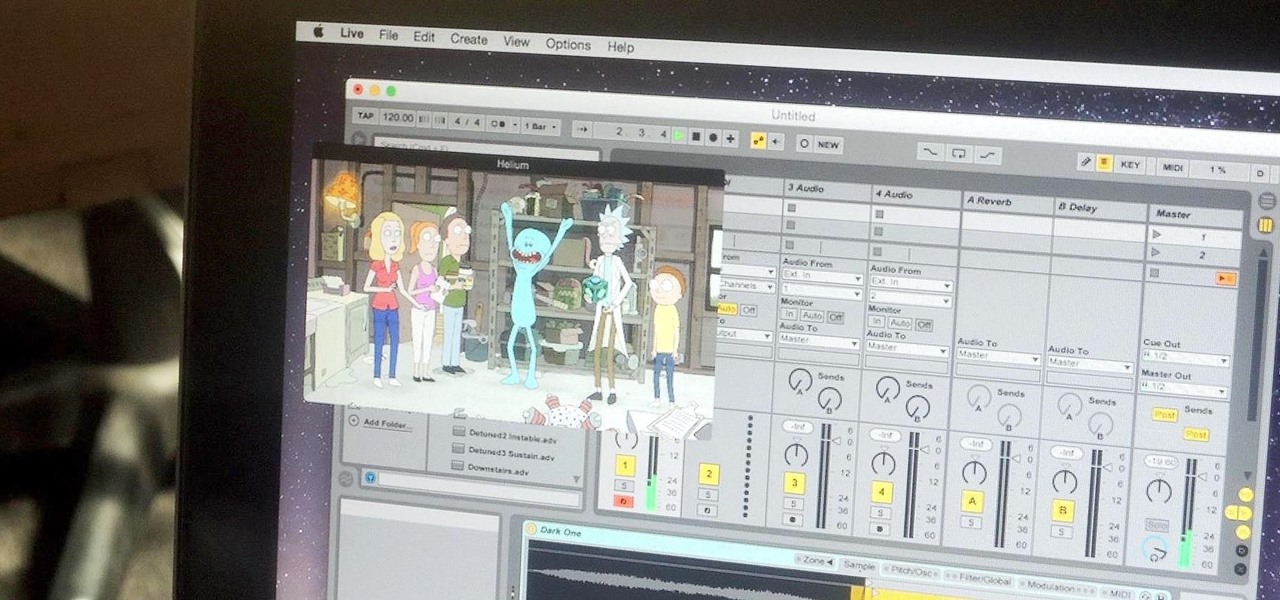
Hello, everyone! If you haven't read the recent announcement on the official release of the Null Byte suite, I suggest you do so. This is going to be a quick tutorial on how to download and install the suite so you can see our communities genius. So, let's get started!

Welcome back, my budding hackers! In this series, we are trying to understand how AV software works so that we can learn to evade it. To that end, we are working with the open-source AV software, ClamAV. I had previously introduced ClamAV in Part 2 of this series. If you have not installed it yet, go back to that and install it.

Android has a single text file named build.prop that determines tons of various system-wide settings on your device. You need root access to edit this file, since it's stored on the system partition—but the various lines of codes it contains are actually fairly easy to interpret and modify.

BlackBerry has yet to find a home amongst the iPhone and popular Android phones, with sales plummeting over the last couple years, but this might be a thing of the past thanks to their latest device, the BlackBerry Priv. It has decent numbers so far and was even sold out on Amazon shortly after its initial release.

Hello fellows nullbyters, first of i will start saying that im addicted to this community, i feel the challenge growing up so fast, all the newbies, amateurs,advanced and professionals hackers around trying their best to help the community, badly but we got some script-kids too but anyway, today we are going to learn how to install and use clanAV in kali linux.. INTRODUCTION

Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI.

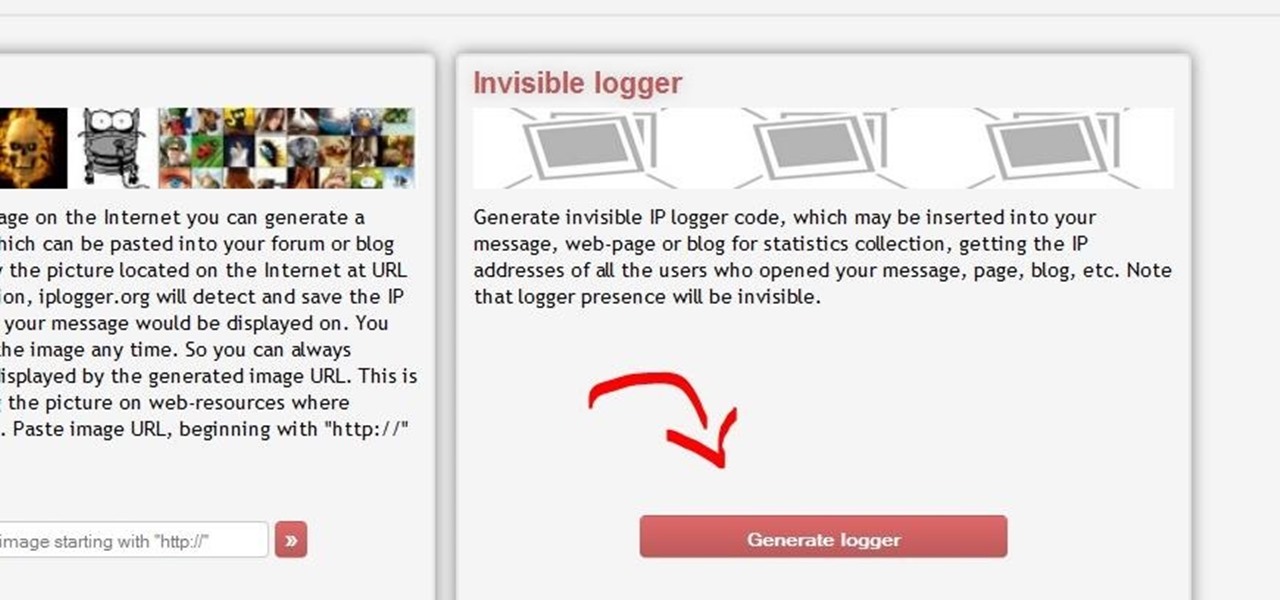
This is a quick and easy method for receiving the backend IP (1) of a server who is hidden behind a proxy (2) or a firewall (3).

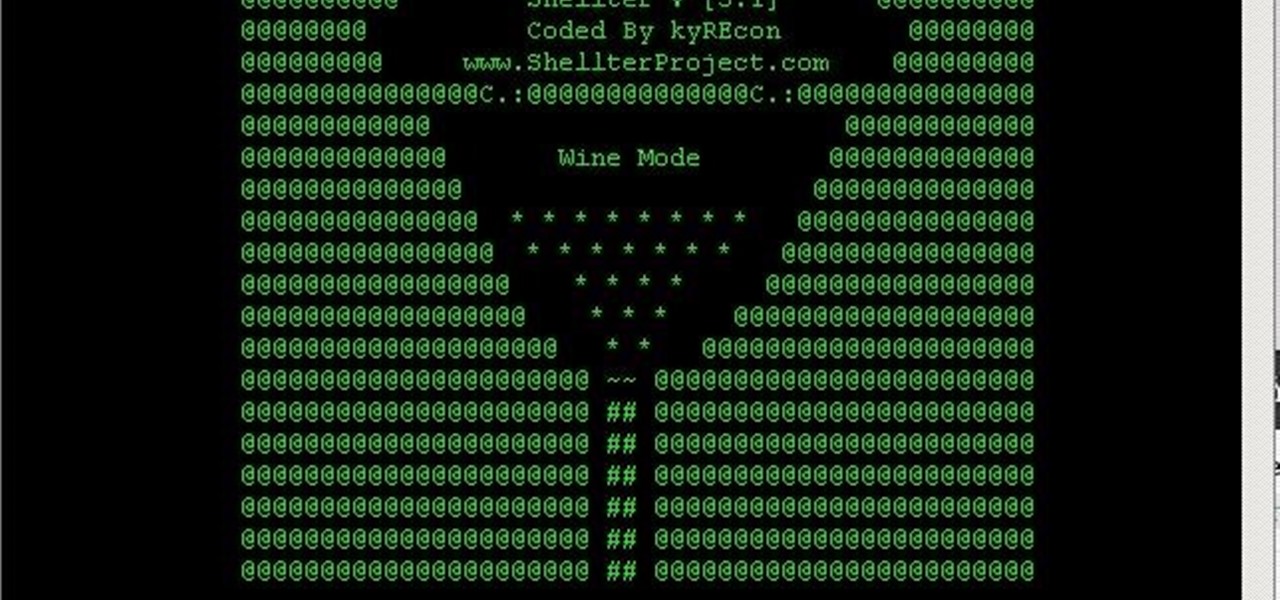
You always wanted to make an undetected payload and make it look legit, Well this is what this tutorial is about, You're going to learn how to backdoor any (Unfortunately only 32-Bit) software, Let's get into it

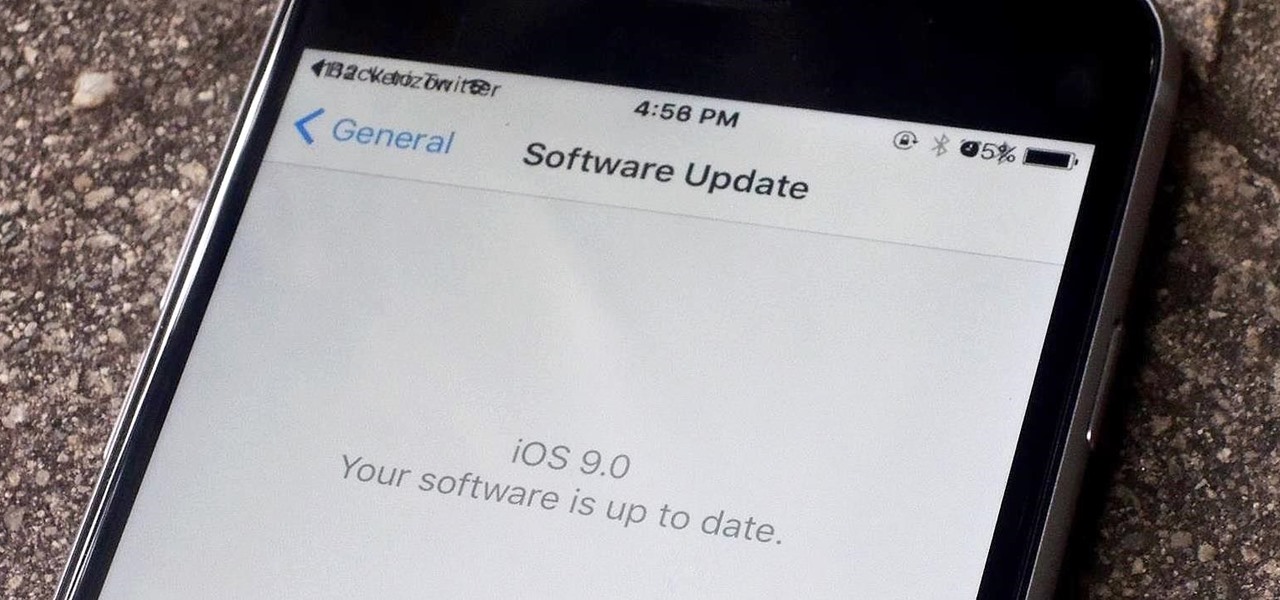
Apple's unveiling of the iPhone 6S, iPhone 6S Plus, Apple TV, and iPad Pro dominated the news today, but at the end of their special September 9th event, they quietly released the final version of iOS 9 to developers, called the Gold Master (GM) build.

OneDrive, formerly known as SkyDrive, is a free online storage solution developed by Microsoft. If you're a fan of using cloud-based storage systems, then OneDrive offers you plenty of benefits. It's also heavily integrated into Windows 10, including the new File Explorer, in an effort to make utilizing OneDrive easier for you.

Welcome back, my hacker novitiates! In an earlier Linux Basics tutorial, I had demonstrated the basics of the Apache web server. Since Apache is the world's most widely used web server on the Internet (as of July 2015, Apache was 38%, IIS was 26%, and Nginx is 15%), the more you know about it and understand it, the more success you are likely to have hacking it.

There's a whole world of wallpapers out there. Apple always includes a selection of stock wallpapers, some unique to every iPhone model you have. Of course, sometimes, stock wallpapers don't cut it. Sometimes, you want to add your own style to your home screen and lock screen. In these cases, using an app to find the best wallpapers out there can be just what you need.

Due to recent conflicts, I feel the urge to post this, in hopes that some of you will feel less hatred towards newbies, or a more respectable name, beginners.

Like most people who spend a good deal of time in front of their computer—whether for work, school, or play—I jump back and forth from window to window, working and playing with different things at the same time to get my work done faster or procrastinate harder.

As the Insider Preview builds of Windows 10 progressed, certain features were removed as new ones joined the fray. Some came back, while others disappeared, seemingly for good. One feature that seems to have been removed are the colored title bars on app windows.

If you have some photos, videos, and documents that you want to keep completely hidden and encrypted on your Android device, Andrognito is the app you need. We showcased this app in the past, but since then, CODEX has rebuilt it from the ground up with new and improved features.

Remembering keyboards shortcuts can prove difficult, especially when there are so many to remember, not to mention that they differ from app to app. While tools like CheatSheet can make them easier to use, today I'm going to show you how to enter them without using your keyboard at all.

We recently lost Grooveshark, the free music streaming service that supplied users with a huge catalog of free music anytime, anywhere. Since its shutdown, I have been scrambling to find a half-decent alternative, and my expectations were more than exceeded when I found NetEase Music.

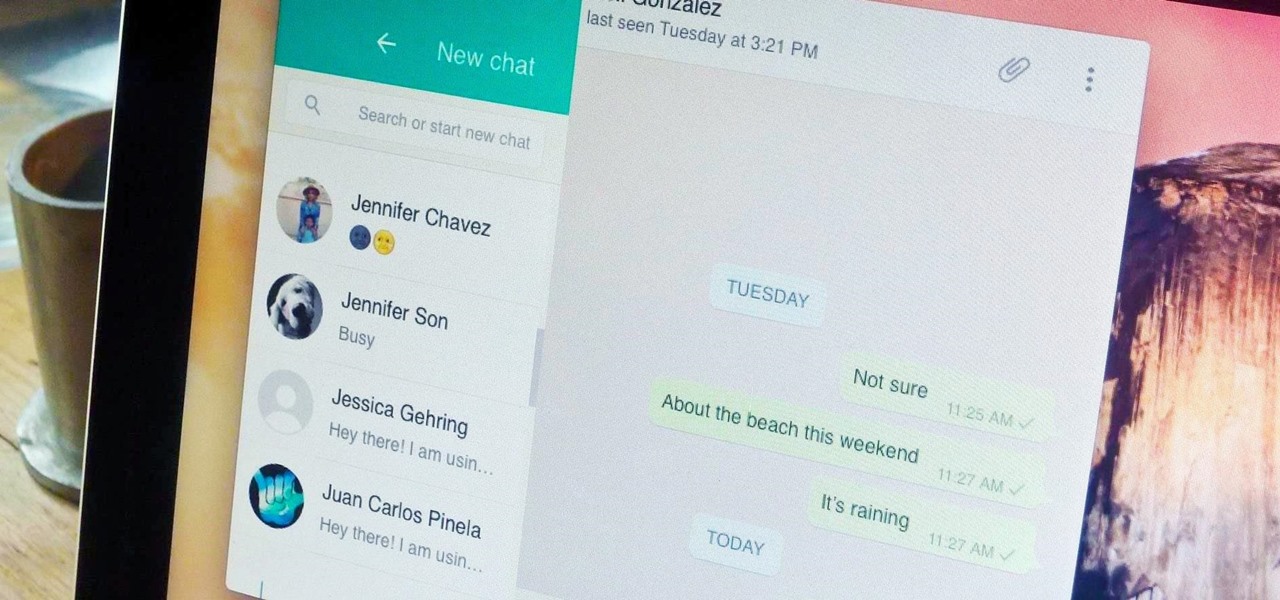
Boasting over 800 million users a month, WhatsApp has quickly become one of the most popular messaging services available today. Thanks to its low price, ease of use, lack of ads, cross-platform functionality, and great features, its popularity is well-deserved.

KNOX is a major pain for Samsung owners who like to modify their devices. Its combination of hardware and software security measures make things rather difficult when you're trying to modify system-level files and functions without voiding your warranty.

Ad blocking on Android usually requires root access, but a pair of new browsers based on the open source Chromium and Firefox builds are looking to change this.

Chromecast is so small and portable that it would seem to be a perfect device for making PowerPoint presentations. But even now that you can mirror your Android device's display, there are still a few issues.

Mobile service providers have an uncomfortably strong grip on the Android platform as a whole. For instance, all four U.S. versions of the Galaxy S6 and S6 Edge play their carrier's obnoxious jingle every time they boot up. You don't get any say in the matter—if you buy your phone from one of the big 4, you're a walking audible billboard.

Thanks to leaks and hard working developers, rooting tools for brand new Android devices are usually available right around the time of the smartphone's release, if not earlier. The Samsung Galaxy S6 and S6 Edge are no exception.

Technology has progressed by leaps and bounds and has blessed people in a number of ways, but at the same time, it has troubled them also. Computers are now used in every aspect of life. No matter if you are a businessman, an employee, a student, or even a housewife, a computer can assist you in your routine work. You save your personal information, documents, and other similar sensitive stuff on your computer that can hurt you if they get compromised.

CyanogenMod continues to be the most popular custom ROM for a good reason. Their team of developers always stay on top of the latest trends, and ensure that their software is packed with nice tweaks and awesome features. One such feature is an audio equalizer that allows you to fine-tune your device's various sound outputs. It's got a great interface, and works with any app that calls on Android's default audio mixer.

The long-awaited Apple Watch is ready for retail, with pricing and availability announced at Apple's Spring Forward event. Each of the three variants—Apple Watch Sport, Apple Watch, and Apple Watch Edition—will be available in two sizes, 32mm and 44mm, with preorders beginning on April 10th and the retail launch on April 24th. The Watches will initially be available nine countries: Australia, Canada, China, France, Germany, Hong Kong, Japan, the United Kingdom, and the United States. You'll b...

The Nexus Player is one of the most robust set-top streaming devices on the market. This is mainly due to the fact that the base software it runs is a direct fork of Android, which is a very powerful operating system itself.

Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.

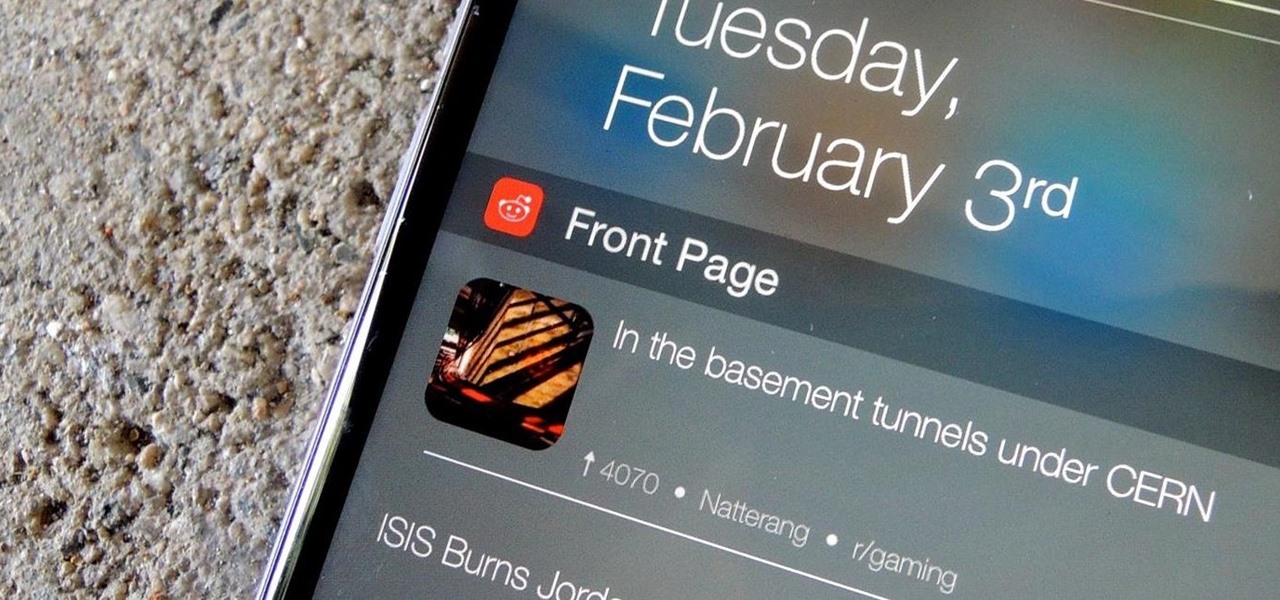
Reddit is a force to be reckoned with. What started out as link aggregator has become one of the world's most popular websites, with over 170 million unique visitors and 6 billion monthly pageviews. Whether you're into cute animals, crazy conspiracy theories, sports, or Taylor Swift's armpit, Reddit definitely has something for every taste, interest, and morbid curiosity.

With the sheer amount of photos, videos, and miscellaneous files we place on our computers, proper organization becomes necessary. Not only so that we can quickly get to a file when it's needed, but also to declutter folders and keep them from looking like random file dumps.

During class or while at work, it can take an immense amount of self-control to resist navigating over to Reddit. The link-aggregator and meme-warehouse makes it too easy to kill time... most of which you should be spending on various other tasks.

Welcome back, my nascent hackers!

If you've ever flashed a custom ROM on any of your devices, one of your main motivations for doing so was likely the set of neat tweaks and extra options that come with something like CyanogenMod. Another deciding factor was probably the fact that most custom ROMs offer a much cleaner interface than manufacturer skins.

Does your Samsung Galaxy Note 3 feel slower than it used to? Background processes, cached files, malicious applications, and buggy updates can all lead to a sluggish smartphone. It's just what happens over time.

There's a common bug that affects many Samsung Galaxy S5 users, myself included. The software that drives the fingerprint sensor can randomly fail to load, leaving you without one of the most unique features of your beloved smartphone.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

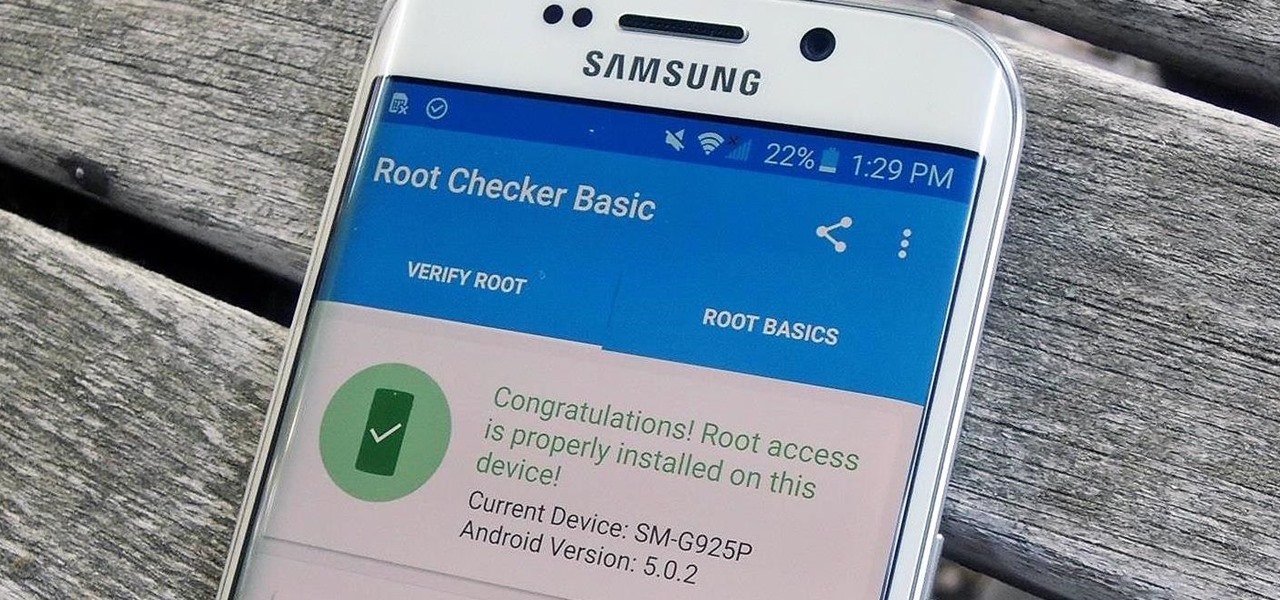
Whenever a new Android device is realized, the first thing I figure out how to do is to get it root access. Generally speaking, rooting has never been easier, with many one-touch methods like Stump and Towelroot available. But as manufacturers and carriers increase security with each new product, there is one tried-and-true root method that continues to work on most Samsung devices—Chainfire's CF Auto Root.

As carriers finalize their variations of the Android 4.4.4 update, we're left with only brief glimpses of what the new "Eye Experience" holds in store for us while we wait. However, thanks to a system dump of an updated European HTC One M8 and some clever hackery by donmarkoni, we can now install the new camera app on any variant of the HTC One M8.

iCloud Drive is Apple's new solution to file management syncing across iOS and Mac OS X. If you've upgraded to iOS 8 and you have an iCloud account, you can use iCloud Drive to store files for certain apps. While you won't really be able to benefit with file syncing between iOS and Mac apps until you get Yosemite, you can still access your iCloud Drive documents online.