If you've seen our guide on the 18 coolest features in iOS 7, you know that there's a lot to like about Apple's new mobile OS, but there's also a laundry list of grievances to go with it. One that bugs me is the lack of Home screen customization, something that has always driven me to jailbreak in the past.

There are definitely some very cool things about the new iOS 7, but it's also got plenty of downsides, one being the updated look of stock app icons. Apple drastically changed their glossy skeuomorphic icons for a flat, modern squircle look using their golden ratio grid.

Welcome back, my fellow hackerians! Today we'll be hacking Facebook profiles on your local network. You may think, "How is this useful, nobody but me is using my network." Well, you can use this on other Wi-Fi networks that are available for free (like at Starbucks) and crack their precious Facebook profile!

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

How to patch a hole in drywall / plasterboard / Sheetrock. Everyone at some stage in their life will need to patch a hole in drywall / plasterboard / sheetrock. Instead of doing some dodgy patchwork, watch this video to see how simple the job is. The steps are as follow in point form. This method is particularly suitable for holes that are larger than about 100mm or 4 inch's in size.

It's always a good idea to have a pack of mints on hand, especially right after a cup of coffee or a lunch made with loads of garlic. Whether you're going on a date, to the dentist, or to an interview, bad breath is a major faux pas and totally avoidable. Simply pop a mint! But not just any old mint — homemade ones not only freshen your breath but can give you a sense of pride every time you need one.

Video: . Step 1: Today We Are Going to Draw an Airplane. Let's Start with a Rectangle in Two Point Perspective. Before We Begin We Need to Figure Out Where Our Horizon Line and Vanishing Points Will Be. Sit Back and Think What Kind of Look You Are Going for.

Ralph Waldo Emerson once observed that "the seed of science" was "wonder," and taking a look at this nine-layer liquid tower from Steve Spangler's Sick Science! channel, one can't help but do just that — wonder. How is this possible? Is this magic or what?

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

Store-bought fake blood isn't too expensive, but the consistency and color are always the same. Real blood varies, from bright red when oxygenated (arterial blood) to deep, dark red when deoxygenated (venous blood), and it can be either thick or thin. So to achieve the best special effect, you're better off making a batch of DIY fake blood yourself to get the look and texture you're going for. And it's very simple to do.

We've all attempted to fold a paper airplane before, right? One we hoped would sail majestically through the air for a good while but just ended up nose-diving into the grass. Paper planes, an invention likely as old as paper, are models of engineering; and they must account for the same dynamics as real planes, from drag force to stability to weight. So what is the perfect design?

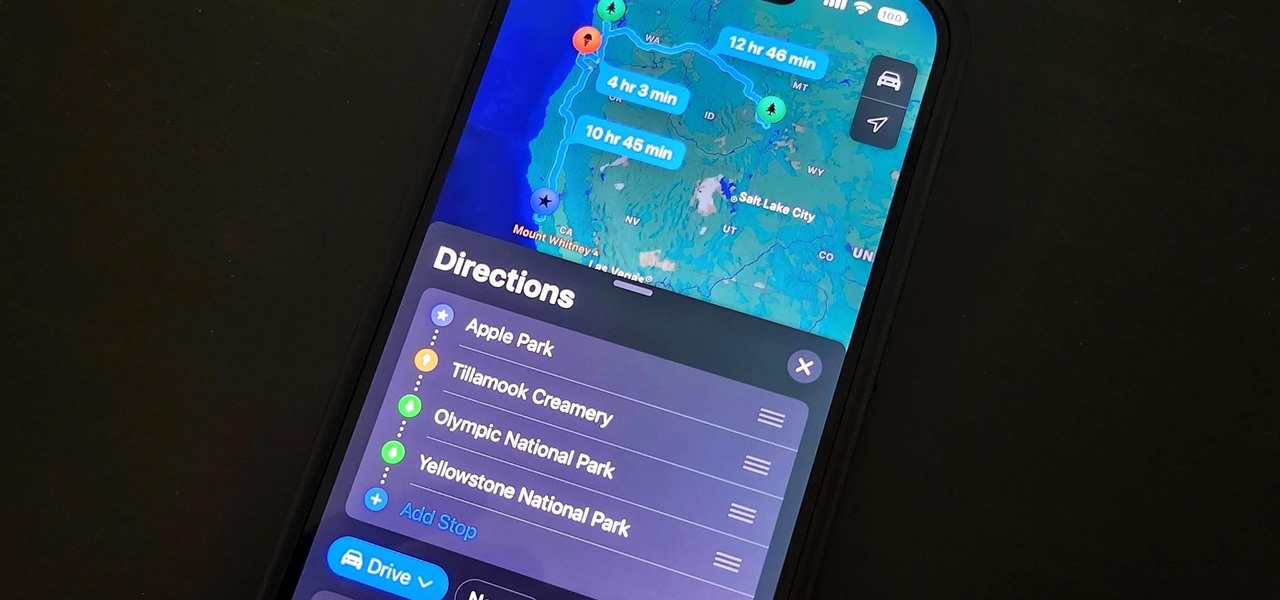
One thing Apple Maps always lacked was the ability to add stops along a route while planning a trip. Navigation would help you travel from the beginning location to the final destination, and the only places you could add between that were pit stops like banks and ATMs, coffee shops, convenience stores, eateries, fast food, gas stations, and parking lots. That all changes in Apple Maps' latest update.

Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for us, we can limit the damage caused by those mistakes by running SELinux.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

Pronunciation is key to learning any new language. Before diving into the vocabulary and basic phrases, a good approach is to listen and try and get your aural perception honed in. A new word or phrase, like "je m'appelle" in French, is awesome to learn, but it's important to learn it correctly: that starts and ends with pronunciation.

The long name of this technique makes the meticulousness and dexterity skills of making jewelry a must. If you aren't perfect in all your techniques, this might stump you, but practice makes perfect. Wire wrapping a center-drilled, single-end stone takes skill. This demonstration video will help walk you through the process of doing a center-drilled single-end wire-wrap.

As the best-selling toy of all time, the odds of you once playing with a Rubik's Cube are pretty high. And if you're like me, or even the cube's inventor Erno Rubik, your first attempts likely ended in futility. Every twist, every turn, the cube just gets more and more mixed up. Is there really a solution?

In these music studio recording and production videos, learn how to use a 4-track reel to reel tape recorder to capture your vocals, guitar parts, drums, record songs, or even make a demo CD. Our expert will walk you through the operation of a fairly simple reel to reel machine in several steps, including the basic and advanced functions, rear components, using mics and connecting to other mixing boards, recording on four different tracks, mixdown, bouncing tracks, and final tips for masterin...

Watch the full gameplay for Castlevania: Lords of Shadow on the Xbox 360. Lords of Shadows is yet another video game in the popular Castlevania franchise, which has been around since the days of the NES. In this lengthy walkthrough, you'll see all the vampire killing action, set in the Middle Ages, with protagonist Gabriel Belmont. This is a handy video guide if you ever get stumped on a level.

Dive (or more appropriately, soar) into another Tom Clancy video game on the Xbox 360— This walkthrough series for Tom Clancy's H.A.W.X. 2 covers the whole entire gameplay for the newly released sequel. Gun down countless MiGs, bomb enemy tanks and shoot down nuclear missiles before they destroy their targets! This video game is all about speed, battle and adrenaline. Try out this air combative flight simulator yourself, and see if you're not on the edge of your seat. Watch the full walkthrou...

Skulls. What spooky Halloween décor or staging of Hamlet is complete without a skull or two popping up? For ghoulish special effect and/or setting a dramatic scene, skulls are absolutely integral. Well, with some artistry, hardware supplies, and a good dose of patience, you can create your own inexpensive prop skulls for use however you please.

It's been done for ages, but for most of us, "regift" entered our vocabulary after the 98th episode of Seinfeld—"The Label Maker." In this episode, Elaine calls Dr. Whatley (played by Bryan Cranston) a "regifter" after he gives Jerry a label maker—the same label maker that Elaine gave Whatley.

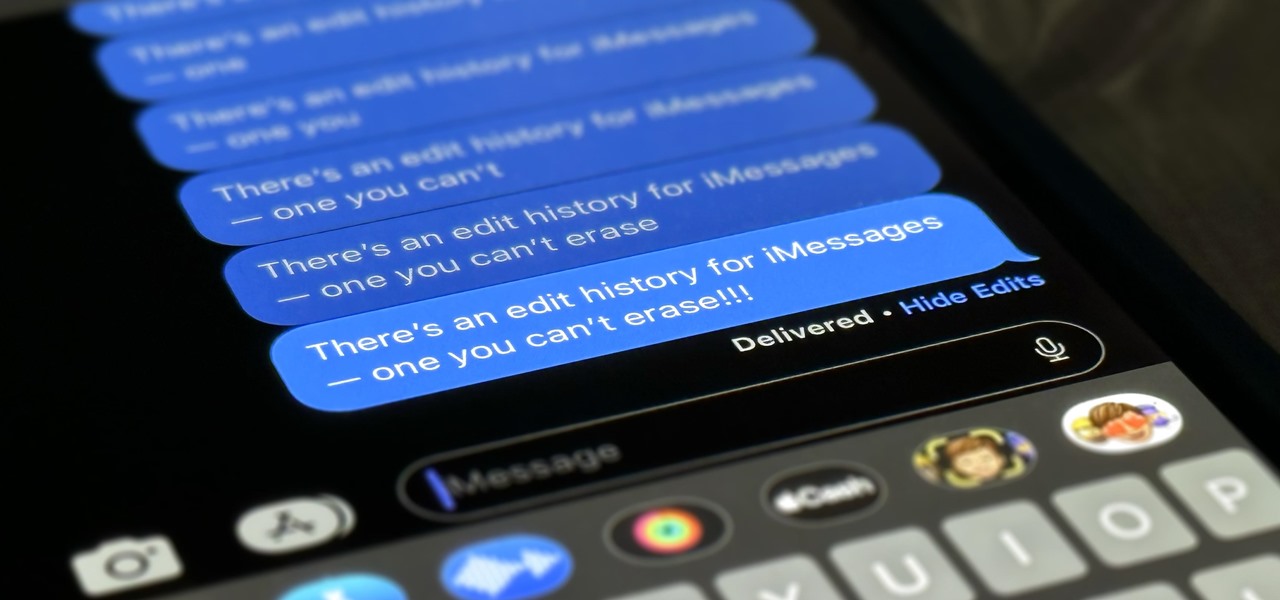
Apple lets you edit iMessages in the Messages app on iOS 16 and later, but everyone in the chat can see all the edits between the final and original text. Thankfully, there's an easy workaround to stop that from happening when you only want them to see the last message and nothing else.

While the third-generation iPhone SE is a decent upgrade from the second-generation model two years prior, there aren't many things about it that stand out from Apple's iPhone 13 lineup. Well, there is one thing worth singling out.

One of the most iconic architectural landmarks on the planet, the Arc de Triomphe in Paris, France, will become a part of augmented reality history thanks to a new project from Snap.

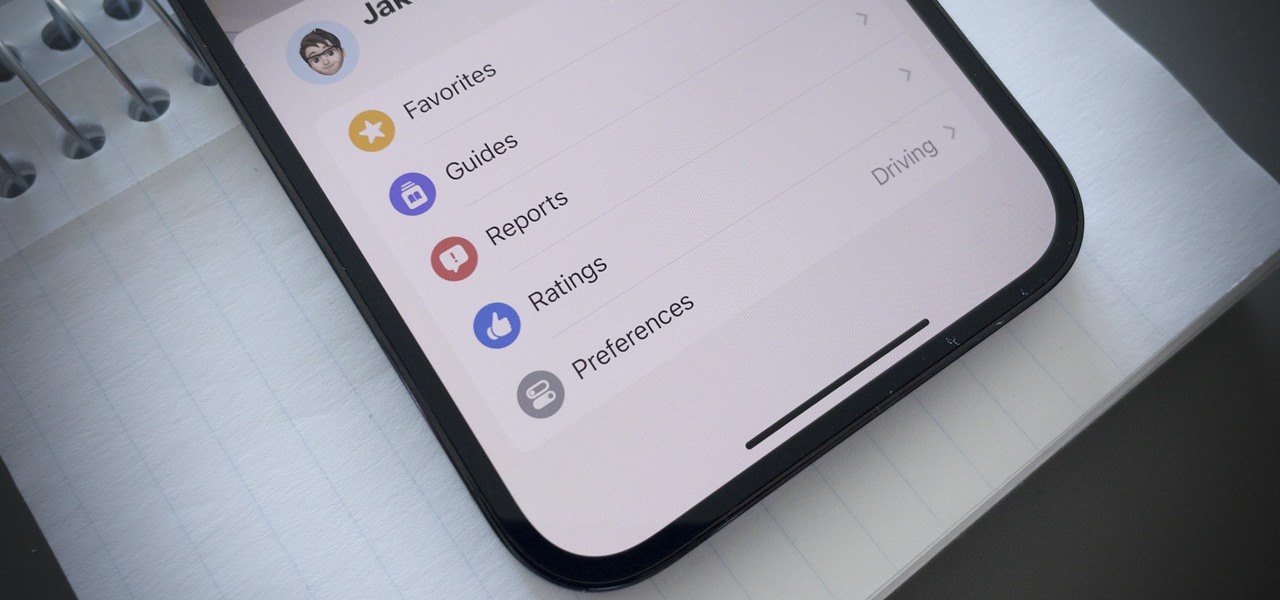
One of the many great reasons to use Apple Maps is to find fun food options, chill cafes, enlightening museums, cute gift shops, and other interesting businesses that you might otherwise overlook, as well as must-see places of interest. But after a while, you might forget about some of these hidden gems. With iOS 15, it will no longer be an issue.

Having thousands of photos and videos in your Photos gallery can make it difficult to find the best ones, but your iPhone does make it a bit easier. Memories, which have been around since iOS 10, automatically group your photos and videos into mini-movies by location, date, or person. It's a fun feature that does the work for you, and it's getting better with the release of iOS 15.

Sound Recognition was introduced with iOS 14, and the accessibility feature uses on-device intelligence to detect 13 different sounds and then notify you whenever it hears one. Apple increases that number to 15 with the addition of two more detectable sounds in iOS 15 that it should have included from the get-go.

When you first open Safari after updating your iPhone to iOS 15, you might be a bit surprised by the design change. Apple attempted to make browsing the web on its smartphones more natural and cohesive, but it may leave you wondering just how to actually navigate your tabs.

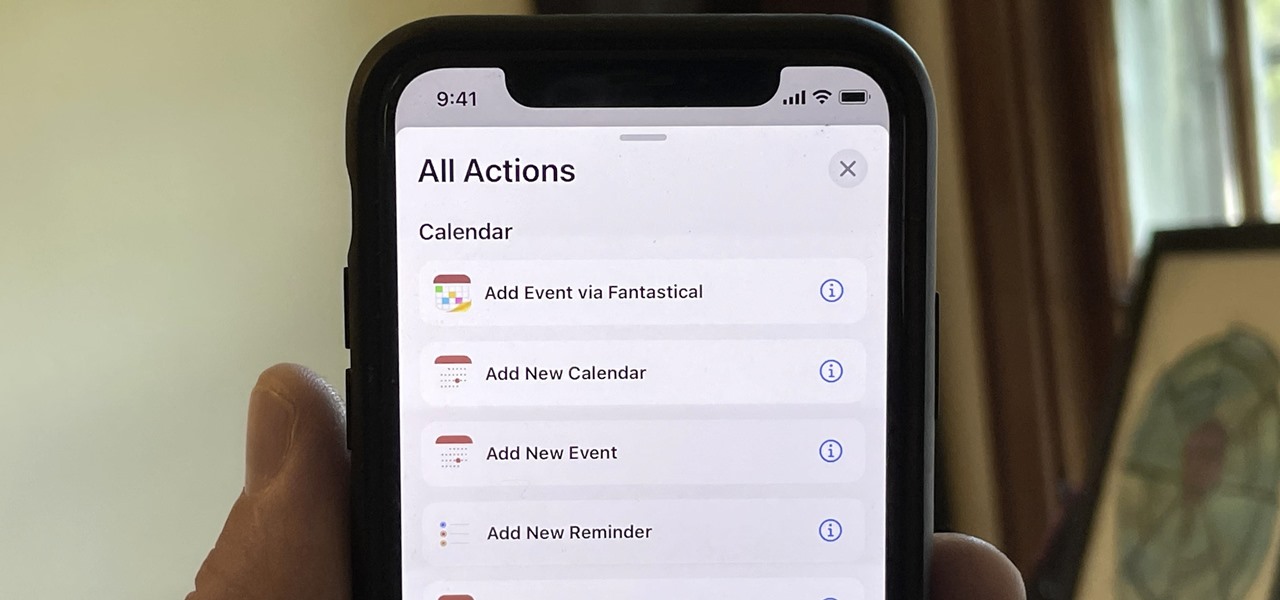
One thing you couldn't do in the Shortcuts app when building a shortcut was browsing the entire list of available actions for all of the apps and services on your iPhone. That all changes in iOS 15.

Apple's exclusive chat services, iMessage and FaceTime, force many of us to stay locked into iOS, iPadOS, and macOS to communicate with other Apple users, so chatting with Android-using friends means SMS texts, third-party messaging apps, and third-party video chat services. However, Apple is breaking boundaries with iOS 15 so that we can FaceTime with Android, Linux, and Windows users.

Your iPhone's search bar has so many great uses. For example, you can quickly find apps on your device, browse different Safari results to find the site that's right for your question, and even search across different iOS apps like Messages, Mail, Notes, and Photos. With iOS 15, Apple has introduced the fastest way yet to start searching with Spotlight on iPhone.

Apple released the eighth iOS 14.5 public beta on Tuesday, April 13. The update (build number 18E5199a) comes three hours after Apple seeded developers 14.5 beta 8, so we know that it contains little-to-no surface-level features or changes. Any changes, at this time, appear to be under the hood.

Did you know that you could learn all the fundamentals of web development for less than $35? Set yourself up for your new coding career in 2021 with The Ultimate 2021 Web Developer & Designer Super Bundle, which is on sale for just $34.99 right now — a huge 98% off the regular price of $1,886.

Android's status bar is ever-present. It sits at the top of almost every screen in every app, making it the most prominent part of your Pixel's theme. So it only makes sense that Google would give you a way to change the icons it uses.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android device to flash TWRP on another.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.