, by default for all email communications, so all of your emails will use the standard encryption as long as the recipients also support TLS. But there's a way to add even more security to your Gmail emails, and you can use your iPhone's Mail app to do it.

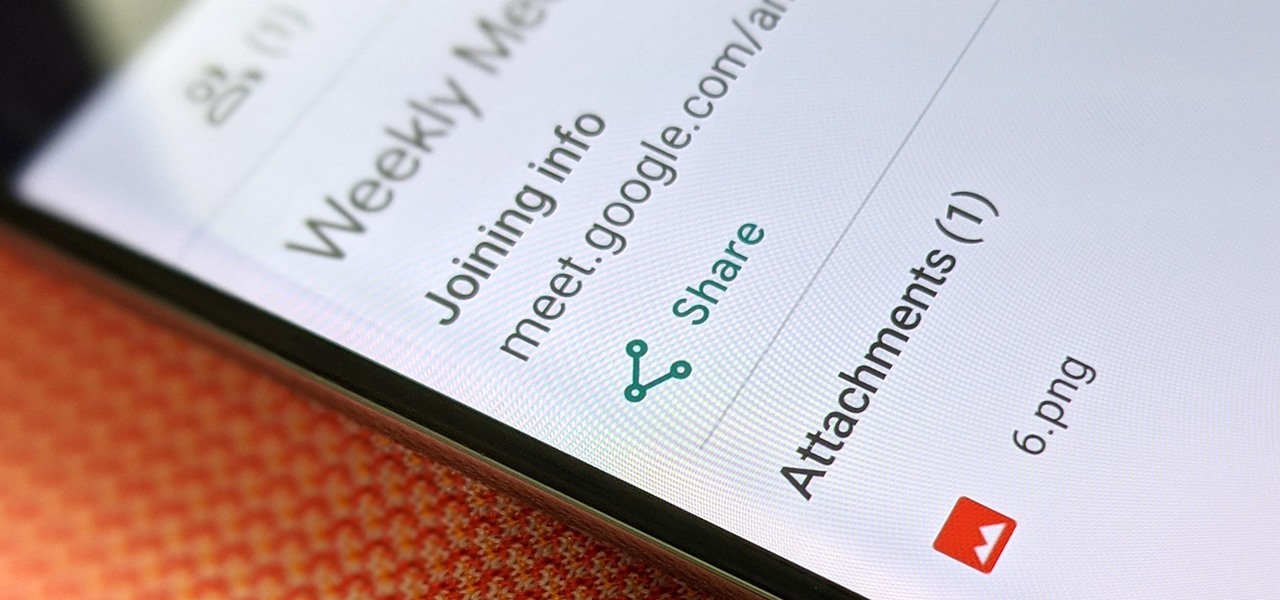
Google Meet might not have virtual backgrounds like Zoom, but it hits all of the other basics, from hosting many multiples of video participants to sharing your screen, that you'd expect from a robust video conferencing platform.

In the past, if you upgraded to a new Galaxy or if you had to factory reset your existing one to fix an issue, you had to restore your home screen layout manually. Your wallpaper, widgets, icon placement, and launcher settings were all dependent on you to be put back in their place. Thankfully, this isn't an issue anymore.

Without an available browser, it is challenging to enjoy media on your Nvidia Shield outside of the apps on the Play Store. It is because of this limitation that file transferring is vital, as only then can you enjoy your movies and music.

Netflix has offered its beta program officially through the Play Store for some time now. Still, the issue most of us face — the beta availability is always scarce. Without getting lucky and landing a beta spot early on when the gates were open, there wasn't much you could do about it. However, there's now a brand new method you can use to sideload the Netflix beta app and join in on the fun.

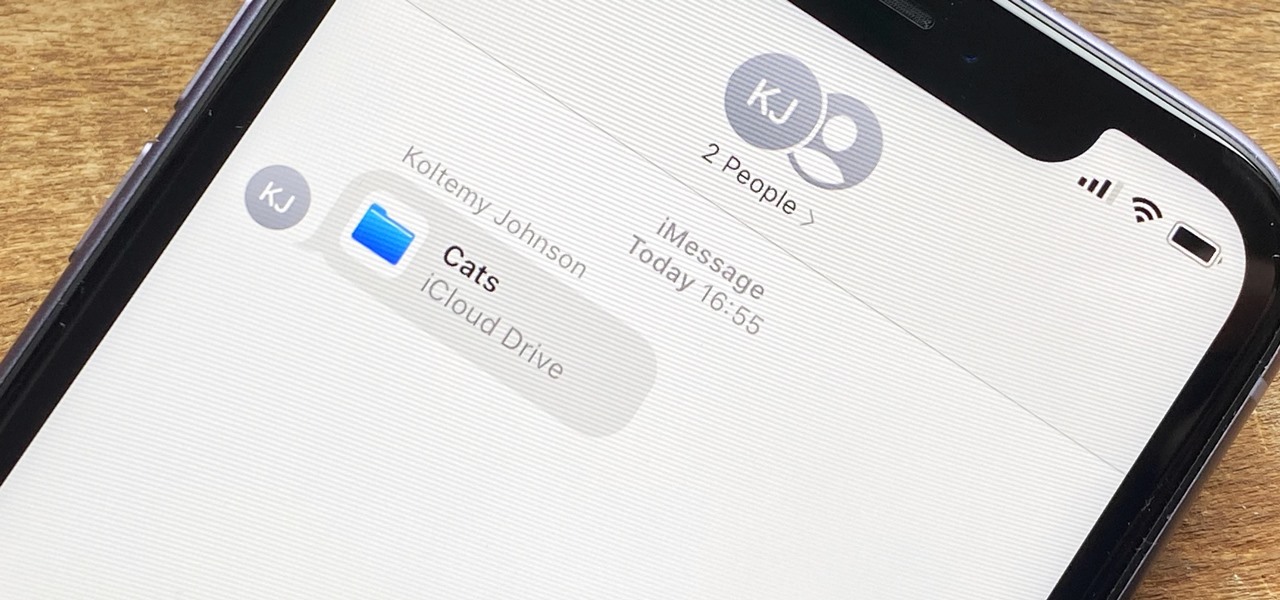
In the iOS 13.4 update, Apple added folder-sharing capabilities in the Files app. That means you can share multiple documents at the same time instead of doing it one by one. But that's not all — you can share folders with numerous contacts and even enforce access and permission settings.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

Android 11 won't be available as a beta update for Pixel devices until May 2020. Until then, the only way to try the latest Android version is by manually installing it. Usually, this means carrier models are left out since their bootloaders are locked, but there's still a way to get it done.

Google just released the first version of the next major Android update. Early Android 11 builds will only available as developer previews, so you can't just sign up for the beta program and install the update as an OTA for the first couple months. That said, it's still pretty easy to get.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

One of Android's biggest strengths relative to iOS is how simple it is to sideload apps that aren't on the official app store. Rather than having to sign IPA files or tell your phone you trust a developer every two weeks, you can just enable a setting and be done with it.

At least one hurdle to China-based augmented reality startup Nreal going mainstream in the United States may be about to be knocked down, thanks to behind the scenes legal movements Next Reality has uncovered.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

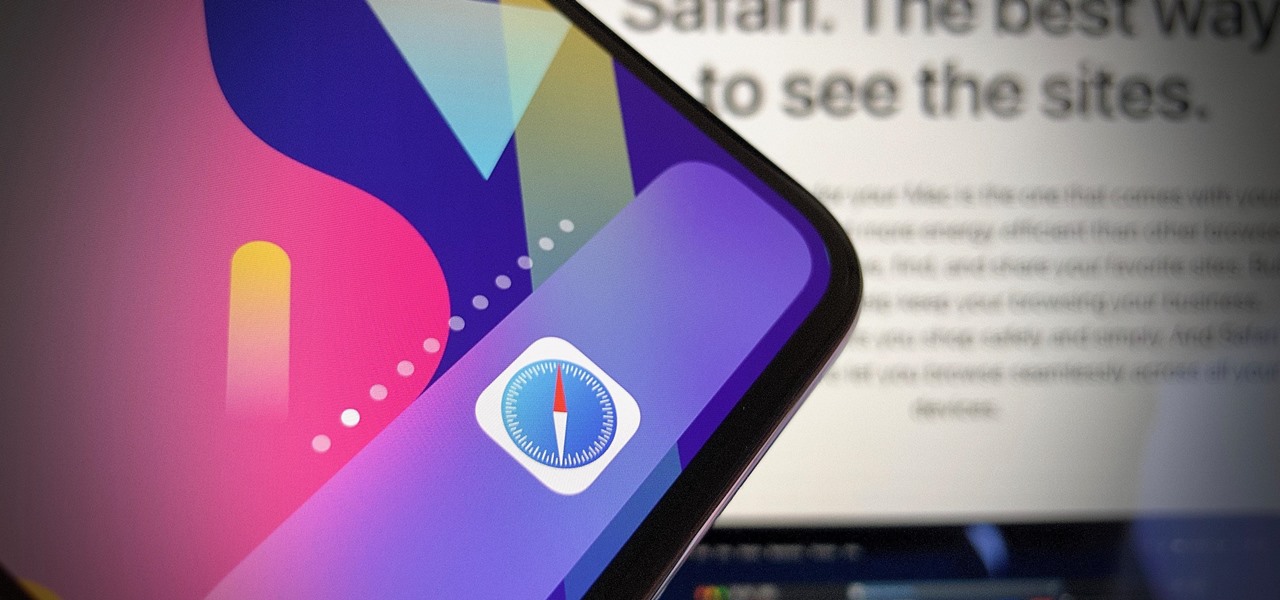
Apple's iOS 13 for iPhone includes new features in Safari that make browsing the web a little bit better when compared to iOS 12. Some changes are small while others add functionality that just wasn't there before. Plus, there are more security enhancements.

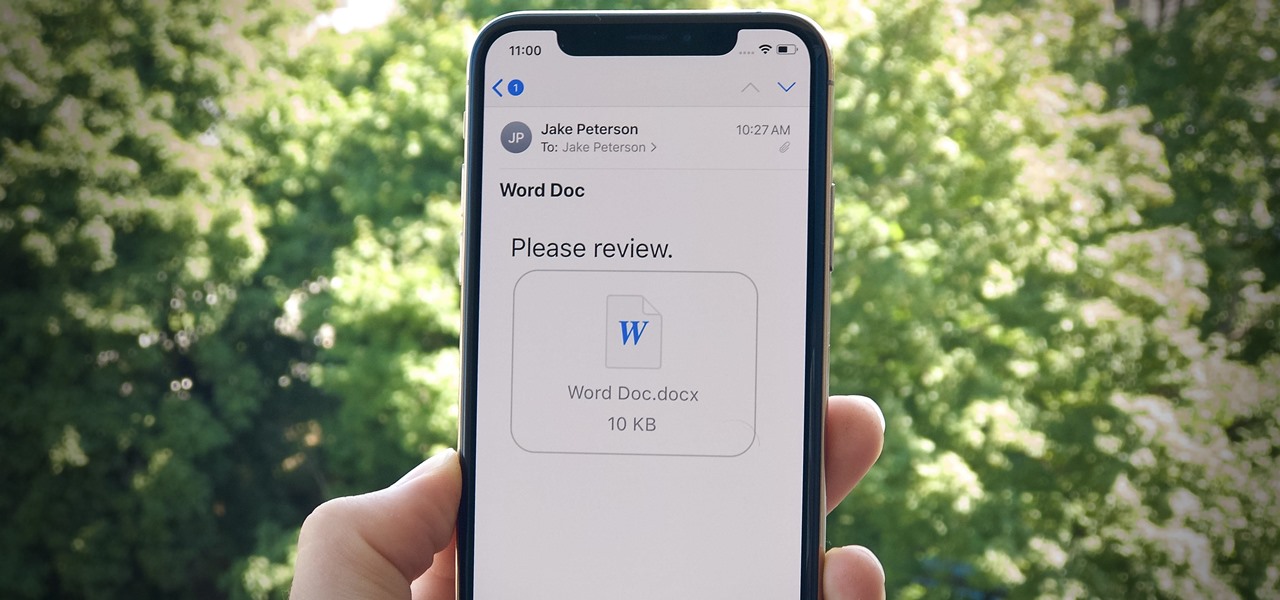
There's no doubt that Microsoft Word is the go-to for businesses worldwide. As such, you might receive Word documents to open on your iPhone, whether or not you actually have Word for iOS installed. If you prefer editing text documents with Pages, Apple's own word processor, you can import and export Word docs easily.

Although Mail didn't get a massive update in iOS 13, the new formatting and attachments toolbar makes it easier to stylize your messages and get quick access to files you'd like to send. It even includes the excellent document scanner built into iOS, so you can use your iPhone to turn a physical document into a PDF and attach it to your message — all from within the Mail app directly.

OnePlus has purposefully made their devices easy to root so that you can spend less time waiting and more time doing. These phones are a solid choice for anyone looking to dive into the rooting and modding scene. Using the same principles that Google has with the Pixel line, you can always be sure your OnePlus 7 Pro will get first-class treatment from launch day and beyond.

The Pixel 3a came out of nowhere and flexed its muscles to show the industry that you can have a great phone without a hefty price tag. Since Pixel smartphones are first-party devices straight from Google, you can be sure you'll have root access one way or another. For right now the method used to get your Pixel 3a rooted will take a few steps, but they go by real quick.

Every model iPhone since the 6s has boasted a 12-megapixel rear camera. You can take some pretty spectacular, professional-looking photos with it, especially on devices that have more than one rear lens. But the file size of each photo can become a problem when sending as an iMessage, which can eat up data.

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

When Stardew Valley launched back in 2016 on Steam for PC, it was instantly deemed a success for steering the RPG farming simulator genre back on the right track. Before its release, we hadn't seen too much in this particular field of games that caught the eye of the general public. Since then, the mega-hit Stardew Valley has made its way to the mobile world of Android and iOS.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

Switching phones has never been easier. Google backs up most of your app data on the cloud, which can then be restored onto your new phone. Sadly, Signal doesn't use this feature since it could compromise your security. Instead, Signal stores encrypted backups locally, requiring a bit of work to restore these messages.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

When Google introduced the Pixel 3 on October 9th, one of new additions they briefly mentioned was the Titan M security chip. While they did talk about how it will improve overall security, they didn't expand on the number of changes it brings to the Pixel 3's security. Well, they finally shared more, and it's a pretty big deal.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

Note-taking apps are a dime a dozen on the Play Store. However, due to their inability to sync across devices, many can't compete with Google Keep. Mozilla decided to throw their hat in the ring with Notes by Firefox, and unlike others, their notes app syncs easily with one of the most popular browsers, plus it's encrypted.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.