If you're completely new to Android, you're in for a treat with all of the software tweaks and customization options that your smartphone or tablet offers out of the box. But if you really want to take things to the next level, the ability to mod your device expands exponentially when you're rooted.
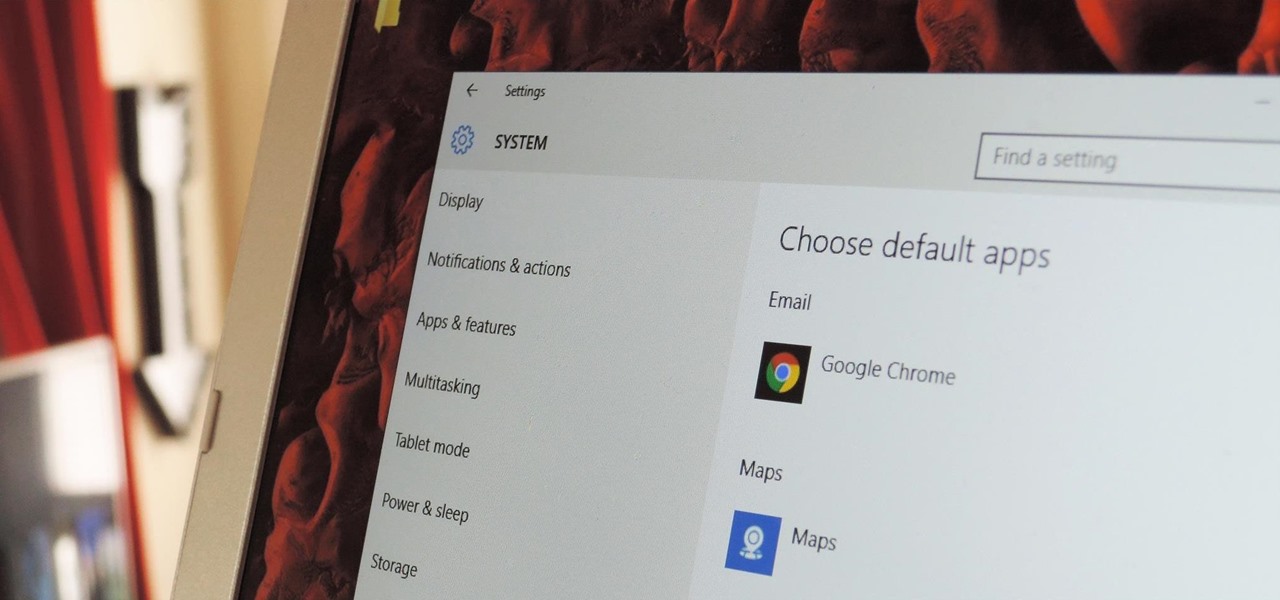
The first time you launch any type of file, Windows 10 will usually prompt you to select an app to open it with. Occasionally, though, this "Open with..." screen doesn't show up, and instead Windows will use a pre-installed system app to launch the file without ever giving you a choice in the matter.
Microsoft's Windows 10 has proven to be a solid release by Microsoft, with faster adoption rates than its predecessor builds. The seamless integration of cloud services and tweaks both major and minor make using Windows easier than ever now. And it's almost enough to forget you ever used Windows Vista... almost.

Welcome back, my budding hackers! In this series, we are trying to understand how AV software works so that we can learn to evade it. To that end, we are working with the open-source AV software, ClamAV. I had previously introduced ClamAV in Part 2 of this series. If you have not installed it yet, go back to that and install it.

Hello fellows nullbyters, first of i will start saying that im addicted to this community, i feel the challenge growing up so fast, all the newbies, amateurs,advanced and professionals hackers around trying their best to help the community, badly but we got some script-kids too but anyway, today we are going to learn how to install and use clanAV in kali linux.. INTRODUCTION

Android Beam is one of those features that makes you look at technology in awe, wondering how exactly something like that works.

In the second part of this tutorial, we are going to crack the hashes that we've captured previously. I'm going to explain how to do it with the powerful John the Ripper. It comes with Kali by default, so no need to install!

You always wanted to make an undetected payload and make it look legit, Well this is what this tutorial is about, You're going to learn how to backdoor any (Unfortunately only 32-Bit) software, Let's get into it

OneDrive, formerly known as SkyDrive, is a free online storage solution developed by Microsoft. If you're a fan of using cloud-based storage systems, then OneDrive offers you plenty of benefits. It's also heavily integrated into Windows 10, including the new File Explorer, in an effort to make utilizing OneDrive easier for you.

If you've switched ROMs before or flashed quick mods on your Android device, you've probably used TWRP or another custom recovery to install them. But another great purpose for flashing through a recovery is to install your own custom .zip file filled with everything a fresh ROM needs—namely, all your apps.

It's official: The next version of Android will be code-named "Marshmallow," and we're getting a whole number bump to version 6.0. Lots of exciting new changes are coming to the world's most popular operating system, including a "Now on Tap" feature that will give you relevant information about any screen at the press of a button.

Windows 10 marks a new era for Microsoft with the return of the Start menu, the demise of Internet Explorer, and the introduction of the remodeled Windows Store.

As the Insider Preview builds of Windows 10 progressed, certain features were removed as new ones joined the fray. Some came back, while others disappeared, seemingly for good. One feature that seems to have been removed are the colored title bars on app windows.

Firstly let me start by giving credit to Lucid for their guide on Evilzone which inspired this idea, as well as the recent talk of anonymity on here.

When we hack a web server, we usually want to be able to control it in order to download files or further exploit it. There are many websites that let you upload files such as avatar pictures that don't take the proper security measures. In this series, I will be showing you how to gain root access to such a web server.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

Mobile service providers have an uncomfortably strong grip on the Android platform as a whole. For instance, all four U.S. versions of the Galaxy S6 and S6 Edge play their carrier's obnoxious jingle every time they boot up. You don't get any say in the matter—if you buy your phone from one of the big 4, you're a walking audible billboard.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Technology has progressed by leaps and bounds and has blessed people in a number of ways, but at the same time, it has troubled them also. Computers are now used in every aspect of life. No matter if you are a businessman, an employee, a student, or even a housewife, a computer can assist you in your routine work. You save your personal information, documents, and other similar sensitive stuff on your computer that can hurt you if they get compromised.

Part 1: What is Popcorn Time? Part 2: What is a torrent?

While you may not have loads of secret files hiding on your computer, there might be one or two items that need a little extra security, like a file of website logins or a folder of risqué photos.

With the sheer amount of photos, videos, and miscellaneous files we place on our computers, proper organization becomes necessary. Not only so that we can quickly get to a file when it's needed, but also to declutter folders and keep them from looking like random file dumps.

Does your Samsung Galaxy Note 3 feel slower than it used to? Background processes, cached files, malicious applications, and buggy updates can all lead to a sluggish smartphone. It's just what happens over time.

Android 5.0 "Lollipop" has only existed for a few months, but a leaked version of Samsung's take on the firmware has already been spotted in the wild. This update came straight from Samsung, and brings with it a plethora of new features, including greatly improved performance and a revamped TouchWiz UI.

Blizzard Entertainment, the wildly successful video game developer that brought us World of Warcraft and StarCraft, has finally released their popular trading card game Hearthstone: Heroes of Warcraft to the Android platform.

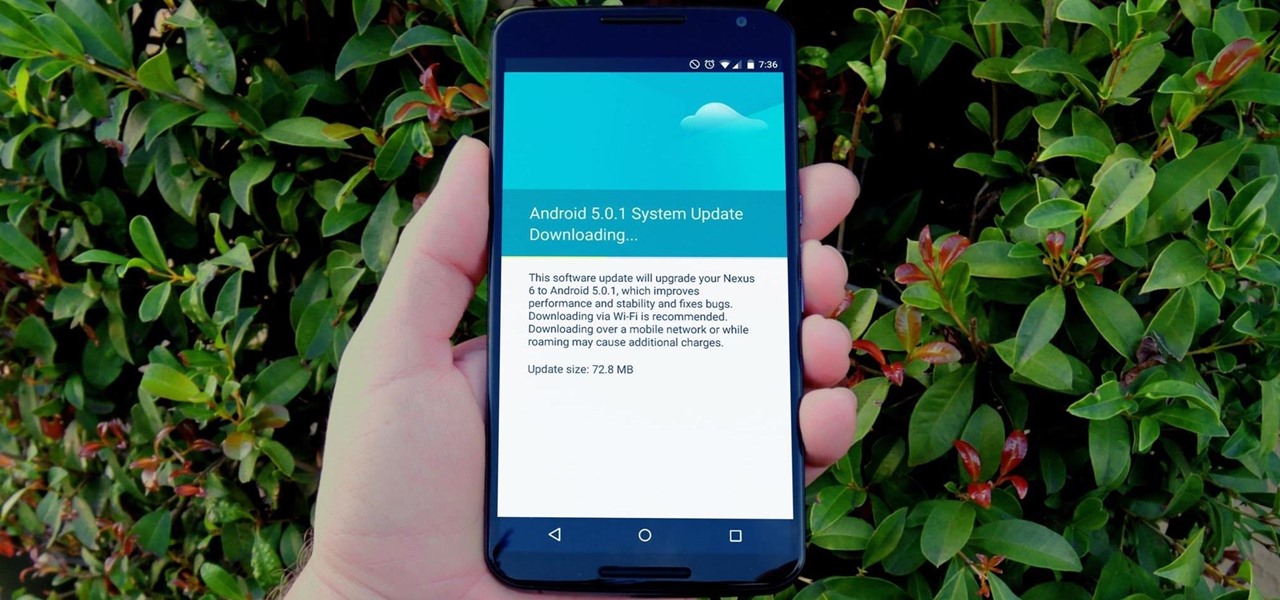
One of the main reasons to buy a Nexus device is the fact that they're always the first to get new Android updates. Another great selling point for the Nexus series is that the devices are amongst the easiest to root and mod. Unfortunately, though, these two features are somewhat mutually exclusive.

One of the more talked-about features of Google's new flagship device is the fact that all of the data on the Nexus 6 is encrypted by default. At face value, this certainly seems like an added bonus for the 6-inch phablet, especially in this day and age with growing security concerns abound. It's definitely something that the FBI is none too pleased about.

Using a combination of my phone, laptop, and an arsenal of apps and plugins, I can send pretty much anything to my Chromecast. However, nothing is ever perfect, and the file type that was still giving me headaches were torrent and magnet files.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

Whenever a new Android device is realized, the first thing I figure out how to do is to get it root access. Generally speaking, rooting has never been easier, with many one-touch methods like Stump and Towelroot available. But as manufacturers and carriers increase security with each new product, there is one tried-and-true root method that continues to work on most Samsung devices—Chainfire's CF Auto Root.

Keeping a close eye on your device storage can be a 24/7 job, especially if you're space is filling up and your device doesn't have SD card support. No matter how close of an eye you keep on it, there are always going to be apps updating databases, adding to their cache, and deleting old files.

Since the release of the Galaxy S5 back in April, the process of converting older models, like the Galaxy S4, to replicate the look and feel of the newest S-family member was inevitable. Galaxy users didn't want to be left out, and for good reason. The revamped interface of the S5 introduced a new color palette that was a definite improvement from the flat boring colors on older models.

As carriers finalize their variations of the Android 4.4.4 update, we're left with only brief glimpses of what the new "Eye Experience" holds in store for us while we wait. However, thanks to a system dump of an updated European HTC One M8 and some clever hackery by donmarkoni, we can now install the new camera app on any variant of the HTC One M8.

There are many different reasons that you might want to revert your Samsung Galaxy S5 back to stock. The main one would probably be that you need to return your device to the manufacturer for warranty purposes. And if you've used root to modify system-level files and components, you'll need to undo those changes before you send the phone back.

Welcome back, my aspiring hackers! Many of you have installed Kali Linux as a virtual machine (VM) using VMware or VirtualBox, while others have installed Kali (or BackTrack) in a dual-boot system. The drawback to installing these hacking systems as a VM is that it then requires an external wireless adapter (your wireless adapter is piped through the VM as a wired device, eth0), but it makes for a great place to test your hacks while honing your skills.

Transition animations are an essential element of any mobile operating system. They give the user a sense of what's happening on the screen, where the apps are coming from, and where they're going.

I'll give Samsung credit where it's due—the stock keyboard on the Galaxy S5 is actually pretty nice. There's a dedicated number row that resides at the top (something that the Google Keyboard needs a hack to achieve), and various settings exist to make switching between languages a breeze.

Now most of the free email providers allow upto 25 MB of file attachment. But we need more. This video will help you how to send or transfer big files upto 2GB over internet without any cost. Watch the video and follow all the steps to do it yourself.

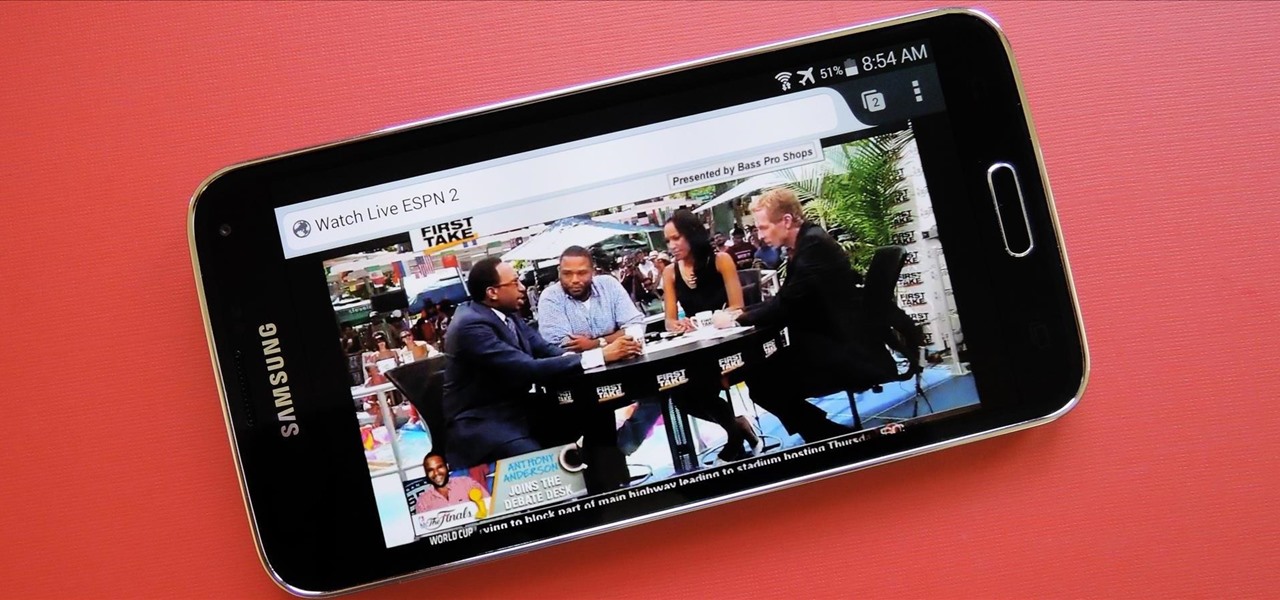
Over the course of the past few years, many websites have begun offering up a mobile-friendly HTML 5 version of their content. Videos that once required Adobe's Flash can now be played on any modern mobile web browser.

It used to be easy to hack tethering—root your device and install a third-party or modded tethering app. But snuck in amongst the changes in Android 4.3, a new data-monitoring service of sorts made its debut. There used to be a time when your data connection was yours. You paid for it, so you were free to use it for whatever you wanted. Unfortunately, those days are long gone.