You may have lost your files but you needn't loose hope, too. In this episode of Lab Rats TV, Andy and Sean show you how to recover your deleted data (and your marriage!) using oranges. For detailed instructions on recovering your own lost data, take a look at this tech how-to.

This Windows XP video tutorial offers an explanation of how to use a little-utilized and known trick that gives you the power to rename multiple files both quickly and with ease. For more, or to get started batch renaming files yourself, take a look!
There are varied approaches to using SketchUp with CAD files. This video series presents one method we suggest as it is quick and creates a good clean SketchUp model.

Want to send a 100MB file via e-mail? How about 1GB? This how-to video can help you do it, and it will cost you nothing. Watch this helpful internet tutorial video to learn how to email large files for free.

This tutorial video will show you how to make an adorable greeting card that has a hole in the middle for storing files. this greeting card it great for any occasion and means so much more because it's hand made.

Watch this software tutorial video to learn how to quickly unzip archived files using the program WinZip. WinZip makes unzipping and unarchiving archived files quick and easy, and this how-to video provides helpful tips on how to use the program.

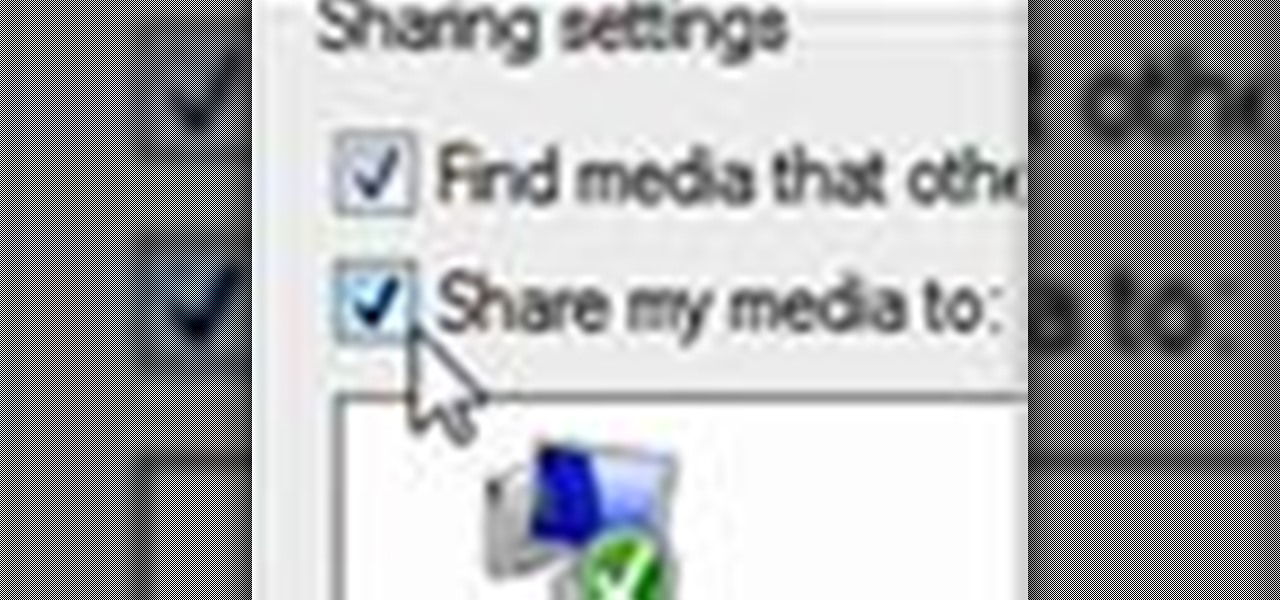
Using Windows Media Player, you can share files among a group of computers and easily access files regardless of where the media is stored. See how to share files in Media Player.

Working in Photoshop and not sure how to save your files? What ARE all those extensions and what exactly are the differences. Well, this video breaks it down so you'll know just how to save your precious work.

Is your hard drive filled to the brim but your not sure which files or file is hogging up all the space? Well check out jDisk for a visual representation of those space hogs.

How does Lightroom handle the process of going between itself and Photoshop? Where are the PSD files and what do we do with them? Check out this video and learn more about psds files and working with them in Lightroom.

Watch this video to learn an easy way to FTP (file transfer protocol) files using the Safari browser.

I show you a great way to take your beautiful .avi files and turn them into much smaller files that are great quality as well. And you don't have to buy extra software to do it!

Learn how to record audio from video files (even Flash .flv files or Youtube videos) using the Windows sound recorder. All of the software used in this tutorial comes bundled with Windows.

Are you tired of having a bunch of files on your computer that you cannot get rid of? Find out how to use Windows notepad to remove unwanted files from your pc.

Have you ever seen a DOCX file, and don't know how to open it? Or you have a DOCX file, and want to convert it? Watch Chris' video to find out more about DOCX now.

You have an assignment due, whether it's homework for school or a project for work, but you've only got a few hours left. There's no way you're going to finish in time and do a good job, and you don't want to turn in anything incomplete or half-assed. While it may seem you're out of luck, there's a simple way to buy yourself more time.

Getting files from an Android device to a Mac or iOS device is not always easy or convenient, and the same goes for transferring content from a Mac or iOS device to an Android device. But we're here to tell you there is a better way than using USB cables, email, and cloud storage, and it gives you the look and feel of AirDrop.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

Your phone is loaded with contacts you've collected over the years. They're an asset, and you should use your library of connections outside the confines of your mobile device. Luckily, your Pixel uses a standardized medium to store contacts that can be used by the likes of LinkedIn, Outlook, Hubspot, iCloud, and more.

The Files app was first introduced to the iPhone with the release of iOS 11. In the two years since its unveiling, we've enjoyed a more desktop-class experience since there's finally a decent file manager for mobile devices. That said, there was always one major issue with the Files app, an issue iOS 13 solves for good.

To make its services more accessible to regions with limited bandwidth, Spotify has rolled out with a leaner, stripped down version of its music streaming app. The aptly named Spotify Lite has been released for Android devices in 36 countries in Africa, Asia, and Latin America, but you can try out the app right now thanks to a simple workaround.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

There once was a time in the Android rooting scene where we couldn't rely on using a custom recovery for all of our modding needs. Manual file flashing was very popular in the early days of Android before custom recoveries started taking over. With the rise of TWRP, it seemed like there was almost no need for manual file flashers; however, they appear to be making a welcomed return in a big way.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

With the macOS stager created and the attacker's system hosting the Empire listener, the malicious AppleScript can be designed and disguised to appear as a legitimate PDF using a few Unicode and icon manipulation tricks.

Any internet user will need to download files eventually, and most simply have faith that what they are downloading is trustworthy. This doesn't give much clarity into the contents of the file, but if the file's author published the original checksum, comparing it to the SHA-256 hash of the downloaded file can ensure nothing was tampered with.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

Despite concerns with SafetyNet, Google actually cares about root. Every phone they sell has an unlockable bootloader, so you can toggle a setting and send a Fastboot command, then start flashing custom firmware right away. The Pixel 2 and Pixel 2 XL continue this tradition, and now they have an official root method.

Steganography is the art of hiding information in plain sight, and in this tutorial, I'll show you how to use Steghide — a very simple command line tool to do just that. In addition, I'll go over a bit of conceptual background to help you understand what's going on behind the scenes. This is a tool that's simple, configurable, and only takes a few seconds to hide information in many file types.

After laying off 40% of its staff this month to cut costs, SoundCloud appears to be struggling to stay afloat. While blog posts from the company have assured fans that the music platform is not in danger of shutting down, some people aren't so sure this is the truth. Internet Archive — a non-profit dedicated to preserving websites and services — announced today that they will be conducting a partial backup of SoundCloud to safeguard the site's content in case of closure.

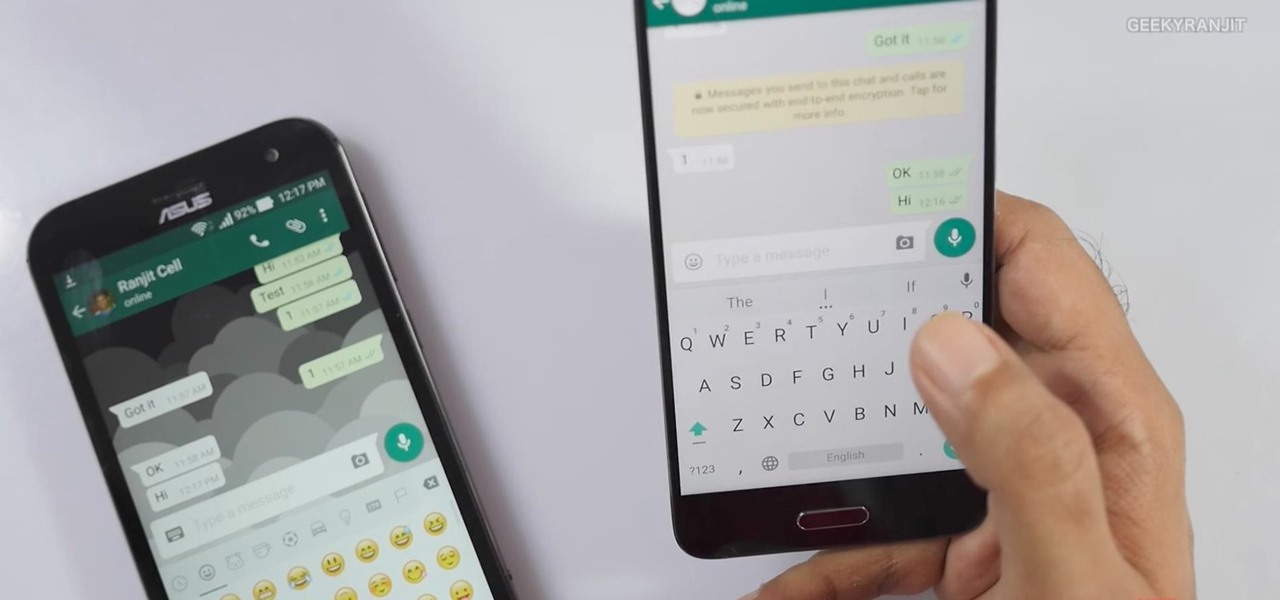
Cell phones have advanced rapidly since their inception. However, one frustrating aspect of our handheld computers is that we sometimes expect more than they can handle. We want smartphones to do all our PCs can do, but in many cases, that just isn't possible; especially when that comes to viewing and sending certain file types. WhatsApp is taking steps to bridge that gap now, by allowing users to send whatever kind of file they want, with one or two restrictions ...

The internet's an amazing place. The entirety of human knowledge is now accessible in an instant, and all sorts of media can be streamed directly to the palm of your hand. But, of course, that also includes the darker side of humanity, so there's plenty of NSFW content floating around out there that's certainly not suitable for children.

Sometimes you need a password to gain access to an older running Windows system. Maybe it's a machine in your basement you forgot about or a locked machine that belonged to a disgruntled employee. Maybe you just want to try out your pentesting skills.

Backdoors are convenient to leave behind once you've already found a way into a server, and they can come in handy for a variety of reasons. They're good for developers who want a quick way into machines they're working on, or for systems administrators who want similar access. Of course, backdoors are also a hacker's best friend, and can be added in a variety of ways. One good tool for doing this is Weevely, which uses a snippet of PHP code.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.