It's so convenient to take a screengrab of one of your most favorite moments from your favorite movie or show, but sometimes you just can't. But you can actually take a snapshot of it. Check out this video tutorial on how to create screenshots from videos on Ubuntu Linux.
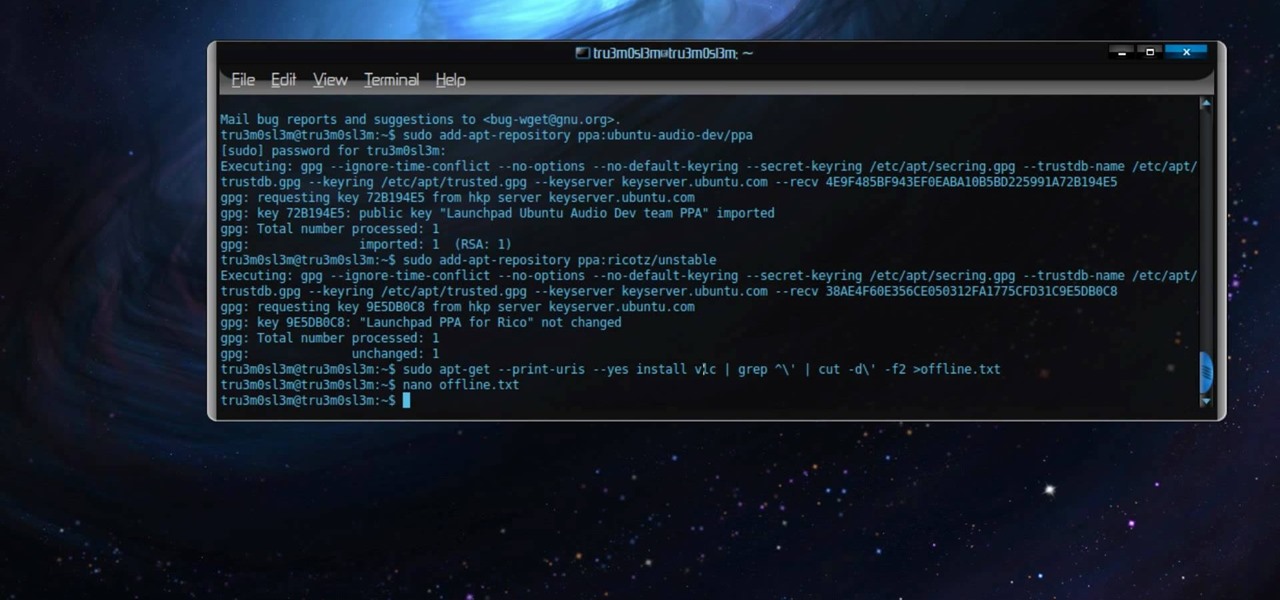
Permanent access to the internet might not always be possible for you and your Linux system, and this computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to offline package install and update on Ubuntu Linux.

Windows 7 is the hot, new operating system replacing the past XP and Vista systems. Windows 7 is the most simplified, user-friendly version that Microsoft has developed - ever. Get acquainted with your new version of Windows straight from Microsoft.
Windows 7 is the hot, new operating system replacing the past XP and Vista systems. Windows 7 is the most simplified, user-friendly version that Microsoft has developed - ever. Get acquainted with your new version of Windows straight from Microsoft.

Ingrown toenails happen when the nails on your toes grow in the wrong direction and dig into the surrounding skin. Follow a few easy steps to treat this painful condition, and prevent it from happening again.
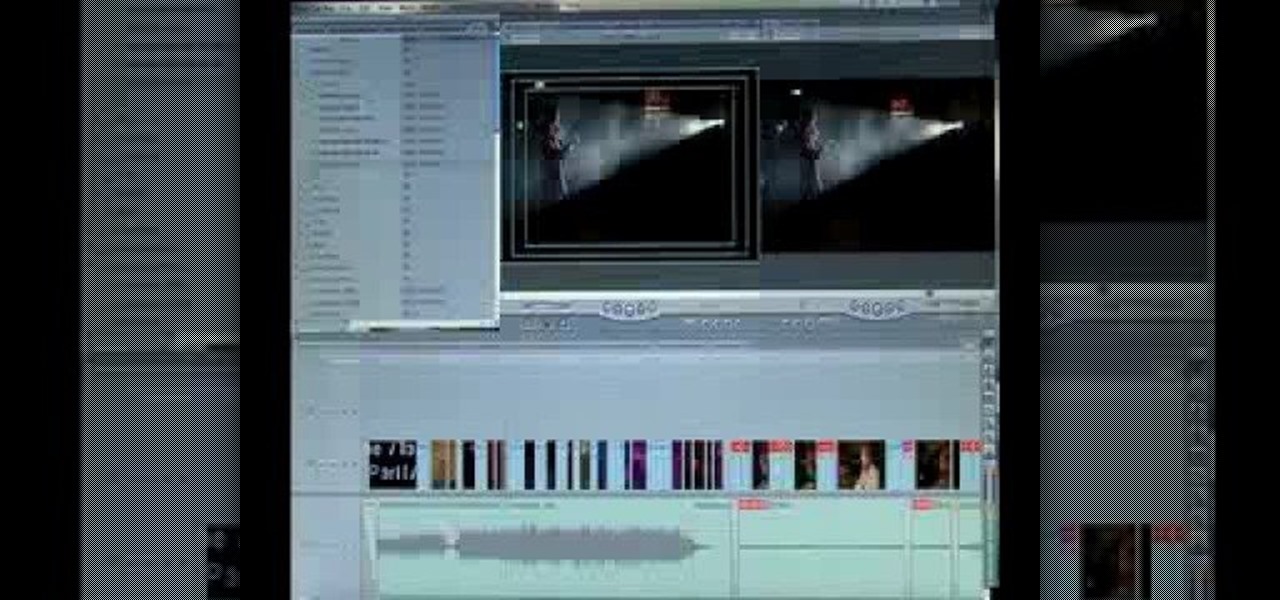
Forgot to take a few production stills on set? No problem, work with what you have... the actual video footage. See how to get photos from video with iMovie or Final Cut Pro 6.

This video helps people make hills and elevation on their farm! Here is my spreadsheet, which might come in handy:

This easy-to-follow video tutorial walks you through steps of converting old VHS tapes to DVD. Roxio Easy VHS to DVD is a combination of software and hardware that allows you to easily and quickly digitize old analog recordings. You simply attach the included hardware to a free USB 2.0 port on your computer, then capture from virtually any analog video or audio source.

Watch to learn how to get infinite EXP with proxies in MyBrute (04/23/09). It shows how to get exp from pupils you make by passing the current two checks (Flash SOL files and IP check).

See how to make some cool gift / party favor bags for any occasion. They are made with envelopes. You can make them from nearly any size and type. The ones in the video are made with some surplus greeting card envelopes. Sometimes you can purchase "leftovers" from an office supply or drug store (any store that sells greeting cards). "Left-overs" mean that the cards get damaged or lost but the envelope is left. Just ask the manager if you can purchase them.

Wouldn't your TI calculator be way cooler with some sweet programs like Nintendo or Tetris? This is a short tutorial on extracting the files from a ZIP archive, and transferring them to your calculator.

He's not exactly demanding sexual favors, but his flirting is getting really gross. What's a girl who likes her job to do? You will need diplomacy and documentation. Assess his behavior. Now, don’t be offended, but we have to ask: Is he really coming on to you, or is he just a sociable, flirtatious kind of guy? If it’s the latter, just ignore it. Do your part to keep the relationship professional. Don't chat about how your last two boyfriends cheated on you and then expect him to know that di...

Adam from Chemical Reaction wants to show you a little movie magic. This video tutorial will show you how to make an Assassin's Creed hidden blade prop for your homemade film. If you're a fan of the Assassin's Creed video game, then you can't not make this hidden blade. This is a great prop for anybody wanting to recreate it for a fan film. It's cheap and quite easy and works pretty well.

Hacker Defender is one of the most widely deployed rootkits in the world. It is a user-mode rootkit that modifies several Windows and Native API functions, which allows it to hide information (files, processes, etc.) from other applications. In addition, Hacker Defender implements a backdoor and port redirector that operates through TCP ports opened by existing services. This means it is not possible to find the hidden backdoor through traditional means, like launching a remote port scan agai...

Need to shoot a film for class and realized you don't have a Fisher Dolly and your cinematographer's hands are a little to shaky for what you would consider good filmmaking? Well, this video tutorial will show you how to make your very own steadycam. Check out how a nautilus design transforms into a more suitable steadycam; the gimbal is the key, and gimbals are very hard to find, especially the right one.

TorrentFlux is an web-based system for managing bit torrent file transfers. It is an open source package (GPL) and developed for Linux, Unix & BSD platforms on the ubiquitous LAMP stack. In video tutorial, you'll learn how to set up TorrentFlux and how to share your downloaded content via a Samba share to an Xbox running XBMC. For detailed, step-by-step instructions, or to get started watching your own torrented media from the comfort of your couch, take a look.

Boris Title Toolkit gives Adobe After Effects users advanced titling capabilities for maximum quality, speed, and creativity. Using Title Toolkit, graphic artists can import ASCII or RTF files for fast, easy credit rolls, take advantage of rich text style options such as bevel borders, gradient fills, simulated extrusion, and embossing, and save or apply custom or preset text styles, gradients, and colors, all of which can be applied on a per character basis.

This tutorial is on GIMP Basics. GIMP is a free Photoshop substitute available for all platforms and pre-loaded in Linux operating systems. The tutorial covers the scale, crop, cut with transparency, flip, and rotate commands of GIMP. Part 2 covers saving and file size reduction in GIMP.

This software tutorial shows how to make an animated gif file that changes the color of your eyes or of anything you want in Photoshop. Animated gifs are perfect for profile pictures on sites like Myspace and forum sites. So check out this Photoshop tutorial and learn how to make your own cool animated gifs.

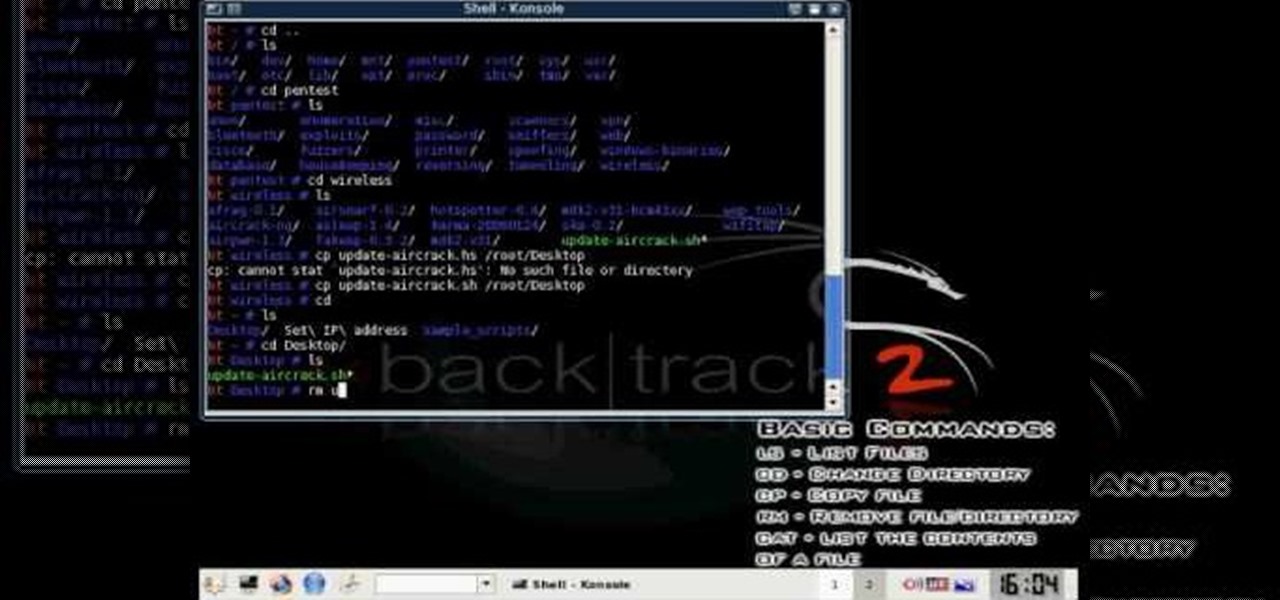
A basic tutorial from InfinityExists.com on using Backtrack - the Linux-based security software package. This tutorial covers: Where to get Backtrack 2, How to burn an .ISO file, How to boot Backtrack 2, How to login, and start the GUI interface. It also illustrates basic Linux commands, and how to set up your Network Interfaces.

If you've never done it before, making a podcast can be tricky, with multiple programs to use and multiple file types to deal with. But, this video series helps you through the complete process of creating a podcast, everything including recording, editing, images, exporting, converting, uploading, and finally… sharing. Watch this whole series to learn how to make podcasts using GarageBand, iWeb, iTunes, and Fugu.

When you need a file on your Mac as soon as possible, you usually have to get your MacBook or hop on your iMac, Mac mini, Mac Pro, or Mac Studio. But that's too much work if you're in bed, lying on the couch, or outside in the fresh air. Why even bother when you can access that file directly on your iPhone or iPad — without moving an inch?

If you use iCloud Photos, Apple's iCloud link feature is meant to make sharing multiple photos and videos faster and easier, but it's not as great as you might think. Luckily, there's a way to stop your iPhone from creating them automatically, as long as you're running iOS 13 or later.

Everybody knows not to store sensitive information in unencrypted files, right? PDFs and ZIP files can often contain a treasure trove of information, such as network diagrams, IP addresses, and login credentials. Sometimes, even certain files that are encrypted aren't safe from attackers. That's where Zydra comes in — a tool for cracking RAR files, ZIP files, PDF files, and Linux shadow files.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android device to flash TWRP on another.

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.

Anyone who has used Linux long enough is familiar with sudo. Short for superuser do (or substitute user do, depending on who you ask), it allows users to run commands as either root or another user on the system. From a hacker's point of view, sudo is often all that stands between them and root access. We'll be exploring an older vulnerability in sudo that allows a user to run commands as root.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

Black Desert Mobile is one of the hottest new smartphone games around, but there seems to be something missing in the frame rate department. Gamers quickly noticed many Android phones are stuck on a 30 FPS cap when it comes to performance. It's not that the phones are too weak to handle higher frame rates, but that there is a particular list of approved devices that can achieve this.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

Whether you're ordering a new 2019 iPhone model online or just want to know how they look in your hand before buying in person, use these printable cutouts to see which one looks and feels best.

During the Google I/O 2019 keynote, the latest Android Q Beta was released to the public for Pixel smartphones along with 15 other non-Pixel devices. It's the third Developer Preview for Android 10, but it's the first official public beta outside of Google's Pixel smartphones. A new public beta means good things are on the way as the future of Android continues to evolve.

The music and sound effects that play in the background of any videos you edit helps set the tone, so it's essential to get it right. Enlight Videoleap, an extremely powerful and popular mobile video editing tool for iOS, lets you quickly and easily add audio from your iPhone and the cloud, but things can still get a little confusing when you have a timeline full of clips.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

The legal drama framing the closure of Meta Company continues even after the company's assets have been sold to a new owner.

After years of rumors and waiting, Samsung's first foldable smartphone is finally a reality. The phone itself is a bit wild, but with Samsung going so far out of their comfort zone with this one, there were some bumps in the road that caused a delayed release. The launch has been pushed back yet again, but when it does hit stores, it could end up being one of the most influential devices in years.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

Recently, buzz for the Google Pixel 4 has been rising thanks to a patent discovered by 91mobiles. This patent appears to show an almost bezel-less phone with a screen-to-body ratio we have only dreamt of, and no notch in sight. The problem is this isn't the Google Pixel 4. It's actually the Pixel 2 XL.