Android's new Material Design language is truly a thing of beauty. Slated to make a full debut alongside the upcoming Android "L" release, the vision and simplicity of this UX design recently won Gold Prize at the annual User Experience Awards.

With recent security breaches in the news, there is no better time than the present to make sure you know exactly what's happening on your device.

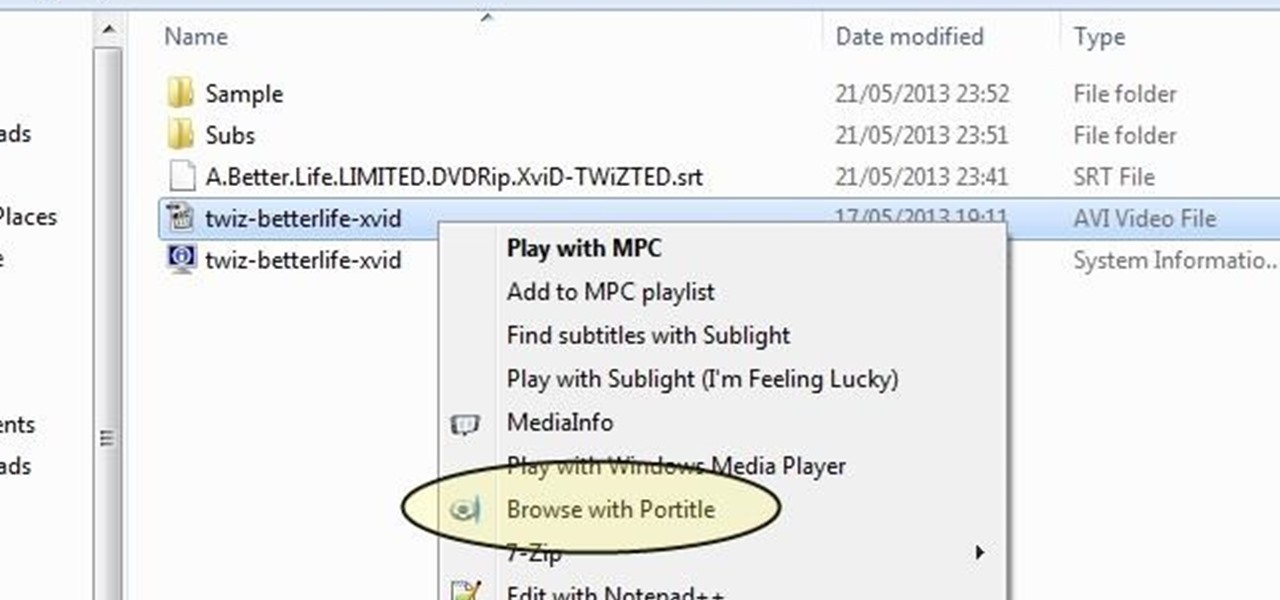
If you have a custom recovery installed on your Nexus 5, you're able to flash custom ROMs and lots of other cool Gadget Hacks. But when it comes time to receive and Over-the-Air (OTA) update directly from Google, having a custom recovery installed can be a fairly big hindrance—and for the upcoming Android L release, you're going to want to alleviate that.
This is a video that I created for teaching you(the viewer) how to batch unrar, unzip, or extract a lot of files at a time but I do it in rap form. I know it sounds weird but I still hope you like it.

Welcome back, my greenhorn hackers! Continuing with my series on how to crack passwords, I now want to introduce you to one of the newest and best designed password crackers out there—hashcat. The beauty of hashcat is in its design, which focuses on speed and versatility. It enables us to crack multiple types of hashes, in multiple ways, very fast.
While Google would like you to believe that Flash is incompatible on Android KitKat, there is a functional workaround that will get it up and running on your Samsung Galaxy Note 3's gorgeous screen in no time.

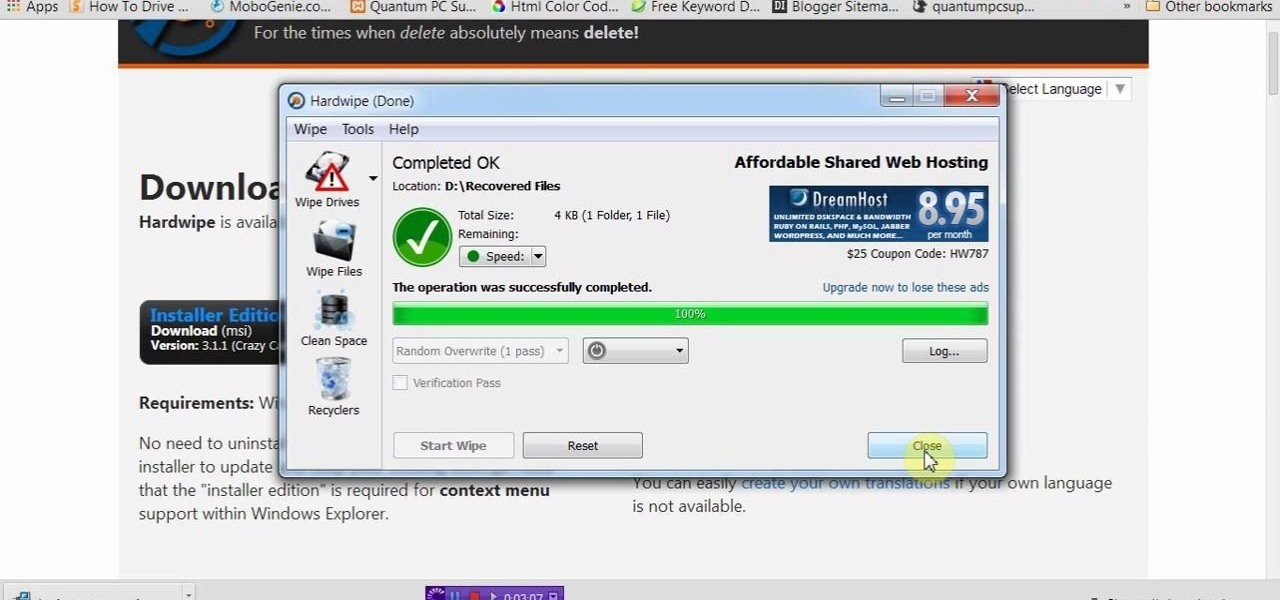
If you delete data by using Hardwipe tool, then it can't be regained by any means. The file or data will be deleted permanently. Watch the video and follow all the steps carefully. Employ the technique in your own PC.

The release of the Nexus 5 marked the debut of the Google Now Launcher. Even with an integrated Google Now page on your home screen, the most talked-about feature was actually the always-listening functionality.

I dabble in video editing, and when working on even the shortest of motion graphics clips, the exported files take up quite a bit of space. For all of you heavy Mac users out there, I'm sure you know my pain.

Windows XP will always have a special place in my heart—it's the operating system I grew up on. It guided me through the glory days of AIM, Napster, and MySpace, but now it's dead. The OS that had been supported by Microsoft for twelve years officially lost its support on April 8th, 2014. Just like that, Microsoft has killed the beast, but for those of you who stubbornly refuse to cooperate, you can resurrect the dead. If you have Windows XP, this little known hack will get you further suppor...

Yesterday, I wanted to remove BackTrack from my system and install Kali, and at the same time didn't want to damage my Windows 7 or my hard drive. I searched a lot of articles, but almost all of them wanted me to have a backup Windows 7 CD, which I don't possess.

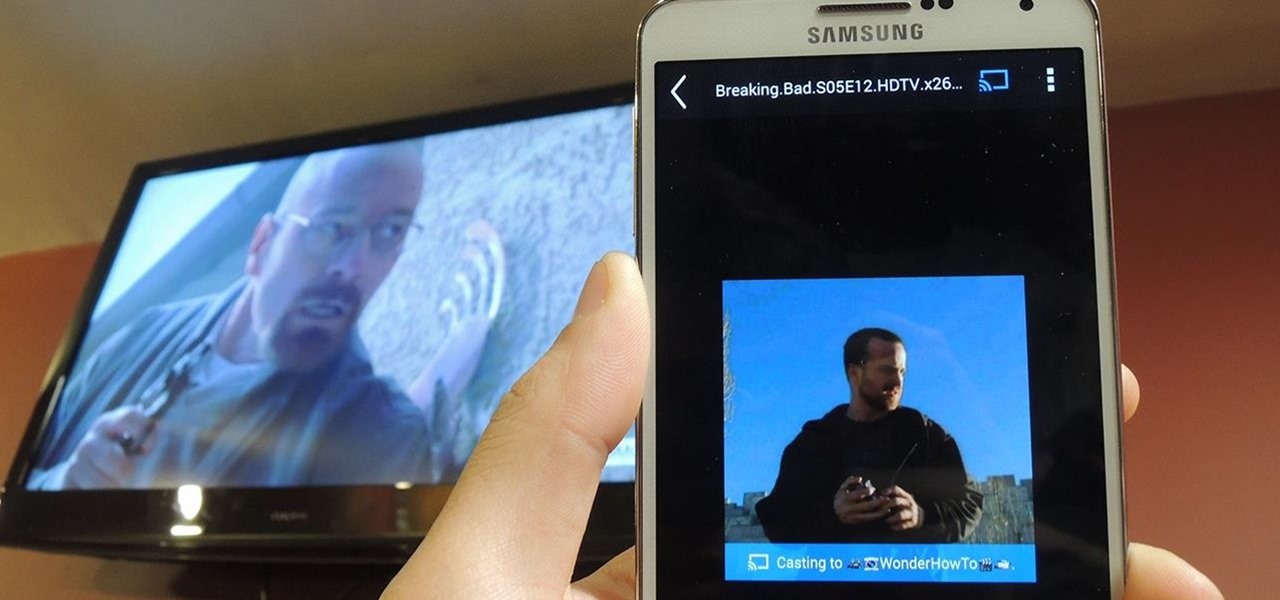
Recently, Google unleashed the Chromecast development kit, which lets developers add Chromecast streaming functionality to their own apps. However, there aren't many apps with Chromecast capabilities yet, and big companies and devs are still working on polishing their final products.

The flexibility within Android is pretty amazing. Unlike iOS, you can make a lot of modifications with nothing more than a download from Google Play, but to really step up your softModder game, you'll need to go a little further.

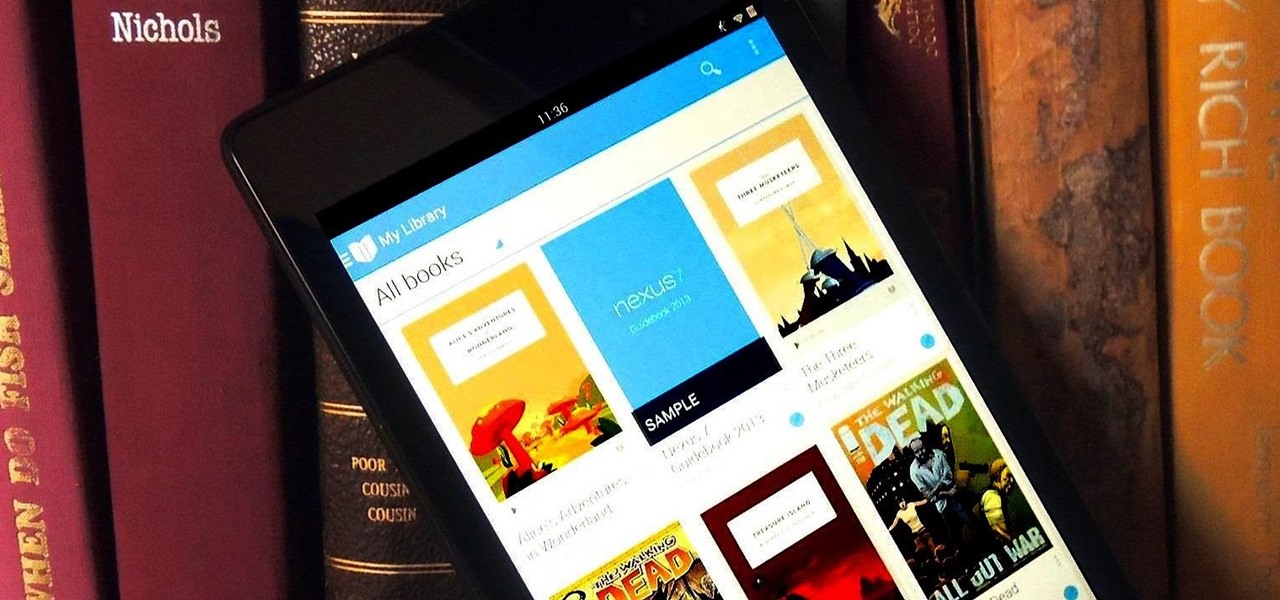
You've got a brand new Nexus 7 tablet for Christmas, and you're extremely eager to start using it. There are many things you can do with it, like shake for new wallpapers, get rounded screen corners, and make it help you fall asleep at night. But, before you get into softModding your Nexus 7, you should know the basics, and if you've come over from a Kindle, turning your new Android tablet into a powerful eReader is a must.

If you're marginally inclined towards computers, you've probably been approached at some point by a family member who wants you to "fix" their system during a visit home. With the holidays coming up, these opportunities (or ambushes) are even more likely.

It's officially the holiday season, which means everyone will soon be traveling home to spend time with loved ones. And anyone who has any knowledge whatsoever of computers knows what else that means—family members left and right asking you to fix their various technical woes.

Welcome back, my neophyte hackers! In today's hack, we're going to have a bit of Halloween fun. Have you ever had a boss who made you miserable with his micro-management and nagging? Maybe you thought he unfairly fired your friend/colleague? Well, now here's your chance to get a bit of revenge and keep him or her off your back!

Hello fellow peoples of the earth and welcome to another tutorial by me! Noah! you know popcap make bejewled blitz and zuma and pvz for facebook but what if you want the big games like pvz or bejewled 3 from them but don't want to pay. Then worry not as this simple tutorial will help you get those games you enjoy for free without any trials or limitations! to the startthetutorialmobile

Welcome back, my hacker novitiates! Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or service.

Welcome back, my fledgling hackers! Nearly every commercial enterprise worth hacking has an intrusion detection system (IDS). These network intrusion detection systems are designed to detect any malicious activity on the network. That means you!

In a previous softModder guide, I detailed how to get the Jelly Bean 4.2 Photo Sphere Camera and Gallery on your HTC One running Sense 5, but that was quickly outdated with the release of the new Google Play Edition HTC One, which has a newer Camera that works great with our hardware.

Understand the Problem of Couch Potatoes I have a lot of movies stored on my PC and when I have to finally have the time to watch something, I do not always remember which movie is which. So now I have to google for each movie with the keyboard or search in IMDB.

Sharing just got a whole lot easier in the new iOS 7. Apple has decided to integrate AirDrop, the local vicinity file-sharing service found in Mac OS X, into the latest version of iOS.

In my first tutorial on Linux basics, I discussed the importance of hackers using Linux and the structure of the directory system. We also looked briefly at the cd command. In this second Linux guide, I'll spend a bit more time with changing directories, listing directories, creating files and directories, and finally, getting help. Let's open up BackTrack and getting started learning more Linux for the aspiring hacker.

BitTorrent—corporations hate it with a passion, but the people love it. The notorious file-sharing protocol was responsible for 36.8% of all upstream Internet traffic last year, as well as 10.3% of all traffic.

It is typical to share video and files for those who are not friendly with windows 8. But with the help of this video you can share all which you want.

Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly all of the hacking tools are developed specifically for Linux. There are some exceptions, though, including software like Cain and Abel, Havij, Zenmap, and Metasploit that are developed or ported for Windows.

There are a lot of apps in Google Play for your Samsung Galaxy Note 2 that let you create, edit, and view Microsoft Office files on the go, but none match up to the power of an app called Polaris Office for Samsung Galaxy devices.

Throughout history, almost every superstition dealing with evil has had something to do with left hands. In the seventeenth century, it was thought that the Devil himself baptised his followers using his left hand. Today, studies show that left-handed people are more likely to be schizophrenic, alcoholic, delinquent, dyslexic, have Crohn's disease and ulcerative colitis, and a slew of other medical problems. To top it all off, left-handed people have an average lifespan that is 9 years shorte...

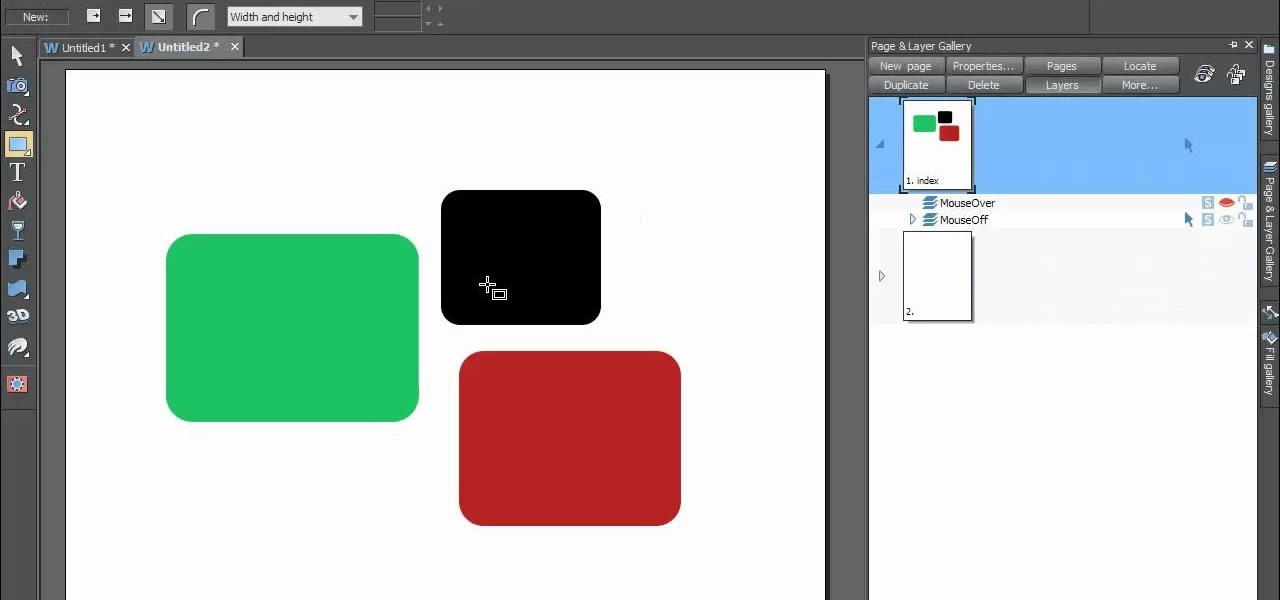
In this web design tutorial Learn how to create a multi-page document, duplicate and create new pages and edit page file names. This Web Design Tutorial for Xara Web Designer is really important because it also covers why you should never change the "index.htm" file name for your homepage.

Welcome back, my tenderfoot hackers! So many of you responded positively to my post about using the keylogger, as well as my post regarding turning on the webcam, that I decided that you might enjoy another similar hack. In this article, we will enable the audio recording capability on the remote system of your roommate.

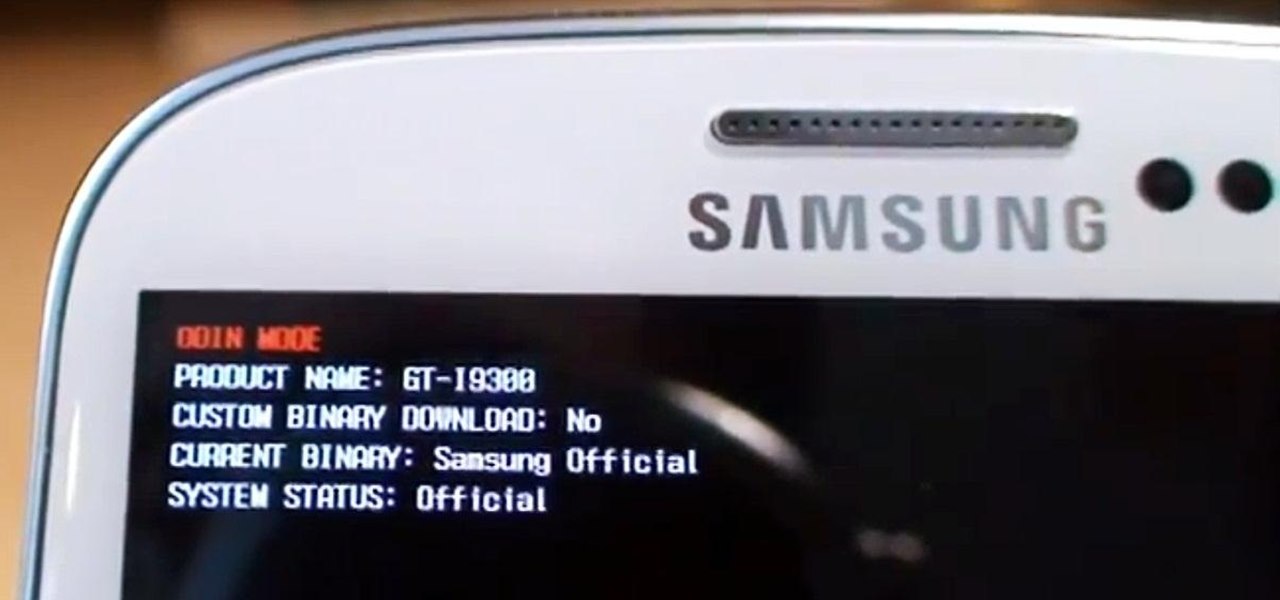
Need root on your Samsung Galaxy S3? Phone not getting the Jelly Bean update? Stuck on the Samsung screen? Phone bricked? Need to restore back to stock? Odin can help!

Megaupload was one of the very first file-sharing sites I ever used. But since 2005, the beloved (and pretty gangster) Kim Dotcom, has been in a legal battle with the U.S. Justice Department over copyright infringement.

The Jelly Bean update brought a lot of cool features to the Samsung Galaxy S3, but one nasty bug remained. Something was causing "Android System" usage to be consistently high. Of course, the percentage of this process that is used is dependent on what you're doing at any given time, but it shouldn't be anywhere near this level with "standard" use (calls, texts, emails, light browsing, etc.).

The advantages of rooting are vast. From free wi-fi tethering, being on the latest and greatest software, theming all aspects of the OS, to ditching Touchwiz for a pure Google experience and much much more.

There's a lot going for the Samsung Galaxy Note 2—smart screen rotation, huge HD display, great rear camera—which makes it an awesome device for reading, watching videos, and taking pics. But all of those luxuries will end up hogging up your internal memory, which is one of the few things the Note 2 could use some help in. The device comes with 16 to 64 GB of internal storage, depending on your model, with the option of adding a microSD card for more space. Only problem is, everything automat...

Like a computer, your brain can store and process large amounts of information. It can remember names, solve math problems, and save tips that you might need at a later time.

This guide will explain how to configure a USB Flash Drive / Memory Stick so that you can run a keylogger within just a few seconds of plugging it in any computer.

In the Windows 8 Enterprise edition, you can use the Windows to Go feature to travel with Windows 8 OS, personal files, documents, settings and many more. All you need is an external hard drive or USB drive of 32 GB space or more and USB 3.0 support or more for fast Windows 8 booting. We need the storage media of above specification to create bootable USB to access the data anytime by plugging the media into different PC running latest version of Windows 8 PRO or Windows 7.