New documents reveal that electric car company Tesla has filed a surprising new patent that has nothing to do with batteries or autonomous driving and everything to do with augmented reality.
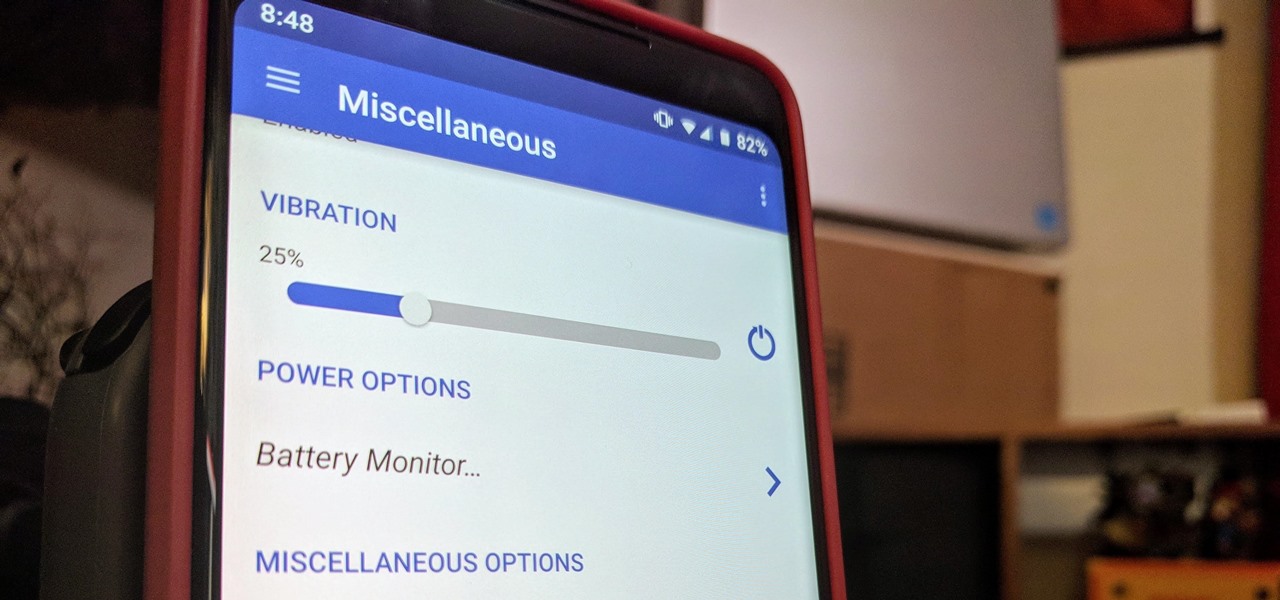
Haptic feedback and vibration of our smartphones have come a long way in recent years. These features are much more premium now than they once were, but most users are still unable to adjust the intensity for notifications or phone calls. Most higher-end devices make less noise on surfaces than in the past, but adjusting these values can still come in handy even today.
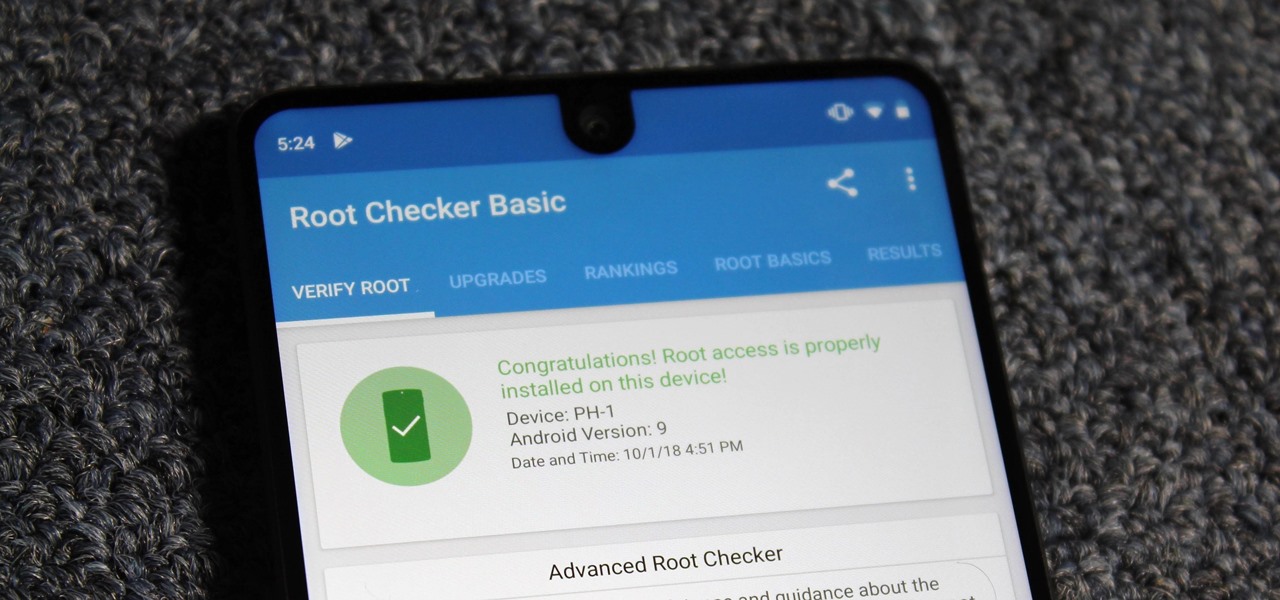
Despite its rocky start, the Essential PH-1 has a lot going for it. Not only does it get consistent security patches and system updates hours after the Pixels, but like the Google-developed lineup, it's also great for rooting. Not only is your warranty not void with rooting, but the process is pretty straightforward.

In a previous tutorial, we were able to measure horizontal surfaces such as the ground, tables, etc., all using ARKit. With ARKit 1.5, we're now able to measure vertical surfaces like walls!

In order to increase the security and harden the integrity of an email account and its content, you'll want to use PGP on your Windows, macOS, or Linux computer. This is usually the first thing security analysts do to protect communications with encryption, and everyone else should consider it too, especially since there's an easy way to incorporate PGP that anyone can follow.
In an SEC filing published on Monday, Snap, the company behind Snapchat, disclosed that Imran Khan, its chief strategy officer and a member of the NR30, is leaving the company to "pursue other opportunities."

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

In our last ARKit tutorial, we learned how to measure the sizes of horizontal planes. It was a helpful entryway into the arena of determining spatial relationships with real world spaces versus virtual objects and experiences.

Based on its continued research, it appears Microsoft recognizes that the next HoloLens needs a wider field of view (FoV). Based on a recently-revealed documentation, the company's research team has found another way to accomplish that objective.

Have you noticed the many utility ARKit apps on the App Store that allow you to measure the sizes of horizontal planes in the world? Guess what? After this tutorial, you'll be able to do this yourself!

Less than two months since unveiling Project North Star, Leap Motion has released the reference design that will allow developers, makers, and even manufacturers to build their own augmented reality headsets based on Leap Motion's work.

Augmented reality headset maker Meta Company unveiled Meta Viewer, its first software application, during its keynote at the Augmented World Expo in Santa Clara on Wednesday.

After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire features some useful post-exploitation modules which make hacking Macs very easy.

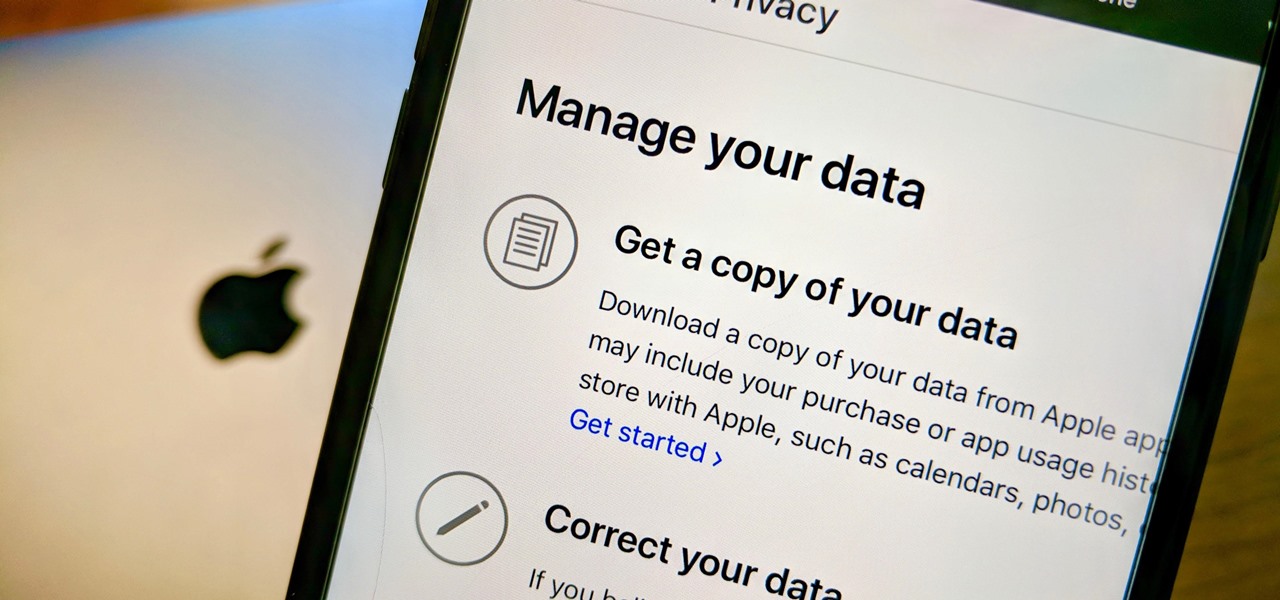
Personal data is a hot topic right now, and for good reason. Never before has the public been so on edge about how companies use their information. Services like Facebook and Google now allow you to download all of the data each has on file. Soon, you'll be able to see exactly the same for Apple as well.

Google's ARCore has expanded its support to include the Galaxy S9 and S9+, which means you get access to all the cool new apps that can sense the world around them. But one of ARCore's coolest uses so far is still Pixel-exclusive: AR stickers built right into the Google Camera app. Thankfully, XDA user lofass33 has an ingenious workaround for using these stickers on your S9.

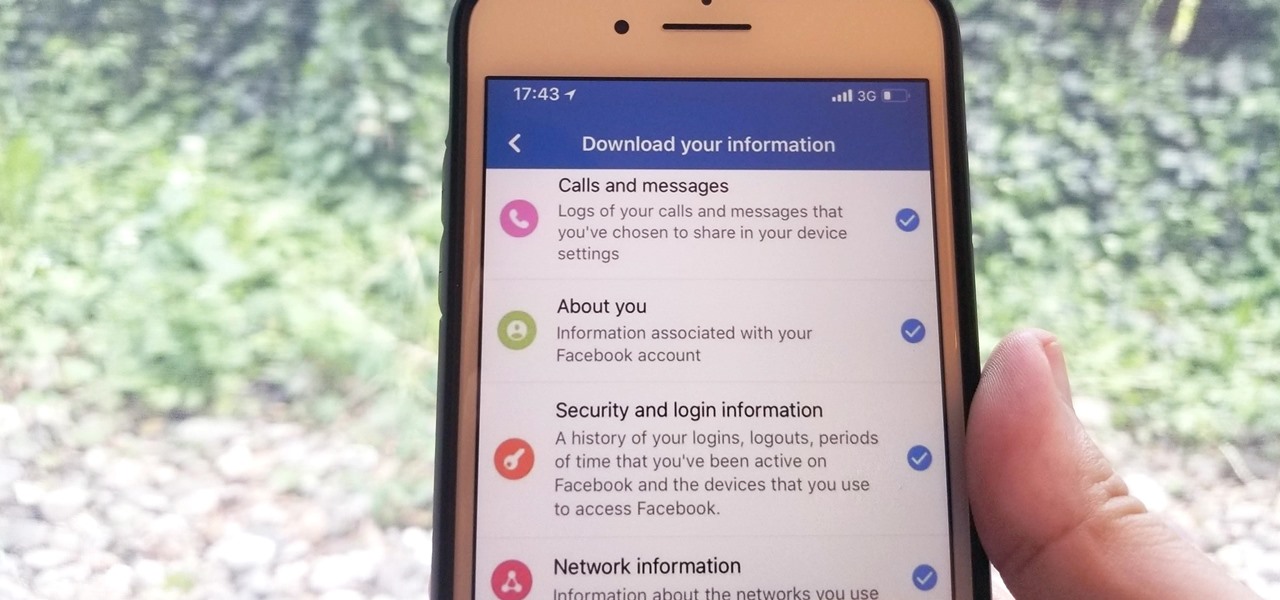
We've been able to download our Facebook data onto our computers for a while now, but now you can do so right from the comfort of your iPhone or Android phone. With it, you'll be able to integrate your data into other apps that support it or even just download it before you deactivate your account.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

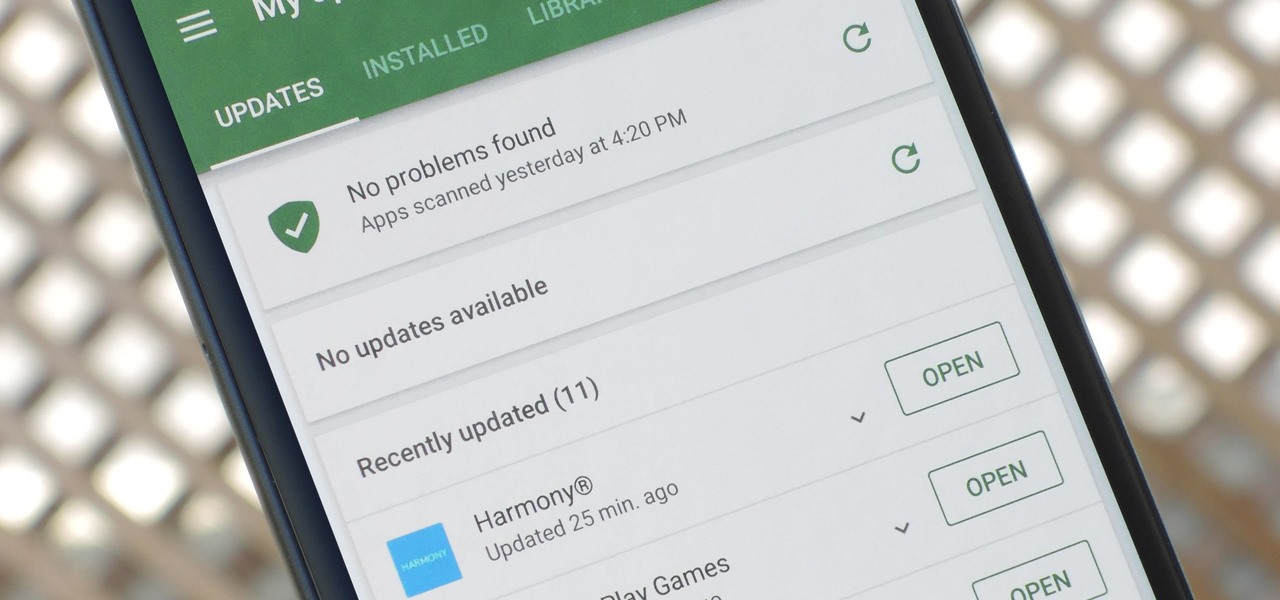
App updates bring new functionality, but they can also break old features or introduce changes no one wants. Unfortunately, if you're holding onto an older app version because you don't want to accept the update, it becomes a lot harder to keep the rest of your apps updated.

Augmented reality device maker Vuzix has filed a defamation lawsuit asking for $80 million in punitive damages, money damages, and interest against a short seller who has publicly claimed that the Amazon Alexa functionality of the company's Blade smartglasses is fraudulent.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

By default, the Galaxy S9 and S9+ only have 15 media volume steps — in other words, there are only 15 increments between silent and full volume. That's usually fine if you're using your phone's speakers, but if you're wearing headphones, more fine-tuned controls would be helpful.

Noted poet T.S. Elliot once wrote that "April is the cruelest month." But Magic Leap might argue that March is the most miserable, as the Ides of March brought more legal woes to augmented reality startup. Elsewhere, its closely-held branding secrets have been spilled by way of the US Patent and Trademark Office (USPTO).

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

When it comes to media players, few are more capable than VLC. With its extensive codec support, VLC is able to play almost any video file. Partly due to its open-source nature, features are constantly added. This trend has continued with a new update that added native Chromecast support.

To please those of us who love to mod and root our Androids, OnePlus has made both the OnePlus 5 and 5T relatively easy to customize — so much so that the 5T topped our list for the best phones for rooting. Unfortunately, unlocking the bootloader and using root to modify the firmware on your OnePlus 5 or 5T makes it hard to update to a new firmware such as Oreo when compared to stock.

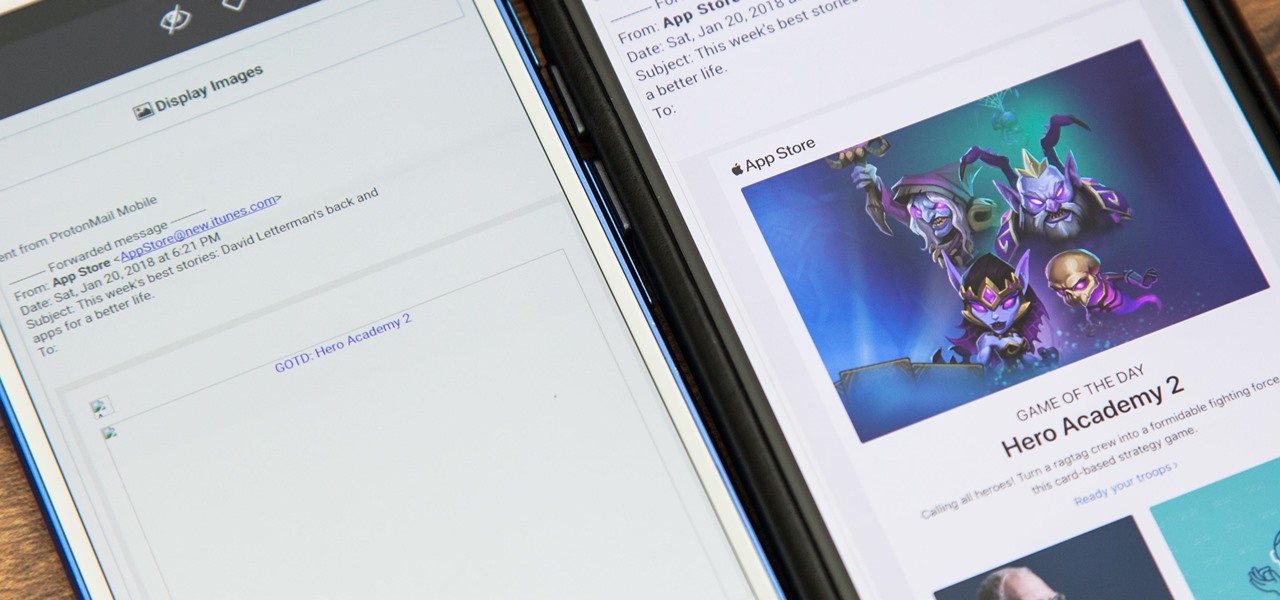
By default, images embedded using external links will not automatically load in any emails that you get with ProtonMail. This is a security mechanism that can prevent malicious code from being executed on your system, but it can also be fairly annoying to have to manually load images in email after email.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

Whether you're a veteran augmented reality developer looking for a quick access point to add a new platform to your arsenal or just getting started with your first AR head-mounted display, get ready to start developing for the Meta 2.

PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.

When it comes to streaming services, Google Play Music is one of the best options for both Android and iOS. Perhaps its single greatest feature is the fact that you can upload as many as 50,000 of your own songs to Google's servers, then stream your library to any device without ever paying a dime.

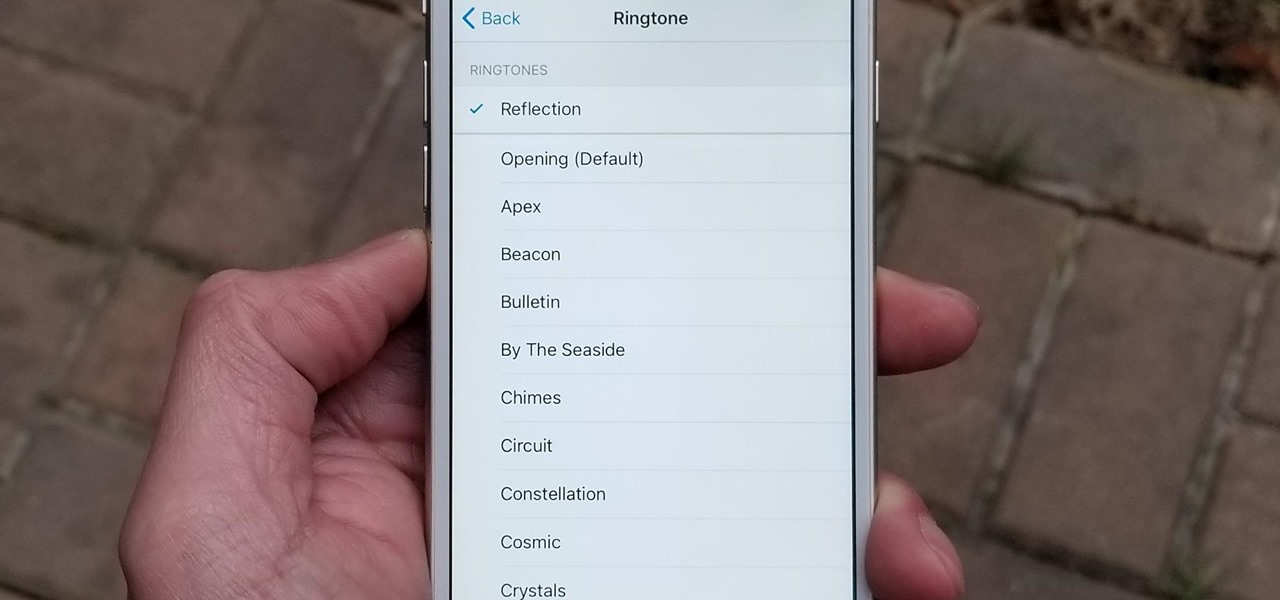
The new iPhone X sets itself apart from its predecessors not only as the first Apple smartphone to use an AMOLED screen, but also as the first iPhone to cost over $1,000. True to form as an exclusive device, Apple's latest flagship also features a distinct ringtone. With a little tinkering, however, you can make the new "Reflection" ringtone your very own, regardless of which iPhone you may have.

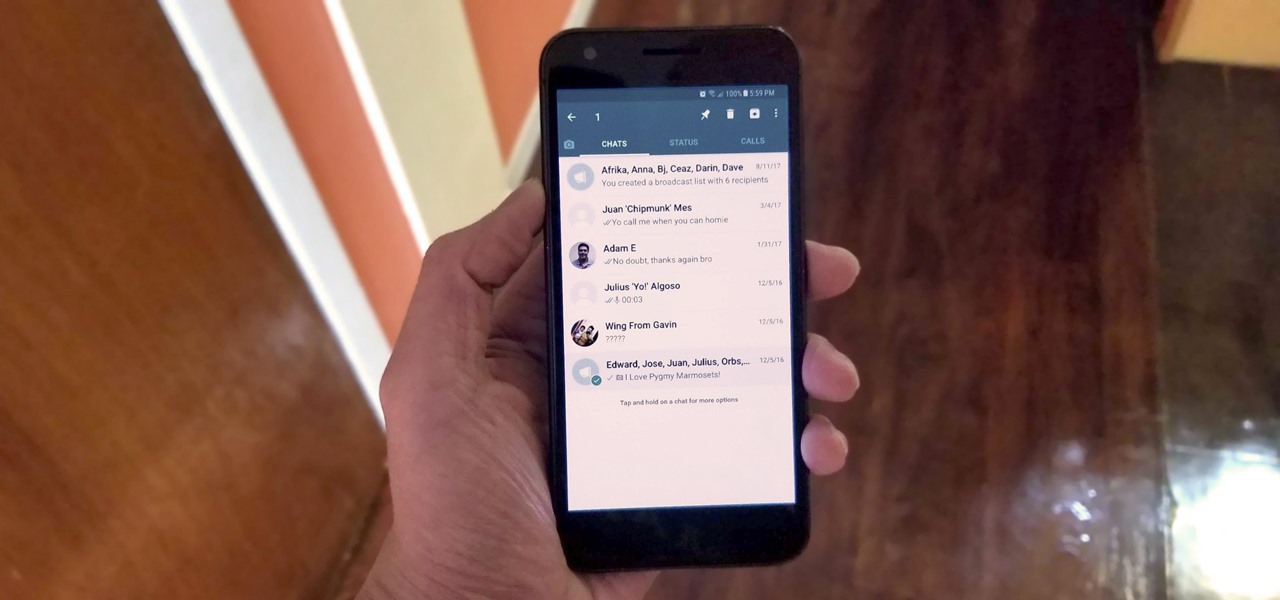
One of the downsides of living in an unprecedented age of connectivity is the near-constant bombardment of information. WhatsApp, the go-to messaging app for people the world over, is just as susceptible to buildup of useless media files, thanks to awesome features that allow us to communicate in multiple ways, such as broadcasting to friends and family. Luckily, the app makes it easy to remove old and unwanted data from your iPhone or Android.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.

Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn a Raspberry Pi into a router running through PIA VPN, which will ensure every connected device gets the VPN treatment.

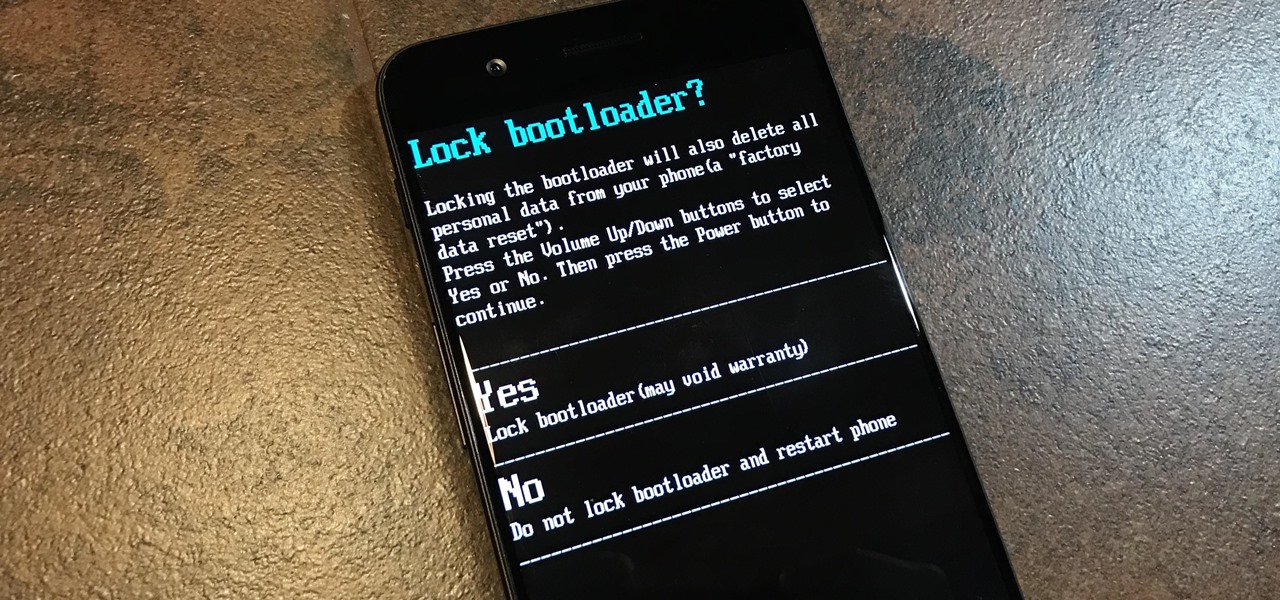
So you spent all day customizing your phone. You tinkered with all the settings, searched the web high and low for the perfect wallpaper, and found an ideal icon pack to complement the color scheme. You go to sleep, proud of the work you accomplished when the unspeakable happens — your phone freezes and tech support is telling you to do a factory reset to fix the problem.

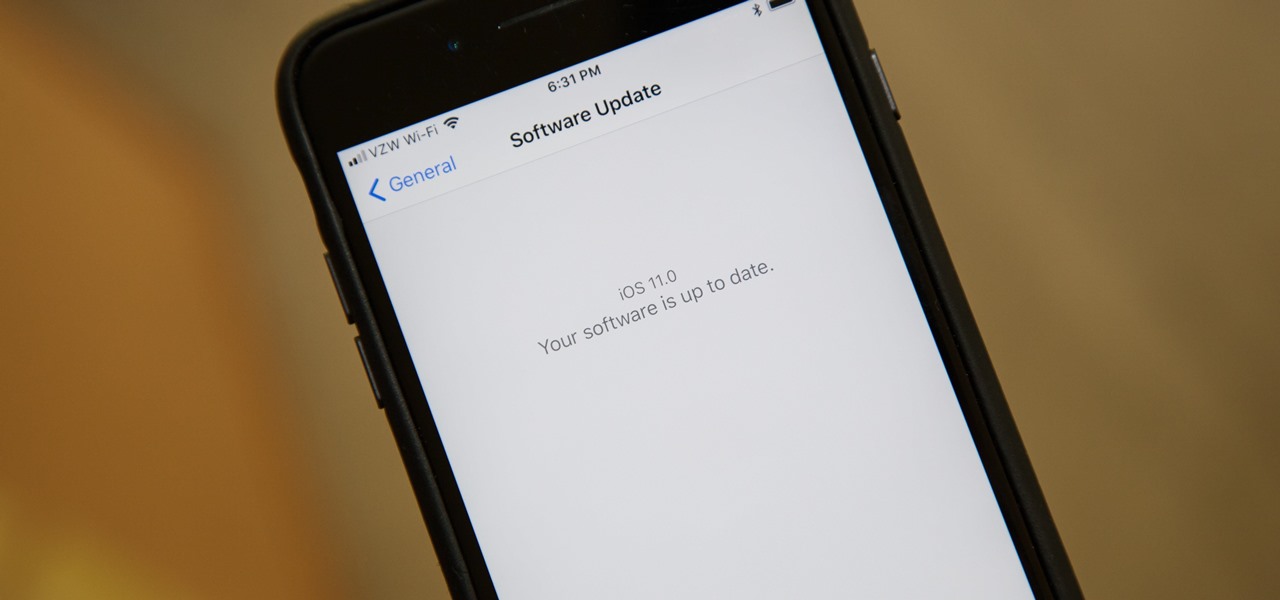
The final developer version of iOS 11 was leaked a few days ago, but Apple quickly stopped signing it so nobody else could install it. With Apple's Sept. 12 event now over, the Golden Master (GM) version of iOS 11, the same version that will be released to everyone around Sept. 19, is available to install again — and anyone can get it.

Adding additional photos to a movie project in iMovie for iPhone is relatively simple, but incorporating more videos to your timeline is a little bit more involved, only because there's more that you can do. Unlike with photos, you can trim the length of new videos, select the audio only, and add overlay effects.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.