Google Meet might not have virtual backgrounds like Zoom, but it hits all of the other basics, from hosting many multiples of video participants to sharing your screen, that you'd expect from a robust video conferencing platform.
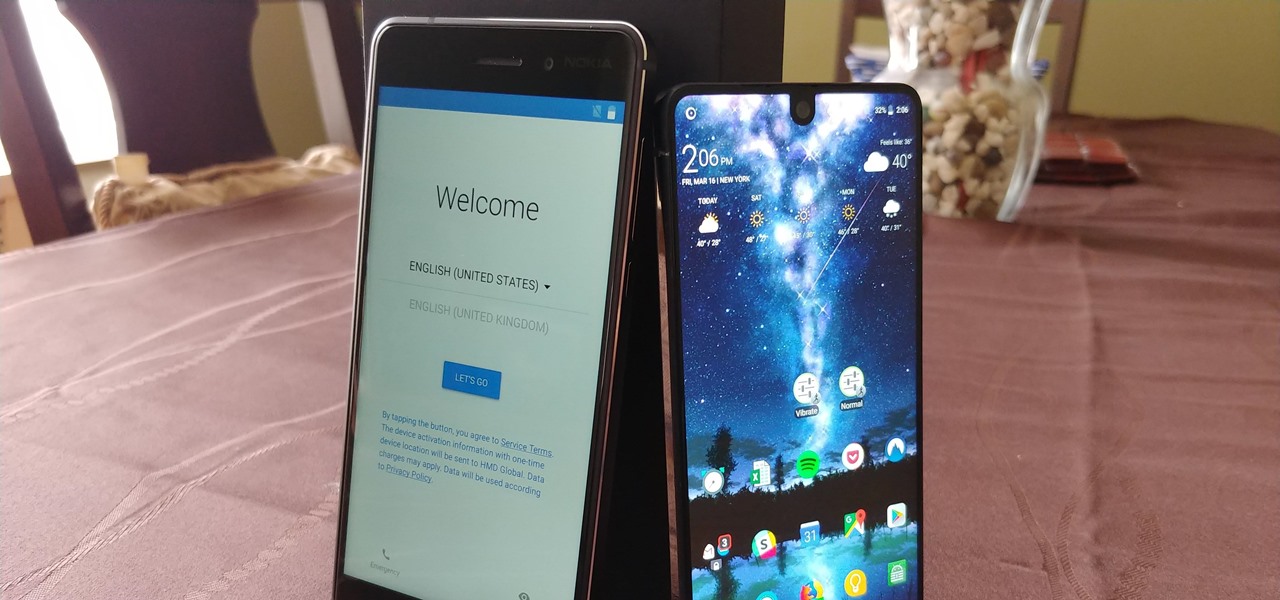
In the past, if you upgraded to a new Galaxy or if you had to factory reset your existing one to fix an issue, you had to restore your home screen layout manually. Your wallpaper, widgets, icon placement, and launcher settings were all dependent on you to be put back in their place. Thankfully, this isn't an issue anymore.

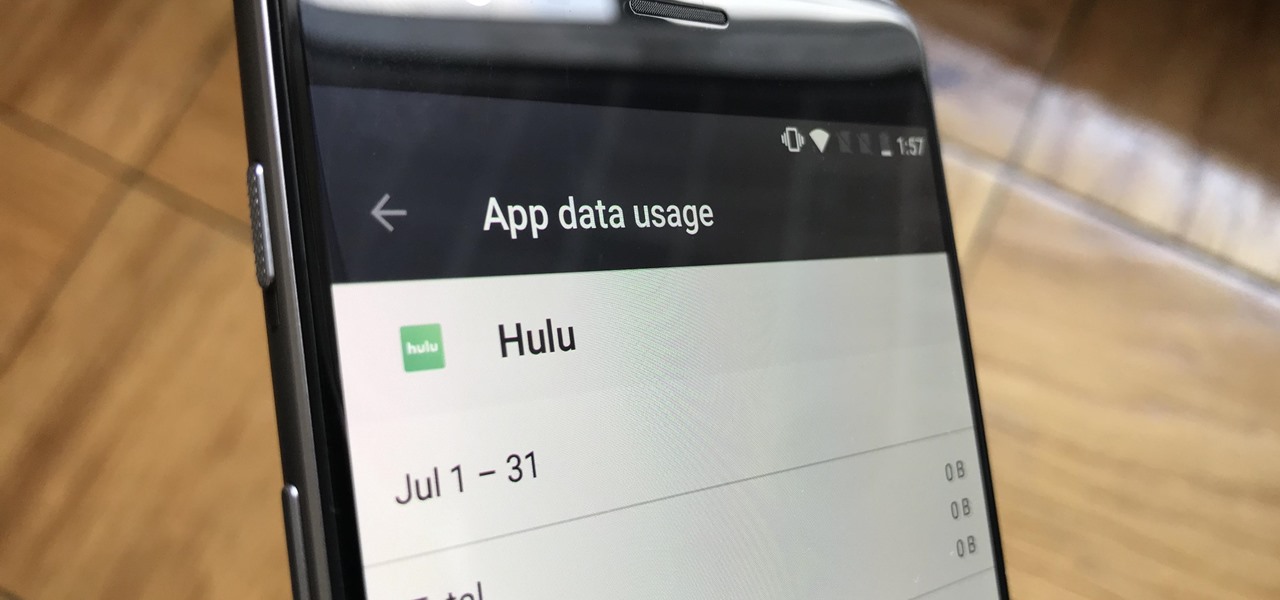
Without an available browser, it is challenging to enjoy media on your Nvidia Shield outside of the apps on the Play Store. It is because of this limitation that file transferring is vital, as only then can you enjoy your movies and music.
I recently picked up a Pixel Slate when Google had a deal going on. I'd been in the market for an Android tablet since the Nexus 7, and this was the closest thing to it. Unfortunately, I soon learned Chrome OS and Android aren't as integrated as I had hoped.
In the iOS 13.4 update, Apple added folder-sharing capabilities in the Files app. That means you can share multiple documents at the same time instead of doing it one by one. But that's not all — you can share folders with numerous contacts and even enforce access and permission settings.

Android 11 won't be available as a beta update for Pixel devices until May 2020. Until then, the only way to try the latest Android version is by manually installing it. Usually, this means carrier models are left out since their bootloaders are locked, but there's still a way to get it done.

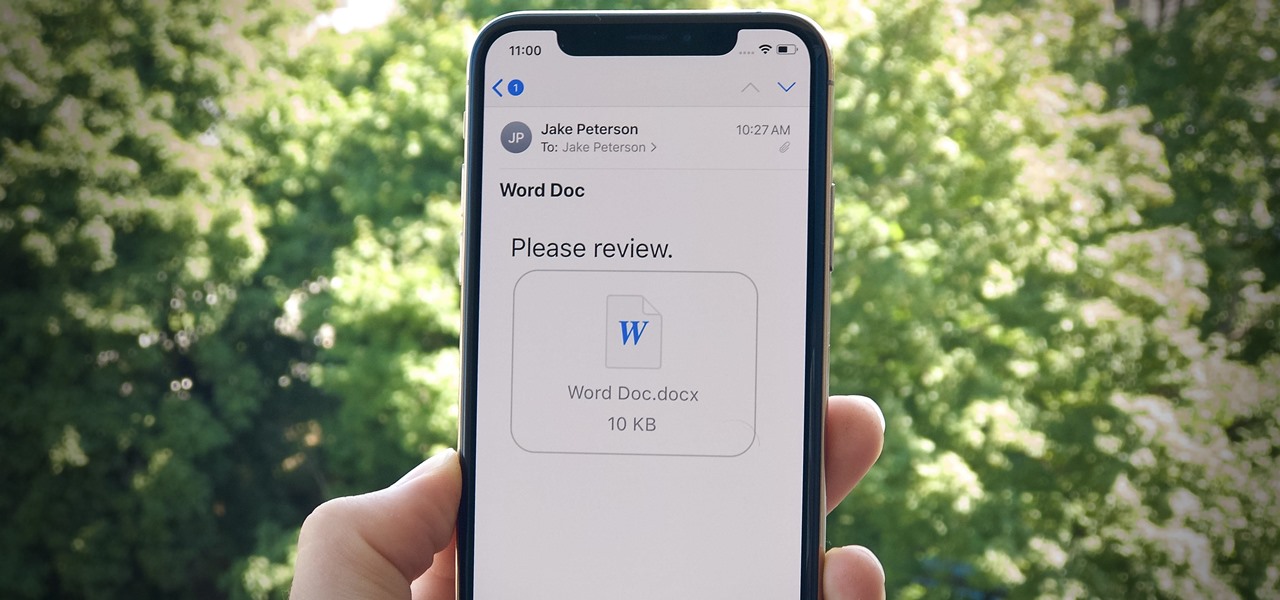
There's no doubt that Microsoft Word is the go-to for businesses worldwide. As such, you might receive Word documents to open on your iPhone, whether or not you actually have Word for iOS installed. If you prefer editing text documents with Pages, Apple's own word processor, you can import and export Word docs easily.

Although Mail didn't get a massive update in iOS 13, the new formatting and attachments toolbar makes it easier to stylize your messages and get quick access to files you'd like to send. It even includes the excellent document scanner built into iOS, so you can use your iPhone to turn a physical document into a PDF and attach it to your message — all from within the Mail app directly.

OnePlus has purposefully made their devices easy to root so that you can spend less time waiting and more time doing. These phones are a solid choice for anyone looking to dive into the rooting and modding scene. Using the same principles that Google has with the Pixel line, you can always be sure your OnePlus 7 Pro will get first-class treatment from launch day and beyond.

Metadata contained in images and other files can give away a lot more information than the average user might think. By tricking a target into sending a photo containing GPS coordinates and additional information, a hacker can learn where a mark lives or works simply by extracting the Exif data hidden inside the image file.

The Pixel 3a came out of nowhere and flexed its muscles to show the industry that you can have a great phone without a hefty price tag. Since Pixel smartphones are first-party devices straight from Google, you can be sure you'll have root access one way or another. For right now the method used to get your Pixel 3a rooted will take a few steps, but they go by real quick.

Every model iPhone since the 6s has boasted a 12-megapixel rear camera. You can take some pretty spectacular, professional-looking photos with it, especially on devices that have more than one rear lens. But the file size of each photo can become a problem when sending as an iMessage, which can eat up data.

Like last year's beta release of Android Pie, Google has allowed the Android Q Developer Previews to support some non-Pixel devices. Announced at Google I/O 2019, there are 15 non-Pixel smartphones eligible for the Android 10 Beta, including 2017's Essential PH-1.

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

Microsoft Office files can be password-protected in order to prevent tampering and ensure data integrity. But password-protected documents from earlier versions of Office are susceptible to having their hashes extracted with a simple program called office2john. Those extracted hashes can then be cracked using John the Ripper and Hashcat.

Switching phones has never been easier. Google backs up most of your app data on the cloud, which can then be restored onto your new phone. Sadly, Signal doesn't use this feature since it could compromise your security. Instead, Signal stores encrypted backups locally, requiring a bit of work to restore these messages.

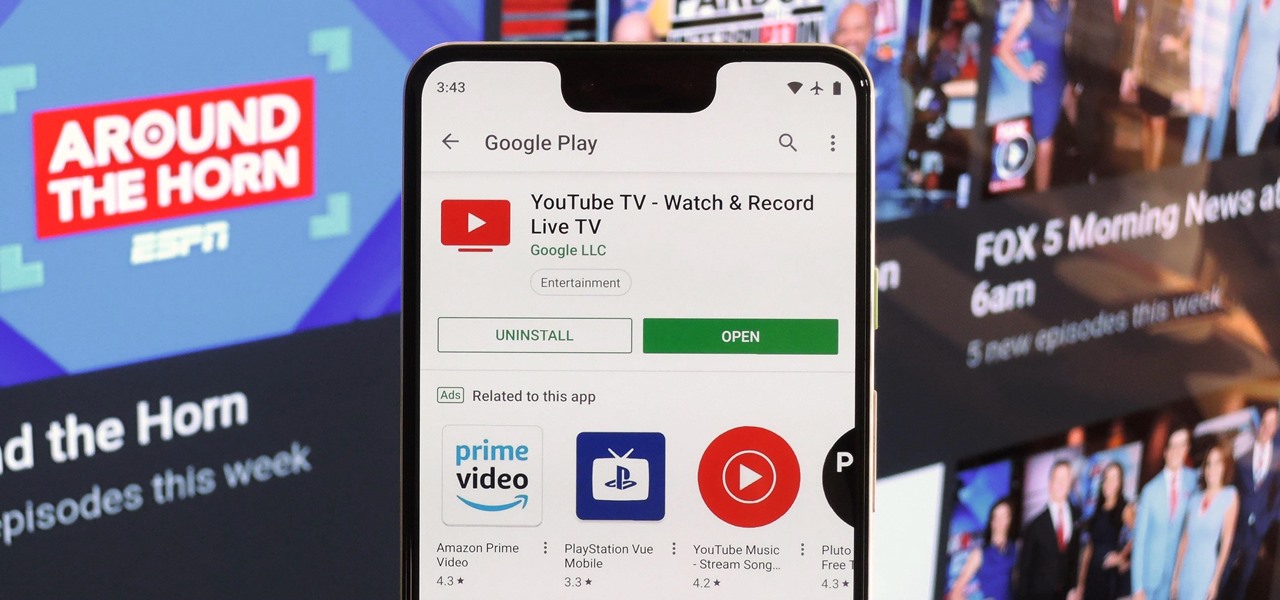
With YouTube TV and DirecTV Now starting at $40/month, and others like Sling TV offering an eye-catching $25/month plan, streaming cable services may sound like a great way to cut costs while cutting the cord. But when you look at all the factors, the price you pay may very well end up being just as high as your traditional cable bill — if not more.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

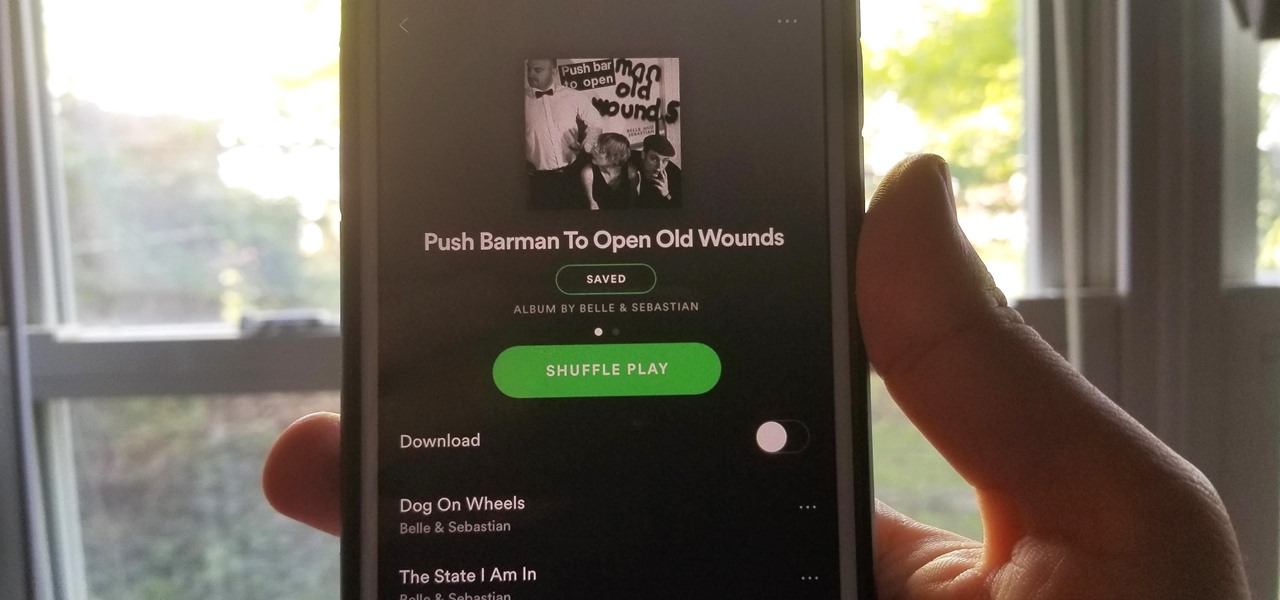
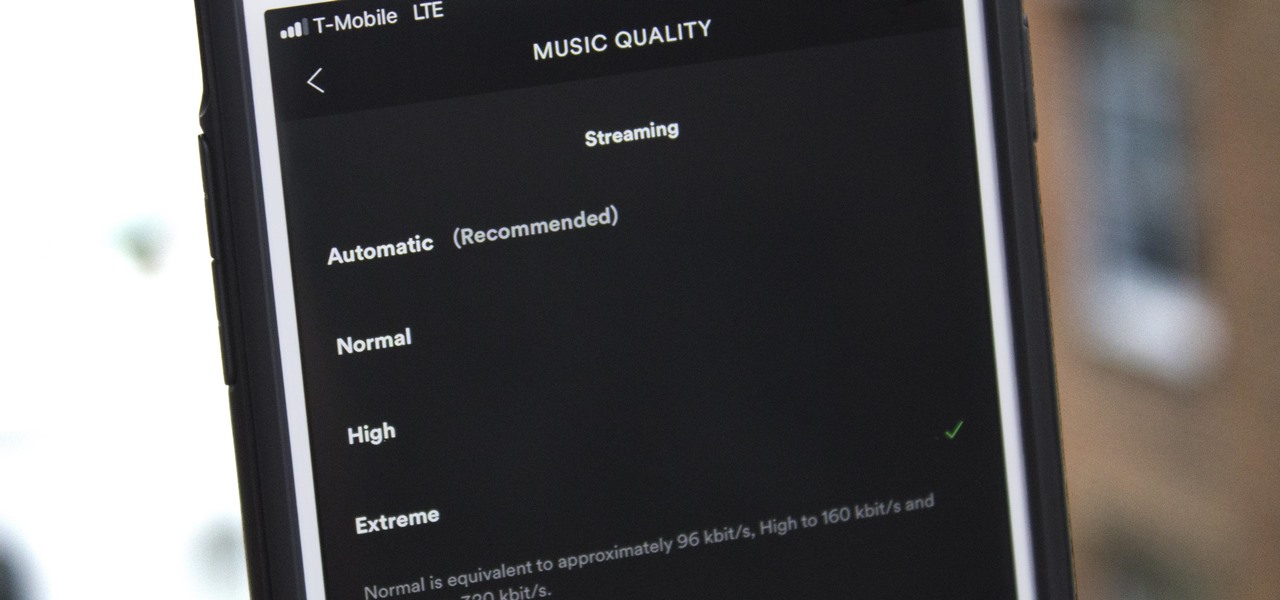
While I love Spotify, I don't like it devouring my data plan when streaming music away from a Wi-Fi network. If you have the foresight or time to download Spotify tracks for offline playback later, great. For those of you who like to listen to your music more randomly like I do, based on your current mood, streaming is the only way to go, and there are settings you can tweak to use up less data.

Setting up a new Android phone can be a pain. Although Google has some automated features, it does not restore everything. When it comes to transferring certain types of data like files and SMS logs, it's even trickier. By following our steps, you can be sure that you all your data will follow you to your new device.

The legal travails of Magic Leap appear to have no end in sight, as a lawsuit filed by an ex-employee further threatens to dampen the startup's 2018 launch.

For the past few months, Fortnite has been one of the most-watched games on Twitch, and it's likely to keep a top spot on the live streaming platform once Fortnite Battle Royale becomes available for smartphones. While there are not any live streaming capabilities built directly into Epic's mobile version of the game, you can still live stream Battle Royale gameplay from your iPhone to Twitch.

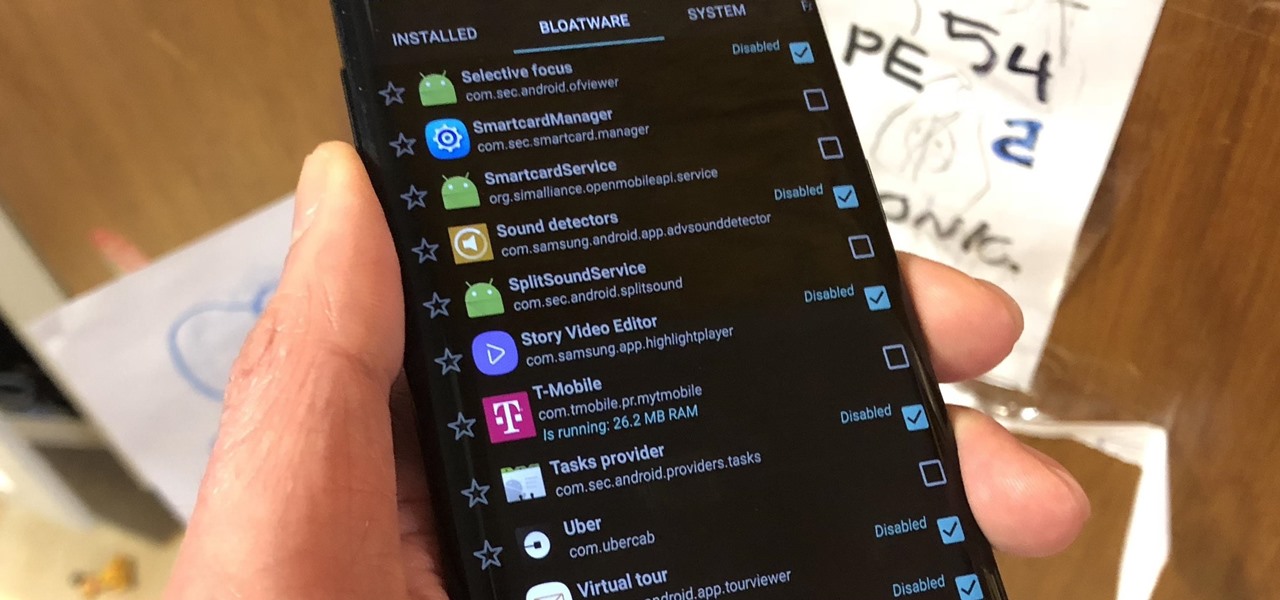
Carrier-branded Galaxy S9 models come with a ton of bloatware that you usually can't get rid of without rooting. With a little digital elbow grease, however, there is a way to disable bloatware on your S9 or S9+, and it's a lot safer that attempting to root and modify you precious device.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

It seems almost every carrier now has an unlimited data plan, and free Wi-Fi is now available in more places than ever before. If you want to be connected, it has never been easier — but that still doesn't mean that everyone can stream as much as they please.

Spotify's massive song catalog can be streamed in decent quality on iPhone or Android without any tinkering. But if you're an audiophile, you've probably noticed that the sound quality can fluctuate from time to time.

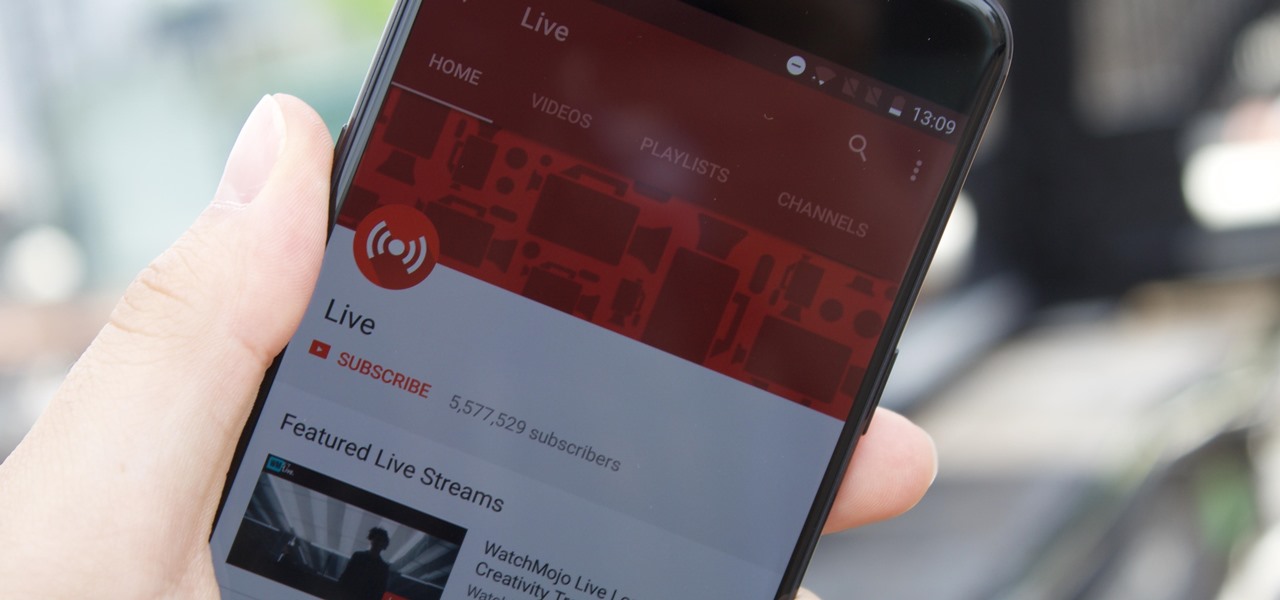
YouTube's mobile live streaming feature is great for connecting with your audience in a more personal way than traditional videos provide. Audiences can view and respond to content in real time, and creators can do the same. While unfortunately not available to everyone — you need at least 100 subscribers — live streaming is possible, even with your smartphone.

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.

Carrier-branded Galaxy S8 models come with a ton of bloatware that you usually can't get rid of without rooting. If you dig a little deeper, however, there is a way to debloat your S8, and it's relatively hassle-free.

Jailbreaking gives iPhone users almost unfettered access to their devices, offering a slew of customizations, new features, and improved apps that you just can't get elsewise. Unfortunately, Apple has clamped down hard on the latest iterations of iOS, making jailbreaking extremely unstable at best. Hope is not lost, however, as there's still a way to install modded and unofficial apps on your iPhone, iPad, or iPod touch without any jailbreak.

There are two things you're not supposed to talk about in a social setting: religion and politics. When it comes to the latter, though, a certain orange-hued reality TV star has made it all but impossible to stay mum about the goings-on in DC.

Now that we've talked about encryption and managing your passwords, let's continue this series on getting your Mac ready for hacking by turning our attention to the terminal.

Counter-Strike is one of the most popular first-person shooters of all time, and deservedly so. What originally started out as a third-party Half-Life mod garnered such a cult following that Valve had to hire the developers and purchase the intellectual property to make it an official standalone release.
Hello, I'm a new guy around here and since I'm not seeing much tutorials in C i thought of contributing with something relatively simple. This will be a short series.

It's been a while since I wrote up an article for this series but I did say that I'd be covering some WinAPI. So if you're interested in programming for the Windows platform, hop aboard and follow along.

Welcome back, my tenderfoot hackers! As you should know from before, Snort is the most widely deployed intrusion detection system (IDS) in the world, and every hacker and IT security professional should be familiar with it. Hackers need to understand it for evasion, and IT security professionals to prevent intrusions. So a basic understanding of this ubiquitous IDS is crucial.

Google is rolling out an update for Google Drive that streamlines the online file storage/sharing app, and finally gives you access to the Trash folder that had only been available on the desktop version.