This image editing software tutorial shows you how to use Dr. Brown's Interpret Video & Fit Video to Audio script for Photoshop CS3. Change the frame rate of video files with these easy to use scripts. These scripts will only work with Photoshop CS3 Extended.
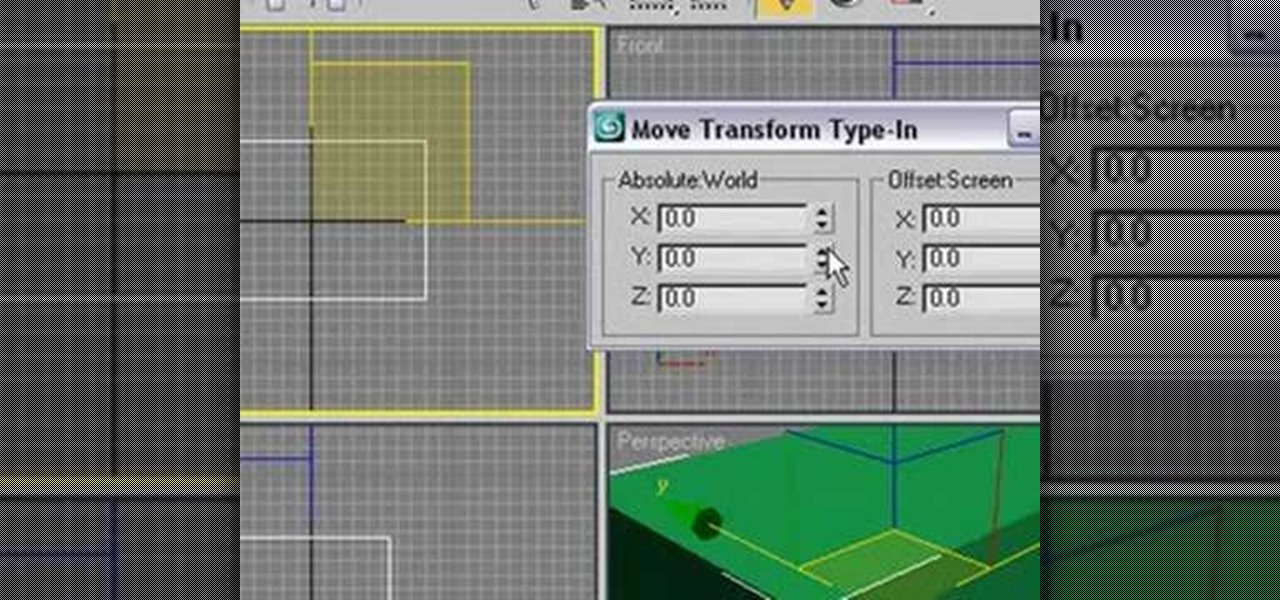
This software tutorial series teaches you how to box model in 3DS Max. Specifically, you will learn the basics of box modeling in 3D Studio Max, then box model a jet and animate it for PaperVision3D.
Google Earth is a great tool of the web, if you know how to use it the right way. Learn everything you need to know about using Google Earth in this powerful video series set to show you all the basic maneuvers and tricks to using the well known application. Google Earth is a cross-platform program, so the steps shown in this video series will work on Windows operating systems, as well.
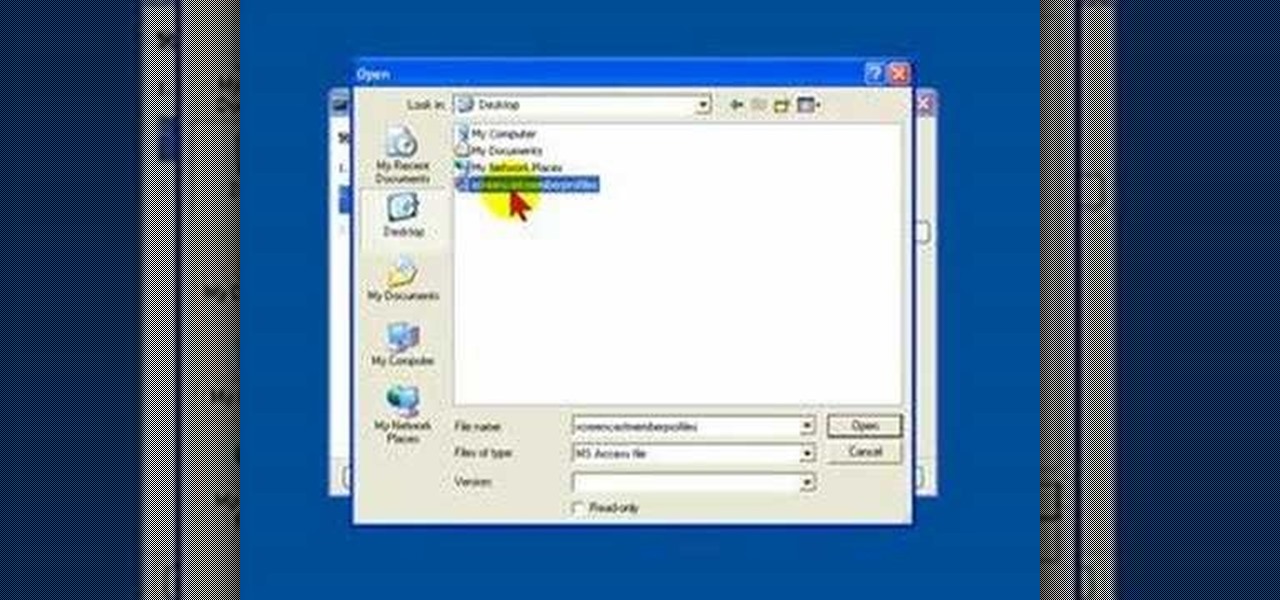
While you cannot directly open a Microsoft Access database file in OpenOffice Base, it is possible to connect Base to an Access database, and manipulate the data contained within it.
This tutorial shows you how to use specular maps to create textures on a lemon in Maya. Lesson files here:

This video shows how to make your own webserver to share files or host websites for anyone on the net to access for free, in under 7 minutes using Apache, which is free software.

Have a million 3-inch reel-to-reel tapes piling up in your garage? Keepsake audio tapes?

Aperture provides two sophisticated sharpening tools, edge sharpen and sharpen. Both help you improve the fine details in your images. Most images from digital cameras need a little sharpening, especially RAW files.

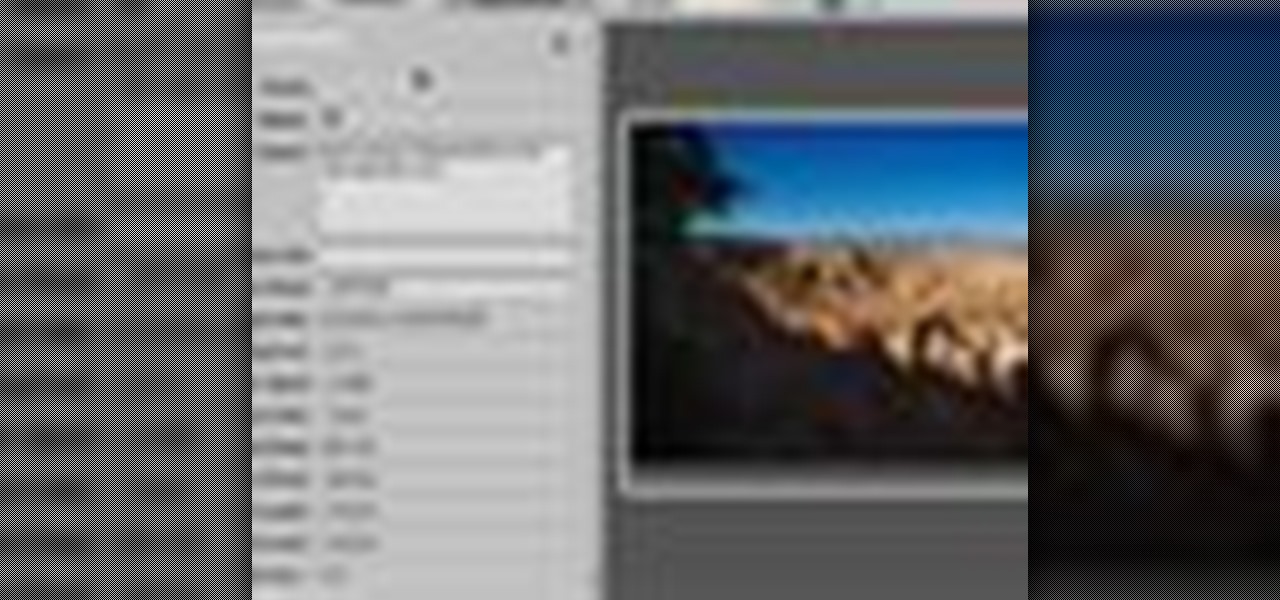
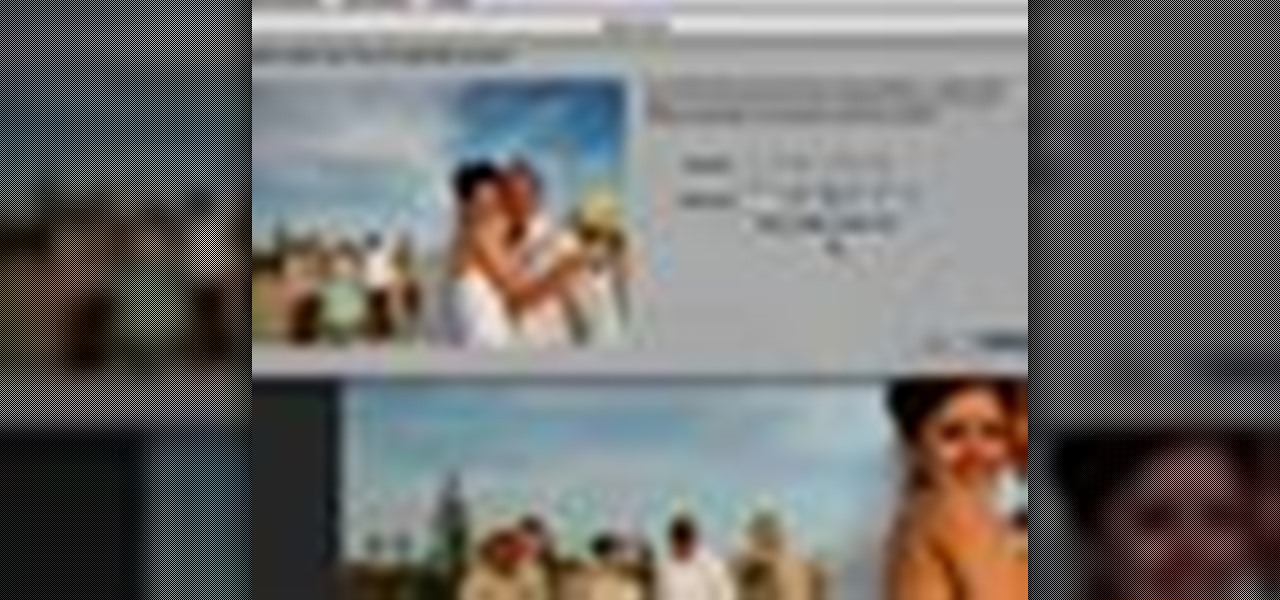
Aperture's metadata inspector is a one-stop location for editing the metadata associated with your images. Some of this metadata is automatically stored within the image files of your digital camera, and aperture automatically reads it when you import your photos. You can add other metadata, such as keywords, yourself.

All digital cameras automatically record the date and time each photo was taken and store this time stamp as metadata within each image file. In Aperture 2, you can change these time stamps. This is particularly useful if the clock in your camera is set incorrectly or if you're trying to synchronize photos taken by multiple cameras at a single event.

With Aperture, you can include IPTC metadata when you export a version of an image and embed it when you export a master file.

When you add accurate information about each song, it'll be much easier to browse and find songs in your library. Choose a song, go to the file menu, and click "Get info." You can even add comments of your own to a song's information. These are great tools you can use to organize your music.

When you save your iDVD project, you can save a version of the project in what's called a project archive. Archives contain all the files, menus, movies, and slideshows that make up your DVD. Once created, the archive can be saved to an external disk, copied to another Mac, or saved on your desktop.

Final Cut Pro and Final Cut Server work seamlessly to give you a smooth and integrated work flow. To upload a Final Cut Pro project into Final Cut Server, drag the project file into the Final Cut Server asset pane.

Final Cut Express makes it easy to convert or capture your videotapes into digital video files. All you need to do is set the desired capture format and destination for your clips. The Final Cut Express menu also provides an Easy Setup function.

Learn how to write your movie to tape or store it as a digital file using Apple's Final Cut Express in order to share it with others. Using this process, you can play your movie on a VCR, website, iTunes, iPod, DVD, or any other device or format.

Prank a friend's Windows PC computer so that it plays embarrassing female orgasm noises every time the computer is turned on.

Mastering the concepts of the BOOT.INI file (the boot loader) in Windows XP to better control your Windows configuration.

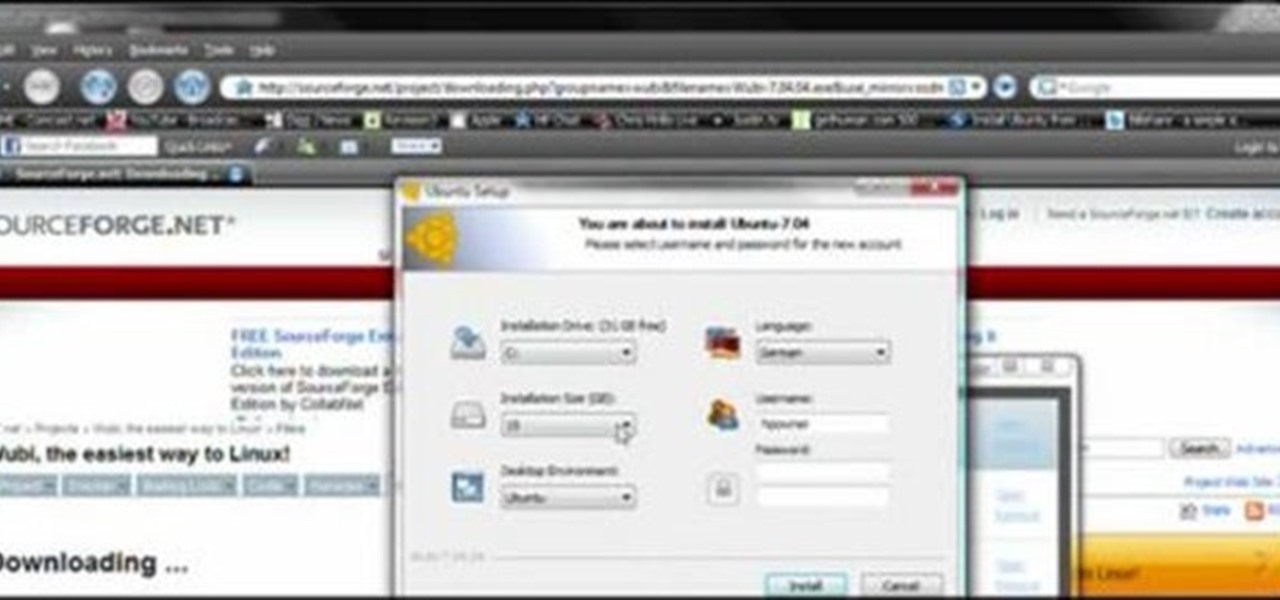
This is a easier way to install Ubuntu with out having to partition your hard drive. Wubi (www.wubi-installer.org) allows you to boot into Ubuntu by saving a file to the boot folder in Windows Vista or Windows XP. You can always uninstall Ubuntu easily without any complications to Windows Vista or Windows XP. This is not VM ware.

Do you have an old PC sitting around somewhere in your garage? Want a dedicated audio server that will play back MP3s, Internet radio, and other digital music files over your home stereo system? This CNET video teaches you how to convert your old PC into an amazing server!

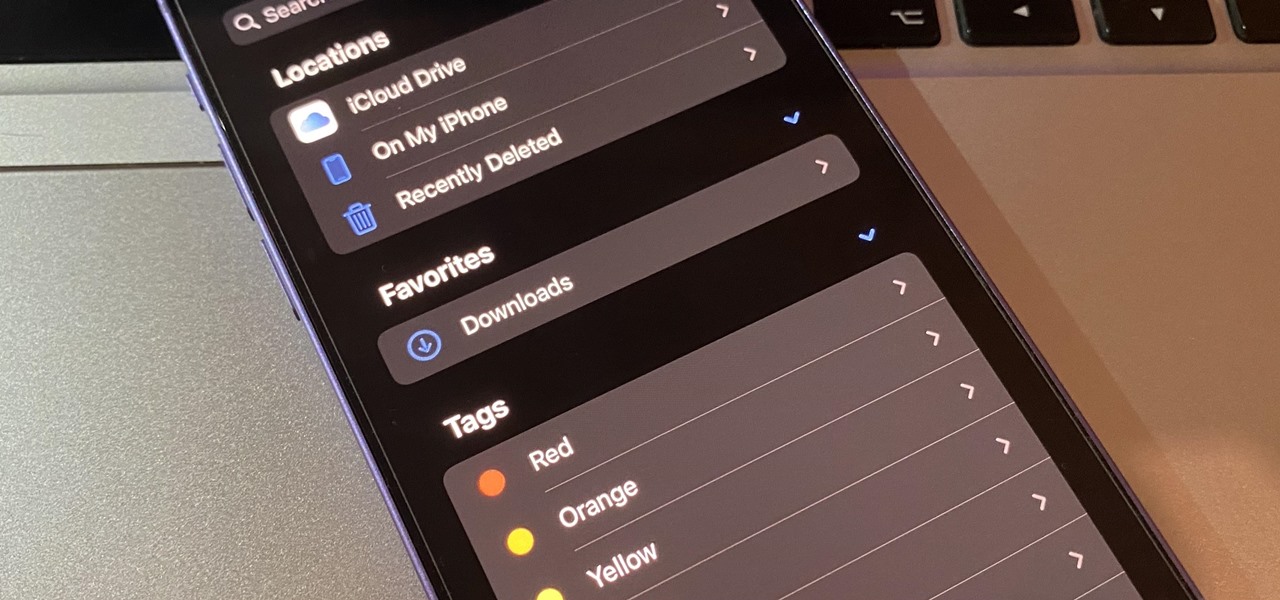
If you're not using your iPhone's Files app yet to manage images, documents, and other files on iCloud, third-party cloud services, or your local storage, it's time to start. Apple's built-in file manager is finally a powerhouse with many tricks up its sleeve in the latest software update.

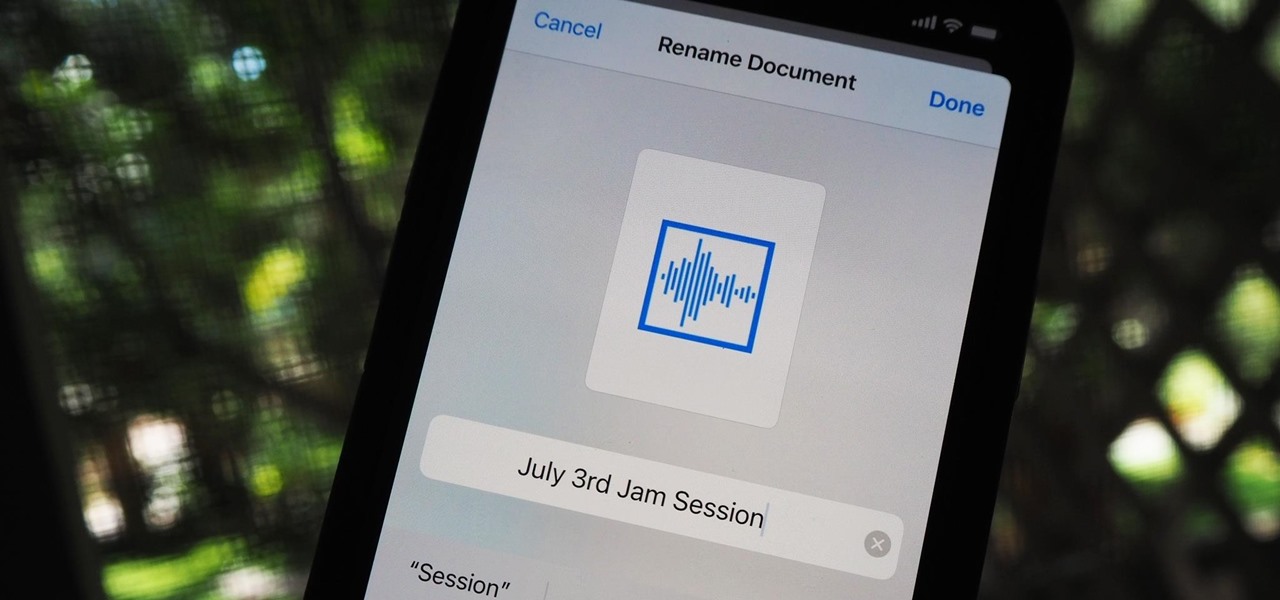
You can easily remove audio from videos in the Photos app on your iPhone, but the same cannot be said about removing video and just keeping the audio track. However, another stock Apple app can help extract the sound clip, and it barely takes any work to set it up.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

After introducing and launching Reality Composer alongside iOS 13 and ARKit 3 last year, Apple is making it easier for developers to create apps with it.

Unlike some of the popular app lockers out there, a nifty app fittingly named App Hider completely erases apps, files, and their associated footprints from your smartphone. Think of App Hider as a micro-OS within your smartphone's system. This miniature ecosystem can operate copied apps independently, thus giving it an unprecedented layer of privacy and freedom within your handset.

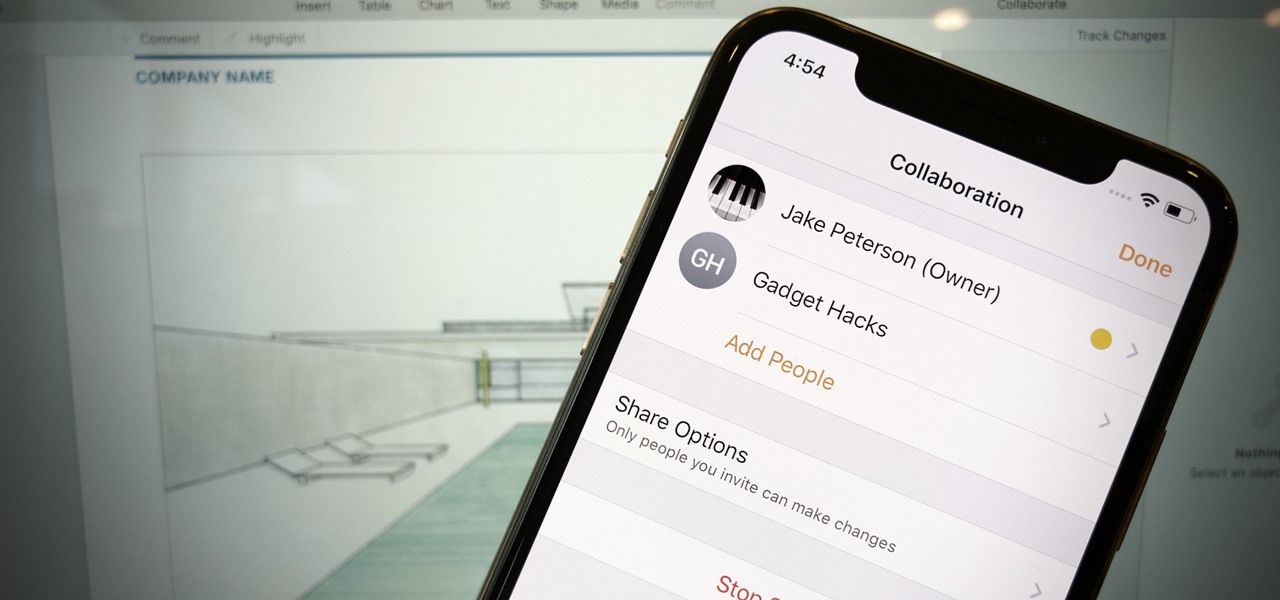
Google Docs is made for teamwork and collaboration, but Apple's iWork suite also comes with the same functionality. If you're working on a Pages document on your iPhone, and you want input from other members of your team, you can easily invite them to view, comment, edit, and more right alongside you.

When new Android versions come out, the modding community has to find new ways to root the OS. It's a fun cat and mouse game to follow, but it also means the process of rooting isn't exactly the same as it was the last time you did it. Android 10 changes how root works on a system level for some devices, but luckily, the developers are already on top of things.

In a legal brief entered on Monday, Florida-based startup Magic Leap has filed suit against the founder of Nreal, a former employee of Magic Leap, claiming that the company's Nreal Light smartglasses were built using Magic Leap's intellectual property.

Rooting usually means sacrifice. With most root methods, you lose access to apps like Netflix and Android Pay when SafetyNet gets tripped. More importantly, you lose the ability to accept OTA updates, forcing you to manually flash new Android versions. But there's a way around all of this if you root the right way.

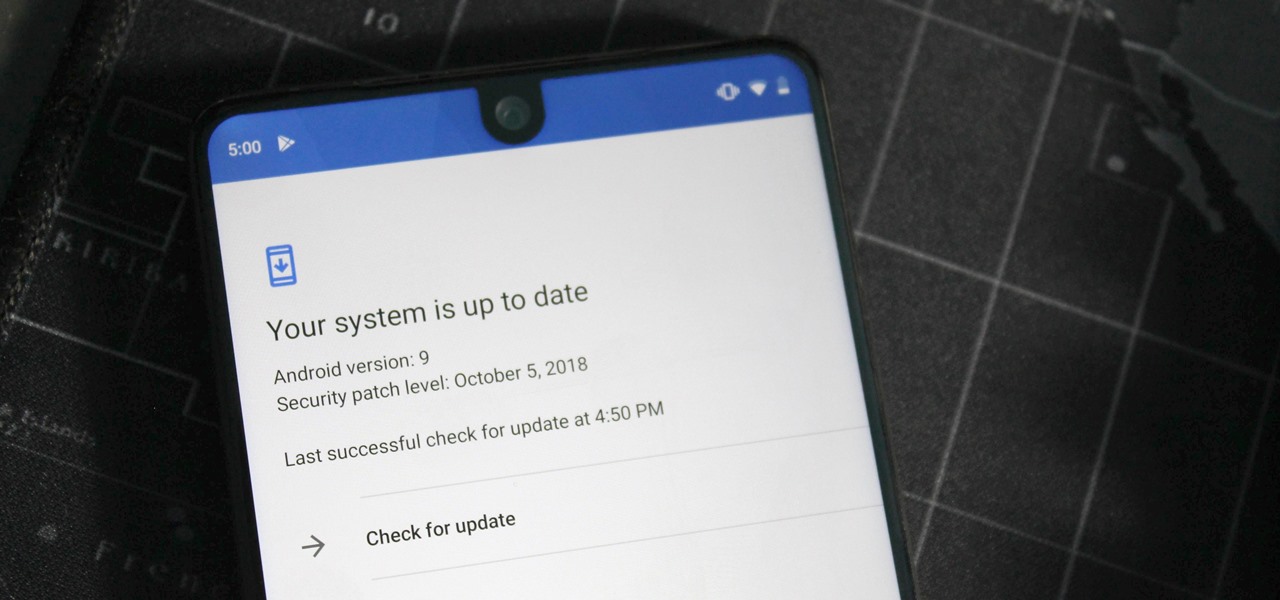
So, you rooted your Pixel 2 or 2 XL and everything seems to be working quite well. However, a month passes, and you get a notification to install the monthly security update. Like clockwork, Google has been pushing out OTA security patches every single month for a while, but there is a new problem for you at this point — as a rooted user, you are unable to apply the update correctly.

One of the issues with rooting your device is the inability to update your phone via OTA. Any security patches or software updates pushed out by the OEM are lost because your bootloader is unlocked. However, you still can update your device, it just a take a bit more effort.

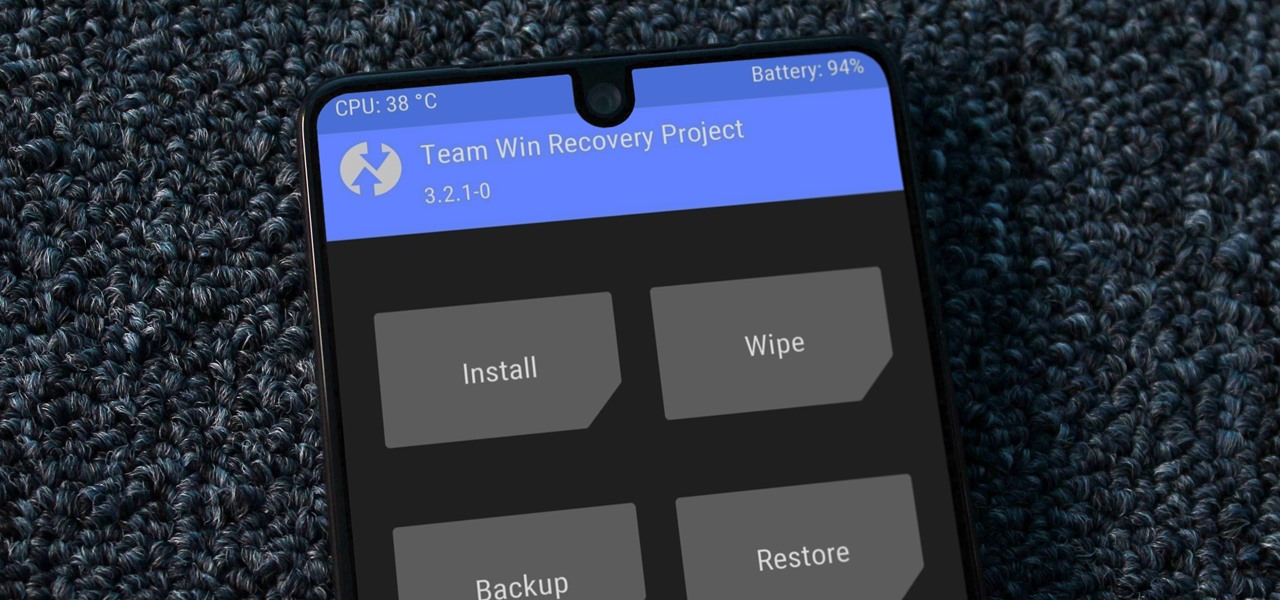
For modders, there are few tools more important than TWRP. TeamWin's custom recovery makes flashing mods like Magisk, Xposed, and custom ROMs incredibly easy, and it lets you root your phone at the press of a button. On top of that, it can make complete backups of your phone in case you mess up. That's why, for Essential users, this should be the first mod you add.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

Net neutrality is dead and your internet service providers can collect all the data they want. While VPNs are a great way to protect some of that privacy, they're not perfect. There is another option, though, called Noisy, which was created by Itay Hury. It floods your ISP with so much random HTTP/DNS noise that your data is useless to anyone even if they do get it.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

Online shopping giant Shopify literally cannot wait for ARKit 2.0 to arrive via iOS 12 this fall to implement its latest augmented reality feature.

It always helps to be prepared for the worst. This applies to our phones now more than ever, as we depend on them to be our record keepers for text messages from friends, family, and coworkers. If you ever lose or severely damage your phone, having a backup of your precious texts gives you the peace of mind of knowing that you can always get them back.

As we aim for a wireless world, technology's reliance on cloud computing services is becoming more apparent every day. As 5G begins rolling out later this year and network communications become even faster and more reliable, so grows our dependency on the services offered in the cloud.

Flying under the radar during Magic Leap's big week at the Game Developers Conference, the company settled a potentially ugly lawsuit with a former employee.

While installing the new Android 9.0 Developer Preview is fairly easy if you're using a Windows machine, it's a little trickier if you want to use macOS instead. To help you get the latest Android OS on your Google Pixel phone, we'll break down the whole process so using your Mac can be as simple as Windows.