Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

Black Desert Mobile is one of the hottest new smartphone games around, but there seems to be something missing in the frame rate department. Gamers quickly noticed many Android phones are stuck on a 30 FPS cap when it comes to performance. It's not that the phones are too weak to handle higher frame rates, but that there is a particular list of approved devices that can achieve this.
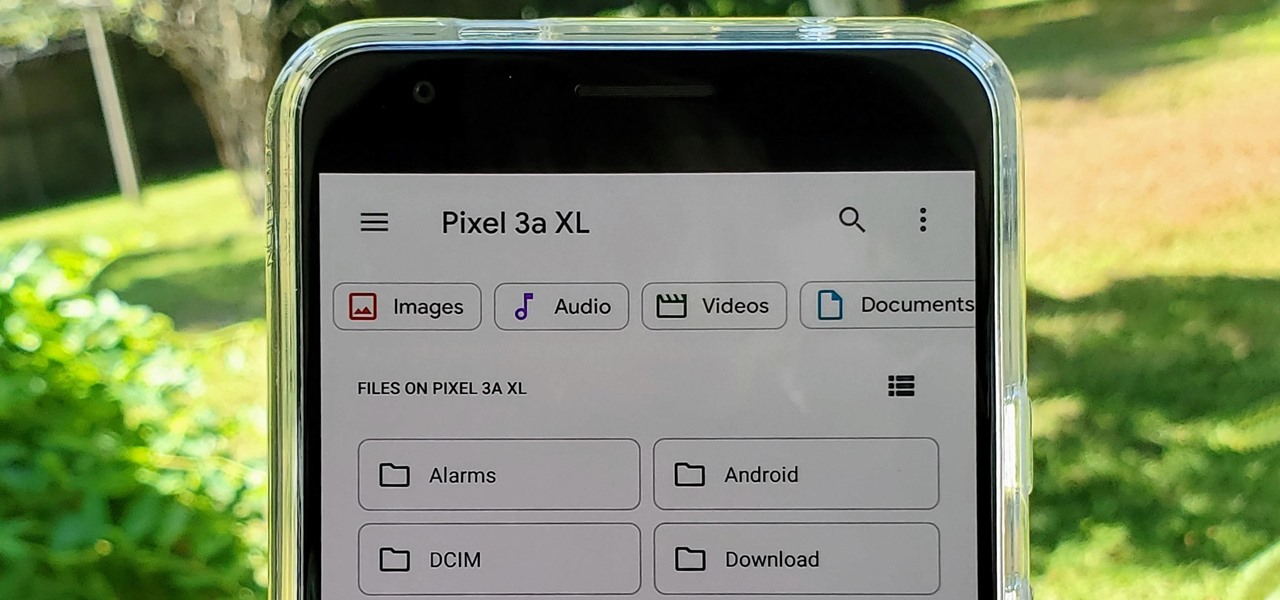
With the files on our devices getting more important as the years go by, the need to keep things organized continues to rise. The longer you have a device, the messier the internal storage might become. Having a file manager would be extremely useful in this situation. You could also reorganize the folder structure as well, just like you could on a desktop computer.

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

To be honest, the Mail app for iPhone had always been somewhat forgettable. It lacked many of the features that made third-party clients like Spark and Edison better, but with iOS 13, the gap between Mail and its competitors is much smaller. Apple updated the layout and added many new features to its native emailing app, and that may be just enough to get you to switch back.

It's finally out. After months of testing, iOS 13 is available to install on your iPhone, which means over 200+ new features you can use right now. The update, released on Sept. 19, can be installed over the air or from a restore image using iTunes in macOS Mojave and older or Finder in macOS Catalina. Ditto for the 13.1 update issued on Sept. 24.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

Google's has expanded ARCore support to numerous Android flagships like the Galaxy S10, so if you have a compatible device, you get access to all the cool new apps that can augment the world around you. One of ARCore's most sought-after features, AR Stickers, is normally exclusive to Google's Pixel lineup, but by sideloading the Google Camera app, you can try it on any ARCore device.

I noticed the neon yellow sign at the new location of Pho Bar in Chinatown right away. The sweeping cursive yellow letters spell out "Crazy Rich Broth"; the same phrase printed on the back of servers' shirts. It's the kind of minimalist but colorful design feature that is especially popular on Instagram at the moment — shots of patrons in front of a glowing sign.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

When we reviewed the best file managers on Android, MiXplorer easily topped our list with its abundance of features, including tabbed browsing, support for up to 19 different cloud services, file and folder encryption, and much more. The only major complaint we had was the fact it couldn't be installed from the Play Store, but now, that is no longer the case.

If you ever want to root your OnePlus 6, install TWRP, get Magisk and Xposed, or flash a custom ROM, the first thing you'll need to do is unlock your bootloader.

Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open the payload without knowing they are doing so.

Google's ARCore has expanded its support to include the Galaxy S9 and S9+, which means you get access to all the cool new apps that can sense the world around them. But one of ARCore's coolest uses so far is still Pixel-exclusive: AR stickers built right into the Google Camera app. Thankfully, XDA user lofass33 has an ingenious workaround for using these stickers on your S9.

To quote MKBHD, cheap phones are getting good. Each year we are seeing manufacturers start to offer more for much less. This not only translates to cheaper flagship phones, but better budget phones. The latest example of this is the Alcatel 3V, which is redefining what you can get at $150.

If you're anything like me, when you first find a good song, album, or playlist on Spotify, your initial reaction may be to share it with your family and friends. While there are the usual share methods available in Spotify that are available in other streaming music services such as Apple Music and Google Play Music, Spotify goes one step further with QR-like codes users can easily scan.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

Since making waves at Mobile World Congress 2018, Android Go devices have slowly trickled their way onto US shores. Only one device was officially announced for the US at MWC, but several OEMs have extended availability to the US in the months since, and it looks like we just received another.

The Galaxy S9 and S9+ have a new camera feature that Samsung is calling "Dual Aperture." On the surface, that may sound like your typical techno-jargon, but it actually has some significant implications for the future of smartphone photography.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

So you spent all day customizing your phone. You tinkered with all the settings, searched the web high and low for the perfect wallpaper, and found an ideal icon pack to complement the color scheme. You go to sleep, proud of the work you accomplished when the unspeakable happens — your phone freezes and tech support is telling you to do a factory reset to fix the problem.

Scanning important paperwork on smartphones is a tedious process, often relying on either external scanners or third-party apps that had to be either purchased or were loaded with annoying ads just to get the job done. Thankfully, iOS 11 now lets you easily scan documents using your iPhone, and finally does away with the need for third-party apps or machines.

There are many different ways and many different apps that allow you to censor a racy photo and then share it to Instagram or Facebook. If you're in a time crunch and don't have the time or the patience to deal with something like Photoshop, then Snapseed is a great and easy app that will blur out your raunchy images in a quickie.

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.

Waymo claims in court documents filed yesterday in its lawsuit against Uber that ex-Uber CEO Travis Kalanick knew that former Google engineer Anthony Levandowski was in the possession of stolen documents while employed at the troubled ride-sharing firm.

Seeing that wonderful blue verified badge on Twitter really adds something to your public persona, doesn't it? That's why, when I found out that the average person could get verified on Twitter with the right tools, I jumped on the chance to add that little blue check to my own personal account.

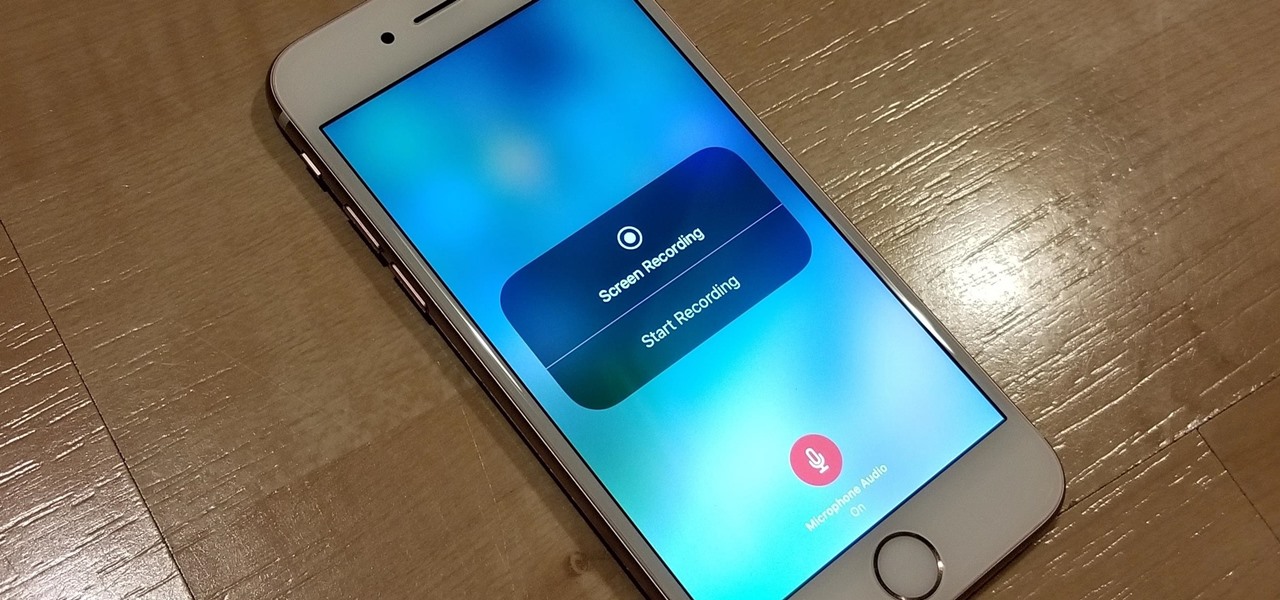
The only official way to record your iPhone's screen before iOS 11 was to hook it up to a Mac and use QuickTime Player to do the recording for you. If you wanted to record your iPhone's screen without an external device, there were unofficial apps you could use, like AirShou, but they required complicated installations. Now, in iOS 11, iOS 12, and iOS 13, Apple has an official, native screen recording tool.

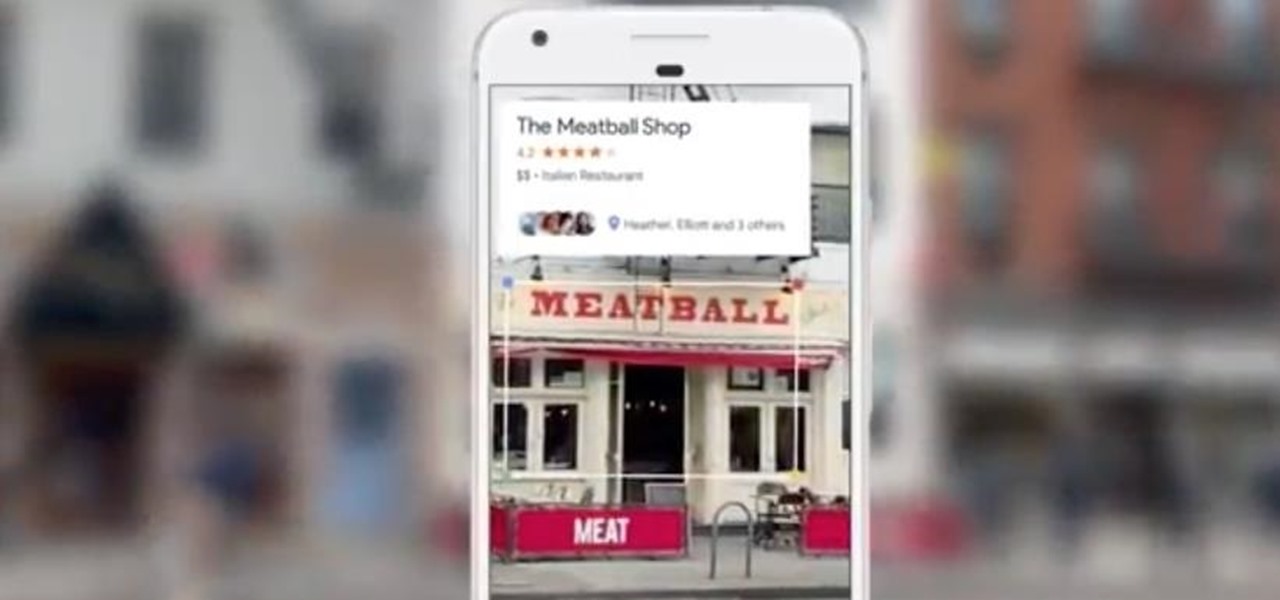
Google Assistant will be getting an AI makeover with the addition of Google Lens. This new feature is basically a set of vision-based computing capabilities within the Assistant.

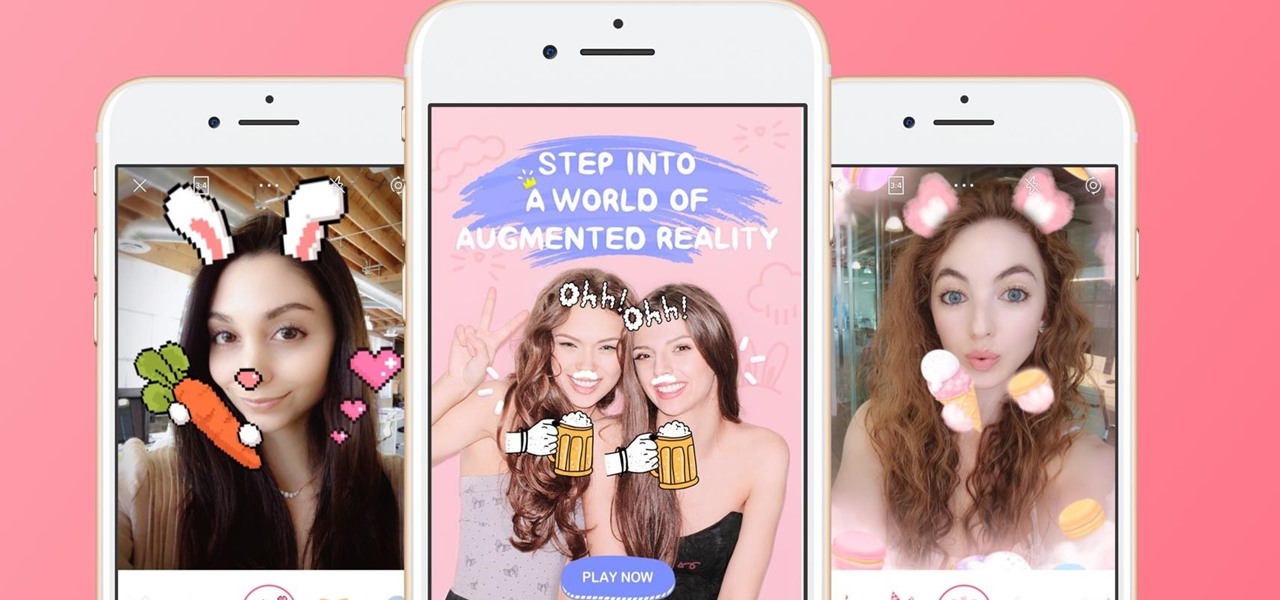
The popular beauty app company Meitu is incorporating augmented reality (AR) video and image filters and effects in its selfie-editing app BeautyPlus for iOS and Android.

Making a NANDroid backup can save you from all sorts of flashing-related mishaps and accidents. Bootloops, SystemUI crashes, accidental wipes, bad ZIPs, or a dozen other possibilities—there's almost no condition in which a NANDroid is unable to correct problems with your device. However, recent changes to Android have created an almost paradoxical situation where restoring a NANDroid can actually lock you out of your phone.

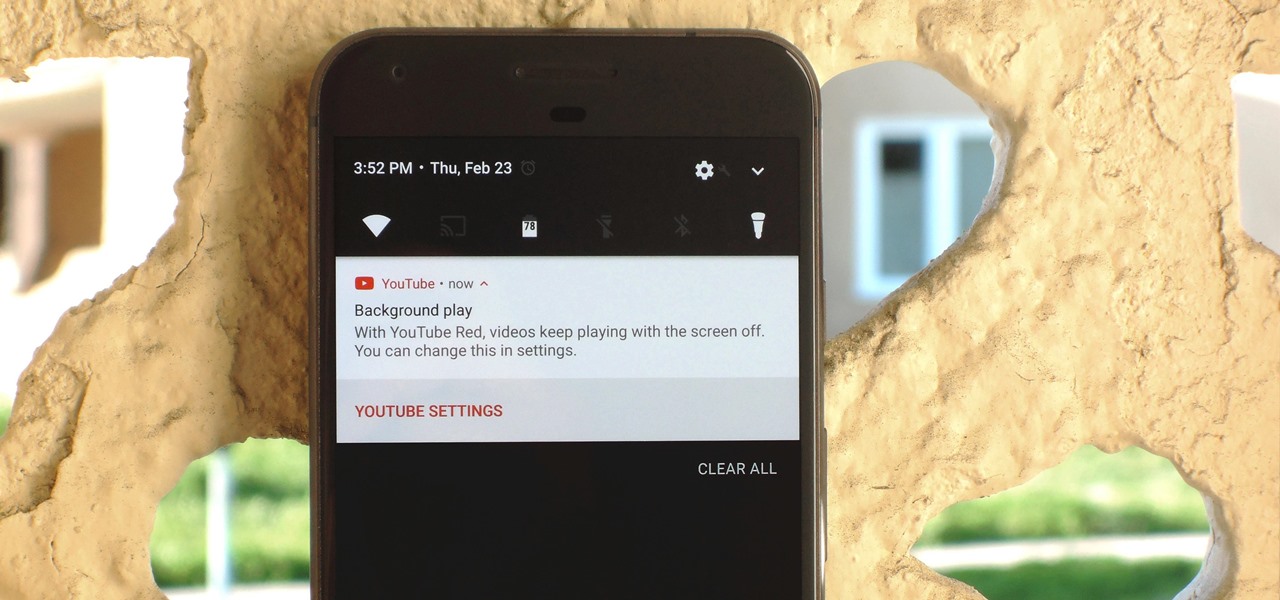
If you have the Xposed Framework installed, there's a module that lets you enable background playback in Android's YouTube app without buying a YouTube Red subscription. But Xposed is not available on many devices—particularly those running Android Nougat—so this isn't an option for everyone.

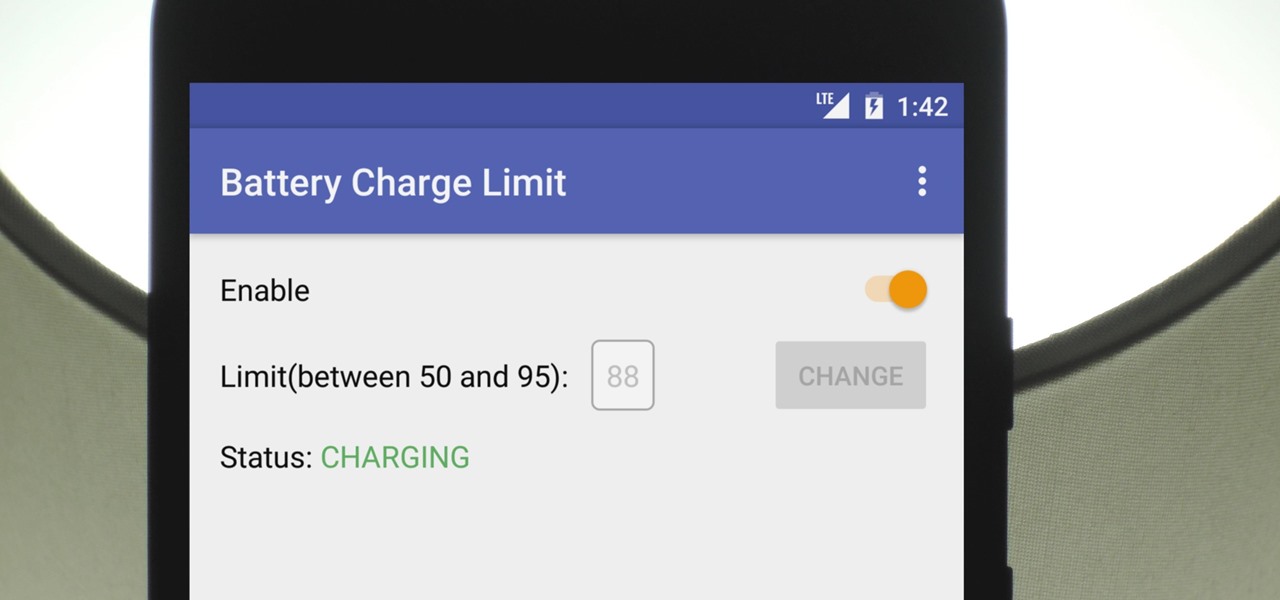
There's a lot of conflicting information out there when it comes to the best habits for charging a smartphone's battery, so let's clear some of that up right off the bat. Lithium ion batteries (the type used in most modern electronics) start to lose their ability to hold a charge over time, and the two biggest factors that contribute to this are excess heat and overcharging.

With the recent news that New York County's District Attorney's office is trying to get into over 400 locked iPhones for use in criminal investigations, you can see why it's important to keep other people away from your personal data. The fact that it can and will be used against you in a court of law is just one reason to protect your phone, because even if you make sure to stay above the fray, identity theft and bank fraud are still very real threats.

With some of the groundwork out of the way in getting a Mac set up for hacking, it's time to start looking at toolboxes. Our first toolbox is Git, which will be used throughout future tutorials.

Now that we've talked about encryption and managing your passwords, let's continue this series on getting your Mac ready for hacking by turning our attention to the terminal.

Google has already issued a few updates to Android 7.0 Nougat. There aren't many headlining features, as these minor updates are mostly bug fixes and performance improvements. But there's a few security enhancements as well, so staying up-to-date with the latest patches is important for a number of reasons.

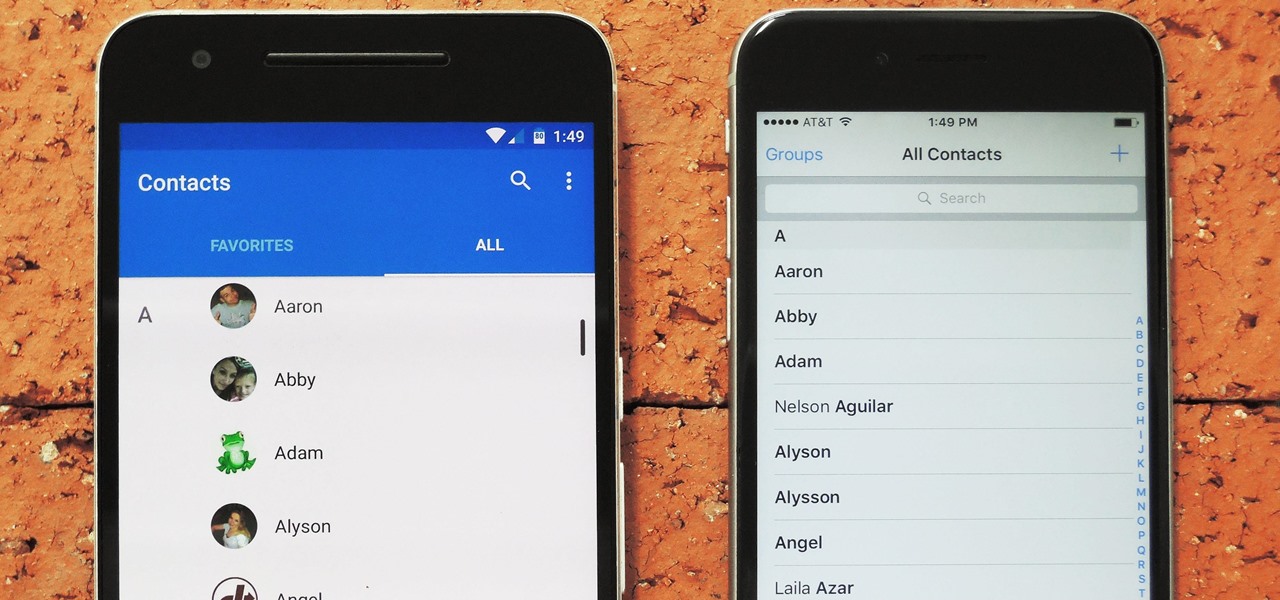
Switching between mobile operating systems is fairly easy, but there are a few bumps along the way that you're bound to encounter. One of the first issues you'll run into is that the contacts on your old iPhone don't easily sync with your new Android device.

Starting in Android 4.3, Google added some code to AOSP that tagged your internet traffic when you were running a mobile hotspot, which made it incredibly easy for carriers to block tethering if you didn't have it included in your plan. But as of Android 6.0, this "tether_dun_required" tag has been removed, which means you no longer have to edit a database file to get tethering up and running.