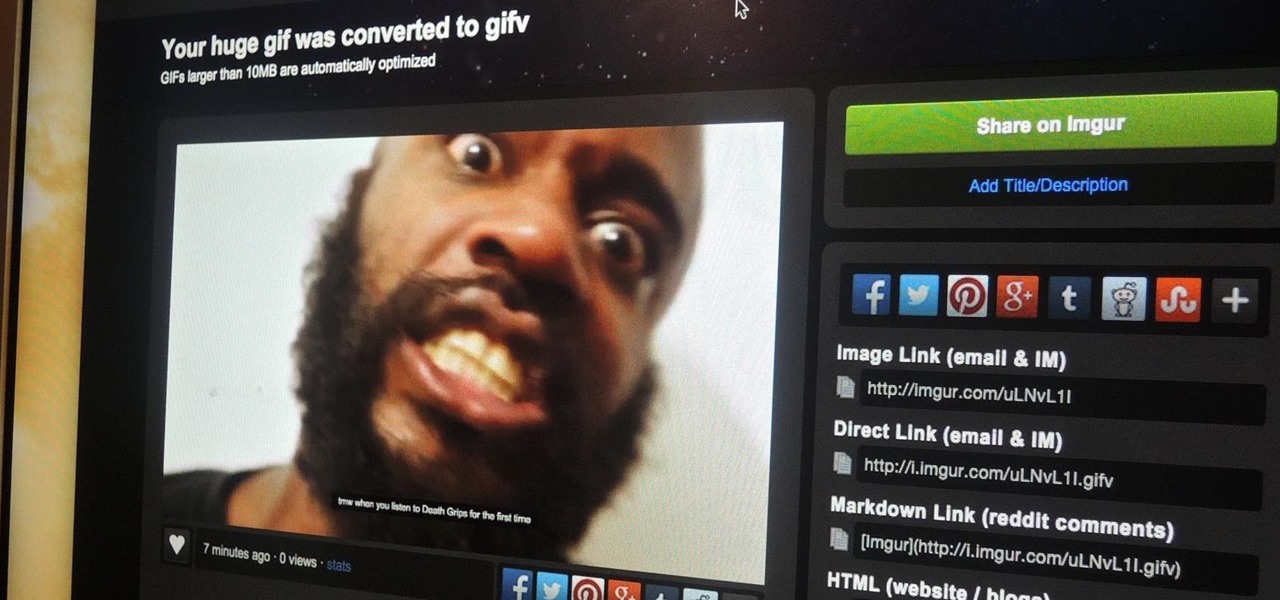
Imgur has just released a brand new feature to make GIFs better than they ever have before. Video to GIF is a tool that allows you to quickly paste any video link, easily select a clip from that video, and turn it into a very high-quality GIF, called a GIFV.

Welcome back, my amateur hackers! Over the course of the next year, we will be developing our own zero-day exploits. In my first article in this series, I introduced you to buffer overflows, which are the source of some of the most lethal exploits, particularly the "remote code execution," so we are focusing our exploit development here on a buffer overflow.

Amazon is currently offering over $80 in free Android apps in the Amazon Appstore, but only for Friday and Saturday, so make sure to grab them quick before they all go back to normal price. Highlights include the Fleksy Keyboard (normally $3.99), Oxford Dictionary of English with Audio (normally $24.99), and EasyTether (normally $9.99).

Google has already started to roll out the over-the-air update of Android 5.0 Lollipop to older Nexus series phones and tablets, but chances are it will take a long time for the OTA to hit your device.

The OnePlus One comes with CyanogenMod 11S built in, but there are certainly some traditional CyanogenMod features missing from this version. One of the most obvious missing ingredients is the lack of a native SuperUser app, most likely to prevent inexperienced users from causing unintentional damage to their device's software.
It didn't take long at all for developer Chainfire to sort out a root method for the new Android 5.0 Lollipop. After handling a few issues with changes to the SELinux kernel module, Chainfire pushed out an update to his popular SuperSU root app.

For the most part, Finder has had the same basic functionality through the various releases of OS X. But Apple's lack of interest in adding new bells and whistles to the backbone of their operating system simply means that 3rd-party developers get to shine, and Tran Ky Nam is one such developer. He created his own extension for Finder that adds tabbed browsing, dual pane mode, cut & paste functionality, and much, much more.

Anytime you surf the web on your iPad or iPhone, Safari saves which webpages you visit, the information you enter into them, and other types of data. This not only make your internet experience quicker, but it'll also keep track of everything you're doing.

Welcome back, my amateur hackers! Many of you here are new to hacking. If so, I strongly recommend that each of you set up a "laboratory" to practice your hacks. Just like any discipline, you need to practice, practice, and practice some more before you take it out to the real world.

Apple's new iPhone 6 and iPhone 6 Plus go on sale Sept. 19th, but pre-orders begin on Sept. 12th. If you're ready to trade in your iPhone 5 for one of these bigger and more iOS 8-friendly devices, you're probably going to pre-order.

Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on.

One of the best features of Android is the fact that it's open-source, giving developers the ability to use it on pretty much any device they can think of, like on a Windows PC using Andy. That's what drove the creators behind the Android-x86 project to port over the mobile OS to any computer running an Intel processor.

My OnePlus One easily gets over a day of battery life without a problem, but when I try to charge it, it seems to take just as long. For some reason, no matter what charger you plug your OPO into, it never gets more than USB-level power, meaning that charging times are more than double when compared to traditional AC-charging.

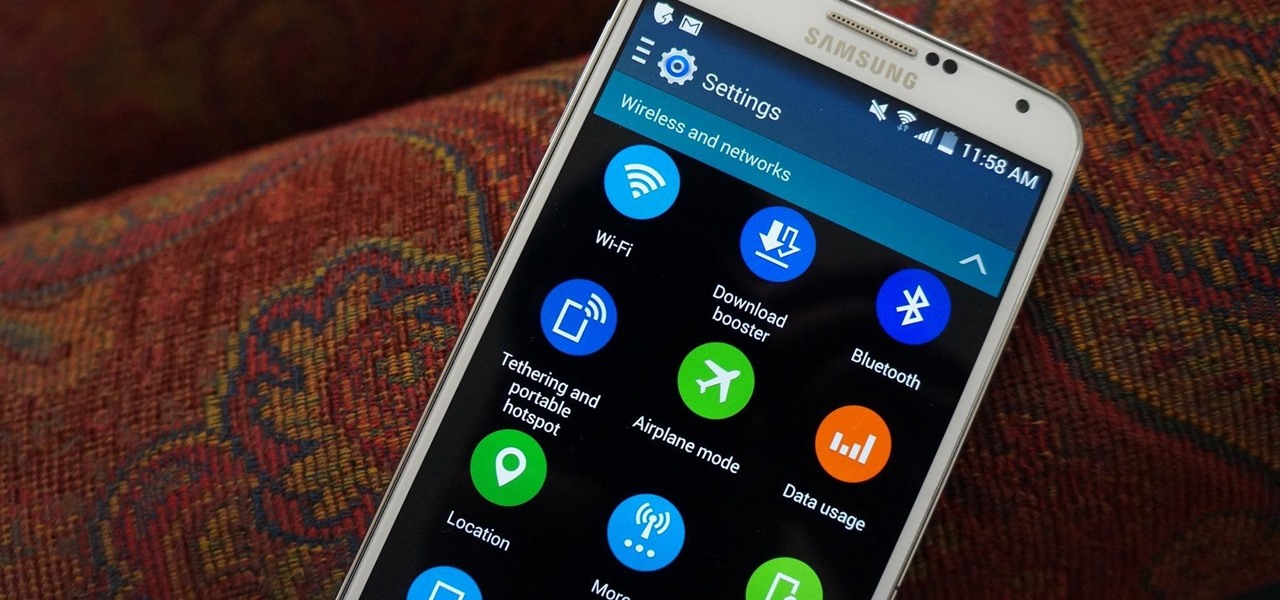
When the Samsung Galaxy S5 launched a few months ago, I was pretty envious of the new UI elements Samsung included on it, as I'm sure you were. The flatter interface provided for a more polished and less cartoony feel, bringing the device more in line with Google's design elements.

If hearing the names of classic PC games like Commander Keen, Fallout, Master of Orion, and Wolfenstein 3D send you into a fit of nostalgia, then DosBox Turbo is the perfect app for your Android device.

With a root bounty of over $18,000 up for the taking, developers were highly motivated to get the AT&T and Verizon Wireless variants of the Samsung Galaxy S5 rooted. Legendary hacker George Hotz, aka Geohot, has won the race and can now step up to claim his prize.

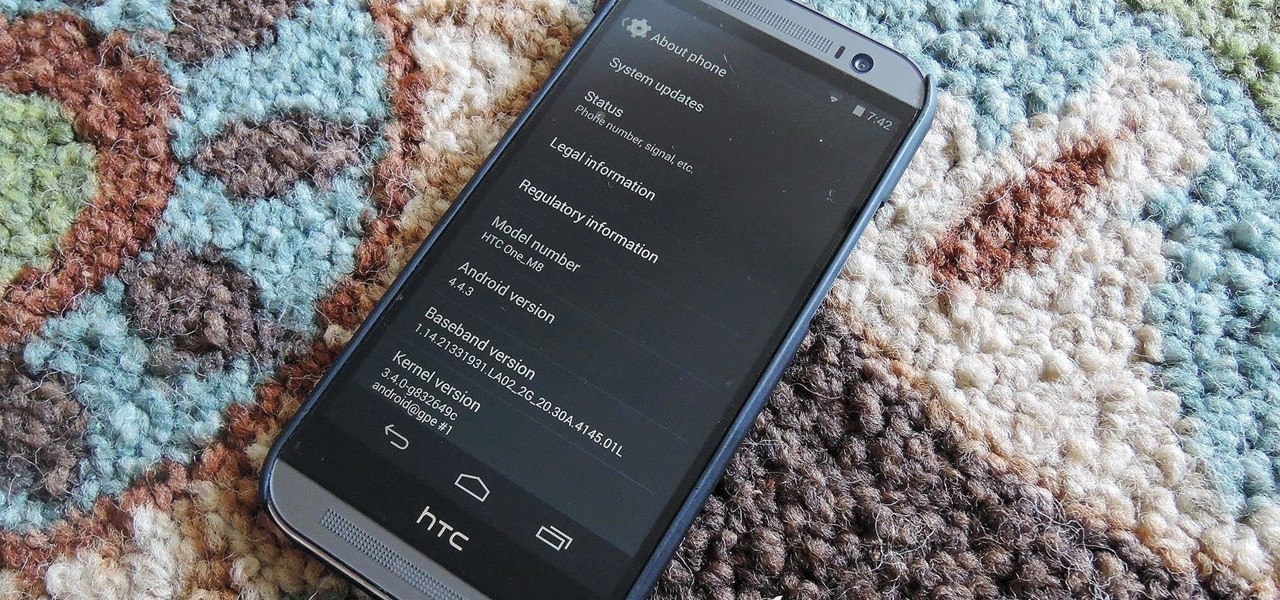
The beauty of having a Google Play Edition HTC One is the ability to get as close to stock Android as possible while still getting some extra non-Google, proprietary HTC features. The newest version of Android, 4.4.3, has just hit the Nexus and Google Play Edition line of phones, but if you are rooted with a custom recovery, you will not be able to apply the OTA.

Update: June 19, 2014 Android 4.4.4 has been released, fixing a small security bug in 4.4.3. The factory images have already been made available to all current-generation Nexus devices, and I've linked them out below. This does not affect the process depicted, you can still use these same steps to bring your device up to date with this latest release.

The Android 4.4.2 KitKat update is available via firmware upgrade for the international GT-N7100 variant of the Samsung Galaxy Note 2, about a month after we saw its first leak. The update is available via Kies in France, with and OTA update soon to follow. Details courtesy of SamMobile are as follows:

Now that Hangouts is Android's default messaging app, it's given us a lot of cool new features. A bouncing ellipsis lets you see when the other party is typing, and an indicator shows you whether they've read your message or not. You can even answer the age-old question of "Where you at?" with a tap of a button, sending a map of your location.

Welcome back, my tenderfoot hackers! We have looked at a number of ways that we sniff traffic on the network with such tools as Wireshark, tcpdump, dnsiff, and others, but each of these tools is only capable of pulling packets off the wire.

A good prank requires decent effort, creativity, and impeccable timing. If you're in the office, there are plenty of hilarious pranks to play on coworkers, and for your family and friends, there's everything from toothpaste-filled Oreos, to solid milk, to impossible-to-solve Rubik's Cubes and smartphone-friendly pranks.

As softModders, the first thing we do after updating to the newest version of Android is to root, install a custom recovery, and install a superuser app. By doing this you open up your HTC One to a vast quantity of new apps and tweaks you can use to truly make your phone One of a kind.

Privacy features have become quite the hot commodity, emerging from the aftermath of the NSA scandals that rocked the United States this past year. While the NSA has the means to gather information on all of us (regardless of any security software we implement), it doesn't mean that they're the only ones looking.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

You probably already know by now that a custom Android ROM can change your user experience and give you what feels like a new OS on your device, and there's no shortage of them out there to try out.

That didn't take very long! Yesterday, after a lengthy delay, Google opened up the development kit for their Chromecast HDMI dongle.

Scrolling through Instagram, you're going to come across a lot of photographs and videos that you "like." But sometimes, you're going to want to remember a photo, and naturally want to save it to your device so you can look at it for forever and ever.

The iOS 7 release brought with it many new aesthetic upgrades, from new flat, vibrant icons to a sleeker text messaging interface. Another small, yet noticeable, difference is the minimal and clean lock screen, which removed the overbearing "Slide to Unlock" background bar in lieu of just the text.

If you have an older Samsung Galaxy Y smartphone, one thing you should be doing is using an microSD or microSDHC memory card to help improve your Android's processing speed and make it easier to transfer large or small files easily. These cards are also compatible with certain cameras and can be inserted into some computers. While all this is all good and well, you'll still need to know how and where to put your SD card in order to indulge in any of these benefits. Your Samsung Galaxy Y (the ...

Let's get one thing straight: CyanogenMod is one hell of a ROM. They've got a great community, a great product, and getting it on your HTC One couldn't be easier with their CyanogenMod installer, which does all the hard rooting and bootloader unlocking for you.

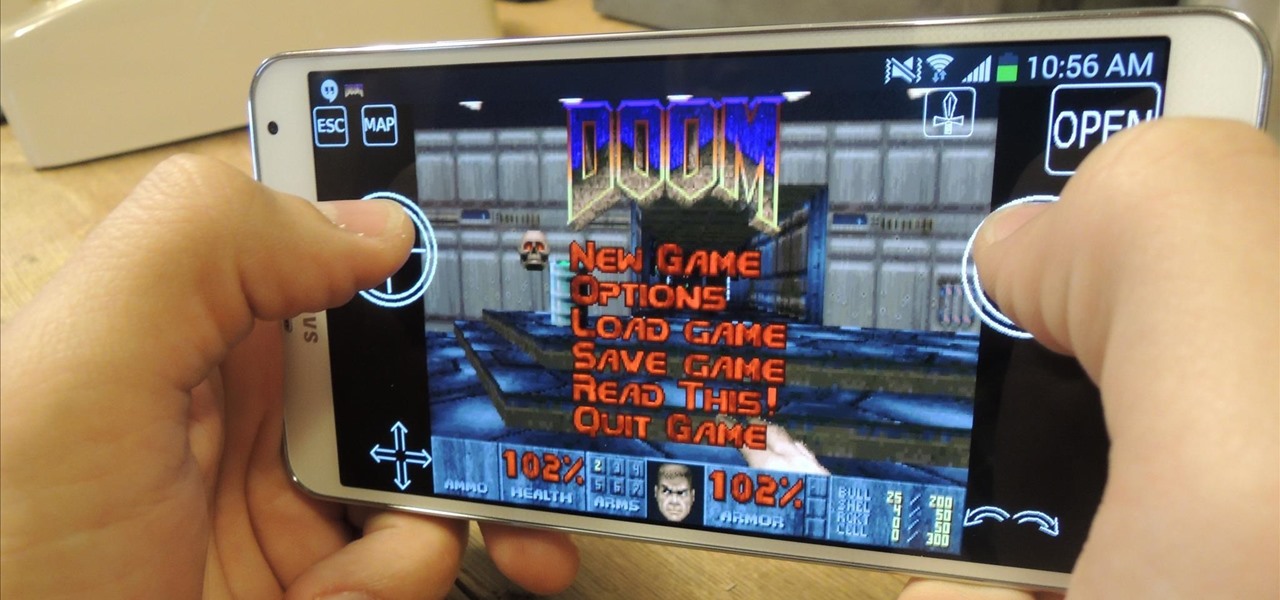
In the wake of its 20th anniversary, the folks over at Eltechs have released Original DOOM, a full shareware version of the revolutionary first-person shooter DOOM for Android, available for free on the Google Play Store. It's unmodded and unaltered from the original FPS classic.

Welcome back, my budding hackers! In my continuing series on Linux basics for aspiring hackers, I now want to address Loadable kernel modules (LKMs), which are key to the Linux administrator because they provide us the capability to add functionality to the kernel without having to recompile the kernel. Things like video and other device drivers can now be added to the kernel without shutting down the system, recompiling, and rebooting.

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

Apple may have made Mavericks more accessible to Mac users everywhere at the fair price of zero dollars, but unfortunately, they made it trickier to create a bootable install drive of the Mac OS X 10.9 operating system.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

Russians are well known for their knack at documenting exciting and horribly beautiful events on the go, from insane car accidents to attempted insurance fraud and even a superbolide meteor streaking across the sky.

To really customize your Samsung Galaxy S3, you'll need to be rooted, because most of the coolest mods and hacks require root access. If you haven't rooted yet, you're just barely touching the surface of what your GS3 can do for you.

There are a ton of cool features available on your Samsung Galaxy Note 2, but if you're a softModder, you can make your phone do just about anything.

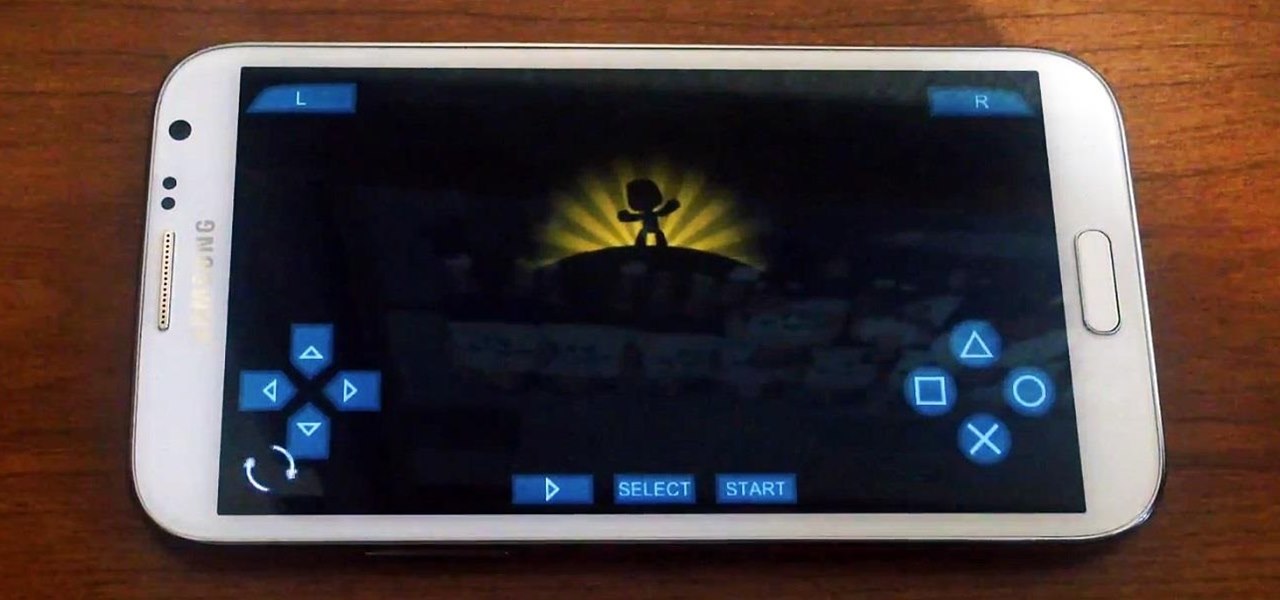
If smartphone video games have a weakness, it's probably their inability to emulate the riveting and immersive experience that consoles offer.